IPSec VPN to OpenWrt Strongswan Travel Router
-
I am trying to make my OpenWrt Travel Router connect via VPN to my pfSense. While I can get this going with OpenVPN, performance on the OpenWrt is not really overwhelming, so I'd like to use IPSec instead.
The ideal target scenario would be for the OpenWrt router to route all traffic from all connected clients to pfSense. However, I'm running into some very basic issues, as the two are not connecting. The error message I'm getting on the pfSense side is
peer requested EAP, config unacceptableI'm not sure if this means that I configured the wrong authorization method on OpenWrt, if there is something wrong with how I'm using the certificate created with pfSense, or if it's something else. The OpenWrt side just says "received AUTHENTICATION_FAILED notify error", which means even less to me.
In case it helps, I have attached more log information and the configuration below.
pfsense log
[...] Apr 30 18:52:36 charon 09[CFG] <5> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Apr 30 18:52:36 charon 09[CFG] <5> received supported signature hash algorithms: sha256 sha384 sha512 identity Apr 30 18:52:36 charon 09[CFG] <5> sending supported signature hash algorithms: sha256 sha384 sha512 identity Apr 30 18:52:36 charon 09[IKE] <5> sending cert request for "C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA" Apr 30 18:52:36 charon 09[ENC] <5> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Apr 30 18:52:36 charon 09[NET] <5> sending packet: from 192.168.1.1[500] to 192.168.1.27[500] (297 bytes) Apr 30 18:52:36 charon 09[NET] <5> received packet: from 192.168.1.27[4500] to 192.168.1.1[4500] (608 bytes) Apr 30 18:52:36 charon 09[ENC] <5> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ IDr CPRQ(ADDR DNS) SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Apr 30 18:52:36 charon 09[IKE] <5> received cert request for "C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA" Apr 30 18:52:36 charon 09[CFG] <5> looking for peer configs matching 192.168.1.1[C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA]...192.168.1.27[CN=OpenwrtVPN, C=..., ST=..., L=..., O=...] Apr 30 18:52:36 charon 09[CFG] <5> candidate "bypasslan", match: 1/1/24 (me/other/ike) Apr 30 18:52:36 charon 09[CFG] <bypasslan|5> selected peer config 'bypasslan' Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> peer requested EAP, config unacceptable Apr 30 18:52:36 charon 09[CFG] <bypasslan|5> no alternative config found Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> processing INTERNAL_IP4_ADDRESS attribute Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> processing INTERNAL_IP4_DNS attribute Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> peer supports MOBIKE Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> got additional MOBIKE peer address: 192.168.168.1 Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> got additional MOBIKE peer address: fd3c:741b:b3ff::1 Apr 30 18:52:36 charon 09[ENC] <bypasslan|5> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Apr 30 18:52:36 charon 09[NET] <bypasslan|5> sending packet: from 192.168.1.1[4500] to 192.168.1.27[4500] (80 bytes) Apr 30 18:52:36 charon 09[IKE] <bypasslan|5> IKE_SA bypasslan[5] state change: CONNECTING => DESTROYINGOn the openwrt side, it looks like this:
Tue Apr 30 16:52:36 2019 daemon.info : 06[CFG] id '192.168.1.1' not confirmed by certificate, defaulting to 'C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA' Tue Apr 30 16:52:36 2019 daemon.info : 06[CFG] added configuration 'ikev2-eap-tls-asymmetric' Tue Apr 30 16:52:36 2019 daemon.info : 08[CFG] received stroke: initiate 'ikev2-eap-tls-asymmetric' Tue Apr 30 16:52:36 2019 daemon.info : 08[IKE] initiating IKE_SA ikev2-eap-tls-asymmetric[1] to 192.168.1.1 Tue Apr 30 16:52:36 2019 authpriv.info : 08[IKE] initiating IKE_SA ikev2-eap-tls-asymmetric[1] to 192.168.1.1 Tue Apr 30 16:52:36 2019 daemon.info : 08[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Tue Apr 30 16:52:36 2019 daemon.info : 08[NET] sending packet: from 192.168.1.27[500] to 192.168.1.1[500] (1072 bytes) Tue Apr 30 16:52:36 2019 daemon.info : 11[NET] received packet: from 192.168.1.1[500] to 192.168.1.27[500] (297 bytes) Tue Apr 30 16:52:36 2019 daemon.info : 11[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Tue Apr 30 16:52:36 2019 daemon.info : 11[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Tue Apr 30 16:52:36 2019 daemon.info : 11[IKE] received cert request for "C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA" Tue Apr 30 16:52:36 2019 daemon.info : 11[IKE] sending cert request for "C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA" Tue Apr 30 16:52:36 2019 daemon.info : 11[IKE] establishing CHILD_SA ikev2-eap-tls-asymmetric{1} Tue Apr 30 16:52:36 2019 authpriv.info : 11[IKE] establishing CHILD_SA ikev2-eap-tls-asymmetric{1} Tue Apr 30 16:52:36 2019 daemon.info : 11[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ IDr CPRQ(ADDR DNS) SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Tue Apr 30 16:52:36 2019 daemon.info : 11[NET] sending packet: from 192.168.1.27[4500] to 192.168.1.1[4500] (608 bytes) Tue Apr 30 16:52:36 2019 daemon.info : 12[NET] received packet: from 192.168.1.1[4500] to 192.168.1.27[4500] (80 bytes) Tue Apr 30 16:52:36 2019 daemon.info : 12[ENC] parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ] Tue Apr 30 16:52:36 2019 daemon.info : 12[IKE] received AUTHENTICATION_FAILED notify errorI have setup pfSense as follows:
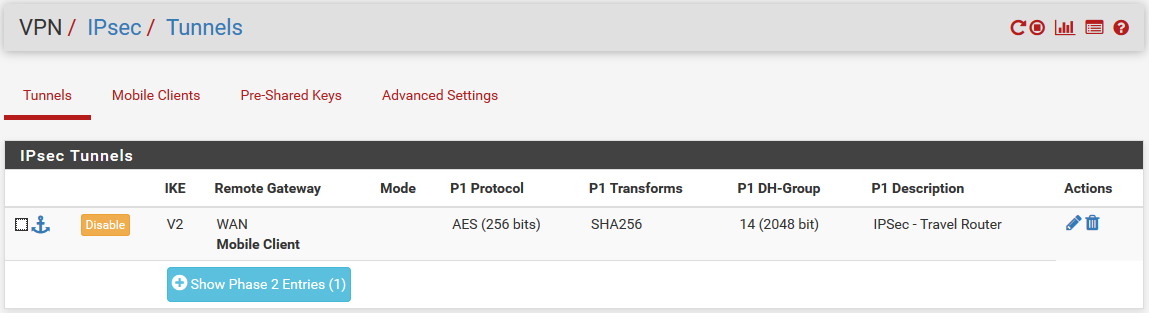
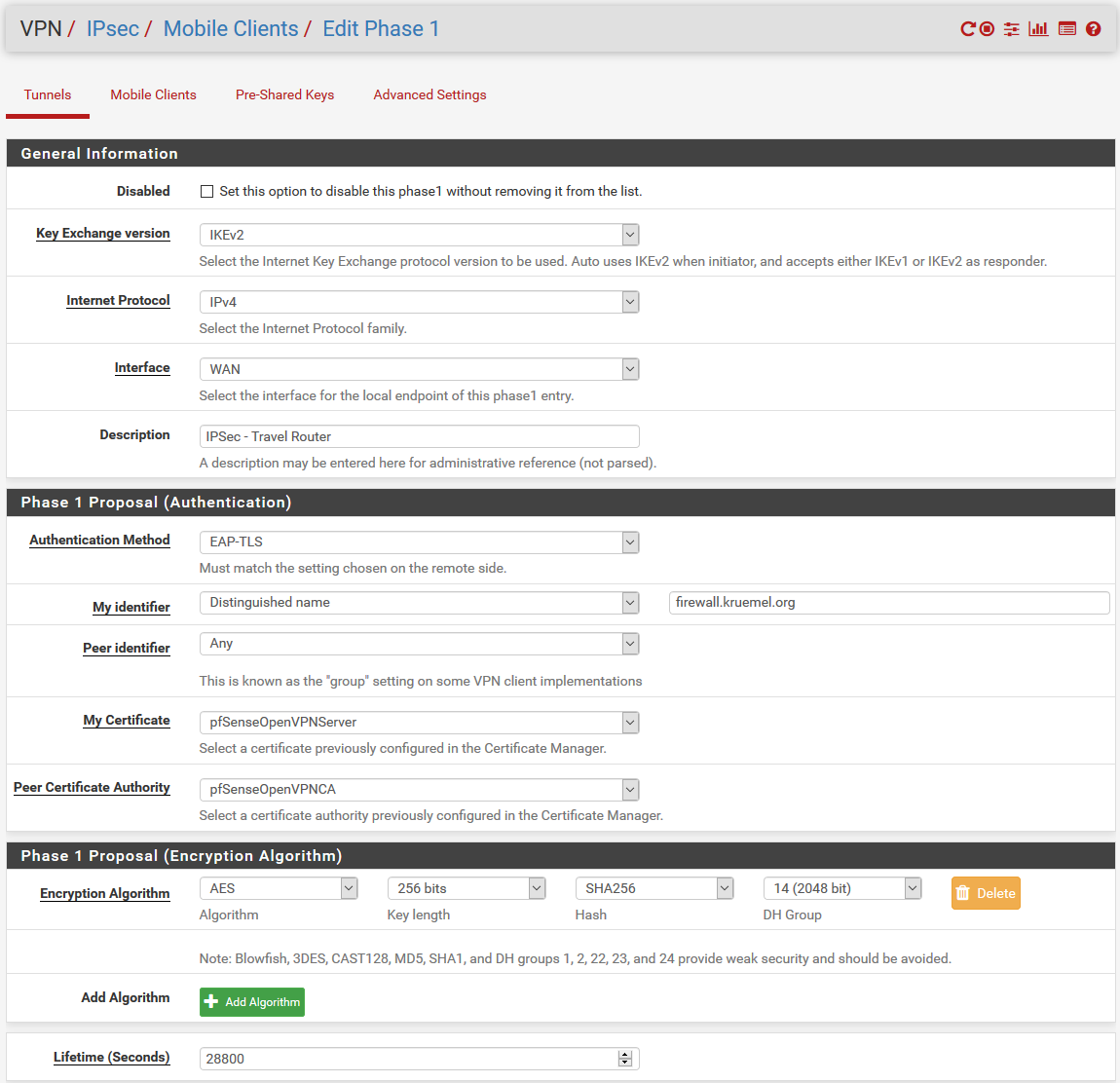

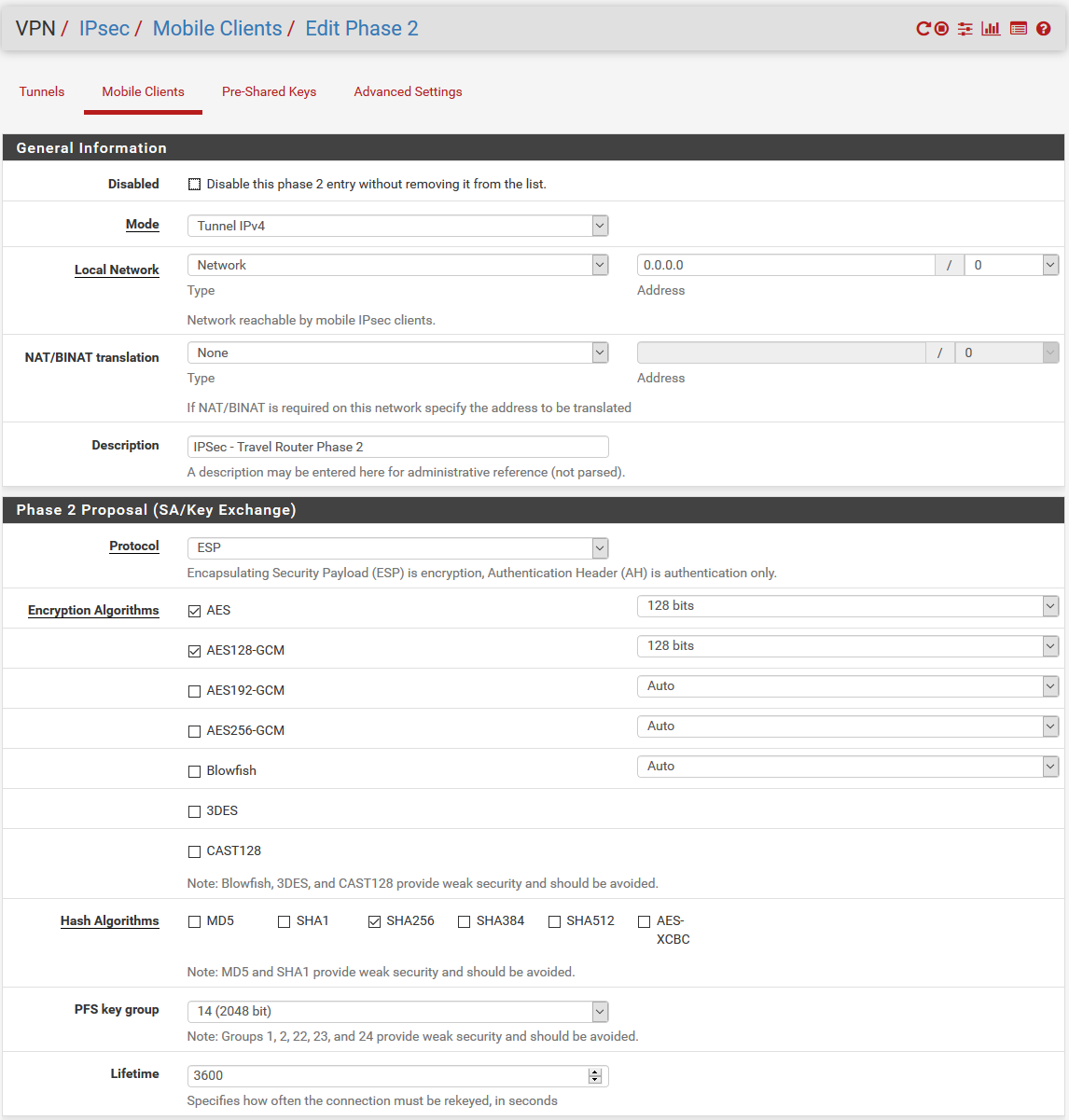

On the OpenWrt side, I am using these configs:
ipsec.conf:
conn rw-base dpdaction=restart dpddelay=30 dpdtimeout=90 fragmentation=yes conn vip-base also=rw-base leftsourceip=%config conn ikev2-eap-tls-asymmetric also=vip-base keyexchange=ikev2 leftcert=/etc/certs.d/openwrt.crt leftauth=eap-tls rightauth=pubkey rightcert=/etc/certs.d/pfsense_ca.crt right = 192.168.1.1 rightsubnet=0.0.0.0/0 auto=startipsec.secrets:
: RSA /etc/certs.d/openwrt.keyswanctl.conf:
connections { ikev2-eap-tls-asymmetric { version = 2 remote_addrs = 192.168.1.1 vips = 0.0.0.0, :: local-1 { auth = eap-tls certs = /etc/certs.d/openwrt.crt } remote-1 { certs = /etc/certs.d/pfsense_ca.crt } children { ikev2-eap-tls-asymmetric { remote_ts = 0.0.0.0/0 } } } secrets { private-mine { file = /etc/certs.d/openwrt.key } } -
@highc said in IPSec VPN to OpenWrt Strongswan Travel Router:
OpenWrt Travel Router
Hey
-
I think you are wrong to set up Openwrt
Here is a link that may help you
https://strongswan.org/testresults.html (example 215) -
I think you need a site-to-site connection between Pfsense and Openwrt
But the problem is that maybe your Openwrt router does not have a fixed ip address, and you can create such a connection using Dyndns ( I did not try ) or making changes to the configuration files PFSense ( this option works for me)
-
-
Thanks for trying to help me. I tried to do what you said, i.e. setup a new site-to-site config in pfSense, and changed OpenWrt configs in line with example 215. I also used local addresses for a start. However, I am still getting the error "peer requested EAP, config unacceptable" in pfSense and "AUTHENTICATION_FAILED" in OpenWrt...
log from pfsense:
May 1 12:33:24 ipsec_starter 97379 'con1000' routed May 1 12:33:54 charon 10[NET] <1> received packet: from 192.168.1.27[500] to 192.168.1.1[500] (548 bytes) May 1 12:33:54 charon 10[ENC] <1> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] May 1 12:33:54 charon 10[CFG] <1> looking for an IKEv2 config for 192.168.1.1...192.168.1.27 May 1 12:33:54 charon 10[CFG] <1> candidate: %any...%any, prio 24 May 1 12:33:54 charon 10[CFG] <1> candidate: 192.168.1.1...192.168.1.27, prio 3100 May 1 12:33:54 charon 10[CFG] <1> found matching ike config: 192.168.1.1...192.168.1.27 with prio 3100 May 1 12:33:54 charon 10[IKE] <1> 192.168.1.27 is initiating an IKE_SA May 1 12:33:54 charon 10[IKE] <1> IKE_SA (unnamed)[1] state change: CREATED => CONNECTING May 1 12:33:54 charon 10[CFG] <1> selecting proposal: May 1 12:33:54 charon 10[CFG] <1> proposal matches May 1 12:33:54 charon 10[CFG] <1> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 May 1 12:33:54 charon 10[CFG] <1> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 1 12:33:54 charon 10[CFG] <1> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 1 12:33:54 charon 10[CFG] <1> received supported signature hash algorithms: sha256 sha384 sha512 identity May 1 12:33:54 charon 10[IKE] <1> DH group CURVE_25519 unacceptable, requesting MODP_2048 May 1 12:33:54 charon 10[ENC] <1> generating IKE_SA_INIT response 0 [ N(INVAL_KE) ] May 1 12:33:54 charon 10[NET] <1> sending packet: from 192.168.1.1[500] to 192.168.1.27[500] (38 bytes) May 1 12:33:54 charon 10[IKE] <1> IKE_SA (unnamed)[1] state change: CONNECTING => DESTROYING May 1 12:33:54 charon 10[NET] <2> received packet: from 192.168.1.27[500] to 192.168.1.1[500] (772 bytes) May 1 12:33:54 charon 10[ENC] <2> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] May 1 12:33:54 charon 10[CFG] <2> looking for an IKEv2 config for 192.168.1.1...192.168.1.27 May 1 12:33:54 charon 10[CFG] <2> candidate: %any...%any, prio 24 May 1 12:33:54 charon 10[CFG] <2> candidate: 192.168.1.1...192.168.1.27, prio 3100 May 1 12:33:54 charon 10[CFG] <2> found matching ike config: 192.168.1.1...192.168.1.27 with prio 3100 May 1 12:33:54 charon 10[IKE] <2> 192.168.1.27 is initiating an IKE_SA May 1 12:33:54 charon 10[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING May 1 12:33:54 charon 10[CFG] <2> selecting proposal: May 1 12:33:54 charon 10[CFG] <2> proposal matches May 1 12:33:54 charon 10[CFG] <2> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/MODP_2048/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/MODP_2048/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192 May 1 12:33:54 charon 10[CFG] <2> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 1 12:33:54 charon 10[CFG] <2> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 1 12:33:54 charon 10[CFG] <2> received supported signature hash algorithms: sha256 sha384 sha512 identity May 1 12:33:54 charon 10[CFG] <2> sending supported signature hash algorithms: sha256 sha384 sha512 identity May 1 12:33:54 charon 10[IKE] <2> sending cert request for "C=..., ST=..., L=..., O=..., E=..., CN=pfSenseOpenVPNCA" May 1 12:33:54 charon 10[ENC] <2> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] May 1 12:33:54 charon 10[NET] <2> sending packet: from 192.168.1.1[500] to 192.168.1.27[500] (489 bytes) May 1 12:33:55 charon 09[NET] <2> received packet: from 192.168.1.27[4500] to 192.168.1.1[4500] (416 bytes) May 1 12:33:55 charon 09[ENC] <2> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] May 1 12:33:55 charon 09[CFG] <2> looking for peer configs matching 192.168.1.1[192.168.1.1]...192.168.1.27[CN=OpenwrtVPN, C=..., ST=..., L=..., O=...] May 1 12:33:55 charon 09[CFG] <2> candidate "bypasslan", match: 1/1/24 (me/other/ike) May 1 12:33:55 charon 09[CFG] <bypasslan|2> selected peer config 'bypasslan' May 1 12:33:55 charon 09[IKE] <bypasslan|2> peer requested EAP, config unacceptable May 1 12:33:55 charon 09[CFG] <bypasslan|2> no alternative config found May 1 12:33:55 charon 09[IKE] <bypasslan|2> peer supports MOBIKE May 1 12:33:55 charon 09[IKE] <bypasslan|2> got additional MOBIKE peer address: 192.168.168.1 May 1 12:33:55 charon 09[IKE] <bypasslan|2> got additional MOBIKE peer address: fd3c:741b:b3ff::1 May 1 12:33:55 charon 09[ENC] <bypasslan|2> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] May 1 12:33:55 charon 09[NET] <bypasslan|2> sending packet: from 192.168.1.1[4500] to 192.168.1.27[4500] (80 bytes) May 1 12:33:55 charon 09[IKE] <bypasslan|2> IKE_SA bypasslan[2] state change: CONNECTING => DESTROYINGopenwrt.log (timezone not set correctly...):
Wed May 1 10:33:54 2019 daemon.info : 13[NET] sending packet: from 192.168.1.27[500] to 192.168.1.1[500] (548 bytes) Wed May 1 10:33:54 2019 daemon.info : 14[NET] received packet: from 192.168.1.1[500] to 192.168.1.27[500] (38 bytes) Wed May 1 10:33:54 2019 daemon.info : 14[ENC] parsed IKE_SA_INIT response 0 [ N(INVAL_KE) ] Wed May 1 10:33:54 2019 daemon.info : 14[IKE] peer didn't accept DH group CURVE_25519, it requested MODP_2048 Wed May 1 10:33:54 2019 daemon.info : 14[IKE] initiating IKE_SA home[1] to 192.168.1.1 Wed May 1 10:33:54 2019 daemon.info : 14[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Wed May 1 10:33:54 2019 daemon.info : 14[NET] sending packet: from 192.168.1.27[500] to 192.168.1.1[500] (772 bytes) Wed May 1 10:33:54 2019 daemon.info : 15[NET] received packet: from 192.168.1.1[500] to 192.168.1.27[500] (489 bytes) Wed May 1 10:33:54 2019 daemon.info : 15[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Wed May 1 10:33:54 2019 daemon.info : 15[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Wed May 1 10:33:55 2019 daemon.info : 15[IKE] received 1 cert requests for an unknown ca Wed May 1 10:33:55 2019 daemon.info : 15[IKE] establishing CHILD_SA home{1} Wed May 1 10:33:55 2019 daemon.info : 15[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Wed May 1 10:33:55 2019 daemon.info : 15[NET] sending packet: from 192.168.1.27[4500] to 192.168.1.1[4500] (416 bytes) Wed May 1 10:33:55 2019 daemon.info : 16[NET] received packet: from 192.168.1.1[4500] to 192.168.1.27[4500] (80 bytes) Wed May 1 10:33:55 2019 daemon.info : 16[ENC] parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ] Wed May 1 10:33:55 2019 daemon.info : 16[IKE] received AUTHENTICATION_FAILED notify errorpfSense config:
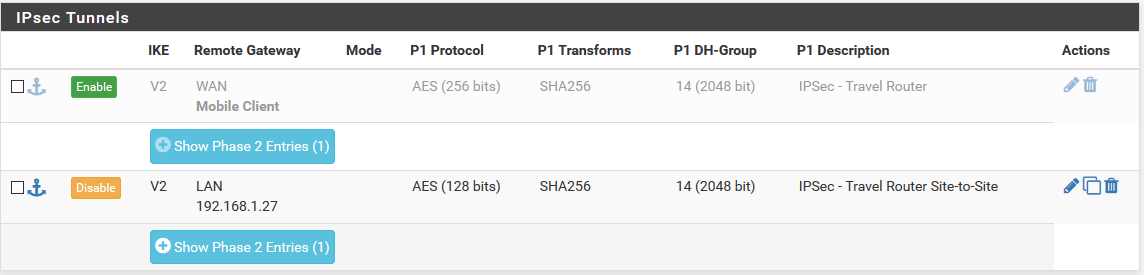
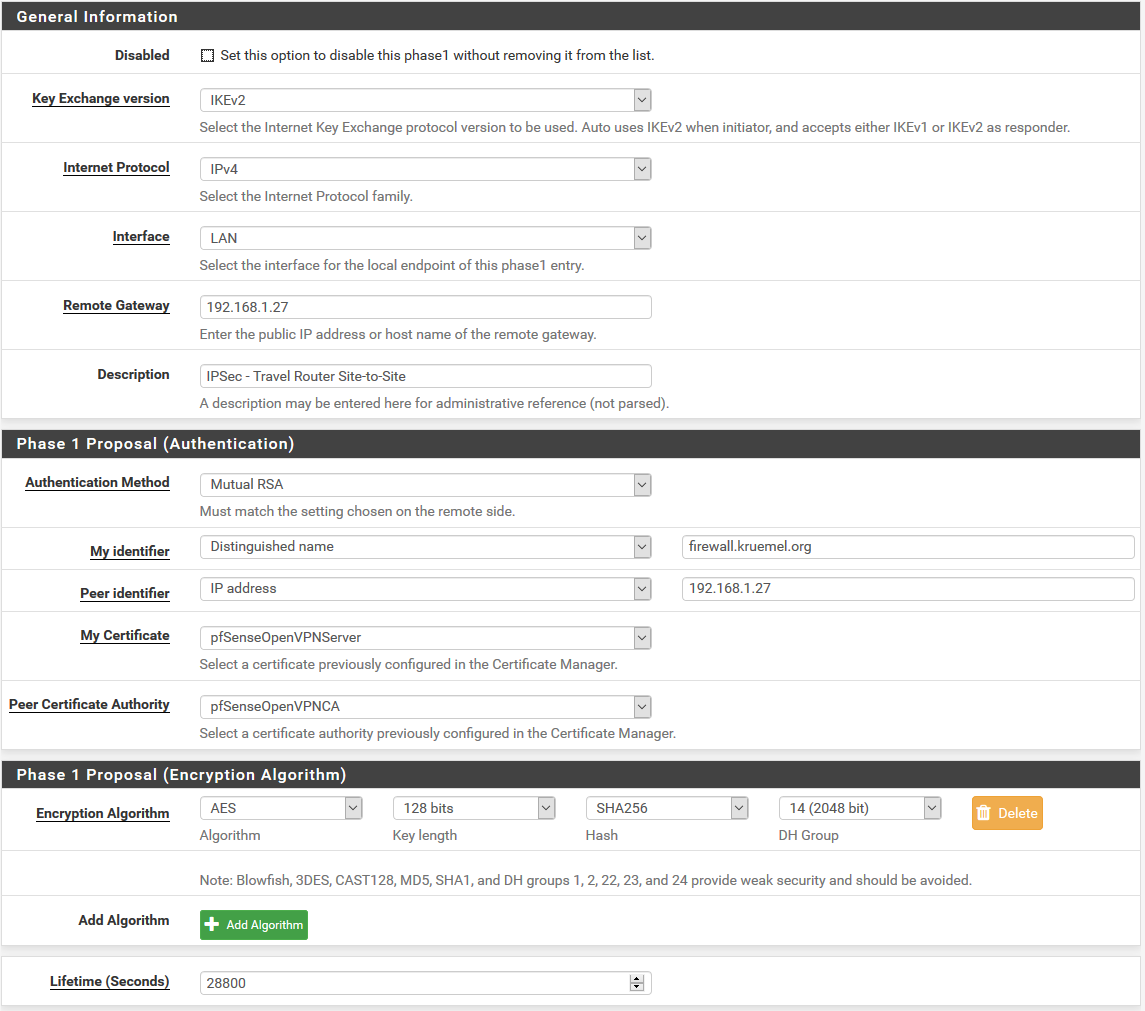
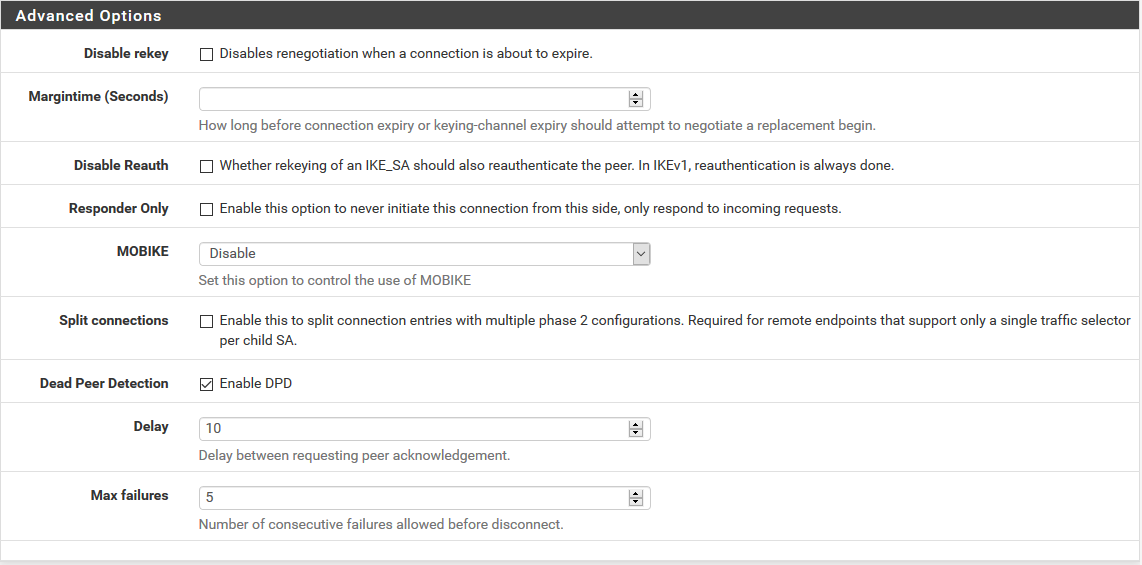
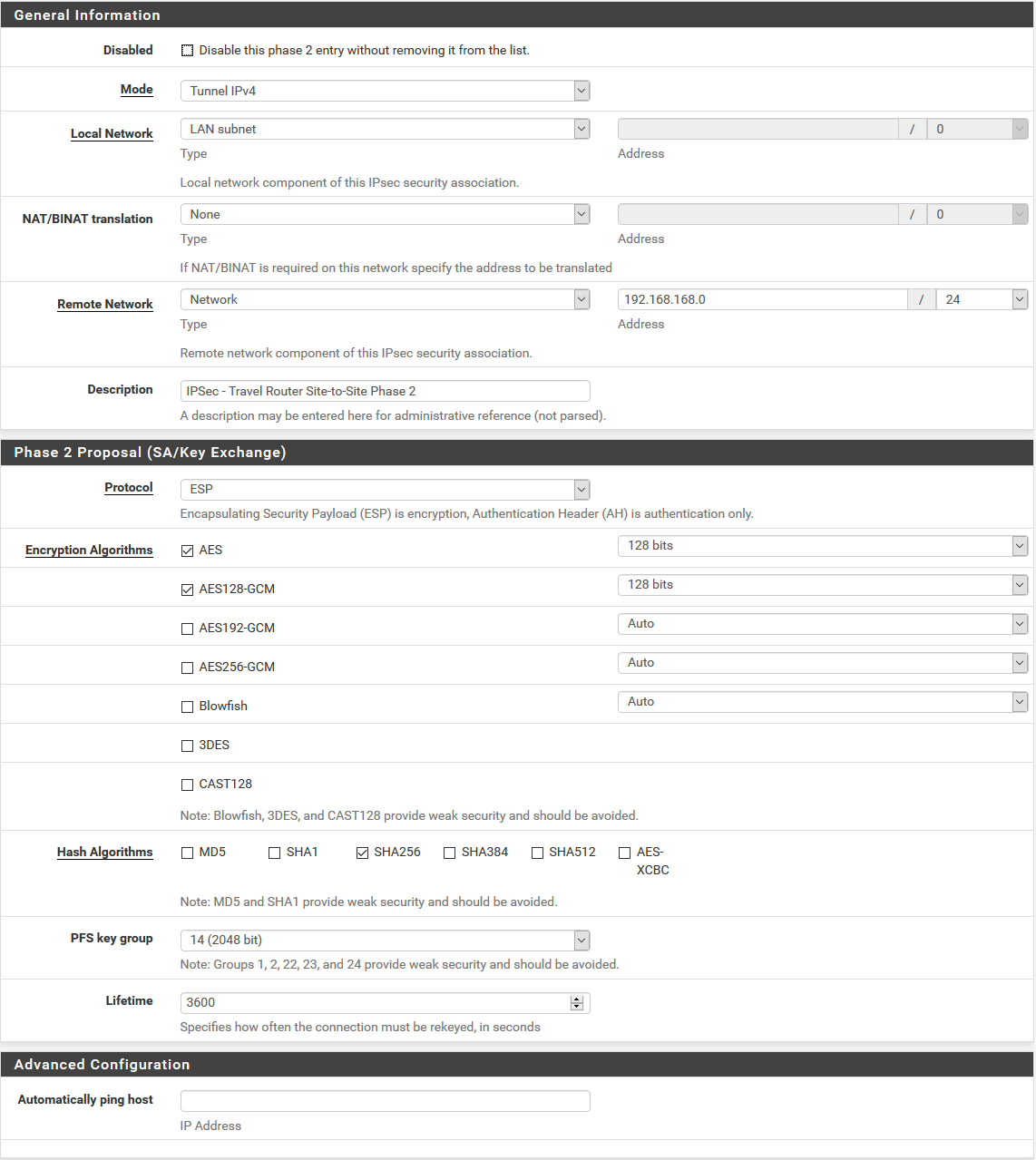
-
@highc said in IPSec VPN to OpenWrt Strongswan Travel Router:
Thanks for trying to help me. I tried to do what you said, i.e. setup a new site-to-site config in pfSense
Look at the file on the PFSense side
/var/etc/ipsec/ipsec.conf
This is an example of what settings should be on the Openwrt router . These settings should mirror the settings on the PFSense (left/right)https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-a-site-to-site-ipsec-vpn.html
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/routing-internet-traffic-through-a-site-to-site-ipsec-vpn.html
For example , my file ipsec.conf (CentOS server, site-to-site connection)
conn es_ru_pfsense_rsa keyexchange=ikev2 authby=pubkey fragmentation = yes ikelifetime=28800s ike = aes256-sha256-modp2048,aes-sha256-modp2048! esp = aes256-sha256-modp2048,aes192-sha256-modp2048,aes128-sha256-modp2048,aes128gcm16-sha256-modp2048,aes128gcm64-sha256-modp2048! left=XX.XXX.XX.XX leftsubnet=0.0.0.0/0 leftcert=strongswan_rsa.pem leftca="C=ES, O=M, CN=e.m.org" leftid=@strongswan.m.org leftfirewall=yes lefthostaccess=no right=YY.YY.YY.YYY rightid=@pfsense.m.org rightsubnet=192.168.55.32/27 auto=add