New User Help! Azure Pfsense, I Can't See Website
-
Hello,
Problem:
I am trying to access my website via its public IP (52.x.x.x) but it keeps trying to connect me to Pfsense GUI even though I specify port 80 for the web server and provide a port forward NAT. I keep getting redirected to port 443 on my web link: http:// 52.x.x.x. Am I doing something wrong in the NAT? Here is my setup:Azure Config:
Azure Network Space: 192.168.0.0/22
WAN NIC IP of 192.168.0.4 address space 192.168.0.0/24
Added Another IP 192.168.0.15 with External IP: 52.x.x.x <- (This is for the website)
LAN NIC of 192.168.1.4 address space 192.168.1.0/24 <- (Going to use this as next hop when routing to internet from server)
Website NIC of 192.168.2.4 address space 192.168.2.0/24
Azure NSG for Pfsense NIC and Website Server NIC:
Inbound: Allow x.x.x.x <- (My Computer) to Any destination on Any port on all NICSPfsense Config:
WAN NIC IP of 192.168.0.4/24 (Static) Gateway: 192.168.0.1
LAN NIC of 192.168.1.4/24 (Static) Gateway: 192.168.1.1
Firewall Rules: Allow x.x.x.x on Destination Port 80 to Any Destination
NAT Rule Port Forward:
(Destination Address): 52.x.x.x Redirect target IP: 192.168.2.4 Port: http (Everything else is left at default)
Virtual IP (IP Alias):
192.168.1.15
Firewall Rules are open to my Public IP x.x.x.x and allowed to access any destination on Port 80 -
I have tried everything, including following everything in the article below. I do no think this is a problem with Azure Network Security Groups because I opened all access to that port
https://docs.netgate.com/pfsense/en/latest/nat/index.html -
Bump
-
Hmm, well if you are hitting the redirect to port 443 then your traffic is not matching the port forward.
Check the state table when you try to connect to the virtual IP. What states are open to that? If the source correct?
You should probably not have a gateway on LAN. Doing so will cause pfSense to NAT the traffic outbound there to the LAN IP. If you have to have that, because it's dhcp, switch to manual outbound NAT mode and remove the NAT rules on LAN.
Steve
-
@stephenw10
Thank you for the replyStrange, it is showing the traffic I expected on the states table minus the redirect. I was expecting a destination of 192.168.0.15 then traffic gets redirected to 192.168.2.4. In the states table traffic is coming in from my public IP x.x.x.x to destination 192.168.0.15 and it is not getting redirected to 192.168.2.4. It shows to be connected on port 80 in the states table. I replaced the three octets with x for privacy on the public IP:
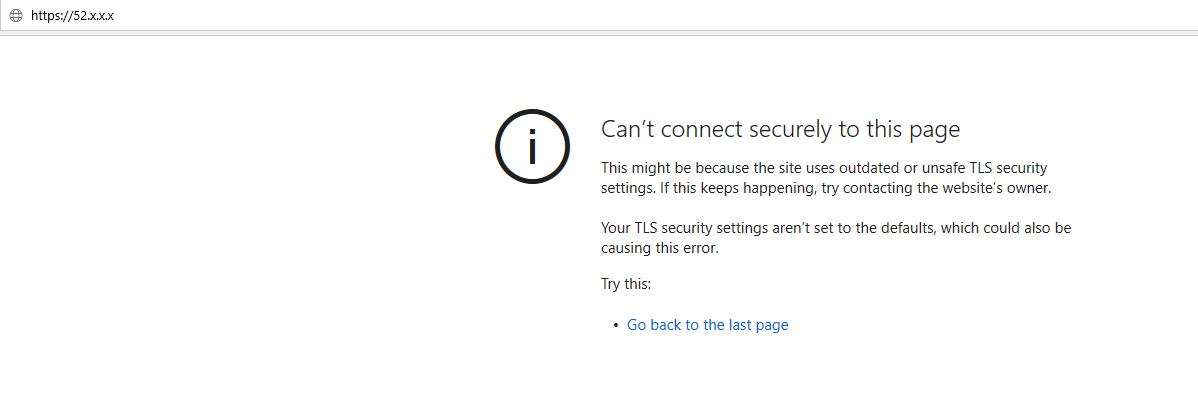
States:
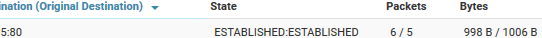
Also, I changed the LAN interface from DHCP to static, added the IP 192.168.1.4, and removed the gateway.
-
Ah, it's probably not matching because your port forward rule is set to catch traffic with destination 52.x.x.x. But by the time it reaches pfSense it has been forwarded by Azure to 192.168.0.15 so that needs to be the destination in the pfSense rule.
Steve
-
It is now redirecting correctly, 192.168.2.4 :80 (192.168.0.15) <--(Original Destination), but I am not getting any traffic through:
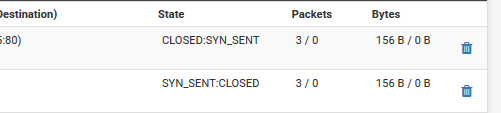
Here are my two rules to permit traffic on port 80 in Pfsense:
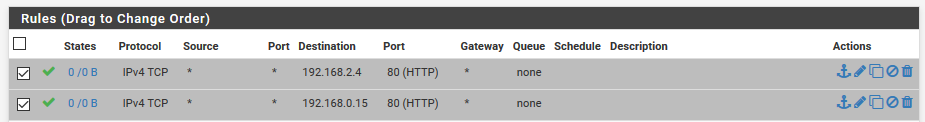
Here are my Inbound Rules in Azure, same Network Security Group, different NICs (I double checked this):
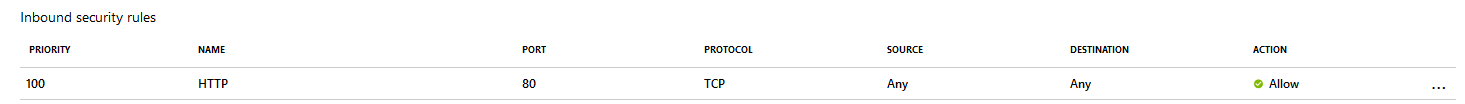
-
Local firewall on the server blocking it? There are zero bytes coming back there.
Steve
-
I added an Inbound rule to the firewall but it still didn't allow me to see the website.
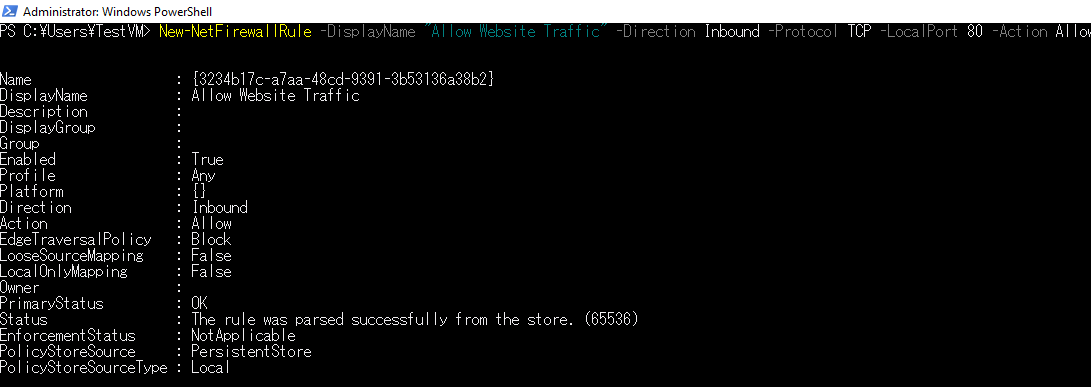
I tried removing the local firewall completely, but I was unable to see the site. I removed the Public IP from the Pfsense NIC associated to IP 192.168.0.15 and placed it directly on the Website NIC in Azure192.168.2.4 and turned the firewall back on and was able to see the site but it is not going through Pfsense anymore :(
I am removing the association and putting it public IP back on the Pfsesense NIC IP with 192.168.0.15
Here are my firewall rules on Pfsesense and Azure:
Here are my two rules to permit traffic on port 80 in Pfsense WAN interface ( I have not added any rules to the LAN interface):
Here are my Inbound Rules in Azure, same Network Security Group, for all NICs (I double checked this):

-
Is the server using the pfSense LAN as it's default gateway? Or being routed there by Azure?
Without that the server may be replying directly and you get out of state TCP blocks. (asymmetric routing)
Steve
-
@stephenw10
I don't think it is. Is the best way to do that by changing the NIC adapter settings or should I make a static route in Azure?
-
Better to route it in Azure otherwise you have to add that to all VMs there. It;s unclear if you actually have two subnets there though. It looks like you might just be using "Azure Network Space: 192.168.0.0/22". That could make the routing difficult, you might have to static route on the server.
Steve
-
@stephenw10
I made three subnets out of a possible four from the address space 192.168.1.0/22.
192.168.0.x/24
192.168.1.x/24
192.168.2.x/24
I felt that it might be a good idea so I can later add a static route if necessary :)I tried adding a route to Azure: Address Prefix: 192.168.0.0/24 Next Hop: 192.168.1.4 Associated Subnet: 192.168.2.0/24, but I had no luck
I added static route in cmd route add -p 192.168.0.0 MASK 255.255.255.0 192.168.1.4, but still nothing :(
I even tried it after killing the session states
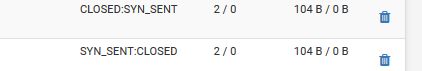
-
The route you need to add is 0.0.0.0/0 via 192.168.1.4. That will allow the server to route back to any external client via pfSense.
But you need to apply that to only devices in 192.168.1.0/24 and you might not be able to do that in Azure unless you really have separate subnets.
Steve
-
I went ahead and tried it anyway, it being add the VM to the 192.168.1.0/24 subnet. I made the VM IP 192.168.1.5 and tried creating a static route via cmd for 0.0.0.0 MASK 0.0.0.0 192.168.1.4. It didn't seem to work. I tried it in Azure as a static route but I found that Azure can only route between different subnets.
Sorry, I am so confused :( ??? Why does the LAN interface subnet need to contain the website VM? Azure will not let me route through that 192.168.1.4 IP if my VM is in the same subnet (192.168.1.5)
-
Replies from the server must go back through pfSense. Otherwise the firewall will only see part of the TCP conversation and will block out of state packets. Check the firewall log.
The only other way to do it is to NAT the traffic as it leaves LAN so the server replies back to that directly as it's in the same subnet.
Steve
-
@stephenw10
Holy Moley! That worked! You are the best, thank you!!! Switching IPs to the same subnet as the LAN then creating route 0.0.0.0/0 next hop 192.168.1.4 to subnet 192.168.1.0/24 in Azure worked like a charm!Thanks again! :)
-
No worries.
