Bridging: physical interface bridge and VLAN bridges
-
Hello,
I'm probably missing something quite basic and I hope that someone here can help:
I have a machine with two physical network interfaces (bge0 and em0), which I need to connect to two redundant switches, one of which is STP root in our network topology. I also need to set up two VLANs on that connections, one for regular traffic (VLAN5) and one for management (VLAN10).
Something like this:

VLAN 5 traffic is untagged, VLAN 10 traffic is tagged, so I've created two bridges on pfsense, configured IP addresses from VLAN subnets on bridge0 + bridge1 interfaces, and configured the switches accordingly:
bridge0: bge0 + em0 bridge1: bge0.10 + em0.10While only bridge0 has STP enabled (I can't enable STP on vlan interfaces on bridge1 anyhow).
However only the untagged bridge0 with physical interface seem to work,as I can access pfsense only on this interface IP address. There are some arp requests coming from bridge1, but responses only arrive to bridge0, as well as any other traffic.
If I set up both bridges as 'VLAN tagged' and configure the switch accordingly:
bridge0: bge0.5 + em0.5 bridge1: bge0.10 + em0.10Everything works (if I connect pfsense only to one switch), but I'm not able to set up the STP on pfsense, as it is seems to be only possible on "physical" interfaces.
If I try something like this (bridge0 has no IP address and serves only for the purpose of STP):
bridge0: bge0 + em0 bridge1: bge0.5 + em0.5 bridge2: bge0.10 + em0.10I can't access bridge1 or bridge2 addresses, as all traffic only arrives to bridge0.
As I've run out of ideas, any help would be greatly appreciated.
Cheers. -
Trying to figure out what is going on here. What is the end goal or what hurdle are you trying to get over by bridging interfaces, etc? It seems like you're trying to construct and implement a workaround instead of addressing the issues with an improved design.
-
I'll help myself with more detailed diagram of our network:
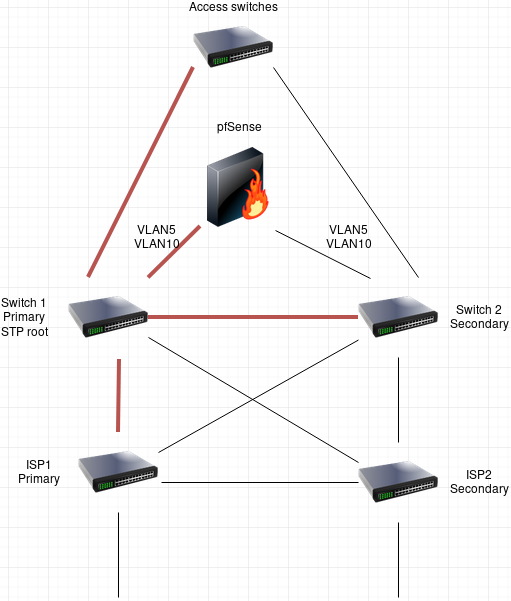
(STP is enabled on all switches to avoid L2 loops, red lines mean that ports on both ends are in forwarding state, pfSense box illustrates what I'm trying to do)If Switch1 (STP root) fails for some reason, the backup switch (Switch 2, secondary) takes it's place. The STP topology is recalculated, so all traffic passes through the secondary.
I'm basically just trying to connect the aforementioned pfSense box to this network, one of it's NICs to switch 1 and one to switch 2, so when switch1 fails, it is still reachable through switch2 on two vlans.
I specifically don't want to connect pfsense to Access switches (on top of the diagram). It would work just fine and do what I want, but those are dedicated for end-user devices.
We had several CentOS servers connected to both switches this way, meaning they had both NICs bridged with STP enabled, but I'm unable to configure the same thing on pfSense. -
I should use tagged vlans only. When bridging a physical interface it captures both untagged and tagged traffic flowing through that interface.
Set the IP address on the bridge not on a member interface.Also check the net.link.bridge.pfil* tunables. To filter traffic on a member interface or the bridge interface. See https://forum.netgate.com/topic/90384/help-clarify-my-understanding-of-the-net-link-bridge-pfil-tunables-please/3
-
Seems more like something in incorrectly stripping the VLAN tags there. You might try running a pcap on the parent interface to make sure packets are arriving from the switch tagged as expected.
Steve
-
@Rai80 I've tried to use only tagged vlans and it kind of works, but I'm not able to configure spanning tree on bridges only consisting of vlan tagged interfaces. I need at least one physical interface bridge to do that.
I've also tried to run packet capture on parent interface and packets indeed arrive with vlan tags, however I can't see them on vlan tagged interface, which seems to confirm what Rai80 says - physical interface probably captures both tagged and untagged traffic.
Playing around with net.link.bridge.pfil* system tunables also didn´t help.
-
Why would you not just do this with a lagg? What specific switches are you working with, take it their are not part of a stack.
-
I'm not sure it's possible to use lagg across two separate switches that are not stacked, i.e. aggregate together some ports on switch 1 and some ports on switch 2.
Both switches are Aruba 2930M. -
@TheGOP said in Bridging: physical interface bridge and VLAN bridges:
Aruba 2930M
you would have to double check but I do not think the 2930M supports VSF, which then you could do a mc-lagg... Pretty sure the 2930Fs support vsf...