Alternate address NAT for IPSEC VTI
-
I am working with a provider to set up a routed IPSEC tunnel (VTI) on a pfsense 2.4.4 installation on AWS. We have the tunnel up and communicating and we can get traffic between the two devices. We would like to NAT outbound from our AWS VPC across the routed IPSEC tunnel using a different IP address.
In this example, we have a private subnet 10.0.100.0/24 routed through as 172.16.9.192/32 using outbound NAT mapping when traversing the ipsec tunnel to IP address 10.200.200.200 host.
In the documentation for routed IPSEC, it indicates:
Firewall rule processing can be confusing, as mentioned in Routed IPsec Firewall Rules. This is still undergoing testing, but likely means that reply-to will not function. There are also known issues with NAT, notably that NAT to the interface address works but 1:1 NAT or NAT to an alternate address does not work.I would like clarification if this configuration will definitively not work or if there has been development since the release of the documentation that has changed.
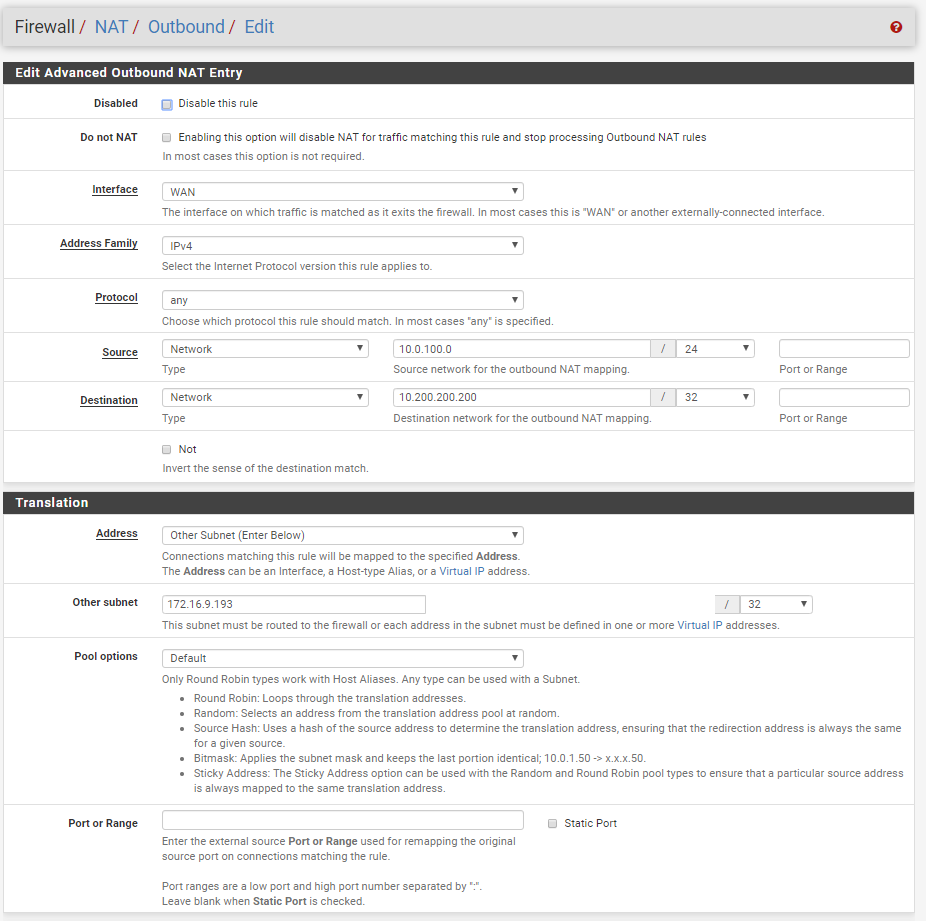
-
Hello guys,
Do you have any news about this limitation @jonathan-v brought up? This limitation is explained here https://pt.slideshare.net/NetgateUSA/routed-ipsec-on-pfsense-244-pfsense-hangout-june-2018 (page 7).
-
Hello guys,
Is that possible that someone from netgate team give us any news about this limitation?
Thank you
-
I ended up going with a traditional IPSEC tunnel and not using VTI because of this limitation and I was able to turn up the tunnel in minutes. It would be good to get an update on if this is something that will be possible at some point in the future but I was never able to get it to work.
-
@jonathan-v hello Jonathan,
I ended up with policy-based VPN too. The problem is that there some security administrators that avoid policy-based VPNs and demand for the route-based. I hope in the future Netgate can provide a solution for this limitation.
-
I'm confused about the wording of that slide. But it would seem that:
- Local Net 10.1.1.0/24 > routed througgh VTI to the VTI GW 10.2.2.1/24 and NATed to that same address should work.
In my case, packets reach the end machine and come back but they stay on the IPSec interface, they do not reach the LAN
Anyone has succeded?? Is it really a limitation/bug??
-
did you manage to make it work? perhaps a workaround?
We are currently trying to get another device to do the NATThank you
-
I don't see the limitation. Is it about NATing to an address of the tunnel network? Why would you try that?
-
@eXo Hello eXo,
If you go with policy-based VPN there is an option in phase 2 where you decide to use NAT or not and, with this configuration, everything work as it should do.
But if you decide to go with route-based(VTI option) there is not this NAT option. So if you would like to NAT your network you would go to NAT options, select the VTI interface and configure the NAT. But this just do not work and this the limitation we are discussing in this topic.
The workaround I am using is policy-based VPN(Tunnel IPV4 option).
-
@Abbys For example if your network is 192.168.10.0/24 and the other side uses this same network too. In this case you must NAT your network, for example with 192.168.20.0/24. The issue we are discussing is this topic is that when you use route-vti option(route-based VPN) the NAT do not work properlly.
-
@enialos Ok, but that is a flawed network design.
If you have to do it, is the translation network properly routed? -
Hello, i also face the problem. We have some customers who want routed vti ipsec tunnels and we need to nat over the ipsec like for a traditionnal one where we can define the NAT in the phase 2. Is netgate going to fix it ? Thanks
-
@Morlock You are right but it happens sometimes in the real world especially when you have to configure VPNs with different customers.
-
@Morlock It should do nat yes, but as far as I know it's not working. Others firewalls like vyatta and Fortigate do. Take a look at this https://pt.slideshare.net/NetgateUSA/routed-ipsec-on-pfsense-244-pfsense-hangout-june-2018 (page 7).