How to route VPN traffic accross multiple LAN subnets
-
Good day,
I have two physically separate sites each with their own lan subnets.
The primary site where the server is has subnet 192.168.3.0/24 The second site is 192.168.1.0/24
The sites are connected with a Ubiquiti wireless bridge using a separate subnet 192.168.0.0/24.
To achieve routing I have a pfSense VM on each site. So far the terminals on site B can communicate with the server on site A and visa versa. But now I need to connect a remote vpn client to a OpenVPN AS server at site B and have it communicate with the server at site A.
The graphic gives a bit a clearer picture.
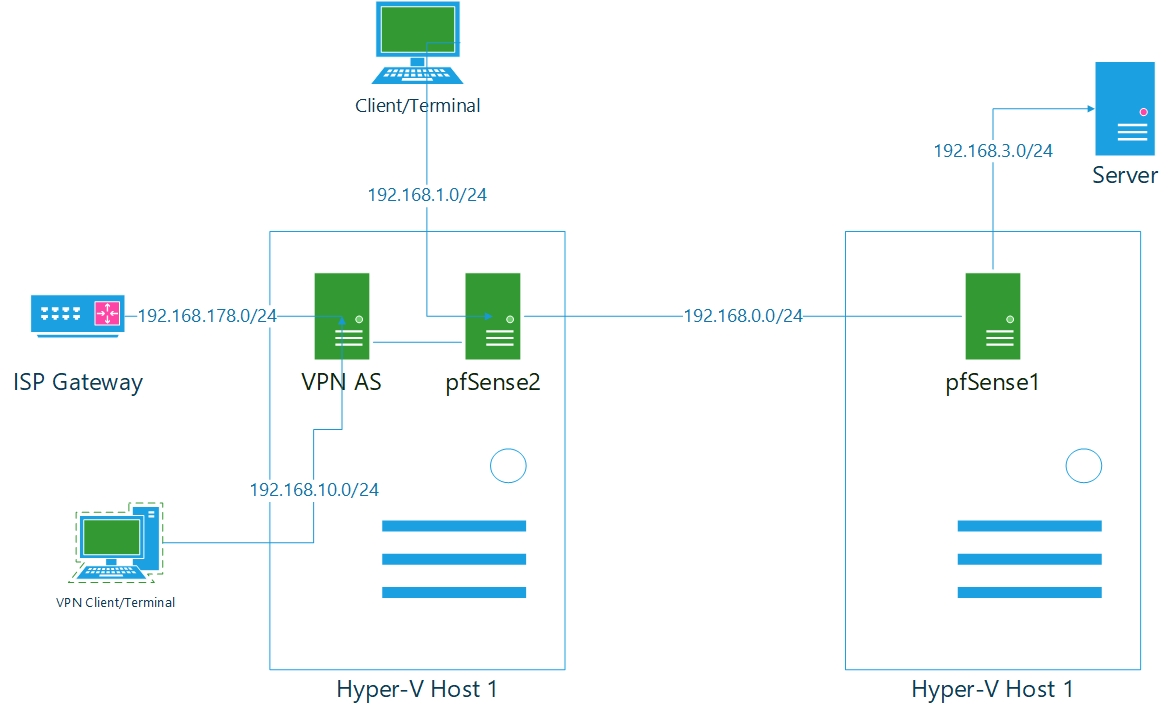
I am using static routes to facilitate communication between subnet 192.168.3.0/24 and 192.168.1.0/24 over 192.168.0.0/24.Now my VPN client and server has an IP address from 192.168.10.0/24
My question is where should I put what static routes to facilitate communication from the VPN client to the server and visa versa?
-
Not clear how the routing is working here. Static routes have to be set on the default gateway to get it work without additional configurations. However, it doesn't seem that the pfSense doing your routing between the sites are the default gateways.
Anyway, if it works for the to sites it should work for the VPN as well.
But that requires that pfSense2 has a route to the VPN client tunnel network.On the VPN server push the routes for both local networks, 192.168.3.0/24 and 192.168.1.0/24 to the client.
On site A add a route for the VPN tunnel subnet to pfSense pointing to pfSense2.Otherwise you have to offer more infos about your actual routing.
-
why would you not just run the vpn server on pfsense on host 1? This makes it much easier.
Now you just need to add your remote 192.168.3.0/24 to your local networks in your vpn server setup on pfsense.
As long as pfsense1 uses pfsense 2 as it default route, or has a route to get to your vpn tunnel network 192.168.10, or you source nat it to your 192.168.0/24 transit.
-
@viragomann
Thanks for the assist I think I got it.pfSense1 is the default gateway for 192.168.3.0/24
it has a static route to 192.168.1.0/24 where the gateway is 192.168.0.11 (the OPT1 address of pfSense2)pfSense2 is the default gateway for 192.168.1.0/24 and it has a static route to 192.168.3.0/24 where the gateway is 192.168.0.1 (the OPT1 address of pfSense1)
I did add a static route 192.168.10.0/24 to pfSense2 where the gateway is 192.168.1.23 (the eth1 address of the VPN AS server) with that I was able to ping my VPN client
I then added a static route 192.168.10.0/24 to pfSense1 where the gateway is again 192.168.0.11
and I added a static route 192.168.3.0/24 to both the VPN AS server and VPN client where the gateway is 192.168.1.2 (the LAN address of pfSense2)Lastly I added a static route 192.168.10.0/24 to the server where the gateway is LAN port on pfSense1.
And obviously set the appropriate firewall rules and I got a ping. So thank you for the help.
-
I do have VPN AS server on host 1. But the other day the ISP connection went down on that site so I needed an alternate connection. The VPN client just so happens to be the CEO of the company so telling him he can't work cause the internet is down on one site is not an option.
-
You have pfsense on the HOST, why would you not just let it host your vpn? Its FREE vs openvpnas - which other than the 2 free licenses you have to pay for.
-
@johnpoz
I use IPSec to create a site-to-site tunnel should the wireless bridge go down. (Hilariously, this is no longer working, but that is a different problem for a different day).I wanted to use the pfSense for the VPN clients but had too much problems setting it up with the win 10 clients. I only have two VPN clients so it is not really a problem at the moment.
But I will probably sit and redesign the whole network. Or I should just get some hardware routers. The win 10 hosts are giving me hell as well.