Unbound versus Bind
-
This post is deleted! -
@gabriiel said in Unbound versus Bind:
Even if you configure unbound to forward requests to upstream DNS servers configured in "System/General Setup", for public domains it will try publicly, completely ignoring any forwards.
Not true at all..
Simple enough to validate.. Just make sure no clients are asking anything else other than pfsense.. Simple enough to do with a firewall rule to only allow dns to pfsense IP..
Then sniff on your wan interface for all dns traffic (upd/tcp 53) Then look at your sniff - is anything other than what you set for forwarder talked too?
-
So just to show how easy this is to validate..
I had a few minutes this afternoon.
So using dnsperf, and sample file that has thousands upon thousands of what amounts to random stuff to query.. Its 239MB in size of just records to query... its used t test dns servers.. You can get info here.
https://www.dns-oarc.net/tools/dnsperfSo created a floating rule to make sure nothing could be doing any queries to any other dns servers while testing. Just simple block to tcp/udp 53 to anything other than pfsense lan IP..
Then set unbound to forward vs resolve - via checkbox, and added 8.8.8.8 to my general setup.
So before you can see that unbound status shows it has lots of different ns it can ask in its cache.. Then after set to forward - it only lists 8.8.8.8 that it can ask for dns.
I then setup a sniff on wan for anything 53, and ran the test tool - let it run for a while - it did over 50K queries.. I had set my sniff to only 10K packets - but you can see the ONLY thing pfsense talked to was 8.8.8.8. This is the only only conversation to any ips on 53 in that sniff.
So not sure what you thought you were doing, but if you set unbound to forward... That is what its going to do, and that is the only thing its going to do..
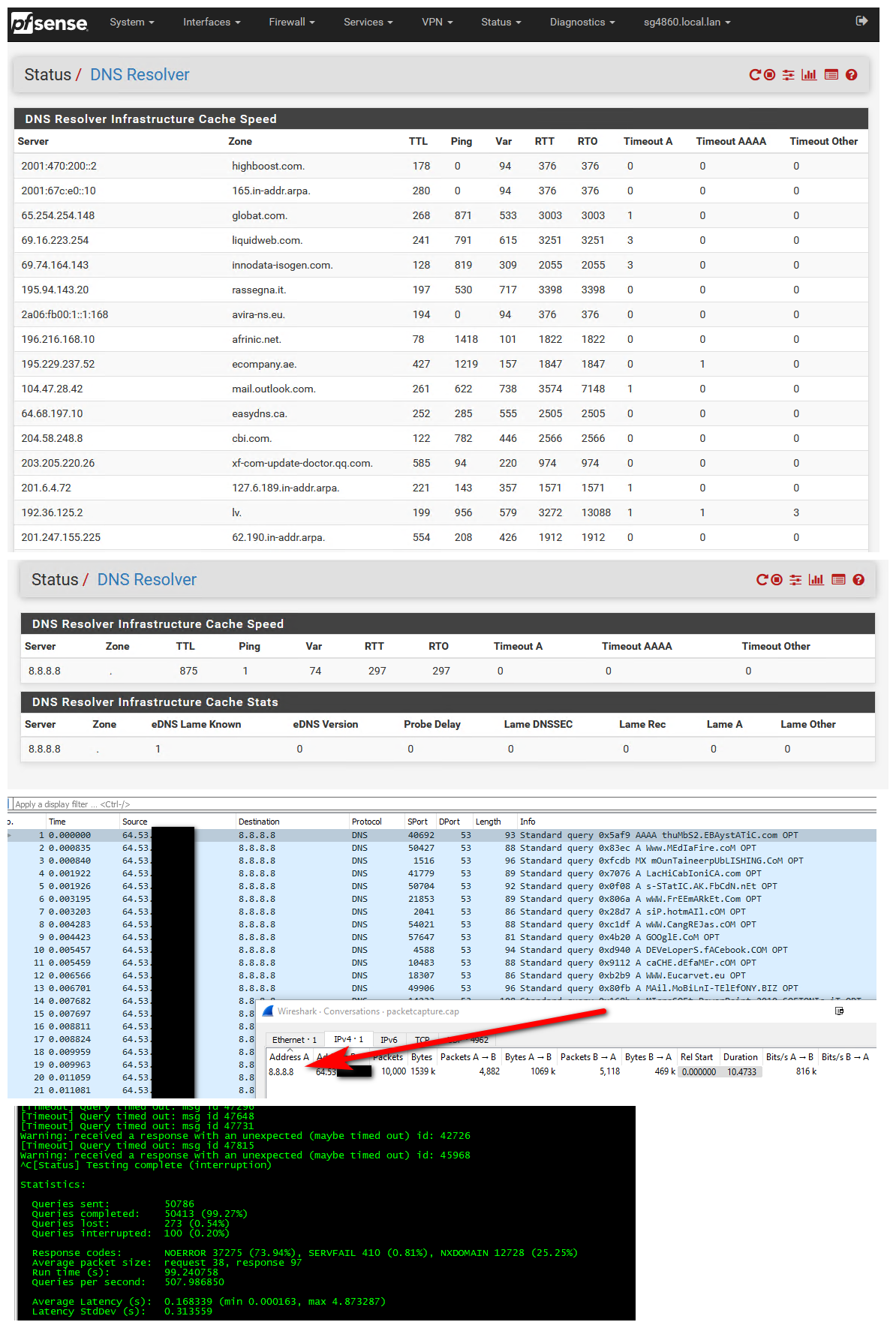
So while bind does have uses for sure.. And there are some stuff you can do with it that are painful if not just impossible to do with unbound.. Unless you need to have an authoritative NS or do zone transfers, etc. unbound is more than powerful enough for most users needs. And is very simple to use - and yet very powerful. And if you tell it to forward, that is what it does ;)
-
This post is deleted! -
@gabriiel said in Unbound versus Bind:
Unbound failed,
If you ask a public dns for something that sends back rfc1918 it is a REBIND, and yeah should freaking fail.. You would have to disable rebind protection, or set that domain to private if you don't want to use rebind protection. https://docs.netgate.com/pfsense/en/latest/dns/dns-rebinding-protections.html
"unexpected" behavior should be investigated so you understand why something happened. Just because you might understand the why doesn't mean its broken or something wrong.
Suggesting clients move too bind, that seems not to have rebind protection on out of the box. Now leaves them open to rebind, etc. Not a good thing at all.
I am a huge fan of bind... Been using it for years and years.. you will get no flame sort of war out of me talking about bind. But you can not just make up stuff and post it.
-
Just delete the thread.
I don't have neither time nor taste to explain this topic into more details.