Snort Thinks Google Is Doing Port Scans
-
I wasn't able to go to google.com and received a DNS error message in Chrome. I looked in my DNS Resolver Logs (Services - DNS Resolver - DNS resolver logs) and found:
May 21 15:32:47 unbound 1888:6 notice: sendto failed: Permission denied
May 21 15:32:47 unbound 1888:6 notice: remote address is 216.239.38.10 port 53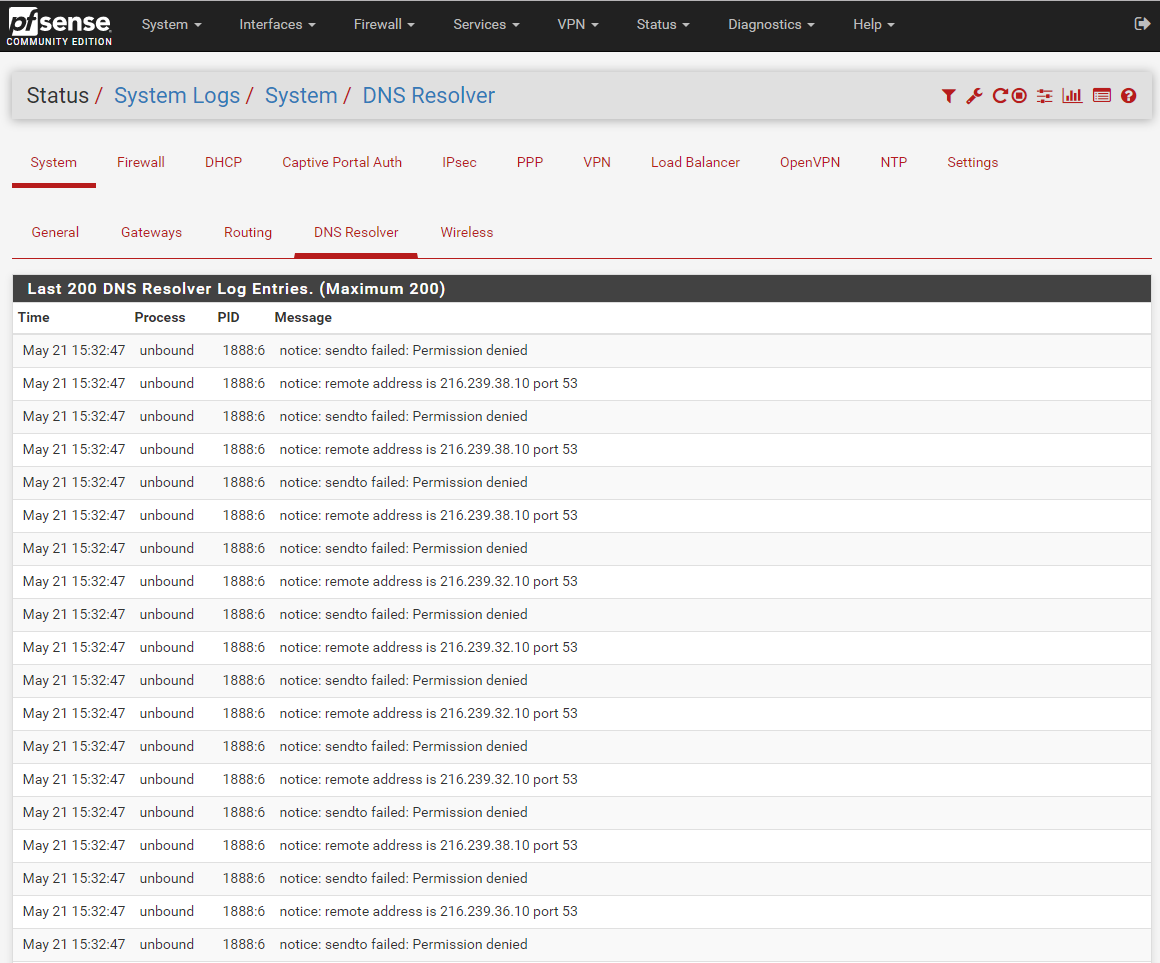
So I searched for the error and found in the forums that I should check to see if Snort was blocking that IP (Services - Snort - Alerts - Alert Log View Filter). Turns out it was and Snort thinks that it is doing this:
Date Pri Proto Class Source IP SPort Destination IP DPort SID Description
5/21/2019 15:20:32 2 Attempted Information Leak 216.239.38.10 ... 122:22:00 (portscan) UDP Filtered Decoy Portscan
5/20/2019 22:00:25 2 Attempted Information Leak 216.239.38.10 ... 122:22:00 (portscan) UDP Filtered Decoy Portscan
5/20/2019 20:47:11 2 Attempted Information Leak 216.239.38.10 ... 122:22:00 (portscan) UDP Filtered Decoy Portscan
5/20/2019 19:08:52 2 Attempted Information Leak 216.239.38.10 ... 122:22:00 (portscan) UDP Filtered Decoy Portscan
5/20/2019 11:14:03 2 Attempted Information Leak 216.239.38.10 ... 122:22:00 (portscan) UDP Filtered Decoy Portscan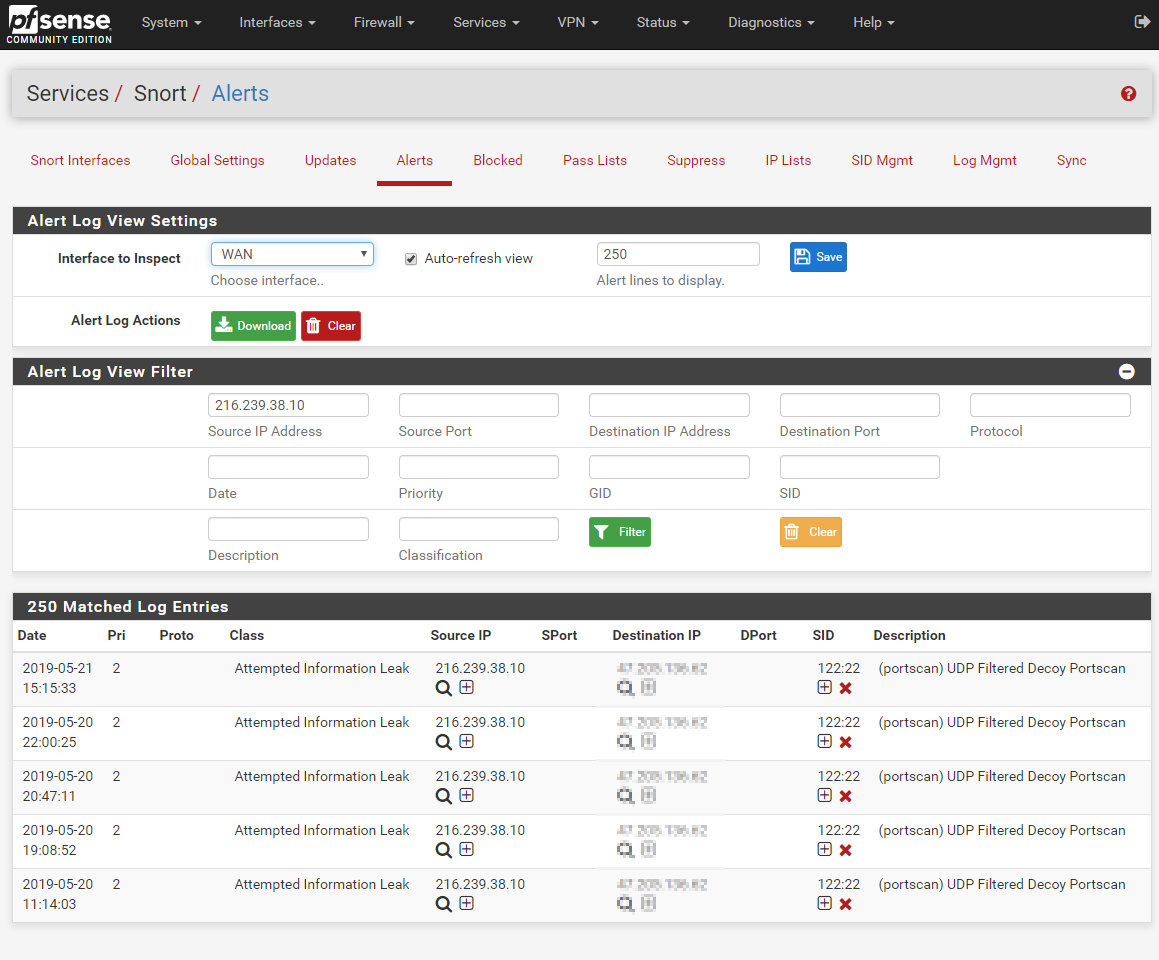
I’m not sure what to make of it. I unblocked Google’s IP for now. Any suggestions? Thanks in advance.
-
This is not all that uncommon. The Snort portscan preprocessor is very "trigger happy" ...
 .
.Go to the PREPROCESSORS tab for the impacted Snort interface and set the Sensitivity drop-down selector to Low. Save the change and restart Snort on the interface. That should help.
If the Sensitivity setting is already Low, then you will probably have to disable that particular rule. Click the red X under the SID column on the ALERTS tab to disable it.