Site-2-Site with Cisco RV120W Wireless-N VPN Firewall
-
Hi guys,
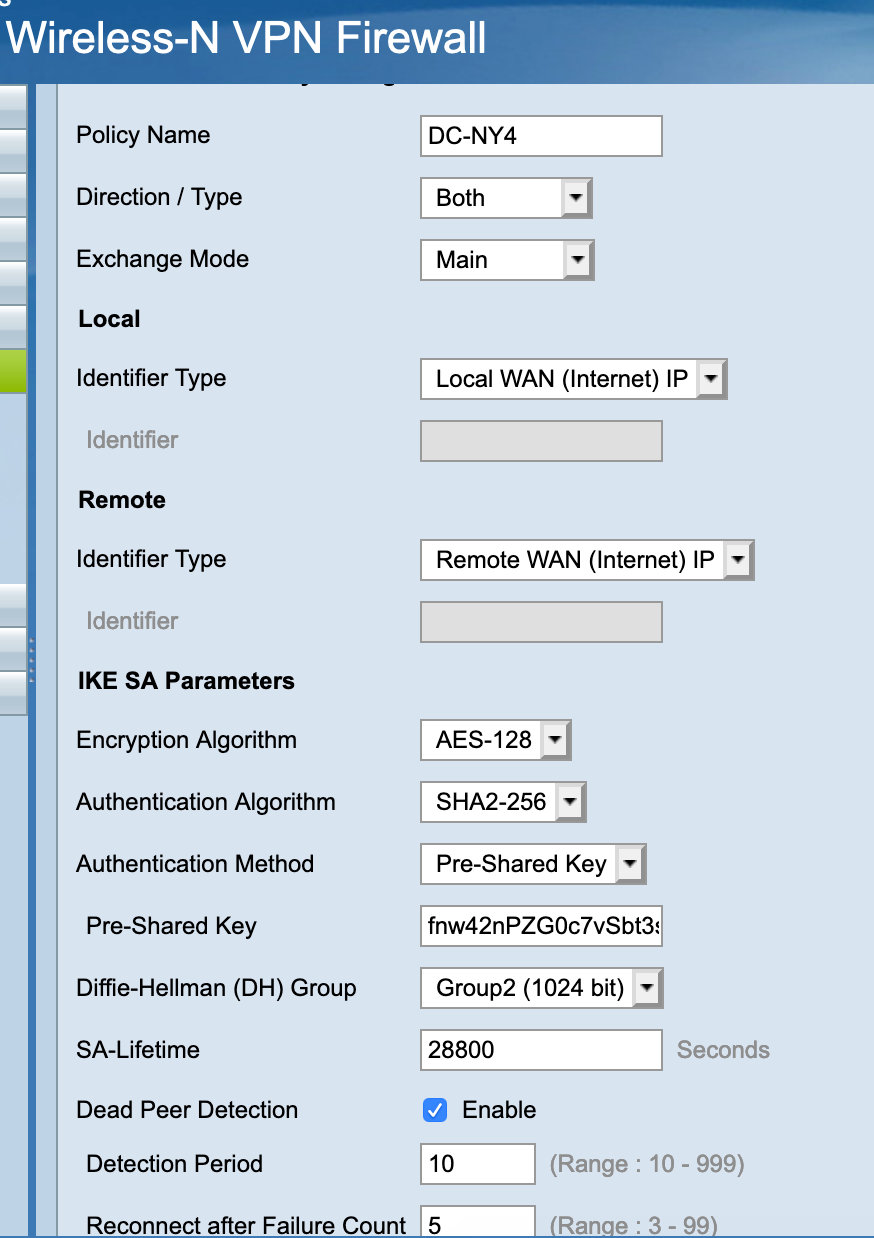
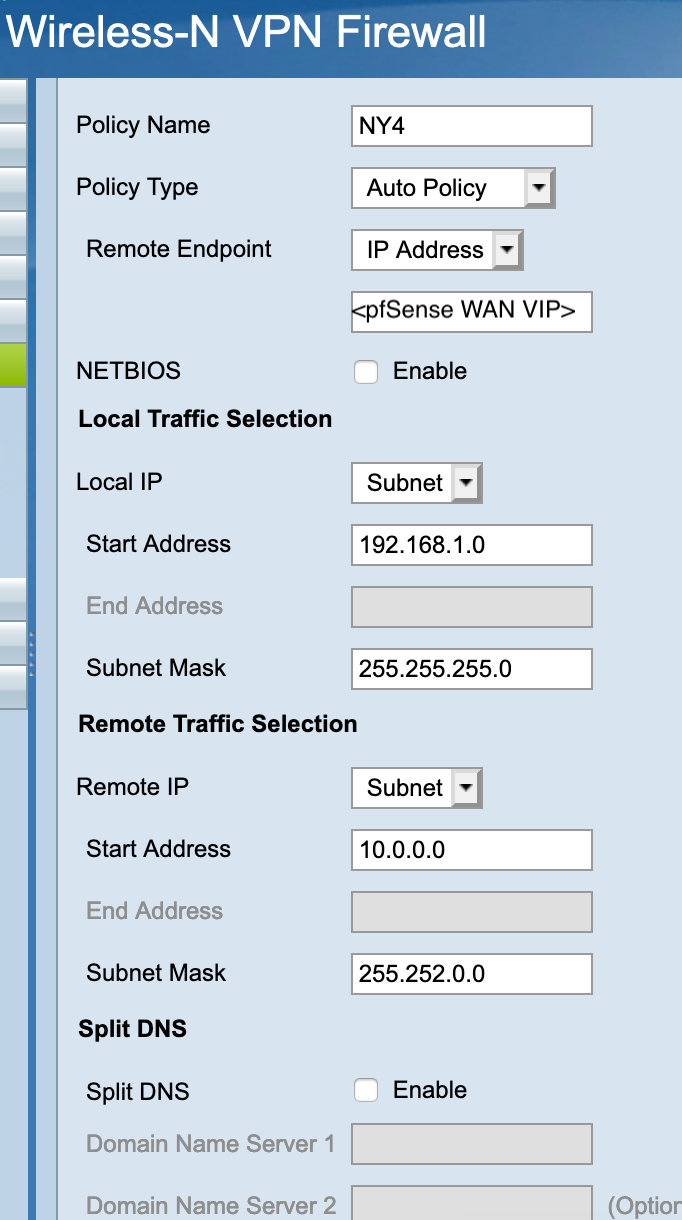
Please help me to solve the following issue. I have a KVM based pfSense cluster on one side and Cisco RV120W on the other one. Last SOHO from Cisco I've touched was 800 Series and it was quite good, CLI, IOS, show, debug... you know. The las one (RV1200W) doesn't provide an interface except some weird GUI and very basic IPSec configuration. Three times I made symmetric IPSec configuration with different crypto/digest parameters obtaining the same result: IPSec phase 1 comes up but no traffic going in/from the tunnel. Here is a relevant part of /var/etc/ipsec/ipsec.conf file
conn con2000 fragmentation = yes keyexchange = ikev1 reauth = yes forceencaps = no mobike = no rekey = yes installpolicy = yes type = tunnel dpdaction = restart dpddelay = 10s dpdtimeout = 60s auto = route left = <WAN_CARP VIP> right = <Cisco RV120 IP> leftid = <WAN_CARP VIP> ikelifetime = 28800s lifetime = 3600s ike = aes128-sha256-modp1024! esp = aes128-sha256-modp1024! leftauth = psk rightauth = psk rightid = <Cisco RV120 IP> aggressive = no rightsubnet = 192.168.1.0/24 leftsubnet = 10.0.0.0/14On the Cisco RV120 I have:
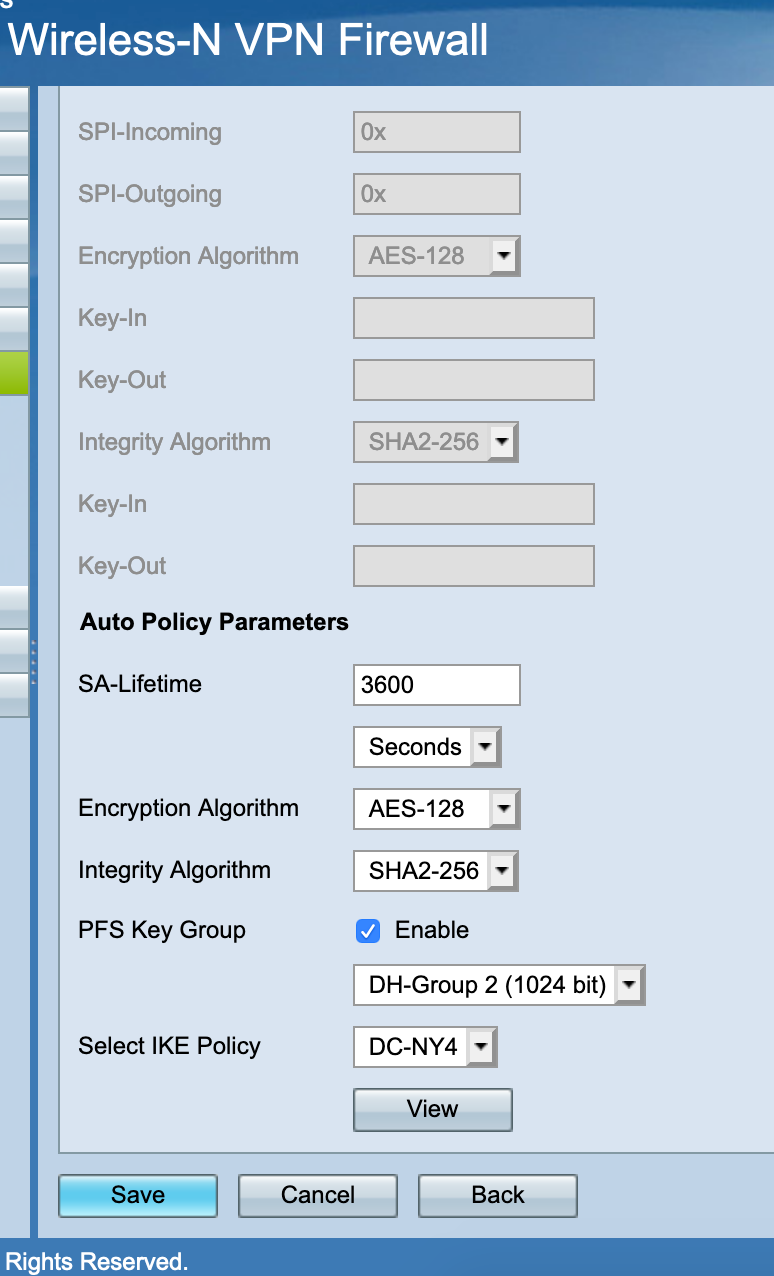
-
This post is deleted! -
When I try to ping the destination behind the Cisco router I don't see child SA counters increase, sometimes there are 2 IPSec SA created at a time:
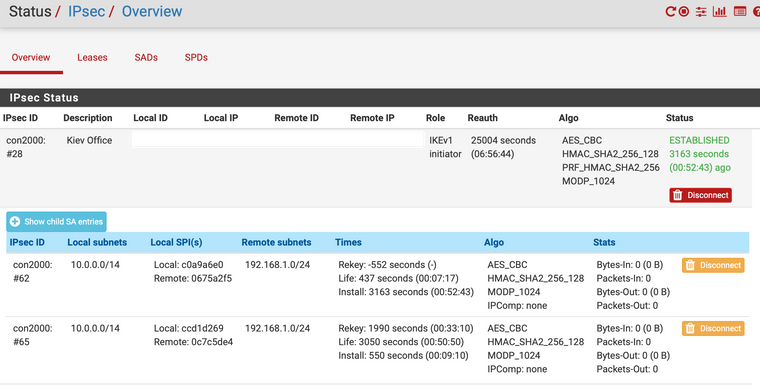
In IPSec logs on pfSense I get:
Jun 23 12:49:01 charon 11[IKE] <con2000|28> nothing to initiate Jun 23 12:49:02 charon 15[CFG] vici client 2141 connected Jun 23 12:49:02 charon 11[CFG] vici client 2141 registered for: list-sa Jun 23 12:49:02 charon 11[CFG] vici client 2141 requests: list-sas Jun 23 12:49:02 charon 11[CFG] vici client 2141 disconnected Jun 23 12:49:03 charon 15[NET] <con1000|26> received packet: from 38.142.65.154[500] to 154.61.34.210[500] (76 bytes) Jun 23 12:49:03 charon 15[ENC] <con1000|26> parsed INFORMATIONAL request 4746 [ ] Jun 23 12:49:03 charon 15[ENC] <con1000|26> generating INFORMATIONAL response 4746 [ ] Jun 23 12:49:03 charon 15[NET] <con1000|26> sending packet: from 154.61.34.210[500] to 38.142.65.154[500] (76 bytes) Jun 23 12:49:06 charon 15[NET] <con2000|28> received packet: from 195.177.74.126[500] to 154.61.34.210[500] (108 bytes) Jun 23 12:49:06 charon 15[ENC] <con2000|28> parsed INFORMATIONAL_V1 request 3823163103 [ HASH N(DPD) ] Jun 23 12:49:06 charon 15[IKE] <con2000|28> queueing ISAKMP_DPD task Jun 23 12:49:06 charon 15[IKE] <con2000|28> activating new tasks Jun 23 12:49:06 charon 15[IKE] <con2000|28> activating ISAKMP_DPD task Jun 23 12:49:06 charon 15[ENC] <con2000|28> generating INFORMATIONAL_V1 request 2486254723 [ HASH N(DPD_ACK) ] Jun 23 12:49:06 charon 15[NET] <con2000|28> sending packet: from 154.61.34.210[500] to 195.177.74.126[500] (108 bytes) Jun 23 12:49:06 charon 15[IKE] <con2000|28> activating new tasks Jun 23 12:49:06 charon 15[IKE] <con2000|28> nothing to initiateOn Cisco's side I see the tunnel up and running, and when try to initiate ESP traffic from that side I see increasing Tx counters on Cisco's IPSec status.
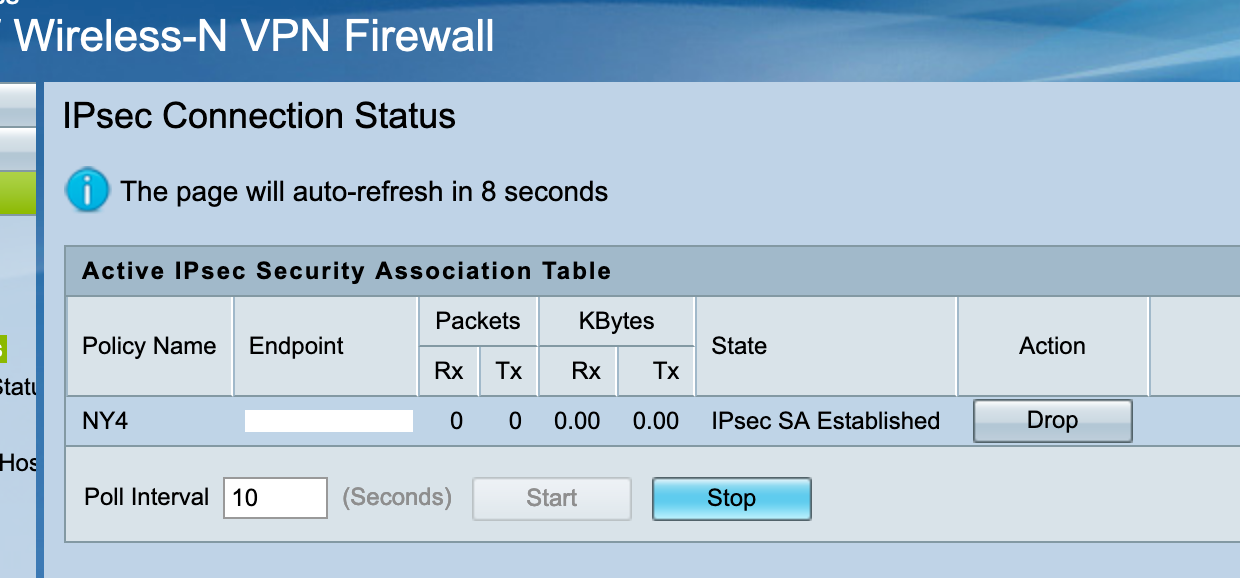
On pfSense tcpdump I receive incoming ESP from Cisco, but I don't see any outgoing ESP packets toward Cisco.
Here is ipsec statusall output from the pfSense:
[$]/root: ipsec statusall Status of IKE charon daemon (strongSwan 5.7.1, FreeBSD 11.2-RELEASE-p10, amd64): uptime: 46 hours, since Jun 21 14:43:34 2019 worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 6 loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey ... Listening IP addresses: .... Connections: bypasslan: %any...%any IKEv1/2 bypasslan: local: uses public key authentication bypasslan: remote: uses public key authentication bypasslan: child: 10.0.11.0/24|/0 === 10.0.11.0/24|/0 PASS con2000: <WAN-CARP VIP>...<Cisco IP> IKEv1, dpddelay=10s con2000: local: [<WAN-CARP VIP>] uses pre-shared key authentication con2000: remote: [<Cisco IP>] uses pre-shared key authentication con2000: child: 10.0.0.0/14|/0 === 192.168.1.0/24|/0 TUNNEL, dpdaction=restart Shunted Connections: bypasslan: 10.0.11.0/24|/0 === 10.0.11.0/24|/0 PASS Routed Connections: con2000{64}: ROUTED, TUNNEL, reqid 4 con2000{64}: 10.0.0.0/14|/0 === 192.168.1.0/24|/0 Security Associations (2 up, 0 connecting): con2000[28]: ESTABLISHED 38 minutes ago, <WAN-CARP VIP>[<WAN-CARP VIP>]...<Cisco IP>[<Cisco IP>] con2000[28]: IKEv1 SPIs: 2316dd2784d9bdac_i* 261b4138e97f82d0_r, pre-shared key reauthentication in 7 hours con2000[28]: IKE proposal: AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 con2000{62}: INSTALLED, TUNNEL, reqid 4, ESP SPIs: c0a9a6e0_i 0675a2f5_o con2000{62}: AES_CBC_128/HMAC_SHA2_256_128/MODP_1024, 0 bytes_i (0 pkts, 2336s ago), 0 bytes_o, rekeying in 4 minutes con2000{62}: 10.0.0.0/14|/0 === 192.168.1.0/24|/0 [$]/root:What could it be, what do you suggest to test in addition?
-
-
@Konstanti
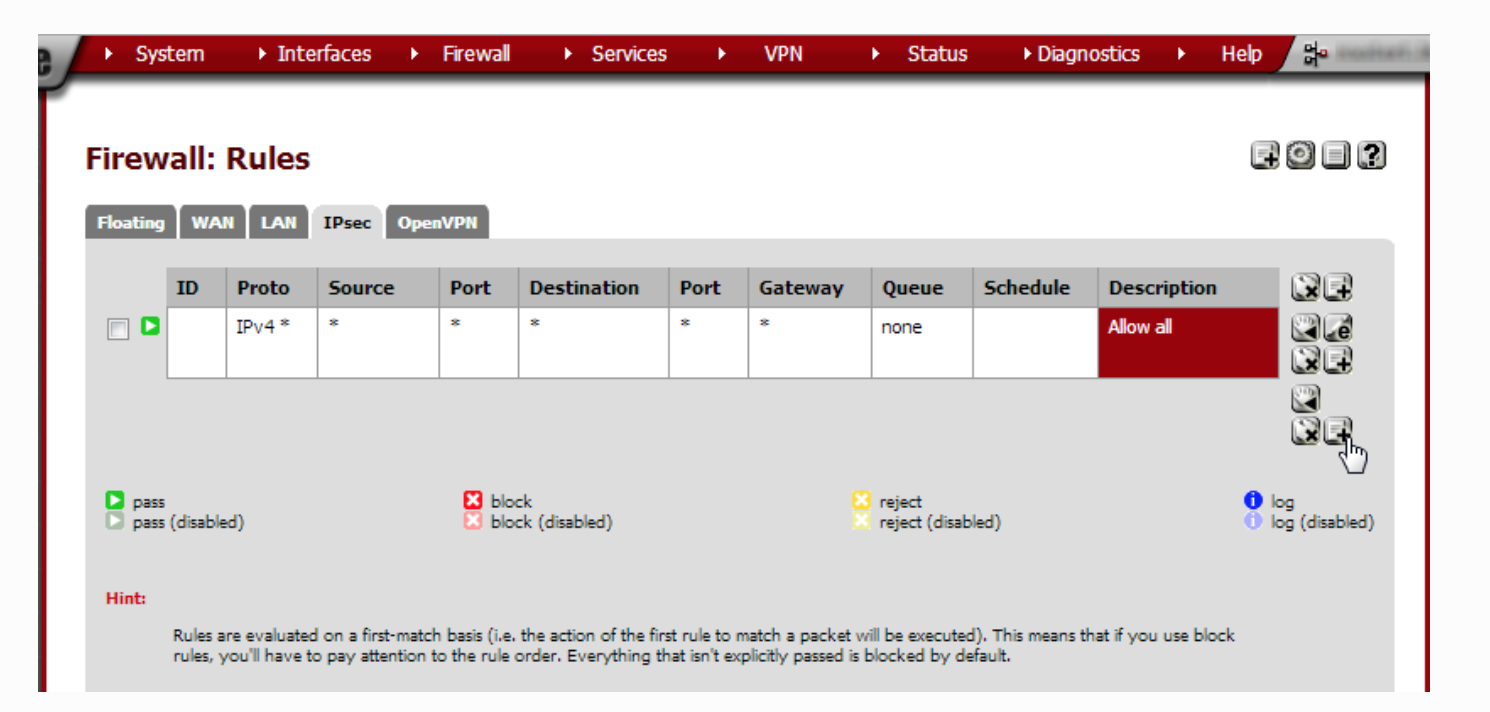
I have such rule, it's not the cause of the problem. -
@shshs
try to start tcpdump on the enc0 interface
for example
tcpdump -netti enc0
what it shows ?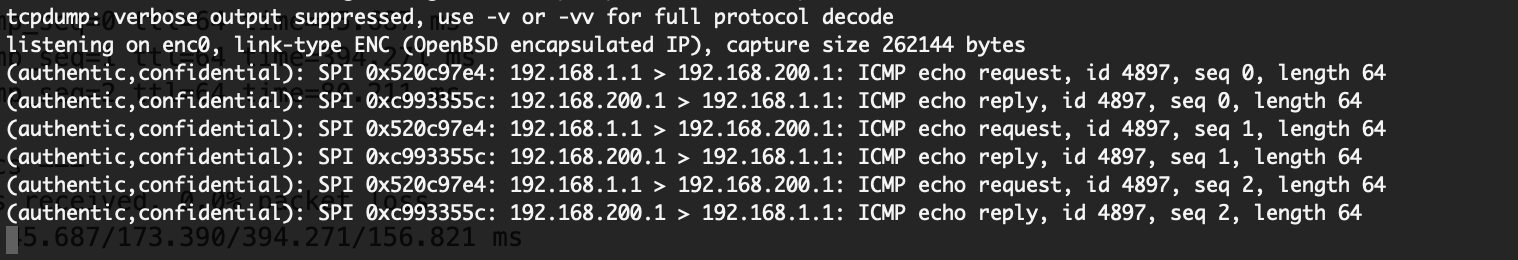
-
@Konstanti said in Site-2-Site with Cisco RV120W Wireless-N VPN Firewall:
tcpdump -netti enc0
While I'm pinging the destination behind the other site of the tunnel, I run tcpdump on enc0 and it doesn't show any relevant information, just traffic from the other IPSec VPNs.
-
Hi guys,
Any ideas why it doesn't work? What's the reason of appearing such logs in pfSense:
Jun 23 12:49:06 charon 15[NET] <con2000|28> sending packet: from 154.61.34.210[500] to 195.177.74.126[500] (108 bytes) Jun 23 12:49:06 charon 15[IKE] <con2000|28> activating new tasks Jun 23 12:49:06 charon 15[IKE] <con2000|28> nothing to initiateWhy there are no outgoing ESP packets from pfSense and why IPSec SA counters doesn't increased?