OpenVPN client cannot see VLAN network(s)
-
Hi everyone,
I am setting up an extended network over multiple server connected via VLAN, and would like a single entry point using OpenVPN, the problem is that when i connect via OpenVPN i can only see the local LAN, but not the LAN across VLAN.. it really has me stumped as to why i cannot get it to work!A little background:
The servers are from Hetzner, have proxmox installed, and setup a vLAN.4000 using the Hetzner interface. each server has a VM with PFSense, with a direct IP to WAN and all the rest are internal virtual adapters for all the Machines.The Layout:
Here is the layout of what the current setup looks like:
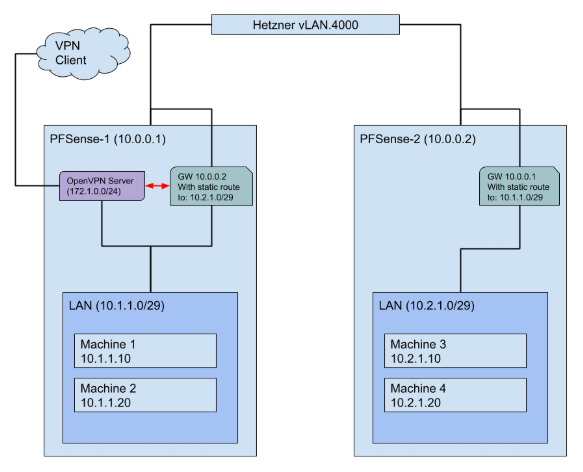
I have created a Gateway on each PFSense to the other pfsense, and added a static route to the network on the gateway.
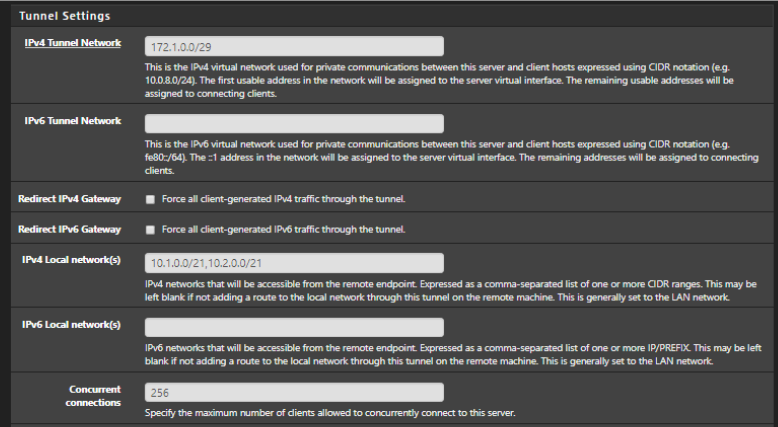
Both networks can see each other perfectly fine, and i can ping between machines 1,2 => 3,4 and vice versa.All firewall rules are set to allow any (for testing!) and i am pushing both networks via OpenVPN:
“10.1.1.0/29,10.2.1.0/29”The problem (red arrow on diagram):
Where it goes wrong, is when i connect in via the OpenVPN server, i can see Machines 1 and 2 just fine, but not reach 3 and 4! no matter what i do, i feel like i have tried everything! but might just be overlooking something simple.. i need your help! I have been googling for days, and just trying things at random at this point, but not a lot to go on with a setup like this.Configurations:
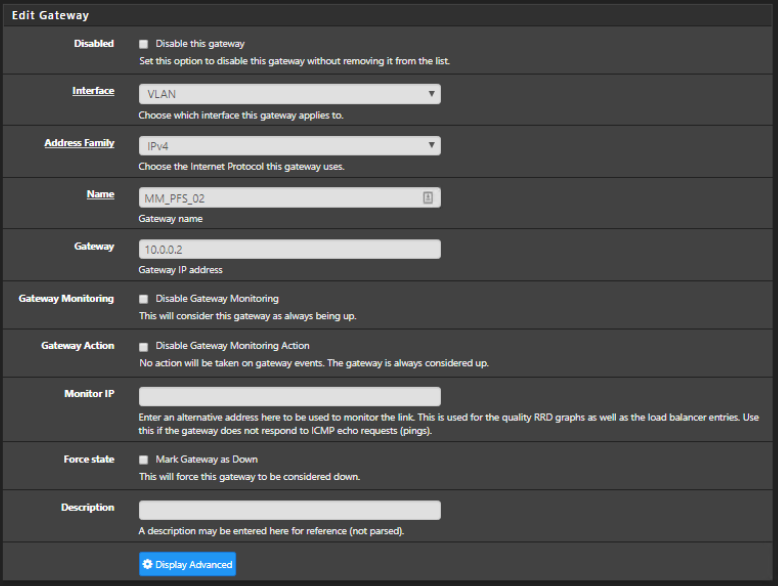
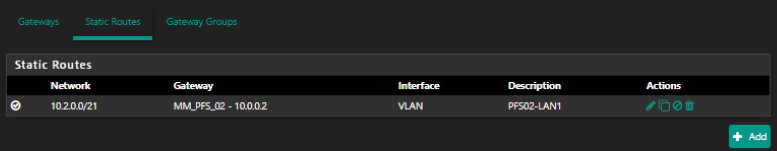
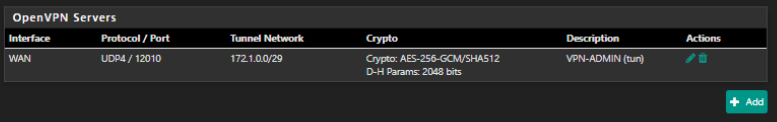
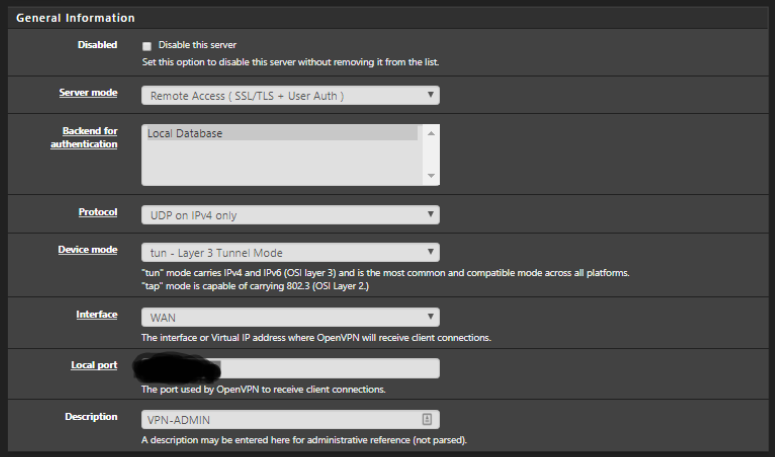
Please let me know if there is any more information i need to add.
Kind regards
Niels -
Unless you are NATing the OpenVPN client traffic leaving pfSense-1 then pfSense -2 will need a static route back to the OpenVPN tunnel subnet (172.1.0.0/29) via GW10.0.0.1. Without that it has no route back so is probably just sending replies out of it's WAN directly.
Steve
-
@stephenw10 Thankyou so much! creating a static route on pfsense-2 => 172.1.0.0/24 works!
Marking it as solved! you are a saint!
-
I try!
