My Virtual Lab
-
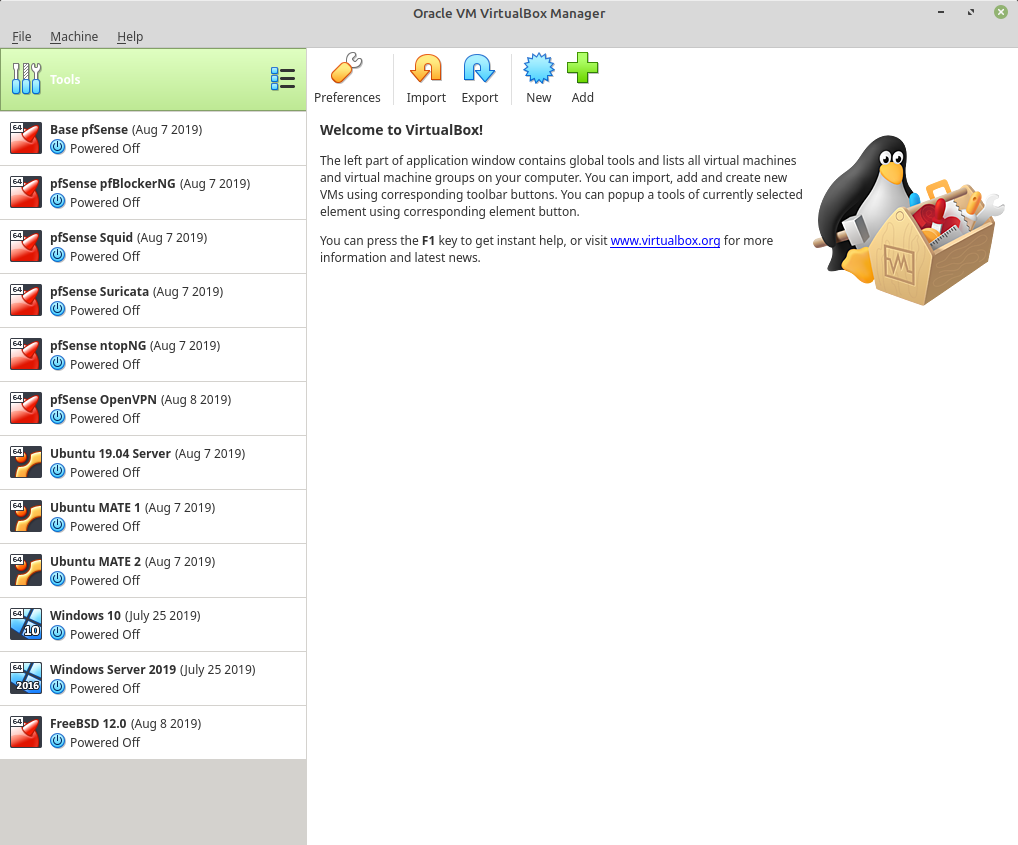
I got tired of recreating specific package configs when trying to help fix a user problem so I decided to spin up a collection of specific pfSense installs, each with a major package installed & configured. I have yet to make a QoS instance and a Captive Portal instance, but those are coming. I have a base install fully configured but basic, and I clone it and then add the necessary package and go from there. There are two Linux clients and one server on the LAN side for client test purposes and port forwards respectively, plus some Windows & FreeBSD systems I'm playing with. Most of the package installs are basic config. Squid is transparent with splice all for URL-filtering with squidguard. OpenVPN has both a server as well as two clients in a VPN gateway group.
-
Today I got around to creating a collection of VMs to be my VPN Site to Site config. 2 pfSense instances with WAN, LAN, DMZ, 2 clients on each LAN, 2 servers on each DMZ. I followed the Netgate guides on creating an IPSec link for the LANs and an OpenVPN link for the DMZs. It all went pretty smoothly, with the one exception of me forgetting to add the WAN rule to allow udp/1194 in.