pfSense - FreeRadius. WiFi EAP (TLS). How apply checking attributes NAS-Identifier ?
-
pfSense - FreeRadius. Access Point : OpenWRT -WiFi EAP (TLS).
I try limit connected user by wifi name of AP used NAS-Identifier.
Additional RADIUS Attributes (CHECK-ITEM)
NAS-Identifier == "ap-test"
It work for users of FreeRadius that use password like PEAP.But in case if wifi users authorized by certificates only (TLS), then this limitation not work. And users can access to any wireless name of AP that use RADIUS.
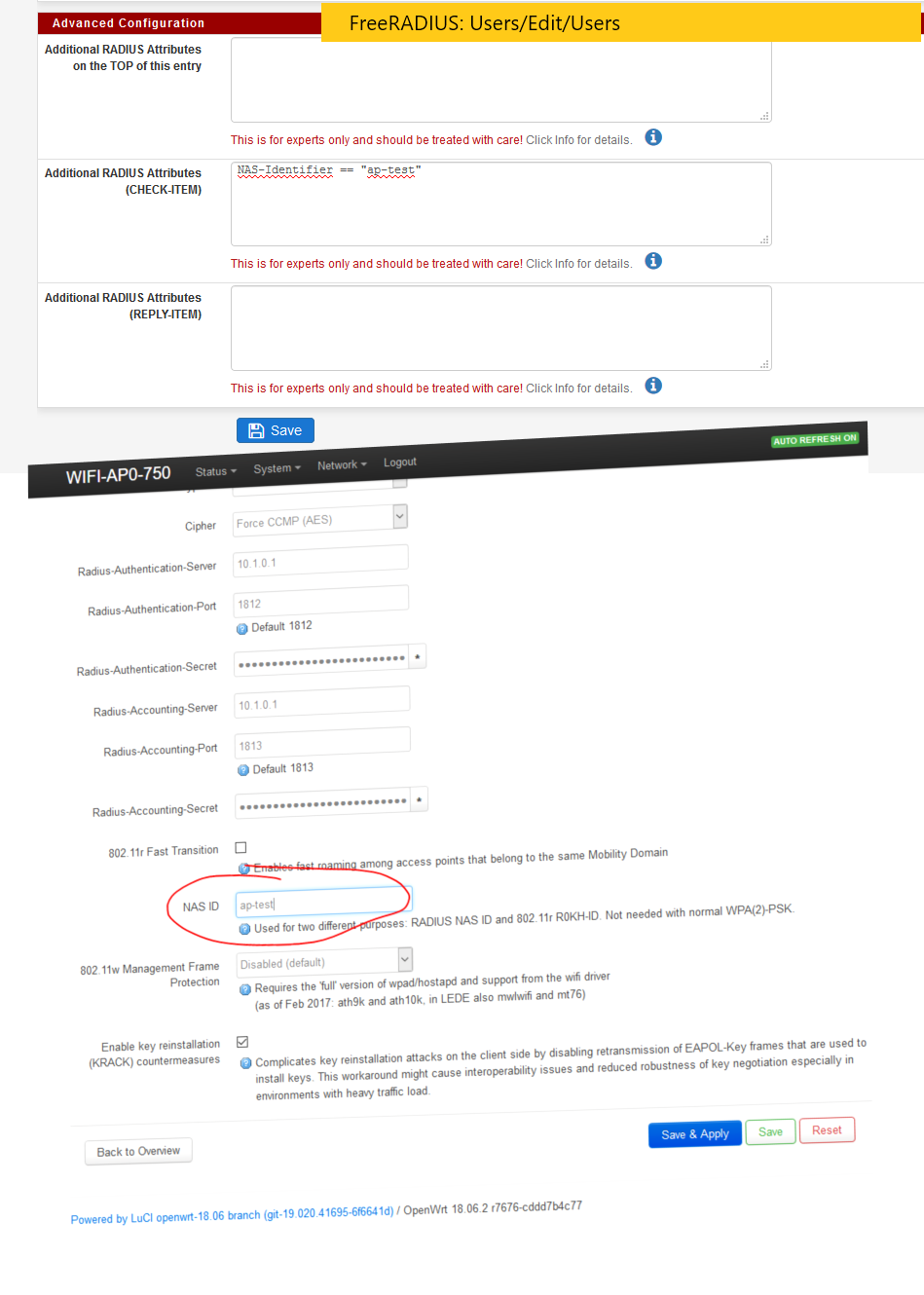
How apply checking attributes NAS-Identifier == "ap-test" for users that use EAP TLS ?
-
Why would you think user would be used if your authing with a eap-tls?
-
As I said elsewhere, try running a radsniff -x on pfSense.
FYI running WPA2EAP on a Test SSID on my Unifi kit:-
2019-05-16 07:52:51.787204 (21) Access-Request Id 11 igb0:172.16.1.11:42825 -> 172.16.0.1:1812 +9.709
User-Name = "test"
Service-Type = Framed-User
Framed-MTU = 1400
State = 0xdd2b3914d420206ea493e31f171cb95b
Called-Station-Id = "B2-2A-A8-98-9D-8C:Test"
Calling-Station-Id = "40-9C-28-A2-E0-7E"
NAS-Identifier = "802aa8969d8c"
NAS-Port-Type = Wireless-802.11
Acct-Session-Id = "DF62544CBD437E21"
Connect-Info = "CONNECT 0Mbps 802.11b"
EAP-Message = 0x020b002e19001703030023ebd0e3a3d0088a72727e2a1aa66622e57f582ef501c6f895a438b5c9702cc78a0c7def
Message-Authenticator = 0x6c905f688a8021116faf602b406cf986
WLAN-Pairwise-Cipher = 1027076
WLAN-Group-Cipher = 1027076
WLAN-AKM-Suite = 1027073
Authenticator-Field = 0x6cb6cf3d0fe08af032cd91b0f3b46115Called-Station-Id = the AP Mac+SSID
NAS-Identifier = AP MACIf I input the wrong NAS-Identifier I can't connect to the test SSID anymore.
-
And he is using eap-TLS...
-
lol didn’t spot that @johnpoz
-
@johnpoz Since username linked to certificate common name.
-
ok that just checks the cn
"Validate the Client Certificate Common Name"What exactly are you looking to accomplish..
-
@johnpoz Validate enabled
TASK check username (from certificate) and SSID name both after auth.
Some users must auth only on specific SSID WIFI.
User-Name = "user1" && NAS-Identifier == "ap-test" : OK
User-Name = "user2" && NAS-Identifier == "ap-test" : OK
User-Name = "user1" && NAS-Identifier == "ap-test-corp" : ERROR
User-Name = "user2" && NAS-Identifier == "ap-test-corp" : ERROR
User-Name = "user3" && NAS-Identifier == "ap-test-corp" : OK
User-Name = "user3" && NAS-Identifier == "ap-test" : ERROR -
So want the user that auths with his cert to only be able to use specific AP?
-
@johnpoz YES
Corporate access only for specific users like specific LDAP GROUP access.
For now any users of FreeRADUIS can auth.
If users of FreeRADUIS use not only for WIFi, for PPPoE for example.
Need split users of FreeRADUIS by tasks. -
You normally don't use eap-tls in when you need to do such a thing.