NAT between local networks
-
I have two VLANs – VLAN 10 (192.168.10.0/24) and 11 (192.168.11.0/24). On VLAN 11 there is a device that only accepts TCP requests from the local network (192.168.11.0/24) and not from the gateway (192.168.11.1).
Is there a way to expose an address on VLAN 10 that is forwarded with 1:1 NAT to VLAN 11? So that users on VLAN 10 could access the device in question on a 192.168.10.0/24 address but where the device would see the request as coming from a 192.168.11.0/24 address (any address but the gateway)?
-
HUH??
11.1 is part of 11.0/24 so why would this device not accept connections from it?
What is this device? Your saying pfsense can not ping it? But this device use the gateway to get to internet or vlan 10?
-
@johnpoz It is a home automation device. It is possible to ping the device and the device also use the gateway for limited internet access (calendar information). It also uses the gateway for NTP and DNS. But it does not allow access to the admin interface from outside the 11.0/24 network and not from the gateway. I suppose it is a primitive attempt to reduce the attack surface.
I have had success in setting up a ssh TCP tunnel over a raspberry Pi on VLAN 2 but I would like something more "permanent".
-
Well set a vip on pfsense vlan 11 interface, and then source nat to that..
No need for 1:1 nat or anything.
Just create an outbound nat on the vlan 11 interface using the vip you create, say 11.2 or something.
This way anything talking to 11.X where X is the IP of this device it would look like its coming from 11.2
-
Thanks. Yes that will work - if I can figure out how to set it up ... will try later.
-
Here you go..
My lan is 192.168.9/24
I have a segment I call my dmz that is 192.168.3/24So create the vip on my pfsense dmz interface .222 for example
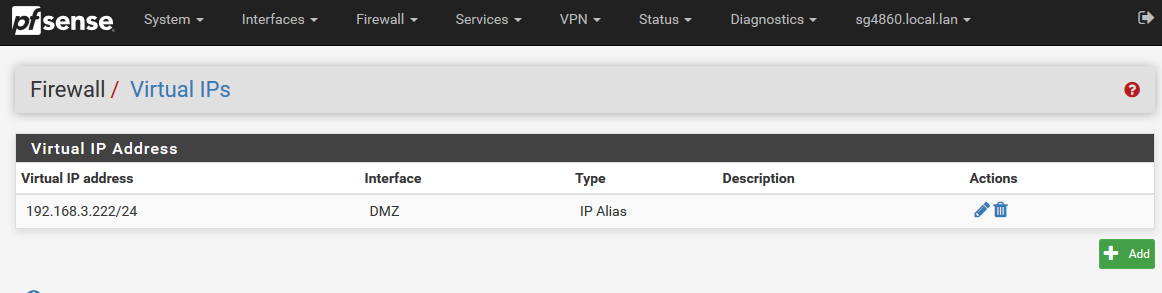
create the outbound nat on the dmz interface to use the vip.
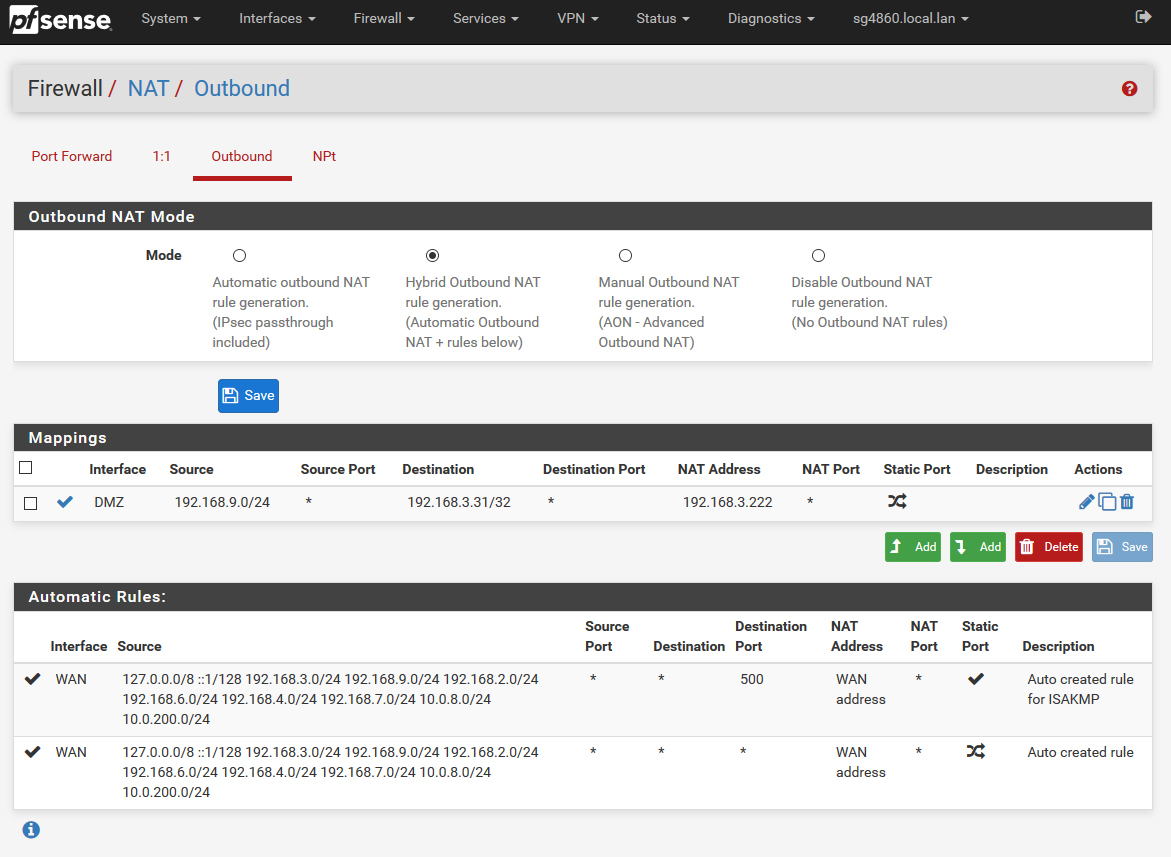
Ping the IP from my lan network, and as you can see from the sniff pfsense nats it to the .222 address
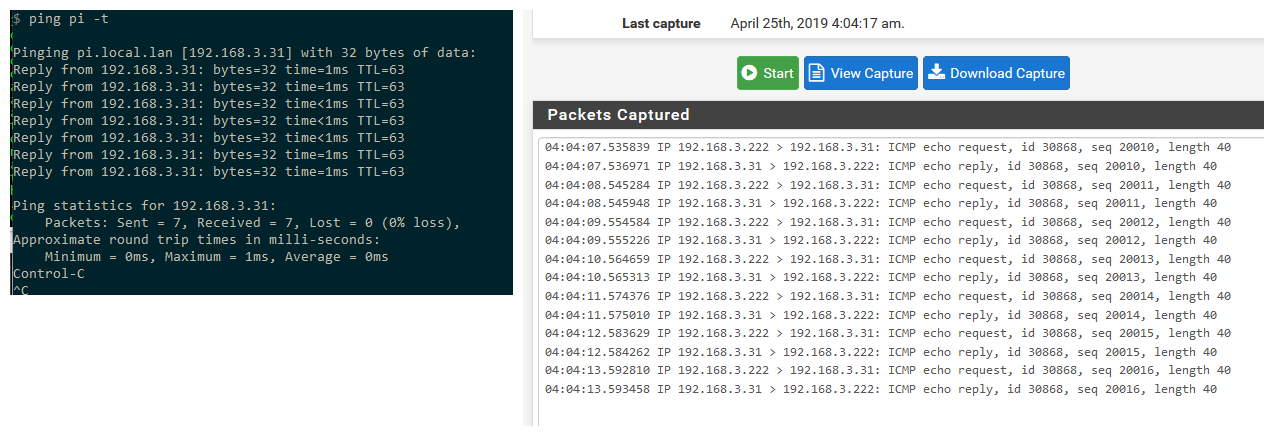
-
Works perfectly. Thanks!