assigning the device to a VLAN using DHCP?
-
Hi,
I need your help in getting DHCP working for the VLANs, it does not work as expected - it looks like there is a mistake in understanding somewhere.
The set-up:
Router has several VLANs, and one LAN (physical interface) without VLAN tag being assigned to it. All have own DHCP assigned with respective IP Range.
Some VLAN related DHCPs have configuration to accept only certain known list of MAC addresses.
All is configured for IPv4. IPv6 is not activated.
All devices are connected to the same network adapter via managed switch (there is a VLAN support, but not activated on the switch itself).
The WiFi VLAN related functionality works well - all mobile devices come via Access Point with VLAN ID assigned - hence DHCP gives IP addresses according to the VLAN tags, and from respective DHCP IP addresses pool.However, PCs in the network asking for the DHCP get the IP address from the LAN DHCP (no VLAN is assigned to it, or better to say VLAN 1), and not from VLAN DHCP, where their MAC addresses are registered for the fix IP assignment.
Expectation: as the MAC address is assigned to the respective VLAN DHCP - the IP should be assigned from that VLAN range. - but this does not happen for PCs connected via the cable.What do I do wrong?
How to get proper VLAN and respective IP being assigned to the PC?any suggestion?
Andrey
-
If you want the dhcpd on a vlan to be handed out to clients, then your switch needs to support vlan tags (needs to be setup).
Just because the switch supports vlans, doesn't mean it magically isolates, etc.
So if your vlan you created on pfsense is say ID 10, then on the switch go and configure which ports are in vlan 10 untagged and which ones are tagged... And which ones carry say multiple vlans to devices that understand like pfsense interface that has vlans setup on it and your AP that has vlans setup on its different SSIDs.
Here is example
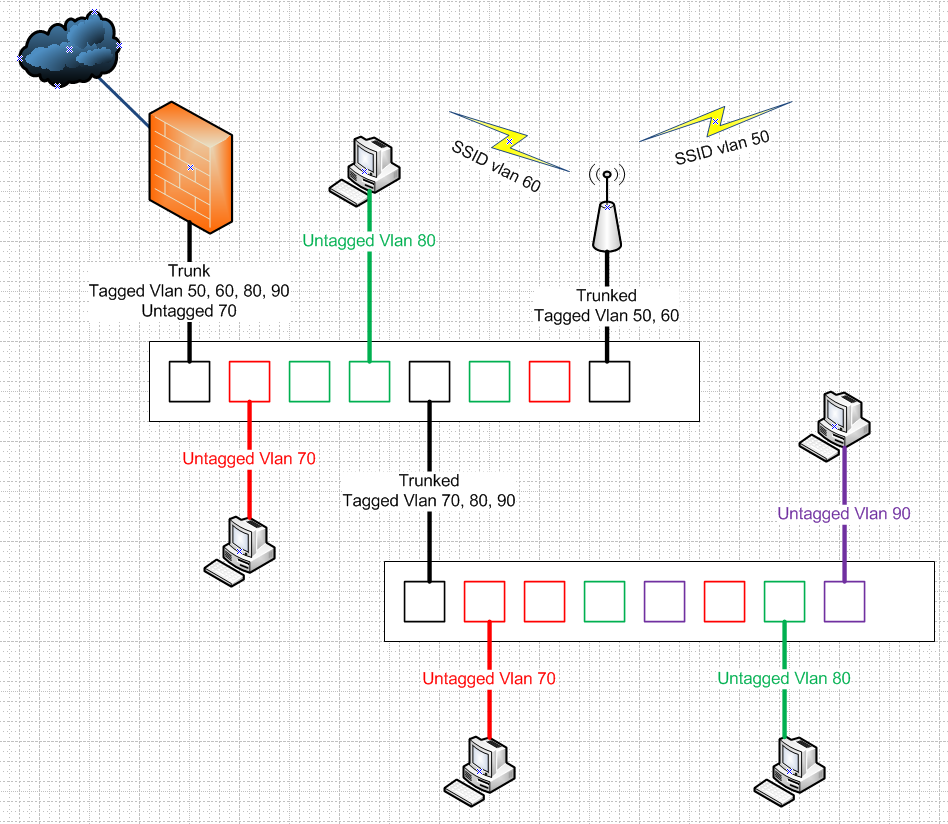
Say your lan is vlan 70 on your switch, and this is the untagged (native) lan on pfsense.. Lets say 192.168.1/24 then you create some other vlans on this nic on pfsense 50,60,80,90 etc.. 192.168.50, 192.168.60/24 etc. etc..
You can connected devices that don't understand vlans to switch ports that you setup on the switch as untagged in that vlan..
Other devices like AP you setup tagged vlans, and possible untagged native network (1 only)..
-
@johnpoz , ok, this means the DHCP would not be able to assign the IP from the VLAN range unless the request comes from the VLAN tagged port (and it needs to be configured on the switch per port). That makes sense, and partially was expected.
This would also mean that the devices, which might be connected to different Ethernet ports in the wall, would not be able to get proper IP, but the one, which is assigned to the RJ45 socket (port on switch and with respective VLAN tag)? - how to address these issue for the devices moving across different RJ45 Ethernet sockets?
Another challenge: What could be done with the access to the internal switch web functionality?
It is within the switch (or access point) and cannot be assigned to the dedicated port (VLAN) - from your explanation I understand that it will always stay in untagged vlan (VLAN01 on the LAN DHCP pool) - would this be correct undertsanding?I would like to move all IPs of these switches to dedicated VLAN, would like to avoid to hard-coded IP within switches, but giving them IPs from the dedicated VLAN and make them "not visible" for the rest of the network. this sounds like not possible or I am still missing something?
-
@AndroGen said in assigning the device to a VLAN using DHCP?:
how to address these issue for the devices moving across different RJ45 Ethernet sockets?
So now you get fancy!!! So you want device X to be able to move to any port on your switch and have that switch assign that port to vlan A..
What switch do you have? This can be done with the freerad package for sure - but your switch needs to be able to dynamic vlans..
would like to avoid to hard-coded IP within switches
vlans have nothing to do with IPs on switches? vlans are at layer 2.. IPs are at layer 3.. Sure if you want to route on your L3 capable switch then you could setup IPs in the different vlans (SVI)..
Keep in mind devices don't normally go up and moving about ports they are connected too.. So while dynamic vlans can be useful for say a corp environment where billy might use any specific cube on any given day, etc.. Such a setup is not very common in a smb setup.. Be happy to go over how you can do this with pfsense, freerad and a switch/ap that supports it... But its rare that such a setup would be done by anyone that doesn't already have the skillset to do such a thing..
-
It looks like it slowly moves above the HW capabilities.
Netgear Gigabit ProSAFE Plus switches are in the landscape. They definitely do not support dynamic VLAN assignment.This sounds like I would need to dig into the freerad (freeradius, right?) to get a bit further details what can be done there - this might be also beneficial to reduce some double maintenance on the pfsense and access points.
The environment I am in has some devices moving within the building, and due to multiple reasons they need to have different routing / internet access rules (also scheduling).
Just to check once again, that I have understood it right: DHCP will not assign the IP from VLAN range if the request is not coming from that VLAN (via switch port assignment to respective VLAN).
Entered MAC addressed into VLAN DHCP would not change anything - right?Another question: what if these MAC addresses would be explicitly denied in the LAN (VLAN 1) DHCP? - Would DHCP server seek other VLAN DHCP where these MAC addresses are allowed?
"would like to avoid to hard-coded IP within switches" - my mistake, I meant VLAN assignment to the port.
"But its rare that such a setup would be done by anyone that doesn't already have the skillset to do such a thing" - yep, but we are all learning.
I am currently in the lab set-up to get familiar with pfsense, but there is a real project behind. -
dhcpd is at the layer 2 level - so no it can not hand out an IP to something in a different layer 2 network..
What can be done is you can have a dhcpd that resides in a different L2 than the client, and then with use a dhcp relay/helper dhcp discovers that are seen on that layer 2 can be forwarded to a dhcp server that has a scope for that layer 2 and hand out the correct info for that vlan..
The environment I am in has some devices moving within the building, and due to multiple reasons they need to have different routing / internet access rules (also scheduling).
what do you mean by different routing... Lets say user billy moves machine from vlan X to vlan Y... Where X is say 192.168.1/24 and Y is 192.168.2/24
You could limit what "billy" could do by having him auth to say a captive portal or your proxy to what he could do on the internet, etc.
Would need more details of what exactly your wanting to control with billy or this machine as it moves about the campus and ends up on different vlans.
Just to check once again, that I have understood it right: DHCP will not assign the IP from VLAN range if the request is not coming from that VLAN (via switch port assignment to respective VLAN).
So if all you want to do is control the IP for client X via its mac - is you could just use 1 network, ie vlan and assign specific IP to this device based on its mac no matter where it goes.. Then you could for sure firewall rule based on this IP..
And while yes it is possible to have your switching or wifi environment assign a specific vlan based upon the mac of the device - that is not controlled by the dhcp server. Dhcp serer can hand out a specific IP, and even different info say a different router, different dns, etc.. based up on that mac address - but it can not assign it a IP outside the dhcp server scope.
-
@androgen said in assigning the device to a VLAN using DHCP?:
Netgear Gigabit ProSAFE Plus
Hi,
I know this i an old topic and you may already have changed your infra, but I have similar setup and also using Netgear Gigabit ProSAFE Plus.
My netgear has 4 tagged vlans (plus untagged native 1) on all ports and I have solved your issue by creating a virtual interface on the wired client (macbook) and fixed it with desired vlan tag. This way your dhcp queries get out tagged and pfsense leases the IP from correct dhcp pool.
The physical interface on MacBook was still pulling the IP from its native net (tag 1), but I just disabled it.
It is not a typical setup scenario, but works for anybody that's running out of ports and doesn't feel like buying another/new switch...
Cheers,