IPSec Mobile from AWS pfSense AMI to Windows 10
-
I'm starting to run out of ideas. I am setting up an IpSec connection from Windows 10 to a pfSense AMI running on Amazon. I've gone through all the articles I could find on this. Some contrary to each other. I've got the connection to the point (according to the log) where the IpSec server has sent IKE_SA_INIT response 0 but I don't see anything beyond that. Of course Windows just says "The network connection between your computer and the VPN server"... and the log shows "The error code returned on failure is 809."
Configuration on pfSense:
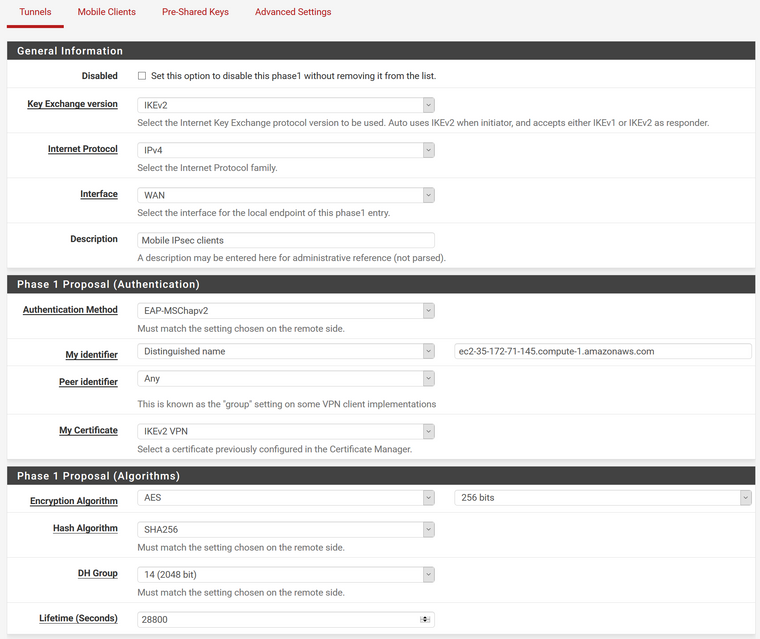
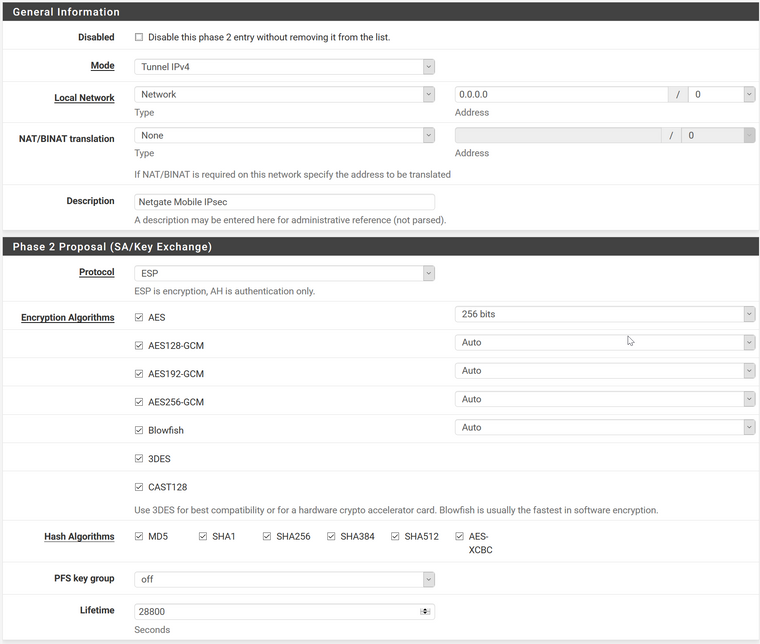
Windows 10:
Name : AWS2
ServerAddress : ec2-35-172-71-145.compute-1.amazonaws.com
AllUserConnection : False
Guid : {4ABABD2E-4032-4964-AD66-5D3DB6614F24}
TunnelType : Ikev2
AuthenticationMethod : {Eap}
EncryptionLevel : Custom
L2tpIPsecAuth :
UseWinlogonCredential : False
EapConfigXmlStream : #document
ConnectionStatus : Disconnected
RememberCredential : True
SplitTunneling : True
DnsSuffix :
IdleDisconnectSeconds : 0So what am I missing?
-
P.S. Here's what I see in the IpSec log:
Apr 25 09:21:42 charon 06[IKE] <con7000|2> nothing to initiate
Apr 25 09:21:42 charon 06[IKE] <con7000|2> activating new tasks
Apr 25 09:21:42 charon 06[NET] <con7000|2> sending packet: from 10.20.20.26[4500] to 52.20.128.152[4500] (92 bytes)
Apr 25 09:21:42 charon 06[ENC] <con7000|2> generating INFORMATIONAL_V1 request 3857552390 [ HASH N(DPD_ACK) ]
Apr 25 09:21:42 charon 06[IKE] <con7000|2> activating ISAKMP_DPD task
Apr 25 09:21:42 charon 06[IKE] <con7000|2> activating new tasks
Apr 25 09:21:42 charon 06[IKE] <con7000|2> queueing ISAKMP_DPD task
Apr 25 09:21:42 charon 06[ENC] <con7000|2> parsed INFORMATIONAL_V1 request 4023988409 [ HASH N(DPD) ]
Apr 25 09:21:42 charon 06[NET] <con7000|2> received packet: from 52.20.128.152[4500] to 10.20.20.26[4500] (92 bytes)
Apr 25 09:21:40 charon 06[NET] <4> sending packet: from 10.20.20.26[500] to 50.232.48.141[500] (473 bytes)
Apr 25 09:21:40 charon 06[ENC] <4> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ]
Apr 25 09:21:40 charon 06[IKE] <4> sending cert request for "C=US, ST=MN, L=Minneapolis, O=Prepare-Enrich, E=wayne.johnson@prepare-enrich.com, CN=PEAWSVPN"
Apr 25 09:21:40 charon 06[IKE] <4> remote host is behind NAT
Apr 25 09:21:40 charon 06[IKE] <4> local host is behind NAT, sending keep alives
Apr 25 09:21:40 charon 06[CFG] <4> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Apr 25 09:21:40 charon 06[CFG] <4> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Apr 25 09:21:40 charon 06[CFG] <4> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Apr 25 09:21:40 charon 06[CFG] <4> proposal matches
Apr 25 09:21:40 charon 06[CFG] <4> selecting proposal:
Apr 25 09:21:40 charon 06[IKE] <4> IKE_SA (unnamed)[4] state change: CREATED => CONNECTING
Apr 25 09:21:40 charon 06[IKE] <4> 50.232.48.141 is initiating an IKE_SA
Apr 25 09:21:40 charon 06[ENC] <4> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02
Apr 25 09:21:40 charon 06[IKE] <4> received Vid-Initial-Contact vendor ID
Apr 25 09:21:40 charon 06[IKE] <4> received MS-Negotiation Discovery Capable vendor ID
Apr 25 09:21:40 charon 06[IKE] <4> received MS NT5 ISAKMPOAKLEY v9 vendor ID
Apr 25 09:21:40 charon 06[CFG] <4> found matching ike config: 10.20.20.26...%any with prio 1052
Apr 25 09:21:40 charon 06[CFG] <4> candidate: 10.20.20.26...%any, prio 1052
Apr 25 09:21:40 charon 06[CFG] <4> candidate: %any...%any, prio 24
Apr 25 09:21:40 charon 06[CFG] <4> looking for an ike config for 10.20.20.26...50.232.48.141
Apr 25 09:21:40 charon 06[ENC] <4> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ]
Apr 25 09:21:40 charon 06[NET] <4> received packet: from 50.232.48.141[500] to 10.20.20.26[500] (544 bytes) -
Solved (I think).
Turns out that not only do you have to add IPSec ports to the pfSense firewall, I had to add UDP 4500 to the AWS Security Group (AWS version of a firewall). The person who set up the Security Group had added UDP 500, but not 4500.