DNS over TLS with pfSense
-
I followed the instructions from this link ( DNS over TLS with pfSense ) to setup DNS over TLS.
Question: There was no mention of applying any other settings within the DNS Resolver. Does the following settings look correct?
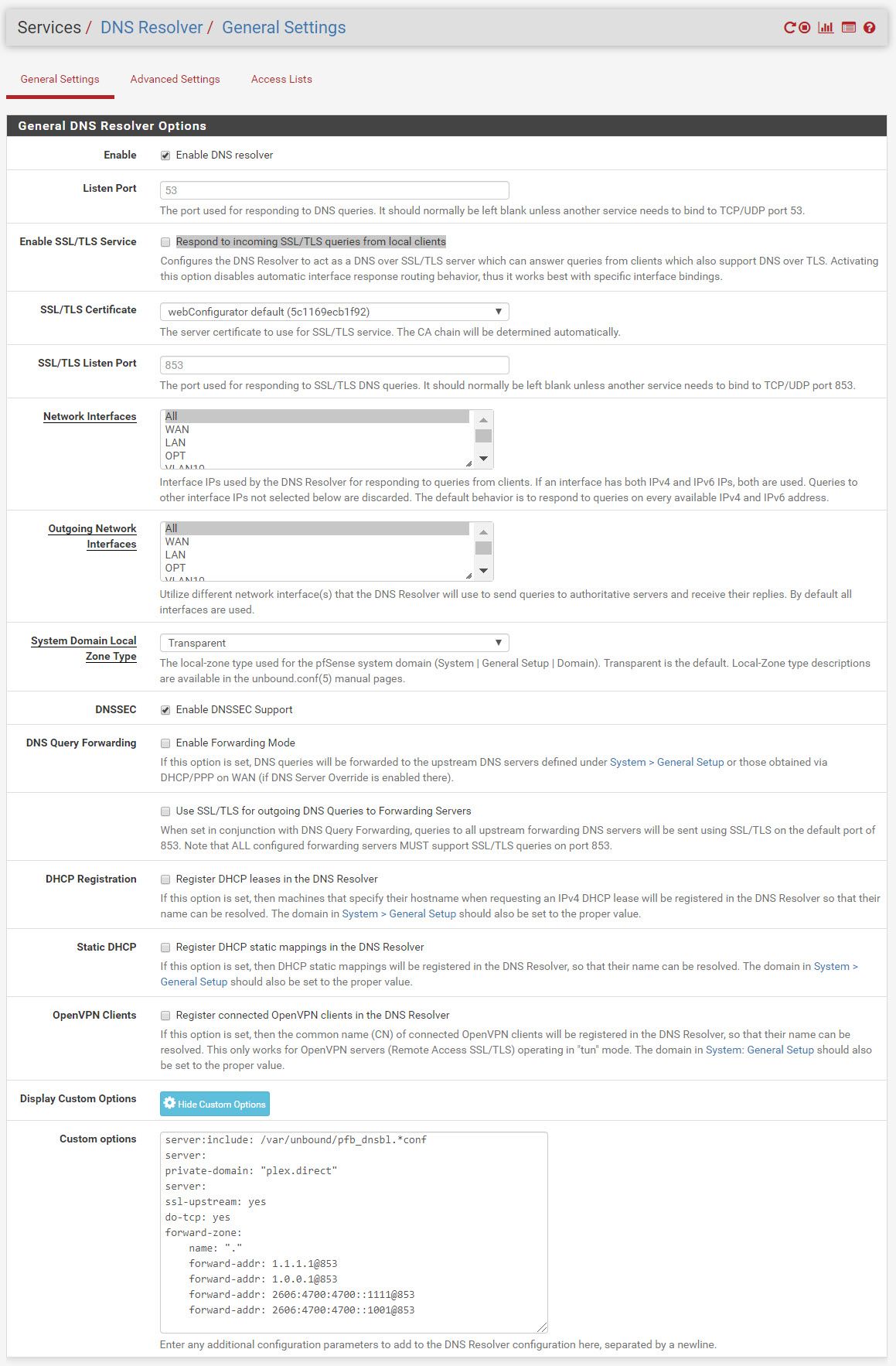
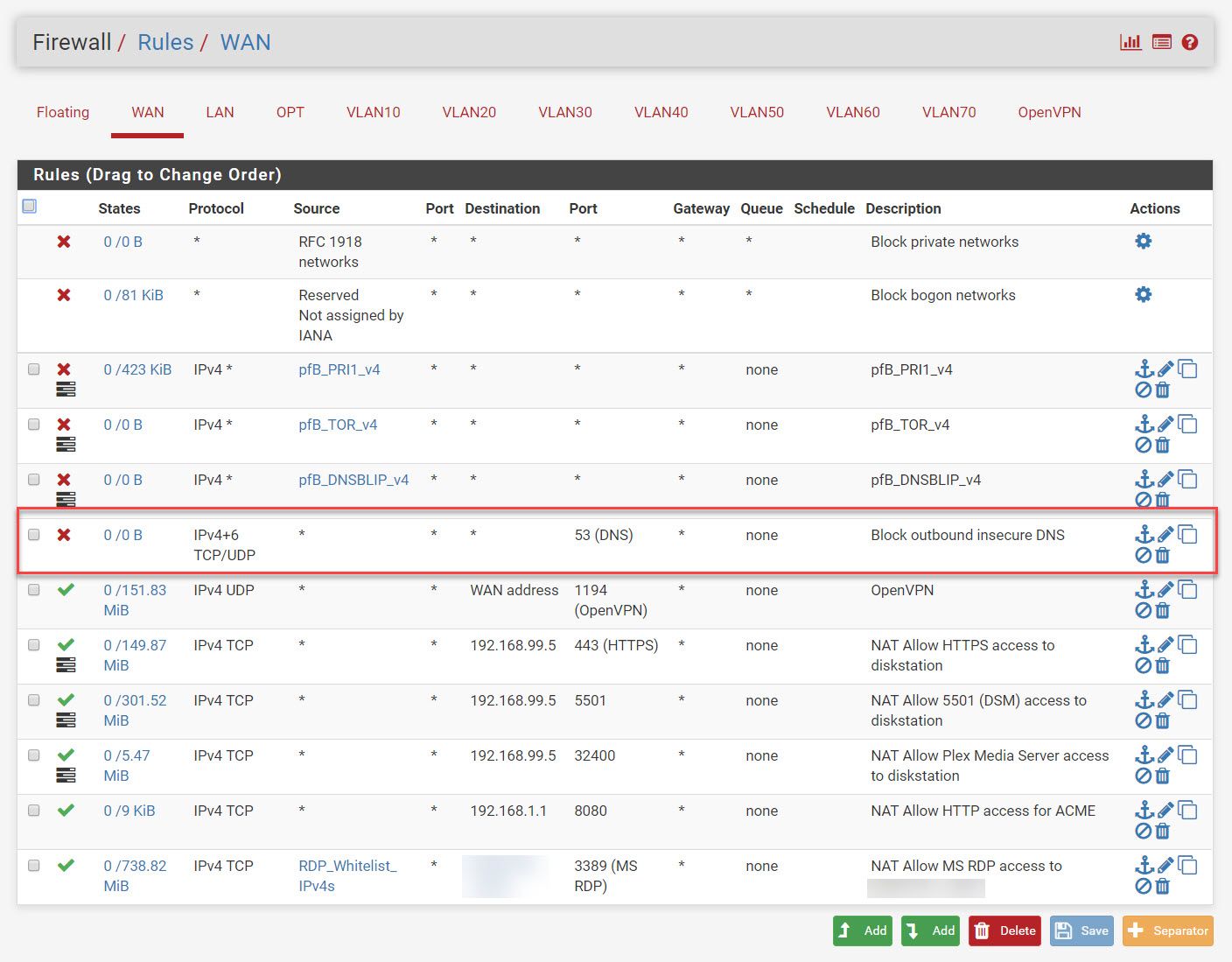
I also added a rule within the WAN (blocked in red)
-
You wouldn't put a rule on wan to block in bound dns?? Not sure where you got the idea that would do anything?
Also the blog is dated, you can just enable dns forwarding over tls in the gui now.. No need for those options in the custom box.
Says so right here in the blog post
"This feature will be available as a GUI option in pfSense 2.4.4, and at that time the custom options can be removed." -
@johnpoz said in DNS over TLS with pfSense:
you can just enable dns forwarding over tls in the gui now
Thanks! I removed the settings as you suggested and verified the WAN traffic using packet capture. It works!
-
@johnpoz said in DNS over TLS with pfSense:
You wouldn't put a rule on wan to block in bound dns?? Not sure where you got the idea that would do anything?
Also the blog is dated, you can just enable dns forwarding over tls in the gui now.. No need for those options in the custom box.
Says so right here in the blog post
"This feature will be available as a GUI option in pfSense 2.4.4, and at that time the custom options can be removed."@johnpoz I think now would be a good time to put up a post about pfsense and the options available concerning DNS. There continues to be confusion over what you get and why you would do DNS over TLS and what you get and why you need DNSSEC. I think too many people are worried about DNS privacy while ignoring the more important issue of spoofing. Who are you trusting and what does that mean.
I could write something up and post it but I think you, as a moderator, would do a more precise job of that in the context of what pfsense offers. Admittedly, I have not looked at the "book" to see what is there. If it's already well covered, just ignore me...
-
@jwj said in DNS over TLS with pfSense:
why you would do DNS over TLS
I would never do dns over tls.. If I had reason to think my isp was intercepting and manipulating my dns, then I would use a vpn, or better yet get a new isp ;)
I would only ever do such a thing, if I was doing it to a server I controlled, and from there it was resolving with dnssec, etc. But there there would have to be some justification for it, other than I think my isp is spying on me ;)
I could write a book - wouldn't do any good. Users are more than capable of doing their own research vs believing the nonsense.. Why should they take my advice over the 100 sites saying they "need" a vpn for xyz, they "need" to do dns over tls for "abc" etc.
Feel free to write up something - I will either shoot it down or give it a thumbs up ;)
What I will say is the out of box configuration of resolving with dnssec should be fine for vast majority of users.. Most users don't even understand the difference of resolving or forwarding, or what doh or dot means even. Or what dnssec does - they just know their "buddy" told them they should be doing dns over tls for "security" Or some website says they need to pay $7.95 to be secure and private from the "man" <rolleyes>.
But hey - its fine if I let store xyz know everything I buy and when I buy it, which branch I most shop at, etc.. - because they give me 2$ for every 100 I spend in discounts ;) But F that ISP if am going to ask their dns for www.cnn.com - those spying bastards!!!
-
@johnpoz said in DNS over TLS with pfSense:
@jwj said in DNS over TLS with pfSense:
why you would do DNS over TLS
I would never do dns over tls.. If I had reason to think my isp was intercepting and manipulating my dns, then I would use a vpn, or better yet get a new isp ;)
I would only ever do such a thing, if I was doing it to a server I controlled, and from there it was resolving with dnssec, etc. But there there would have to be some justification for it, other than I think my isp is spying on me ;)
I could write a book - wouldn't do any good. Users are more than capable of doing their own research vs believing the nonsense.. Why should they take my advice over the 100 sites saying they "need" a vpn for xyz, they "need" to do dns over tls for "abc" etc.
Feel free to write up something - I will either shoot it down or give it a thumbs up ;)
I'll try to not make an ass of myself :)
-
i'd certainly give it a read. always eager to read and see/ learn new things
-
I have spent a few moments thinking about how I would approach this. What I kept at the top of my mind was to be very careful to not present this is a way that would leave anyone with a false sense of security.
To that end I spent a minute to see what's up with the major banks address records. None are signed. Not one that I could find. None of the major e-commerce sites are either.
I left the last bit off these, the part with my prefix. They were resolved by unbound on my pfsense gateway with the default settings.
dig com +dnssec +multi ; <<>> DiG 9.10.6 <<>> com +dnssec +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7536 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;com. IN A ;; AUTHORITY SECTION: com. 900 IN SOA a.gtld-servers.net. nstld.verisign-grs.com. ( 1562934892 ; serial 1800 ; refresh (30 minutes) 900 ; retry (15 minutes) 604800 ; expire (1 week) 86400 ; minimum (1 day) ) com. 900 IN RRSIG SOA 8 1 900 ( 20190719123452 20190712112452 3800 com. avcNVlAvjwzI6xv7j+ROd1vA019vMhdlv/zhV4HXQDHR vQ+9BzsJi/oDhHdf/7vhZ7yBTfoyn9AZXq/nzD+cdW99 Nv48Ph+ixfHgW8XnTpgyeC3sfYKMpLVvJ60h9gBFBek7 Qif5zfOco9Mh4g7XHPrs56aDBBVnbybf+N1NIOs= ) CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 66325 IN NSEC3 1 1 0 - ( CK0Q1GIN43N1ARRC9OSM6QPQR81H5M9A NS SOA RRSIG DNSKEY NSEC3PARAM ) CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 66325 IN RRSIG NSEC3 8 2 86400 ( 20190718044523 20190711033523 3800 com. ONmwWPAAvAgVL8WqNm0awFazl0sEvM9ZKsgVDj/yDbNP VFWrhfeM1pR9vDwjqSum3mH4mZTN7YapI4lRnvateuv6 k4dEL51p8JNTArkZTKyPlQm8EACMfgPNqZmrm7Gf2AOU cIvSeUUq/GObMSY2Mygm6DnnrHcVOxPACuwb8M0= )Is exactly what I expect. Signed. Notice the 'ad' flag.
dig www.wellsfargo.com +dnssec +multi ; <<>> DiG 9.10.6 <<>> www.wellsfargo.com +dnssec +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39715 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;www.wellsfargo.com. IN A ;; ANSWER SECTION: www.wellsfargo.com. 900 IN A 159.45.170.145 www.wellsfargo.com. 900 IN A 159.45.2.145 www.wellsfargo.com. 900 IN A 159.45.66.145Not signed. None of the big banks are.
Do not for one minute think that DNSSEC is the key to anything. It's not. It could be an important part, but it's not happening at the moment. You know, as best you can, that when you go to your banks site you're really on the real site by looking at the certificates. That's an entirely different can of worms. I'll not touch that.
One the other topic, DNS over TLS. I dislike surveillance capitalism with the heat of an erupting volcano. If you use your ISPs DNS servers you are handing them a bunch of data for, basically, no work. The thing is this: it's just a drop in the bucket. I will not say "get over it", but there are much bigger issues that can't be solved by adjusting your gateways settings. If you forward to some other resolver, lets say cloudflare, you are just bumping your trust upstream to someone else. Who do you trust? Why do you trust them?
On balance, the pfsense defaults are good. You are your own resolver. You really need a good reason to fiddle with them.
I'm still thinking about what could be said about all of this that would be helpful. I will continue to chew on it and see if I can conclude that something worthwhile can be said without just adding to the noise.
-
@jwj said in DNS over TLS with pfSense:
Do not for one minute think that DNSSEC is the key to anything
Agreed!
If you forward to some other resolver, lets say cloudflare, you are just bumping your trust upstream to someone else
Agreed... And lets keep in mind they could be handing you bogus info as well.. That they have cached, they are just an upstream resolver/forwarder that you seem to trust more than your isp NS.
On balance, the pfsense defaults are good. You are your own resolver. You really need a good reason to fiddle with them.
Agree and concur ;)
I dislike surveillance capitalism with the heat of an erupting volcano
Well stated...
-
@johnpoz said in DNS over TLS with pfSense:
I would never do dns over tls.
Based on the feed back you and other commented, I am going to revert back to using the settings pfsense has set out of the box.
I was wanting to use DNS over TLS to make it harder for Comcast to capitalize off of the DNS data.
-
@costanzo said in DNS over TLS with pfSense:
I was wanting to use DNS over TLS to make it harder for Comcast to capitalize off of the DNS data.
So you your just letting xyz that you forward capitalize on it ;)
But when you resolve - you are sending queries to the authoritative NS directly - your not handing anything to comcast - they would have to sniff all dns traffic and record it, etc. not just parse the logs of their dns server(s).
Keep in mind - they can still tell where your going even when https via the SNI that is in the clear.. Be it they have your dns traffic or not, etc. etc.
What you do for sure when you have your dns go over tls - is take a huge freaking hammer to the overall performance if you ask me ;)