Migrated from igb to bge Suricata Won't Run (solved)
-
So, I moved from an HP Pavillion a6242n to a Mac Mini Server 2011 and when I restore from backup, Suricata installed but will not run. Any ideas what to look for? All prior setting had been exported so, it seems that it could be the network interface. I was surprised that pfSense selected the thunderbolt ethernet adapter for bge0.
-
The bge network driver is not listed as supporting netmap operation. Netmap compatibility is required for inline IPS mode. That has been mentioned here over and over and over. You either need to install a netmap compatible network card or else switch to Legacy Mode blocking. That mode does not use netmap.
These are the NIC driver families listed by FreeBSD as supporting netmap operation: em, igb, ixgb, ixl, lem, re or cxgbe.
-
Here are some data:
Shell Output - ifconfig bge0
bge0: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=c0098<VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,VLAN_HWTSO,LINKSTATE>
ether a8:60:b6:23:11:34
hwaddr a8:60:b6:23:11:34
inet6 fe80::aa60:b6ff:fe23:1134%bge0 prefixlen 64 scopeid 0x1
inet 68.226.181.34 netmask 0xfffffe00 broadcast 68.226.181.255
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
media: Ethernet autoselect (1000baseT <full-duplex,master>)
status: activeShell Output - cat /var/log/system.log | grep sig
Jun 15 23:17:29 pfSense syslogd: exiting on signal 15
Jun 15 23:25:02 pfSense syslogd: exiting on signal 15
Jun 15 23:27:37 pfSense syslogd: exiting on signal 15
Jun 15 23:48:10 pfSense syslogd: Logging subprocess 84491 (exec /usr/local/sbin/sshlockout_pf 15) exited due to signal 15.
Jun 15 23:48:10 pfSense syslogd: exiting on signal 15
Jun 15 23:50:10 pfSense syslogd: exiting on signal 15
Jun 15 23:53:24 pfSense php-fpm[1248]: /interfaces_assign.php: Shutting down Router Advertisment daemon cleanly
Jun 15 23:53:24 pfSense php-fpm[1248]: /interfaces_assign.php: Gateway, none 'available' for inet6, use the first one configured. ''
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/sbin/ifconfig 'igb1' -staticarp ' returned exit code '1', the output was 'ifconfig: interface igb1 does not exist'
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/usr/sbin/arp -d -i 'igb1' -a > /dev/null 2>&1 ' returned exit code '1', the output was ''
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/usr/local/sbin/dhcpd -user dhcpd -group _dhcp -chroot /var/dhcpd -cf /etc/dhcpd.conf -pf /var/run/dhcpd.pid igb1' returned exit code '1', the output was 'Internet Systems Consortium DHCP Server 4.3.6-P1 Copyright 2004-2018 Internet Systems Consortium. All rights reserved. For info, please visit https://www.isc.org/software/dhcp/ Config file: /etc/dhcpd.conf Database file: /var/db/dhcpd.leases PID file: /var/run/dhcpd.pid Wrote 1 leases to leases file. No subnet declaration for igb1 (no IPv4 addresses). ** Ignoring requests on igb1. If this is not what you want, please write a subnet declaration in your dhcpd.conf file for the network segment to which interface igb1 is attached. ** Not configured to listen on any interfaces! If you think you have received this message due to a bug rather than a configuration issue please read the section on submitting bugs on either our web page at www.isc.org or in the README file before su
Jun 15 23:53:33 pfSense php-fpm[1248]: /interfaces_assign.php: Gateway, none 'available' for inet6, use the first one configured. ''
Jun 15 23:53:39 pfSense php-fpm[1248]: /interfaces_assign.php: Creating rrd update script
Jun 15 23:53:40 pfSense php-fpm[56381]: /interfaces_assign.php: Stopping all packages.
Jun 15 23:53:42 pfSense syslogd: exiting on signal 15
Jun 15 18:55:07 nollipfSense syslogd: exiting on signal 15
Jun 15 18:55:08 nollipfSense syslogd: Logging subprocess 17613 (exec /usr/local/sbin/sshguard) exited due to signal 15.Execute Shell Command
Shell Output - cat /var/log/system.log | grep sig
Jun 15 23:17:29 pfSense syslogd: exiting on signal 15
Jun 15 23:25:02 pfSense syslogd: exiting on signal 15
Jun 15 23:27:37 pfSense syslogd: exiting on signal 15
Jun 15 23:48:10 pfSense syslogd: Logging subprocess 84491 (exec /usr/local/sbin/sshlockout_pf 15) exited due to signal 15.
Jun 15 23:48:10 pfSense syslogd: exiting on signal 15
Jun 15 23:50:10 pfSense syslogd: exiting on signal 15
Jun 15 23:53:24 pfSense php-fpm[1248]: /interfaces_assign.php: Shutting down Router Advertisment daemon cleanly
Jun 15 23:53:24 pfSense php-fpm[1248]: /interfaces_assign.php: Gateway, none 'available' for inet6, use the first one configured. ''
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/sbin/ifconfig 'igb1' -staticarp ' returned exit code '1', the output was 'ifconfig: interface igb1 does not exist'
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/usr/sbin/arp -d -i 'igb1' -a > /dev/null 2>&1 ' returned exit code '1', the output was ''
Jun 15 23:53:27 pfSense php-fpm[1248]: /interfaces_assign.php: The command '/usr/local/sbin/dhcpd -user dhcpd -group _dhcp -chroot /var/dhcpd -cf /etc/dhcpd.conf -pf /var/run/dhcpd.pid igb1' returned exit code '1', the output was 'Internet Systems Consortium DHCP Server 4.3.6-P1 Copyright 2004-2018 Internet Systems Consortium. All rights reserved. For info, please visit https://www.isc.org/software/dhcp/ Config file: /etc/dhcpd.conf Database file: /var/db/dhcpd.leases PID file: /var/run/dhcpd.pid Wrote 1 leases to leases file. No subnet declaration for igb1 (no IPv4 addresses). ** Ignoring requests on igb1. If this is not what you want, please write a subnet declaration in your dhcpd.conf file for the network segment to which interface igb1 is attached. ** Not configured to listen on any interfaces! If you think you have received this message due to a bug rather than a configuration issue please read the section on submitting bugs on either our web page at www.isc.org or in the README file before su
Jun 15 23:53:33 pfSense php-fpm[1248]: /interfaces_assign.php: Gateway, none 'available' for inet6, use the first one configured. ''
Jun 15 23:53:39 pfSense php-fpm[1248]: /interfaces_assign.php: Creating rrd update script
Jun 15 23:53:40 pfSense php-fpm[56381]: /interfaces_assign.php: Stopping all packages.
Jun 15 23:53:42 pfSense syslogd: exiting on signal 15
Jun 15 18:55:07 nollipfSense syslogd: exiting on signal 15
Jun 15 18:55:08 nollipfSense syslogd: Logging subprocess 17613 (exec /usr/local/sbin/sshguard) exited due to signal 15.Execute Shell Command
Shell Output - sysctl -a | grep msi
hw.ixl.enable_msix: 1
hw.sdhci.enable_msi: 1
hw.puc.msi_disable: 0
hw.pci.honor_msi_blacklist: 1
hw.pci.msix_rewrite_table: 0
hw.pci.enable_msix: 1
hw.pci.enable_msi: 1
hw.mfi.msi: 1
hw.malo.pci.msi_disable: 0
hw.ix.enable_msix: 1
hw.igb.enable_msix: 1
hw.em.enable_msix: 1
hw.cxgb.msi_allowed: 2
hw.bce.msi_enable: 1
hw.aac.enable_msi: 1
machdep.disable_msix_migration: 0
dev.bge.1.msi: 1
dev.bge.0.msi: 1Shell Output - sysctl -a | grep netmap
netmap: loaded module
043.352356 [ 760] generic_netmap_dtor Restored native NA 0
043.354388 [ 760] generic_netmap_dtor Restored native NA 0
043.536234 [ 760] generic_netmap_dtor Restored native NA 0
device netmap
dev.netmap.ixl_rx_miss_bufs: 0
dev.netmap.ixl_rx_miss: 0
dev.netmap.iflib_rx_miss_bufs: 0
dev.netmap.iflib_rx_miss: 0
dev.netmap.iflib_crcstrip: 1
dev.netmap.bridge_batch: 1024
dev.netmap.default_pipes: 0
dev.netmap.priv_buf_num: 4098
dev.netmap.priv_buf_size: 2048
dev.netmap.buf_curr_num: 163840
dev.netmap.buf_num: 163840
dev.netmap.buf_curr_size: 2048
dev.netmap.buf_size: 2048
dev.netmap.priv_ring_num: 4
dev.netmap.priv_ring_size: 20480
dev.netmap.ring_curr_num: 200
dev.netmap.ring_num: 200
dev.netmap.ring_curr_size: 36864
dev.netmap.ring_size: 36864
dev.netmap.priv_if_num: 1
dev.netmap.priv_if_size: 1024
dev.netmap.if_curr_num: 100
dev.netmap.if_num: 100
dev.netmap.if_curr_size: 1024
dev.netmap.if_size: 1024
dev.netmap.generic_rings: 1
dev.netmap.generic_ringsize: 1024
dev.netmap.generic_mit: 100000
dev.netmap.admode: 0
dev.netmap.fwd: 0
dev.netmap.flags: 0
dev.netmap.adaptive_io: 0
dev.netmap.txsync_retry: 2
dev.netmap.no_pendintr: 1
dev.netmap.mitigate: 1
dev.netmap.no_timestamp: 0
dev.netmap.verbose: 0
dev.netmap.ix_rx_miss_bufs: 0
dev.netmap.ix_rx_miss: 0
dev.netmap.ix_crcstrip: 0Shell Output - sysctl -a | grep bge0
<5>bge0: link state changed to DOWN
<5>bge0: link state changed to UP
bge0: <Thunderbolt Ethernet, ASIC rev. 0x57766000> mem 0xa4f00000-0xa4f0ffff,0xa4f10000-0xa4f1ffff at device 0.0 on pci7
bge0: CHIP ID 0x57766000; ASIC REV 0x57766; CHIP REV 0x577660; PCI-E
miibus0: <MII bus> on bge0
bge0: Using defaults for TSO: 65518/35/2048
bge0: Ethernet address: a8:60:b6:23:11:34
<5>bge0: link state changed to DOWN
<5>bge0: link state changed to UP
<6>bge0: promiscuous mode enabled
dev.miibus.0.%parent: bge0 -
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
The bge network driver is not listed as supporting netmap operation. Netmap compatibility is required for inline IPS mode. That has been mentioned here over and over and over. You either need to install a netmap compatible network card or else switch to Legacy Mode blocking. That mode does not use netmap.
These are the NIC driver families listed by FreeBSD as supporting netmap operation: em, igb, ixgb, ixl, lem, re or cxgbe.
I didn't see your post until posted the above. That's a bummer; however, could you have a look at the above data just scan see if anything out of norm?
-
I see several error messages related to your old igb1 NIC interface. They should not be happening if your
config.xmlwas correctly migrated over to the new hardware. Unless you actually have an igb NIC in the box, too. Looks like maybe the DHCP client is still trying to find and use an igb1 interface, but it does not exist in the new box. -
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
I see several error messages related to your old igb1 NIC interface. They should not be happening if your
config.xmlwas correctly migrated over to the new hardware. Unless you actually have an igb NIC in the box, too. Looks like maybe the DHCP client is still trying to find and use an igb1 interface, but it does not exist in the new box.Thank you Bmeeks...I will need some fine tuning as Suricata is not running in Legacy mode either. I will be busy from now until the coming weekend and most likely won't follow up till late at nights.
The Mac Mini Server 2011 definitely has WAN on thunderbolt to an ethernet adapter...no igb interface.
-
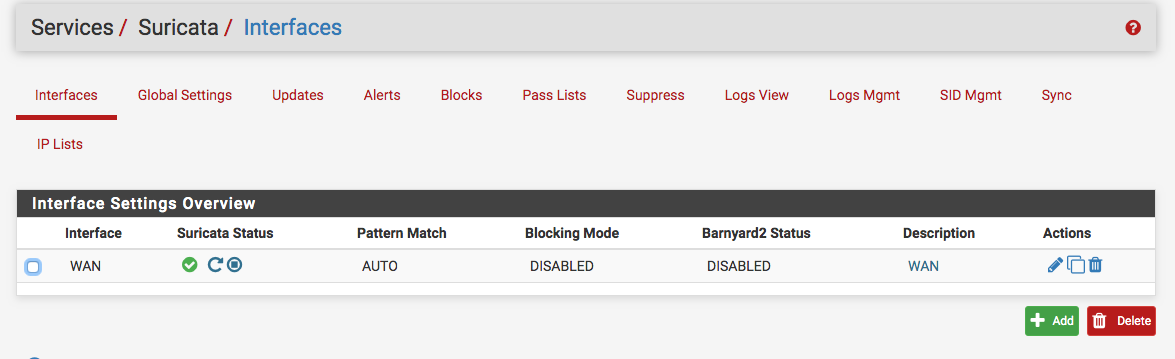
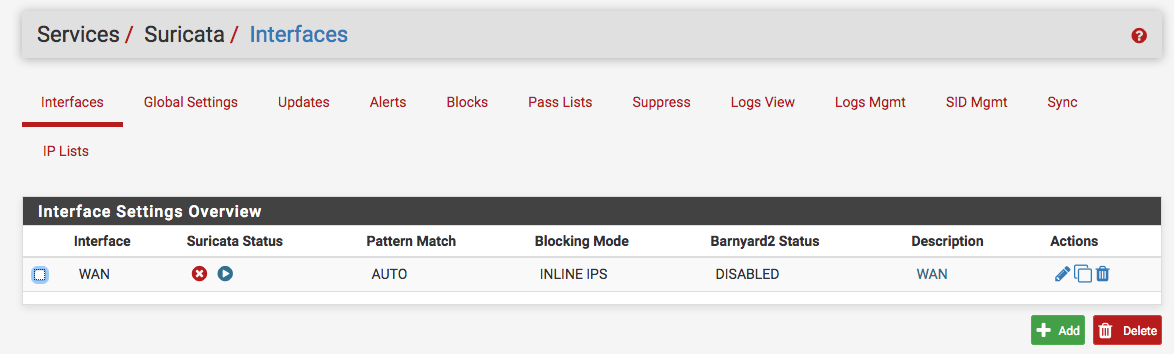
(dev.bge0.0.fc) >This was showing igb in System Tunables; but even after changing that and rebooting, Suricate doesn't show running on interface tab...see below! Looking at the system log shows Suricata started, it seems!
Last 50 General Log Entries. (Maximum 50)
Jun 16 21:53:01 kernel bge1: link state changed to UP
Jun 16 21:53:02 kernel done.
Jun 16 21:53:02 kernel done.
Jun 16 21:53:02 check_reload_status Updating all dyndns
Jun 16 21:53:02 php-cgi rc.bootup: [squid] Installed but disabled. Not installing 'nat' rules.
Jun 16 21:53:02 php-cgi rc.bootup: [squid] Installed but disabled. Not installing 'pfearly' rules.
Jun 16 21:53:02 kernel .
Jun 16 21:53:02 php-cgi rc.bootup: [squid] Installed but disabled. Not installing 'filter' rules.
Jun 16 21:53:02 kernel ..
Jun 16 21:53:02 kernel .done.
Jun 16 21:53:06 php-cgi rc.bootup: Creating rrd update script
Jun 16 21:53:07 kernel done.
Jun 16 21:53:07 syslogd exiting on signal 15
Jun 16 21:53:07 syslogd kernel boot file is /boot/kernel/kernel
Jun 16 21:53:07 kernel done.
Jun 16 21:53:07 php-fpm 356 /rc.start_packages: Restarting/Starting all packages.
Jun 16 21:53:07 php-fpm 356 [pfBlockerNG] Starting firewall filter daemon
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)...
Jun 16 21:53:07 php [pfBlockerNG] DNSBL parser daemon started
Jun 16 21:53:07 php_pfb [pfBlockerNG] filterlog daemon started
Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...
Jun 16 21:53:07 php-fpm 356 /rc.start_packages: [squid] - squid_resync function call pr: bp: rpc:no
Jun 16 21:53:08 SnortStartup 45918 Snort START for LAN(37578_bge1)...
Jun 16 21:53:08 kernel bge0: promiscuous mode enabled
Jun 16 21:53:08 kernel bge1: promiscuous mode enabled
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] Removing cronjobs ...
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] 'Local Cache' not configured, disk cache will be disabled.
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] Please, configure and save 'Local Cache' settings before enabling Squid proxy.
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] Antivirus features disabled.
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] Removing freshclam cronjob.
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] 'Local Cache' not configured, disk cache will be disabled.
Jun 16 21:53:08 php-fpm 356 /rc.start_packages: [squid] Please, configure and save 'Local Cache' settings before enabling Squid proxy.
Jun 16 21:53:09 check_reload_status Reloading filter
Jun 16 21:53:09 Squid_Alarm 53685 Squid is disabled, exiting.
Jun 16 21:53:09 php [pfBlockerNG] DNSBL parser daemon started
Jun 16 21:53:09 php_pfb [pfBlockerNG] filterlog daemon started
Jun 16 21:53:10 php-fpm 357 /rc.filter_configure_sync: [squid] Installed but disabled. Not installing 'nat' rules.
Jun 16 21:53:10 php-fpm 357 /rc.filter_configure_sync: [squid] Installed but disabled. Not installing 'pfearly' rules.
Jun 16 21:53:10 php-fpm 357 /rc.filter_configure_sync: [squid] Installed but disabled. Not installing 'filter' rules.
Jun 16 21:53:10 login login on ttyv0 as root
Jun 16 21:53:25 php-fpm 356 /index.php: Successful login for user 'admin' from: 192.168.1.102 (Local Database)
Jun 16 21:54:02 check_reload_status Syncing firewallSuricata is not running:
-
Package installer said Suricata is installed however, there is no yaml...how could that be? Is there anything I can do at the command prompt?
Shell Output - /etc/suricata/suricata.yaml
sh: /etc/suricata/suricata.yaml: not found -
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box. -
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
Package installer said Suricata is installed however, there is no yaml...how could that be? Is there anything I can do at the command prompt?
Shell Output - /etc/suricata/suricata.yaml
sh: /etc/suricata/suricata.yaml: not foundYou are looking in the wrong directory. That is not where the configuration of local packages exists on FreeBSD installs such as pfSense. The correct directory is /usr/local/etc, but even then that is not the entire path for Suricata or Snort. The interface configurations live in sub-directories underneath /usr/local/etc/suricata or /usr/local/etc/snort.
-
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box.Okay Bmeeks; however, only Suricata is in inline mode with blocking enabled...Snort is running in alert only with no blocking. Had that setup running for almost a year and a half with no problem on the HP box.
You are correct Bmeeks and I'll start over from scratch next weekend.

-
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box.Okay Bmeeks; however, only Suricata is in inline mode with blocking enabled...Snort is running in alert only with no blocking. Had that setup running for almost a year and a half with no problem on the HP box.
You are correct Bmeeks and I'll start over from scratch next weekend.

Having both of those running on the same firewall makes absolutely no sense. They use essentially the same rule signatures. That's almost like running two copies of the same anti-virus program on a PC. What is one going to detect that the other doesn't? Pick one or the other IDS/IPS solution (Suricata or Snort) and use just that one. Don't try to use both on the same box, much less on the same interface.
-
@bmeeks Bill, I had to post this example although it's not related to pfSense...you might know of it and it's from Github: https://github.com/security-onion-solutions/security-onion
Security Onion"Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
For more information about Security Onion, please see our main website, blog, and docs".
They have both Suricata, and Snort on the same OS/box...I am not the only one with that crazy idea. For me, Suricata works WAN and Snort on LAN...I get your point though on potential conflict.
-
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
@bmeeks Bill, I had to post this example although it's not related to pfSense...you might know of it and it's from Github: https://github.com/security-onion-solutions/security-onion
Security Onion"Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
For more information about Security Onion, please see our main website, blog, and docs".
They have both Suricata, and Snort on the same OS/box...I am not the only one with that crazy idea. For me, Suricata works WAN and Snort on LAN...I get your point though on potential conflict.
I still see no point really in running both on the same box, but so long as they are on totally separate interfaces it will work (well, so long as one is using Inline IPS Mode and the other is using Legacy Mode or IDS mode only; otherwise they can conflict with the single snort2c table in
pf). In your case, I saw in the system log snippet you posted that both Suricata and Snort were attempting to start on the same interface (bge0, if I recall correctly). That won't work well at all! One is trying to configure the interface for netmap mode and other is trying to configure it for PCAP mode. Not going to work correctly. -
@bmeeks You did recalled correctly...may be it worked with the Intel card with no problem. However, the bge is a different animal and I should have anticipated problems...of course, my head was all about the cute and very small form factor...only the weekend will tell after taking your advice...will inform you then.
-
I never recommend running both on the same interface, but the only way it can work (well) is if only one application is running with blocking mode enabled. So you could run Suricata in just IDS mode (Block Offenders NOT checked) and Snort in blocking mode with Block Offenders checked; or the other way around. You should never run with both in blocking mode on the same interface.
And my other caution about both running on the same box in blocking mode, even on different interfaces, is valid because they will conflict with each other over use of the snort2c table. There is only a single snort2c table for the entire firewall.
-
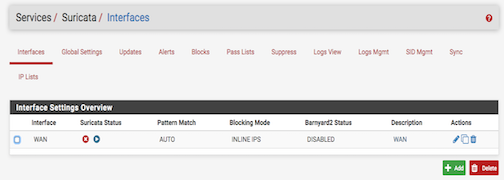
Okay Bill, I did the fresh install and Suricata will not run or not showing that its running on the interface tab. Suricata WAN log shows: 7/7/2019 -- 00:42:47 - <Error> -- [ERRCODE: SC_ERR_INITIALIZATION(45)] - pid file '/var/run/suricata_bge023163.pid' exists but appears stale. Make sure Suricata is not running and then remove /var/run/suricata_bge023163.pid. Aborting!
I went to edit file under Diagnostic and load /var/run

However, I cannot figure out how to delete it...can you help? Here's system log and noticed there is some time issue:
Jul 7 04:12:41 check_reload_status Syncing firewall
Jul 7 04:12:41 check_reload_status Syncing firewall
Jul 7 04:13:30 check_reload_status Syncing firewall
Jul 7 04:13:59 check_reload_status Syncing firewall
Jul 7 04:14:07 check_reload_status Syncing firewall
Jul 7 04:21:55 check_reload_status Syncing firewall
Jul 7 04:22:13 check_reload_status Syncing firewall
Jul 7 04:32:46 check_reload_status Syncing firewall
Jul 7 04:34:20 check_reload_status Syncing firewall
Jul 7 04:34:27 php-fpm 366 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:27 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:27 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:27 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:34:32 php-fpm 365 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:32 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:33 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:33 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:34:36 php-fpm 365 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:36 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:37 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:37 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:51:23 check_reload_status Syncing firewall
Jul 7 05:04:39 check_reload_status Syncing firewall
Jul 7 05:04:50 php-fpm 81239 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:04:50 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:04:51 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:04:51 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:05:49 check_reload_status Syncing firewall
Jul 7 05:05:54 php-fpm 366 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:05:55 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:05:55 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:05:55 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:07:01 check_reload_status Syncing firewall
Jul 7 05:42:24 check_reload_status Syncing firewall
Jul 7 05:42:46 php-fpm 56294 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:42:46 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:42:47 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:42:47 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:46:46 check_reload_status Syncing firewall
Jul 7 05:46:46 syslogd exiting on signal 15
Jul 7 00:46:46 syslogd kernel boot file is /boot/kernel/kernel
Jul 7 00:46:46 nollipfsense.localdomain nginx: 2019/07/07 00:46:46 [error] 50081#100505: send() failed (54: Connection reset by peer)
Jul 7 01:00:00 php-cgi [Suricata] Checking for updated MaxMind GeoLite2 IP database file...
Jul 7 01:00:00 php-cgi [Suricata] GeoLite2-Country IP database is up-to-date.
Jul 7 01:00:00 php-cgi [Suricata] GeoLite2-Country database update check finished.
Jul 7 02:36:49 nollipfsense.localdomain nginx: 2019/07/07 02:36:49 [error] 50154#100632: send() failed (54: Connection reset by peer)
Jul 7 10:39:46 check_reload_status Syncing firewall
Jul 7 10:39:46 php-fpm 365 [Suricata] Updating rules configuration for: WAN ...
Jul 7 10:39:47 php-fpm 365 [Suricata] Enabling any flowbit-required rules for: WAN...
Jul 7 10:39:47 php-fpm 365 [Suricata] Building new sid-msg.map file for WAN...I have been reading your reply here: https://forum.netgate.com/topic/131716/still-seeing-suricata-stop-an-interface-due-to-pid-error/35
Also this and I wondered why permission denied:
Shell Output - /var/log/suricata
sh: /var/log/suricata: Permission deniedBTW, I had increased Stream memory Cap to 512MB for my 8 CPU/Core with no luck.
-
Do you actually have 2 instances of Suricata running on both your LAN and WAN interfaces?
You also seem to have the same UUID on both bge0 and bge1. That is not possible within the GUI. Did you manually edit something in the
config.xmlfile? If so, the configuration is not correct. You should never have the same UUID on any interface. You have 23163 on both bge0 and bge1. While that is not directly the cause of your PID file problem, it does clearly indicate to me that your Suricata configuration is totally hosed up on that box. Is this still that Mac server you were trying to use earlier? -
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Do you actually have 2 instances of Suricata running on both your LAN and WAN interfaces?
You also seem to have the same UUID on both bge0 and bge1. That is not possible within the GUI. Did you manually edit something in the
config.xmlfile? If so, the configuration is not correct. You should never have the same UUID on any interface. You have 23163 on both bge0 and bge1. While that is not directly the cause of your PID file problem, it does clearly indicate to me that your Suricata configuration is totally hosed up on that box. Is this still that Mac server you were trying to use earlier?Yes Bill, it is the same Mac server and no, I didn't edit config.xml. When I first configured Suricata on WAN to see whether it would run without enabling any blocking and it did not. So, I implement LAN to see whether it would run and that didn't either. May be I should have rebooted the machine.
-
Bill, I just rebooted and Suricata is now running!