Need your help will pay 20$: PIA on pfsense Netflix detects proxy
-
Title says it all. I need a step by step with pictures and links. Will Paypal 20$ US if it will work.
thanks
-
to be specific, the vpn must be ON the whole time. i dont need the method where you assign a static ip to the device and route it through WAN (which is what i have rn)
-
Well,
If the WAN IP that was assigned to you by your VPN is on "the list" then there is no work around possible.
"The list" is a list that Netflix uses, they don't like VPN's. -
Geo circumvention via known vpn providers is always going to be a whack-a-mole game.
-
@asphalt3 I've tried dozens of providers and the one I've found out to be rock-solid, no need to change is Windscribe. They have these WINDFLIX (a play on "Netflix", I think) set of servers (i.e; cluster) that they manage themselves and they're on top of it all the time hence it never needs changing. They will also allow you unlimited connections.
The downside is that the service is pretty slow, about 60Mbps max. It's manageable if you connect to several servers at once, but they'd need to be from different locations which would create issues and you'd still wouldn't get the maximum available from your ISP, you'd effectively have tunneled multi-WAN.
I got it because it came in a newsletter promo at USD20 for 3 years, I don't use it because I have a faster provider but the tunnel's been up for ages just waiting. :)
As for the tunnel setup, you have to get an OpenVPN config file from your provider sounds like a pain but most of them have it pretty easy to get in their manual configuration section or something similar to that, open the file with a text editor copy the CA from it beginning on (and containing) the line "-----BEGIN CERTIFICATE-----" up to "-----END CERTIFICATE-----" and add it to pfSense's CAs so you can select it in the OpenVPN client config later you can name it whatever you want, I usually paste it into a blank text document** and save them as whatever.pem so you can open it as a certificate and your OS will show you its information but it's completely not necessary. Afterwards create a new config in VPN>OpenVPN>Clients.
Look in your config file for a section like the CA before, but this should say "-----BEGIN OpenVPN Static key V1-----" and end in "-----END OpenVPN Static key V1-----" and copy it if it exists, it might not be there depending on your provider. Uncheck "Automatically generate a TLS Key" so the box to input it appears.
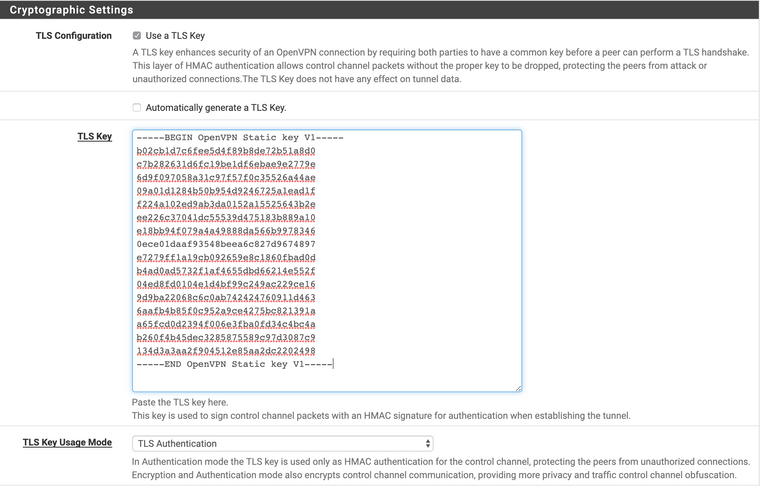
Then move all the way up and trust your gut matching what's on the config file to what's available on pfSense. Not every setting must be set, actually most of them aren't. Each setting has its own line on the config file, if some don't make sense they go all the way down in the advanced box. All providers have a "no-bind" line which is supposed to go in the advanced box but I've found that this setting prevents the tunnels to be brought up. After you're done save it and click the tiny bar graph still on the OpenVPN section:

It'll take you to the tunnel status, if it's up you should see green checkmarks. It should be up before you even get there, it's pretty fast generally. If it's not still on the OpenVPN section click on the log icon, between the bar graph icon and the question mark icon, this will tell you what up and why didn't it come up, you can go to settings on that screen and increase the log display to something like 500 and invert the order so you can make sense of it faster.
When you finally manage to get your tunnel up, pfSense will keep it up all the time, you won't need to worry about it. You're not done though.
Go to Interfaces>Assignments and on the last row select your OpenVPN client (if you attempted configuring one before and you don't know which is the right one, add a description to it VPN>OpenVPN>Clients>[edit]>Description>[save]). When you add the new interface, click its name, it should say something like OPT1,OPT2,etc change the name if you want and enable it by checking the box.
At this point pages will start to load excruciatingly slow, you'll want to kill yourself. That's because dpinger, a pfSense process that pings gateways is not getting an answer, therefore everything else suffers. I don't know why. You can speed things up by going into pfSense, pressing the 8 key for the shell, and typing "killall dpinger". It will recover automatically after a few changes, don't worry. You might actually have to do it over and over because it recovers.
Your provider gives you one IP address per tunnel, even though both sides are likely to be non-routable IP ranges, since the provider is acting like an ISP they don't know what you do with it or what's behind it (i.e; what network range) so you must perform NAT on it (I wish someone would've explained it like that to me when I was first learning). Go to Firewall>NAT>Outbound. Set it to either hybrid or manual, your current config will be automatically added as individual rules if you set it to manual, so you won't be offline just yet--Oh yeah, I should've begun with "before you begin, make a backup of your system..." my bad!
Then allow OpenVPN traffic, Firewall>Rules>OpenVPN>Add a free for all type of rule here, on protocol IPv4, which is not recommended but it'll get you there faster. These tab is like a limbo zone where all other OpenVPN clients and servers pass through before they make it to their own tabs...or something like that. Otherwise known as Group Interface. Usually you don't want to mess with these until you're pretty advanced as a user or network admin, I'm not there yet myself :).
By now your system should be ready to redirect traffic, if I didn't forget anything, I'm sure someone will point it out. Go to Firewall>Rules> and select your main interface, usually "LAN" or do this for the interfaces you want to use the tunnel; edit the existing any to any rule go into its advanced section and change the gateway to the interface name of your OpenVPN client. Save it and you're done.
You might need to add a rule before (above) the existing any-to-any rule you edited just now, but with destination to your pfSense box (interface address) and without a gateway set if you are using services on pfSense such as FreeRADIUS, DNS or whatever, otherwise the packets will be sent right out to your VPN service provider and discarded since they won't know what to do with them.
https://www.netgate.com/resources/ <- Look for OpenVPN
** Use Notepad or Notepad++ on Windows. On macOS use TextWrangler or TextEdit but press Shift+Command+T to make it plain text.
-
@Gertjan well i change the gateway to WAN instead of default which is for the VPN when I do the static ip bullshit
-
@johnpoz @z71prix said in Alarming WAN Leaking using fast.com (Resolved):
Thank you KOM for trying. Really strange that everything on mine seems to be working other than a few sites seeing my real IP. I'll provide details. I followed these instructions. https://nordvpn.com/tutorials/pfsense/pfsense-openvpn/
Disregard looks like it's ok after all. fast.com uses netflix servers. I have netflix passed through VPN. Also www.myipaddress.com uses amazon servers, I allow amazon to pass. Looks like everything is ok. Thank you
seems like this guy was able to do it
-
@skilledinept Unfortunately Ive already payed for PIA and have gigabyte internet Thanks for your answer tho
-
What @Gertjan and @johnpoz are trying to say is Netflix hates VPN providers (in a manner of speaking). They are constantly searching for VPN provider IP network blocks and then blacklisting those IP addresses from using the Netflix service. Netflix does this because they have contractual obligations for the content they stream that prohibit certain content from being shown in particular geographical areas. They know some users attempt using a VPN service to get around this contractual obligation that Netflix has. Should Netflix turn a blind eye to this circumvention attempt, the folks they buy content from will either stop selling to Netflix or might even sue them. Thus Netflix has a team whose mission is to identify VPN network providers and block them, and thus their customers, from accessing Netflix content. Other streaming providers do the same.
So whether or not Netflix works for your VPN setup is mainly dependent on two things. First, has Netflix found the VPN exit node IP subnet for your provider (or more specifically, for the particular exit node your provider has assigned to you)? If the answer is "yes", then Netflix is blocked for you when using the VPN. And that leads to the second dependency. You would need a subscription to a VPN provider who was willing to continue playing the whack-a-mole game with Netflix by swapping around the various exit node IP networks they assign to their users. However, in the end, even this is a losing game as eventually Netflix will find all of the provider's networks and block them.
So you might have your Netflix never work from the start, work fine for some period of time and then break, or if you have a provider such as user @skilledinept mentioned that actively seeks to counter moves by Netflix to block access, then your Netflix will work a while, fail, then start working again for some time, fail ... and rinse and repeat. However, it is likely to eventually fail for good once Netflix finds all of the VPN provider's IP networks.
So the best thing to do is use policy routing on pfSense and route your traffic from streaming appliances to your normal WAN gateway (the one your ISP gives you) and bypass the VPN for streaming traffic. There are several ways to do this. Search this forum and you will find those suggestions. I know you said you didn't want to do that, but it really is the best way to have dependable streaming.
-
Just wondering if anyone has tried using their own VPN from a VPS like linode, AWS or similar?
-
datacenter IP ranges are usually blocked by Netflix as well IME.
-
I subscribe to a few service providers that advertise Netflix working over their service, and it does work using their app.
Over pfsense it does not.
Best luck, I use the over wan method
-
i use expressvpn and work great for netflix install on pfsense box
-
@yepitro1986 unfortunately cant cancel my PIA subscription.
BUMP
-
https://www.reddit.com/r/PFSENSE/comments/4lcfdf/netflix_to_wan_not_opt1vpn/d3mgta4/
This guy got it and it works for me too. I'm not sure how his second approach works; I only did the first.
On the same computer, I am now able to go to ipchicken.com and see my VPN IP address but Prime Videos doesn't give me a VPN warning anymore.
It's somewhat related to: https://forum.netgate.com/topic/96559/routing-netflix-through-wan-and-else-through-vpn/4
-
He is just policy routing, he routes netflix/amazon out his normal wan and other traffic out his vpn.. Duh! Nobody ever said this wouldn't work.. That is how normally do it, netflix not going to block your normal wan IP - they block vpns..
-
@johnpoz said in Need your help will pay 20$: PIA on pfsense Netflix detects proxy:
He is just policy routing, he routes netflix/amazon out his normal wan and other traffic out his vpn.. Duh! Nobody ever said this wouldn't work.. That is how normally do it, netflix not going to block your normal wan IP - they block vpns..
Guess I misunderstood the ask. I thought he wanted to use his ISP for Netflix and everything else over VPN.
-
That what we are suggesting he do ;)
He hasn't been back. bmeeks suggested he just policy route some 22 days ago.
-
Also if he insists on his PIA account he paid for (and obviously didn't read the other posts telling him it won't work unless PIA has a network Netflix didn't already block), then he'll be stuck with his problem.

-
@JeGr said in Need your help will pay 20$: PIA on pfsense Netflix detects proxy:
Also if he insists on his PIA account he paid for (and obviously didn't read the other posts telling him it won't work unless PIA has a network Netflix didn't already block), then he'll be stuck with his problem.

Well I don’t wanna compromise my gigabyte speed using a slower vpn neither lose money on a vpn I already purchased before starting this thread