[Solved ] Newbie on PFSense getting firewall errors that I don't understand
-
Hi,
First of all, I say thank you to you all for this forum and the brilliant piece of software that is pfsense. I finished setting up my build and setting my port forward rules for my applications. I'm using unraid as well, so I needed to open ports for nextcloud, let's encrypt, Open VPN and Plex. And that's working fine.
But I'm getting this logs in the firewall that I don't really understand. Maybe everything is fine and I don't need to stress about it, but it bothers me all this spam in the logs.
FYI. My internet is shared and I have a double NAT and I know I have to open ports twice. Also, I'm blocking IPv6 traffic.
I don't want devices on the ISP network 10.0.0.0/24 having access to my network 172.16.1.1/24
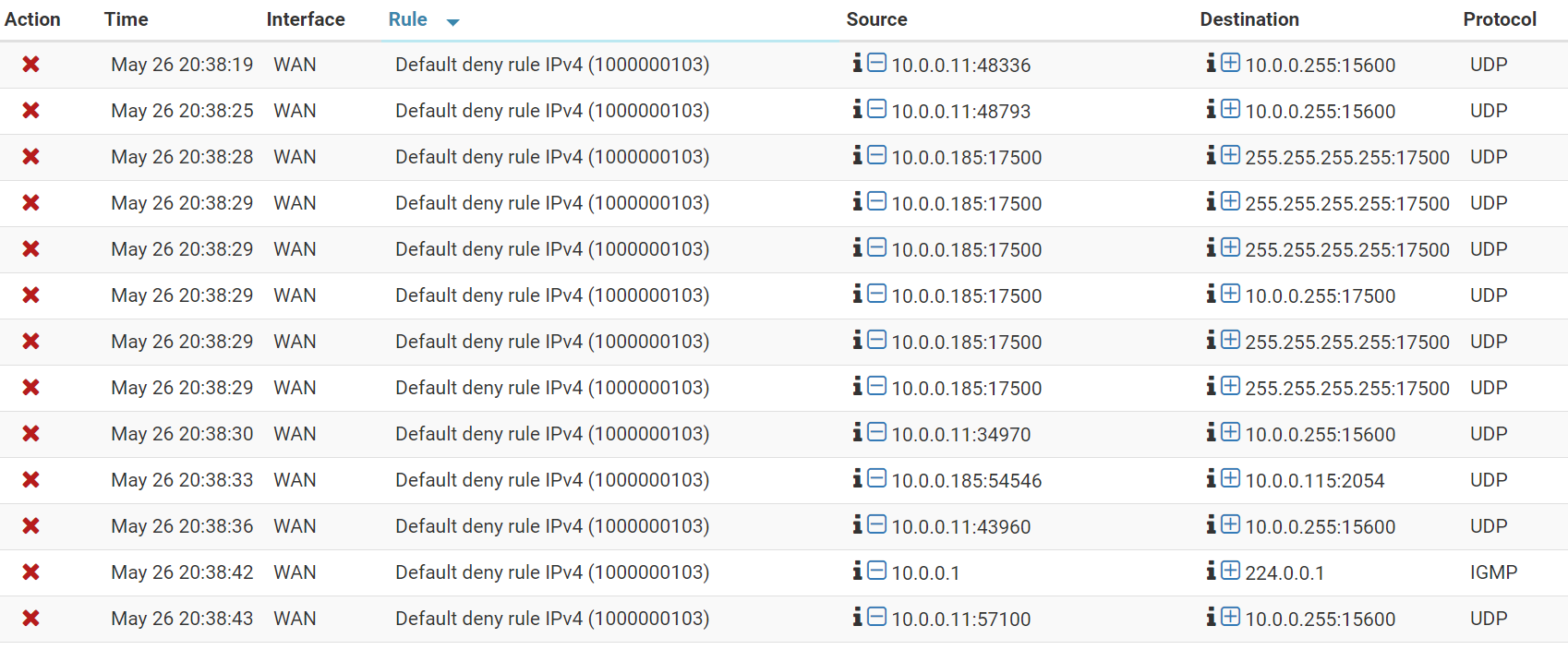
This is the picture of the logs.
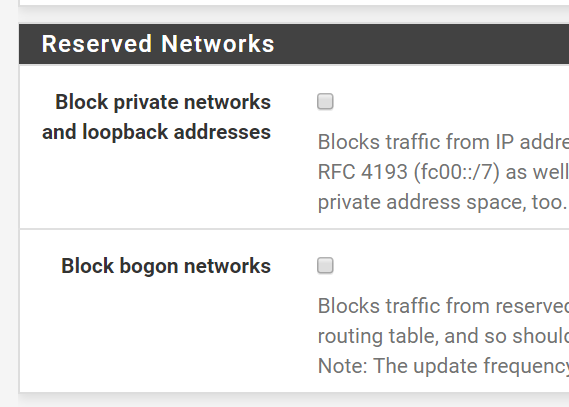
Since I'm in a double NAT situation I have disabled the following. Should I keep it like this?
-
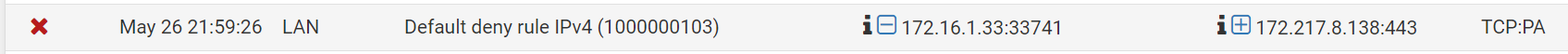
I'm also getting this log blocking an address, which is clearly google, but I already have a rule permitting that.
please see my LAN rule here
-
Hi,
Your first image - first post : You enabled logging of the default (blocking, hidden) firewall rule, the one on the WAN interface.
You see UDP broadcasts from the 10.0.0.0 WAN segment.Next image : is ok.
Second post : the TCP:PA : probably a packet out of sync - no state found -> it got handled by the default block rule one LAN, and again, you log hits on the default rules so your served.
-
I really thought I was going crazy. How can I turn off those logs if I want in the future?
-
@gacpac said in Newbie on PFSense getting firewall errors that I don't understand:
I really thought I was going crazy. How can I turn off those logs if I want in the future?
Check out the log settings :
Status => System Logs => Settings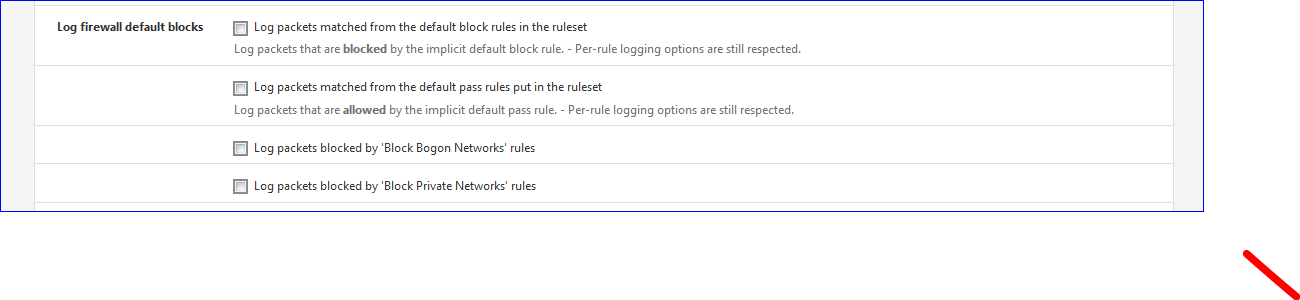
-
You usually want to see traffic blocked by the default block rule. It shows that by default and disabling it means you won't see legit traffic blocked which makes trouble shooting much harder.
You don't need to disable 'block private networks' unless you have port forwards on WAN that you need to access from the WAN subnet itself.
What I would do here is re-enable block-private-networks on the WAN interface. Then disable 'Log packets blocked by block private networks. That should remove that log spam from 10.0.0.X but leave other blocked traffic showing.Steve
-
Thanks for all your help. Now I have a better understanding of how the log works.
I will have to keep the 'block private networks' disabled because I have a double NAT situation and I have to open the ports twice so.I've been reading and a possible solution is that I can turn my router into a DMZ so I only open ports in my ISP router. But I think that leaves me vulnerable anyway, and I rather keep opening ports twice.
-
Think you got it backwards ;)
I can turn my router into a DMZ so I only open ports in my ISP router.
If you can enable bridge mode, which puts a public on pfsense wan you would only have to forward ports on pfsense. If you turn on what many soho routers call dmz mode or dmz host.. You put in the IP of what pfsense WAN rfc1918 address is and all ports are forwarded by your isp router to pfsense...
Then you would only have to forward ports on pfsense for those that you want actually forwarded to devices behind pfsense.
-
Oh, I see.
But I still have a small problem. Some devices are connected directly to the network of the ISP router and they don't work if I connect them to the Pfsense. So I really wouldn't know how to go from there.
-
And what devices are those? Pfsense doesn't care what the device is.. Its just like any other router - EVERYTHING will work behind it.
If your having issues with something you need to let us know what that something is if you want help figuring out what is the problem.
Is it like STB or something for tv/phone that your ISP router does something special for?
-
That's precisely what it is; it feeds a couple of STB and a phone. If not, I would have bought my modem and tossed that one through the garbage. I also called their support and there's not much I can do. It doesn't bother me either.
Now what I'll like to do is something with the host overrides in DNS. I currently have a nextcloud and couple different apps using a reverse proxy with a DDNS, so I have to do xxx1.duckdns.org, xxx2.duckdns.org, xxx3.duckdns.org
I think is possible to use just one xxx.duckdns.org and internally direct them using the host overrides like nextcloud.xxx.duckdns.org, plex.xxx.duckdns.org, webapp1.xxx.duckdns.org
All this apps are using the same IP with different ports, as they reside in the same server (I know I'm putting my eggs in one basket).
I can create that as a separate post if you want, or maybe direct me to a F.A.Q and I can possibly figure it out on my own.
-
Setting the DMZ mode on the ISP router should not affect devices connected directly to it. They should continue to function as previously. It only affects incoming connections which will all be fowarded to pfSense.
Steve
-
I don't think my ISP router allows me to do that. I see the DMZ option, to assign an IP from the lease, where I can only pick. Like my Pfsense box for example and all the ports will be open on my box. I don't see an option to turn off DHCP or get this on bridge mode. But again like I said. Right now that doesn't bother me, because this is a home setup really.
What I will like to figure out is how to do it what I mentioned before with the DDNS
-
If you need to have devices connected directly to it then you can't use a full bridge mode anyway. The DMZ mode should work fine for you in that case.
Steve
-
@stephenw10 Thanks Steve!
I've been reading more and more and I really want to grow PFSense. Maybe use it as a backup for the Fortinet Firewalls in the corporate environment I work on.