IPsec Phase 1 timeout, PFsense to Sonicwall
-
Here is PFsense log:
Jun 26 12:39:58 charon 06[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:39:58 charon 06[IKE] <con2000|98> sending retransmit 5 of request message ID 0, seq 1
Jun 26 12:39:39 charon 06[CFG] ignoring acquire, connection attempt pending
Jun 26 12:39:39 charon 12[KNL] creating acquire job for policy x.x.x.x/32|/0 === z.z.z.z/32|/0 with reqid {8}
Jun 26 12:39:16 charon 12[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:39:16 charon 12[IKE] <con2000|98> sending retransmit 4 of request message ID 0, seq 1
Jun 26 12:39:05 charon 12[CFG] ignoring acquire, connection attempt pending
Jun 26 12:39:05 charon 06[KNL] creating acquire job for policy x.x.x.x/32|/0 === z.z.z.z/32|/0 with reqid {8}
Jun 26 12:39:00 charon 06[CFG] vici client 27759 disconnected
Jun 26 12:39:00 charon 05[CFG] vici client 27759 requests: list-sas
Jun 26 12:39:00 charon 05[CFG] vici client 27759 registered for: list-sa
Jun 26 12:39:00 charon 05[CFG] vici client 27759 connected
Jun 26 12:38:53 charon 12[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:38:53 charon 12[IKE] <con2000|98> sending retransmit 3 of request message ID 0, seq 1
Jun 26 12:38:40 charon 09[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:38:40 charon 09[IKE] <con2000|98> sending retransmit 2 of request message ID 0, seq 1
Jun 26 12:38:32 charon 09[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:38:32 charon 09[IKE] <con2000|98> sending retransmit 1 of request message ID 0, seq 1
Jun 26 12:38:28 charon 09[NET] <con2000|98> sending packet: from x.x.x.x[500] to z.z.z.z[500] (180 bytes)
Jun 26 12:38:28 charon 09[ENC] <con2000|98> generating ID_PROT request 0 [ SA V V V V V ]
Jun 26 12:38:28 charon 09[CFG] <con2000|98> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jun 26 12:38:28 charon 09[IKE] <con2000|98> IKE_SA con2000[98] state change: CREATED => CONNECTING
Jun 26 12:38:28 charon 09[IKE] <con2000|98> initiating Main Mode IKE_SA con2000[98] to z.z.z.z
Jun 26 12:38:28 charon 09[IKE] <con2000|98> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Jun 26 12:38:28 charon 09[IKE] <con2000|98> sending NAT-T (RFC 3947) vendor ID
Jun 26 12:38:28 charon 09[IKE] <con2000|98> sending FRAGMENTATION vendor ID
Jun 26 12:38:28 charon 09[IKE] <con2000|98> sending DPD vendor ID
Jun 26 12:38:28 charon 09[IKE] <con2000|98> sending XAuth vendor ID
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating ISAKMP_NATD task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating ISAKMP_CERT_POST task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating MAIN_MODE task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating ISAKMP_CERT_PRE task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating ISAKMP_VENDOR task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> activating new tasks
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing QUICK_MODE task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing ISAKMP_NATD task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing ISAKMP_CERT_POST task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing MAIN_MODE task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing ISAKMP_CERT_PRE task
Jun 26 12:38:28 charon 09[IKE] <con2000|98> queueing ISAKMP_VENDOR task
Jun 26 12:38:28 charon 12[KNL] creating acquire job for policy x.x.x.x/32|/0 === z.z.z.z/32|/0 with reqid {8}
Jun 26 12:38:00 charon 12[CFG] vici client 27758 disconnected
Jun 26 12:38:00 charon 09[CFG] vici client 27758 requests: list-sas
Jun 26 12:38:00 charon 13[CFG] vici client 27758 registered for: list-sa
Jun 26 12:38:00 charon 12[CFG] vici client 27758 connected
Jun 26 12:37:31 charon 13[IKE] <con2000|97> IKE_SA con2000[97] state change: CONNECTING => DESTROYING
Jun 26 12:37:31 charon 13[IKE] <con2000|97> establishing IKE_SA failed, peer not responding
Jun 26 12:37:31 charon 13[IKE] <con2000|97> giving up after 5 retransmits
Jun 26 12:37:28 charon 13[CFG] ignoring acquire, connection attempt pending
Jun 26 12:37:28 charon 12[KNL] creating acquire job for policy x.x.x.x/32|/0 === z.z.z.z/32|/0 with reqid {8}Sonicwall log:
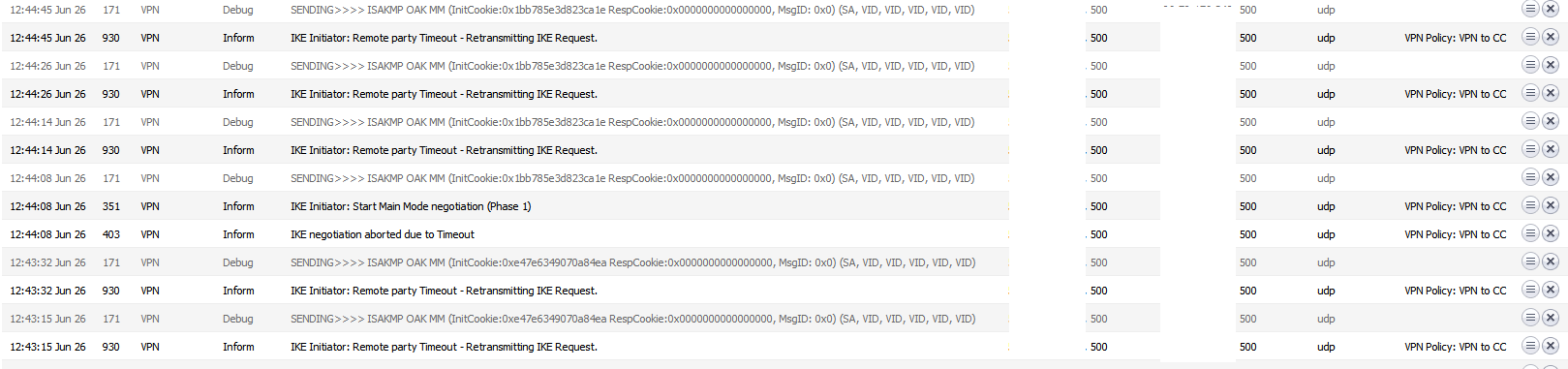
-
nothing in the pfsense firewall log?
The IKE packets are UDP packets with port number 500 as both source and destination, try to do a packet capture to see if you see such packets in both directions if you can -
The other side is not responding. You'll have to look there for the reason.
-
My apology, i fat fingered wrong number in IP address in one option. Kept overlooking it
-
Which is part of the reason its ALWAYS! best to post screenshots of your setup ;) Users saying they Did X, but really doing Y is easier to catch when multiple eyes on the setup.
-
Wouldn't have known it was the wrong address though.
-
very true - unless is had posted what they are suppose to be ;)
-
And managed not to fat-finger that too.

Just poking fun man. Glad you found it. We have ALL done that and taken far too long to see it.