DHCP on LAN out packets lost when LAN bridged to another interface
-
Hi,
I'm currently on 2.4.4-RELEASE-p2 running in a home environment.
I currently have the following setup:
WAN
LAN - 192.168.20.1 - DHCP 192.168.20.0/24
GUESTS_WIFI - 192.168.23.1 - DHCP 192.168.23.0/24At the moment, all wifi clients that are no guests are entering on LAN but I want to have them separated to be able to apply filtering. What I did to achieve this is a new interface called LAN_WIFI that I want to bridge to LAN
I imagined that the following should work:
WAN
LAN - 192.168.20.1 - DHCP 192.168.20.0/24
GUESTS_WIFI - 192.168.23.1 - DHCP 192.168.23.0/24
LAN_WIFI - no ip, no DHCP, bridged to LANWhat I do not understand is that, as soon as I create the bridge, DHCP responses on LAN are not being passed to the clients correctly anymore. I can see the DHCPREQUEST & DHCPOFFER log entries, they are all correct, but apparently the DHCPOFFER packets hardly reach the clients. It needs 6-10 retries until a client gets an IP. After clients got an IP, connectivity seems to work fine though.
I've read about the setup should be DHCP on bridge, not on LAN anymore, but nevertheless, why is it working sporadically? If there was a missing FW rule, all packets would be lost, but that is not the case here.
Given the fact that the purpose of a bridge is that the broadcast domain is identical, I imagined that having a DHCP on LAN should be able to, obviously, still hand out IPs on LAN but also on LAN_WIFI.
I also tried adding a FW rule on LAN to allow any, same for LAN_WIFI, but these rules obviously do not have any effect.
The reason why I want a bridge instead of a separate net is that I have devices that rely on broadcasts to servers on LAN.
Any hint is highly appreciated.
Best,
Lyve
-
@Lyve said in DHCP on LAN out packets lost when LAN bridged to another interface:
The reason why I want a bridge instead of a separate net is that I have devices that rely on broadcasts to servers on LAN.
Just connect your AP into a switch lan port.. Why are you wanting to waste an interface on your router just for a switch port?
-
I don't have a switch that is able to filter packets, which I want. My pfsense is virtualized anyway so I'm not "wasting" a port, I only need to change the VLAN ID of my AP.
-
Well look to your VM setup then to why you having this issue... Which you make no mention of in your OP btw.
If your setup is VM.. Where exactly is your AP connected too.. You sure do not need to create a bridge on pfsense.. You already have a LAN..
What exactly are you looking to filter on the same L2, pfsense can not do that either.. You can filter on 2 sides of a bridge yes.. But how exactly is this all connected if pfsense is a VM?
If your AP can do vlans... Then just you would do those vlans your VM setup.. Love to help you but your going to have to lay out how you have this all connected, and exactly what your wanting to do.. If your AP can do vlans - then you would have SSID for your lan network, and SSID for your guest network.. And then sure guest would go to guest interface on pfsense and your normal SSID that is for your lan would just go to the pfsense lan interface - there is no need of a bridge in pfsense. What VM software are you using, esxi, hyper-v, kvm? virtualbox? etc. etc.
If you have a switch that is connected to your VM host and your expecting to do vlans over it - then you really want a switch that understands vlans.. Be it the switch doesn't strip the tags or not - you have no actual isolation of vlan traffic over this switch if it doesn't support vlans..
Please draw up how you have this all connected and we can figure out how to do what you want to do.
-
I want to have wifi devices on a separate NIC to have the ability to block certain wifi devices from accessing other devices on LAN, for example my kids mobile phones shall not be allowed to access my NAS, but they should still be allowed to use the Chromecast that is connected to the TV. Amazon Echos should be able to find IoT devices using broadcasts, but should not be able to access the NAS, too.
As long as I do not create the bridge, DHCP answers on LAN are fine this is why I'm asking.
VM machine has two physical NICs, one is WAN, one is LAN. System is a ESXi 6.5 hypervisor.
Physical WAN NIC goes to the cable modem
Physical LAN goes to a physical switch, the APs are connected to this switch.
multiple interfaces are created in VMware:
WAN => WAN NIC
LAN, GUESTS (vlan 3), LAN_WIFI (vlan 5) => LAN NIC - the vSwitch on ESXI and all port groups already run in Promiscuous Mode for now to eliminate an issue here.All virtual interfaces are created in vmware and are added to pfsense guest system, so no vlan awareness in pfsense needed, just "normal" interfaces
LAN (wifi SSID xxx, no vlan), GUEST (wifi SSID yyy, vlan 3), WAN, everything is working fine so far.
LAN_WIFI is SSID zzz on vlan 5 but I even did not get that far to try it because just creating the bridge breaks DHCP on the regular LAN already.
-
Not sure how you think you going to be able to filter what traffic via bridge in such a setup.. You only have 1 physical L2 interface on your VM... So how is pfsense to to filter on that? You can create 2 interfaces on pfsense - but they are both connected to the same physical L2.. So you have what amounts to a loop..
You can filter across a bridge when you have 2 actual physical different L2s And you bridge across them over pfsense..
So for example
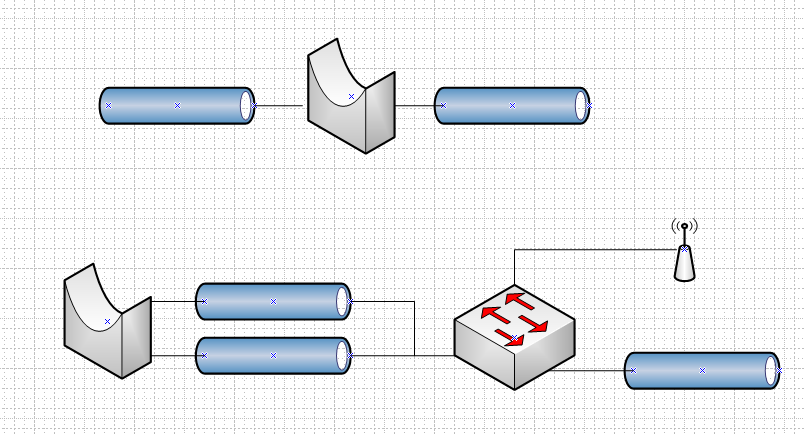
In the top layout you have 2 physical L2 connected via a bridge.. But if understanding your setup correctly have the bottom layout.. How is that going to filter anything.. You have created a loop sounds like to me..
To do what your doing your going to want a switch that can do your filtering for you - you can not do that on pfsense on a VM..
-
The lower part comes close to what I have, but the difference is that on the physical LAN NIC, the nets would be separated by different VLANs.
This already works fine for network GUESTS, which is vlan 3 and network LAN, no vlan.
-
Yes you can do vlans on your VM, and send them to different vnics on pfsense via port groups on esxi.. And let it work out the tags.. But its not going to work with a bridge.. Both sides of the bridge will see all broadcast traffic..
Sounds like to me the simple solution would be just create a vlan/ssid that your chrome and alexa and other iot devices are on that is different from your lan where your nas is, etc.
what exactly are you trying to control with your alexa.. My alexa is on 1 vlan, and my TV and rokus, etc.are on different vlan and I can control them with alexa.. You might be able to do something with chrome and igmp proxy.. But your not going to be able to create a bridge in pfsense with 2 connections into the same L2, and then filter traffic between devices on that same L2 since they are not actually physically different.. If something is connected to your switch/AP and wants to talk to something that is connected to that same L2, why would it be filtered through pfsense?
Keep in mind while you can isolate the different vlans via tag on esxi.. If the devices are all connected to your dumb switch then your not actually isolated.. A dumb switch = 1 L2.. No matter if tagged or not.. All your accomplishing with breaking out the vlans on esxi is running multiple L3 on the same L2.. To actually isolate vlans you need as switch that can do that, or multiple dumb switches and physical interfaces, etc.
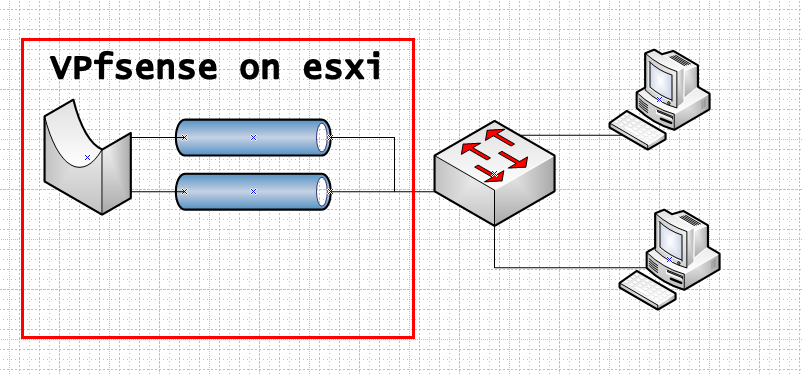
If computer 1 wants to talk to 2 - pfsense has zero to do with that conversation.. Only when the bridge is actually between physically the the 2 different L2 you bridge together could you filter traffic.
-
Understood. I know that all of this is not a pro environment. What I did not get though is, how this explains the behaviour I'm experiencing

Let's imagine that I had a physical pfsense with three ports, I want to bridge port A and B. DHCP is running fine on port A and stops working as soon as I bridge A <=> B.
Failure is outgoing DHCPOFFER packet loss to clients connected to port A although the dhcpd log claims that it's sending these packets.
If I delete the bridge, everything is back to normal instantly.After googling, I might try a different approach this evening: Having LAN_WIFI on a separate subnet & trying out the Avahi pfsense package to forward broadcasts.
-
Dude you created a LOOP.. .that is going to cause all kinds of ODD Shit!!
You you can not run it this way be it home, or a lab or an enterprise. It will not work!!
I already suggest you could try using the igmp proxy.. But if all you need is mdns discovery, then yeah avahi might work.. Can tell you that getting chrome to work across different L2 is going to be a PITA..
Use something else would be my suggestion. Not sure exactly in what context your using it in..
If you want pfsense to filter between the bridge.. Then your going to need another physical interface on your vm host, so you physically separate the L2 you want to filter/bridge between 2 physical networks via different switches. Or a smart switch that you could isolate the L2 via different vlan tags.. You could then bridge across these 2 tags vlans and make them the same on pfsense doesn't have to know about the tags, etc.
So with a smart switch you could do something like this..
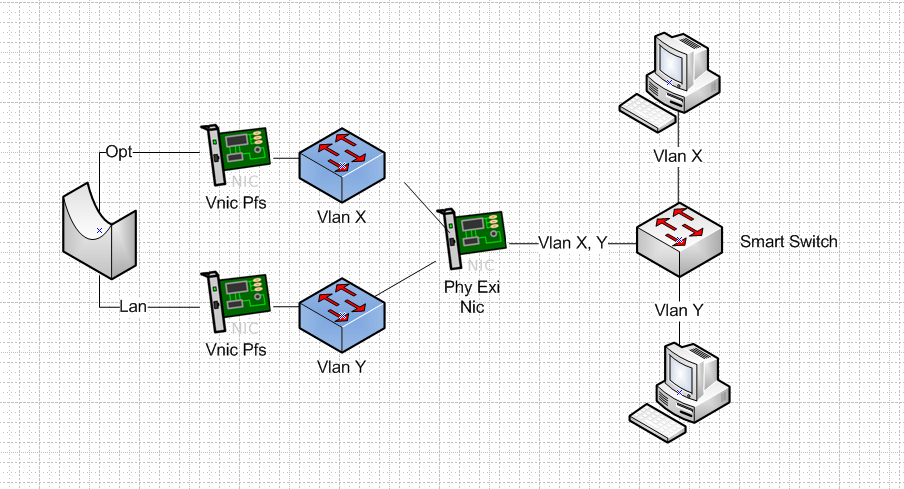
You create 2 different vlans on your switch.. You then isolate these different vlans on your esxi into port group for each vlan.. Then you connect these port groups to 2 different vnics on pfsense that not using tags.. esxi will strip the tags let the port groups handle the tags..
You bridge these interfaces on pfsense.. So you have 2 isolated L2, that you have bridged into a single L2 via pfsense.. So computer on Y not talk to X unless it goes through the pfsense bridge.. Now you can filter and say no Y can not talk nas on vlan X via L3 filtering..
But if your switch is not smart and can not isolate the vlans.. Then this can not work!!!