Static Route via IPSec Tunnel
-
Hi :)
I am looking for some guidance as I can't get routing working.
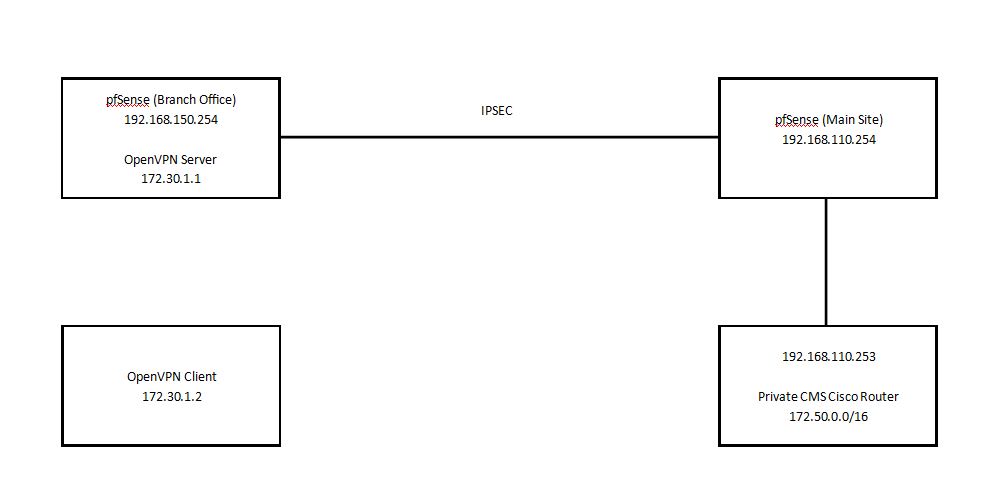
The goal here is for an OpenVPN Client (Laptop User) to OpenVPN into the BranchOffice. And then have routing to the Private CMS System via the Dedicated Cisco router at the Main Site.
Laptop User OpenVPN Client (172.30.1.2) <-------> 172.30.1.1 (Open VPN Server) <---- via IPSEC Link ---> 192.168.110.254 (pfsense Main Site) <--------> Private CMS Platform (172.50.1.100)
The "Main Site" has access to a Private CMS System which is on 172.50.0.0/16. So currently a client on 192.168.110.0/24 can access the Web portal which is on 172.50.1.100. This works via a Static Route on the Main Site pfSense Router.
The CMS provider has created a Static Route for 172.30.1.0/24 to go to 192.168.110.254.
I have an IPSEC Tunnel between 192.168.150.0 <-----> 192.168.110.0 which works perfectly.
I first tried creating a static route on the Branch Office pfSense Router for 172.50.0.0/16 to go to the Main Site pfSense Router (192.168.110.254) which did not work. I then delete this, and created a static route for 172.50.0.0/16 to go directly to the Private CMS Cisco Router 192.168.110.253 which also does not work.
Anyone got any ideas of where I am going wrong here ?
Cheers, Scott
-
Besides 172.50.0.0/16 being real IPs and no private RFC1918 range (what can be quite problematic of its own), I think you are missing some routes and policies on the way.
Wouldn't it be easier to just NAT 172.30.1.0/24 via IPSEC so the VPN Clients arriving via IPsec look like they come from a local IP from 192.168.150.x? Otherwise all devices will need policies to allow traffic from and route back and forth between 172.30.1.0/24 and 172.50.0.0/16. So your Main Site pfSense needs to know about 172.30.1.0/24 (if it doesn't, you didn't tell) as well as the CMS Cisco and your Branch Office pfSense needs to know about 172.50.0.0/16.
I'd add that as Phase 2 entries to the IPsec tunnel so the routes will be pushed automatically.