Pfsense being the gateway for another pfsense device
-
What are those clients using for DNS? Assuming they're Windows clients, what does
ipconfig /allreport for DNS server? Out of the box, pfSense enables the DNS Resolver (unbound) which queries the roots and doesn't need an upstream DNS. DNS should just work if your clients are using pfSense LAN for DNS. If the clients are static IP, make sure they're using the correct DNS. If DHCP, check what's being served to them for DNS.As for your others issues, get one thing working at a time and then make a new post for that specific problem.
-
@KOM The internet is working in all its glory, back to the segregation rules.Pfsense main's client can't access the pfsense secondary device however the second pfsense's clients can access the main pfsense. is there any way I could deny that? I followed the rule above. screenshot:
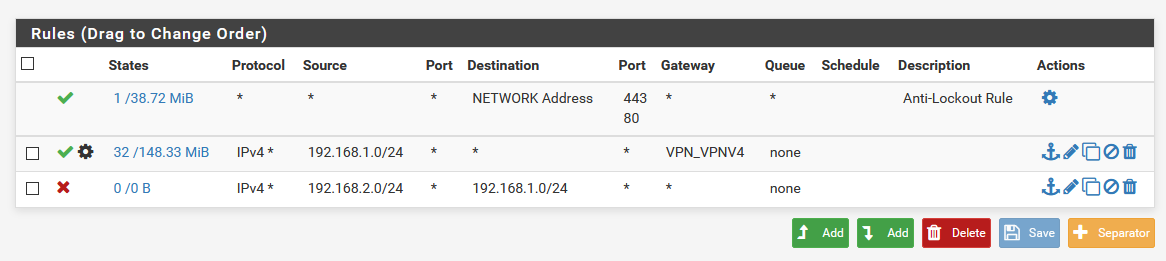
(LAN of the main Pfsense device)
-
Move your block rule above your VPN rule, and then go to Diagnostics - States - Reset States and reset them. Existing states aren't affected by a rule change.
Actually hold on. Why do you have two different networks showing in your rule list? The Source for these rules should always be the network of the interface it's connected to.
-
@KOM I've reset the table, here's the rules now:
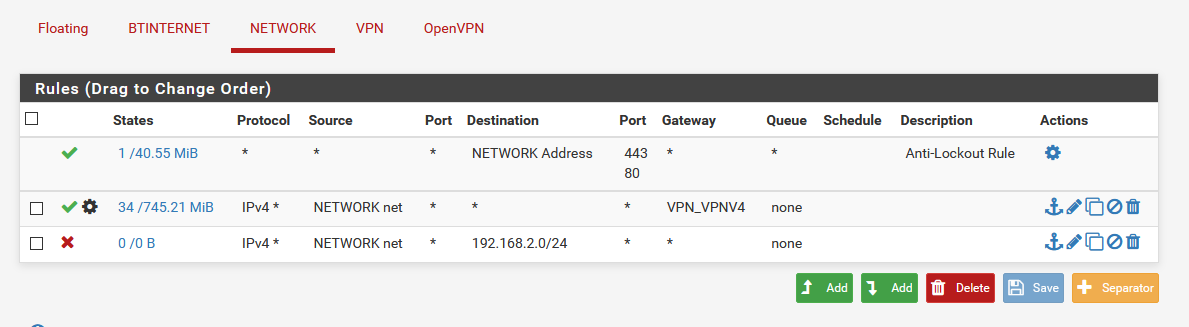
-
Rules are evaluated top-down, first match wins, so rule order is important. You almost always want to put block rules above allow rules.
-
@KOM I can still ping it from the client, does it have anything to do with the fact that it has to connect to the main pfsense device as a WAN that means I can't block it? or am I still missing something?
-
Did you reset your states like I told you to?
-
@KOM Yeah, I did.
-
If you are trying to prevent users of pfsense2 LAN from accessing pfsense1 LAN/pfsense2 WAN, you need to put the rules on pfsense2's LAN tab, not pfsense1.
This would be less confusing if I had a clue about your network configuration details for WAN and LAN on pfsense1 and 2. I did ask for them earlier but you didn't reply.
-
So you have this
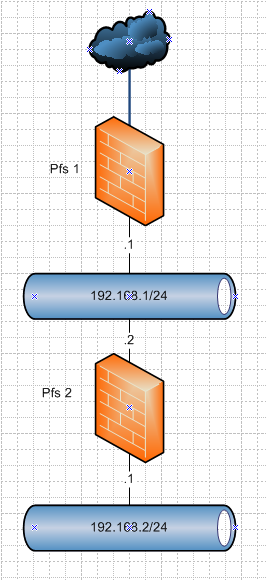
Not sure which network you have were exactly..
But if you don't want 192.168.2/24 (bottom network) from talking to 192.168.1 you would block it on the lan interface of pfs2
You would have allow rule to talk to pfs2 lan addres for dns, ping for example on the pfs2 lan rules
Then you would have a block rule to 192.168.1/24
Then you would have a any rule to allow clients to talk to the internet.. Blocking 192.168.2 on pfs1 lan would be completely pointless and never happen, since pfs2 is directly connected to it.edit: Ah @KOM beat me too it, but he didn't draw a pretty picture like I did ;) heheheh
-
This post is deleted!