NAT to Virtual IP
-
Hi ,
Could you please help me with NAT.
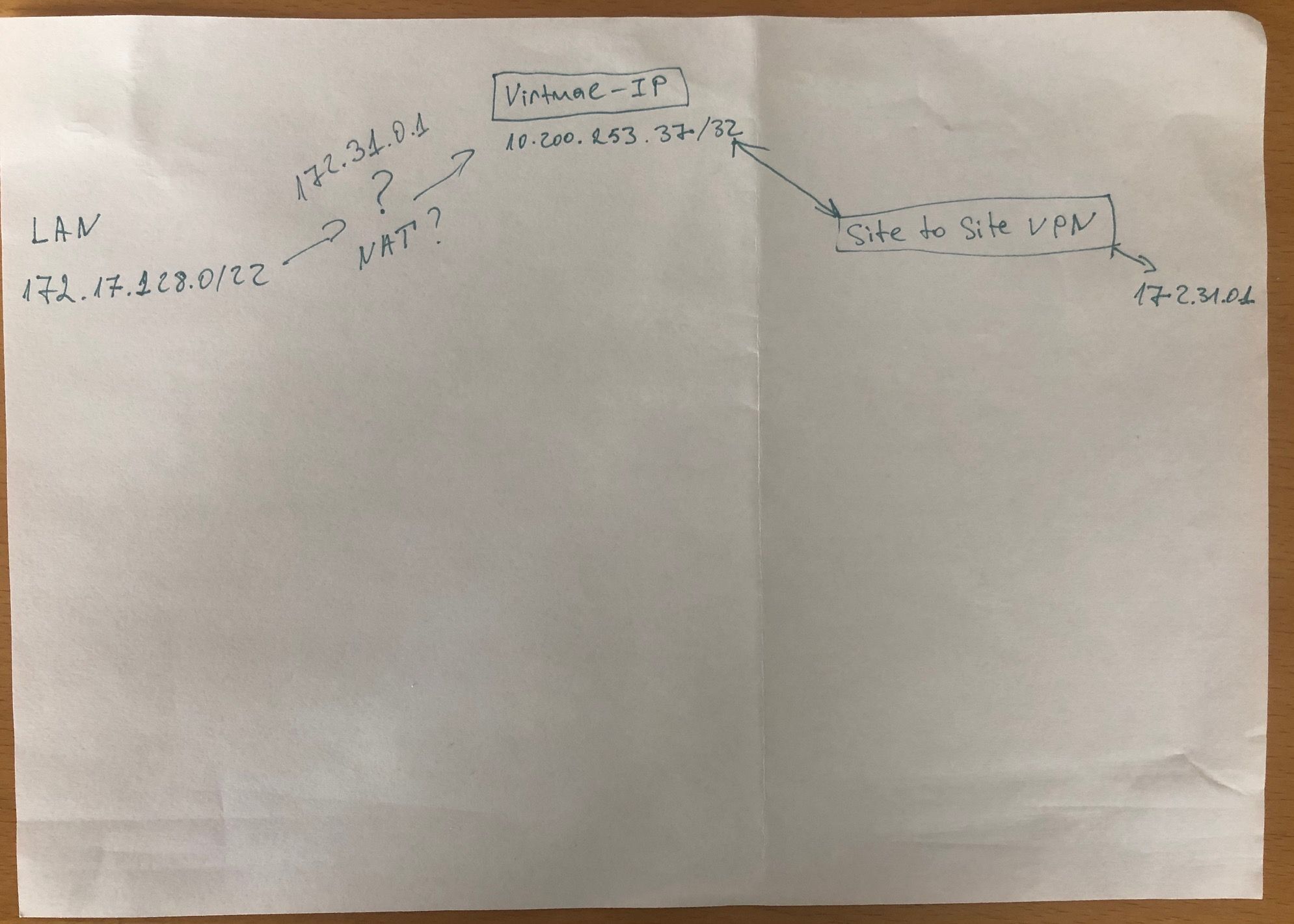
I want to mask my source local ip to my virtual ip and over sito to site vpn to connect to the webserver 172.31.0.1
Thanks!
-
For what possible reason would you want/need to do this?
The only reason to nat in rfc1918 space is overlap, or devices has no gateway, and or circumvention of host firewall, etc..
If you wan to nat, why would not just nat to the vpn IP in the tunnel? Why would you need to create a vip?
-
Hi,
The Webhoster from 172.31.0.1 allow only connections from 10.200.253.37/32. I must mask my local ip 172.17.128.51 to match 10.200.253.37.
-
Well your not going to be able to do it on your end of the tunnel.. How would he know how to get back to you, etc.
your site to site says hey 172.17.128/22 is down that tunnel... Why would the connection on the other end send traffic back down the tunnel to get to 10.200.253.37?
They would need to source nat on their end..
So your trying to circumvent this host firewall? Or is the guy just running the webserver an idiot? If you want to allow other people across a vpn to get to your server.. Then allow the the traffic at the host firewall.. Why would you make people jump through such stupid hoops? Only circumvention would make sense for what your trying to do.
I really don't see how you do it, unless this falls into your tunnel network range, because either way your trying to nat to a vip in a network that is different.. So multiple L3 in the same L2? That is problematic at best, etc. etc..
-
We have till yesterday cisco asa and it worked with the cisco nat
-
The provider will not make sito to site with our local net because of overlap with another clients.
-
pfSense IPsec has NAT at configs on IPsec Phase2 screen, and it must work.
@digitalcomposer its common task...
But avoid VTI, you don't need to configure any vips, etc - this will not work now. Read carefully https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-a-site-to-site-ipsec-vpn.html or look at some videos on YouTube -
Yes, thank you guys. I founded it in Phase 2, so easy :). Now I am definitely away from our small Cisco Asa
-
@digitalcomposer glad to hear
