Unable to route between VLANs
-
I have a netgate SG-2440. The Wan interface is DHCP client to my ISP. The LAN interface has been assigned to the default VLAN 1. OPT6 to VLAN 6 The cable is connected to a CISCO SG-200 managed switch. The port on the switch is a trunking port and is part of all VLANS. (same physical interface as LAN). I have set up the firewall rules to allow all traffic. Everything works as I expect. I am able to connect to the internet from all VLANs etc. I am able to connect to a host on VLAN 6 from a Host on VLAN 1. I cannot go the other way. Connect from a host on VLAN 6 to a host on VLAN 1 At first I thought I had a firewall issue. In trouble shooting I did a traceroute from the VLAN 6 host to the VLAN 1 host. The traceroute showed the packet going out through the WAN interface. Apparently, I've messed something up with the routing although I can't image what.
-
i suppose you set the sg-200 as a layer 2 ?
can you post screenshot of what you have for opt6 ? -
Double-check your subnet masks. The interface static IP configuration has a habit of selecting /32 if you aren't careful.
-
@kiokoman
Hope I'm posting the screen-shot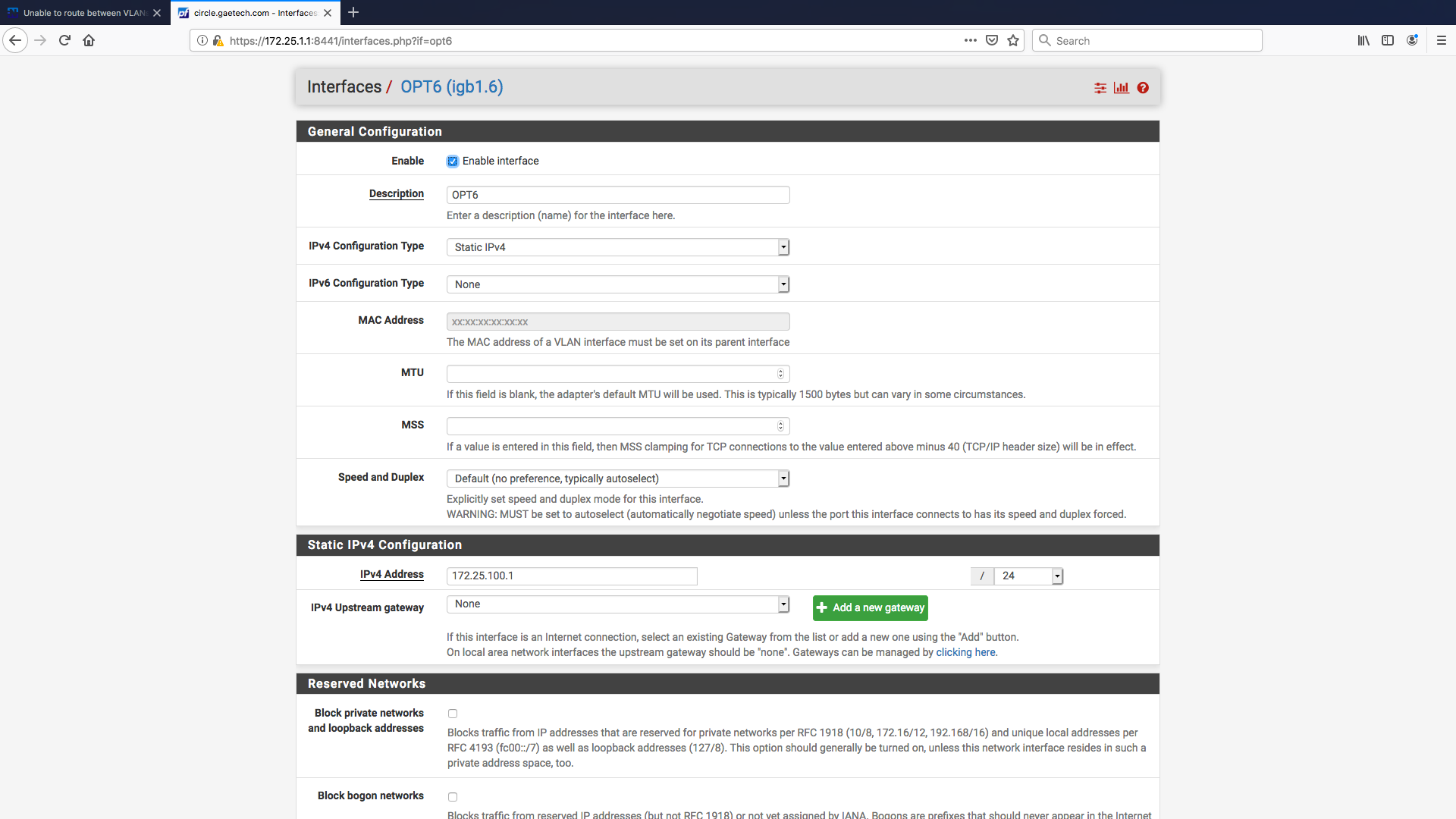 correctly
correctly -
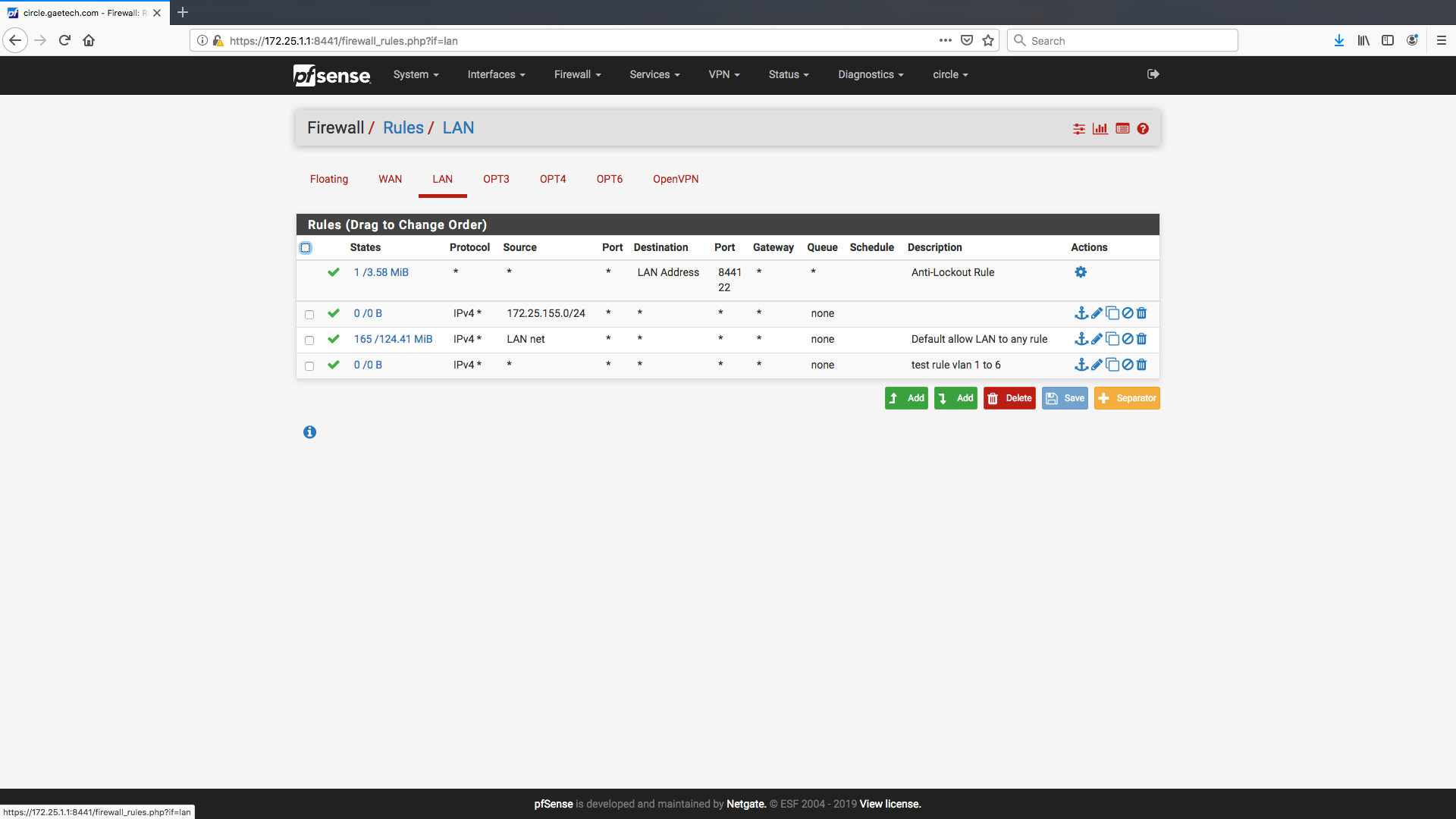
@kiokoman
And from the SG200: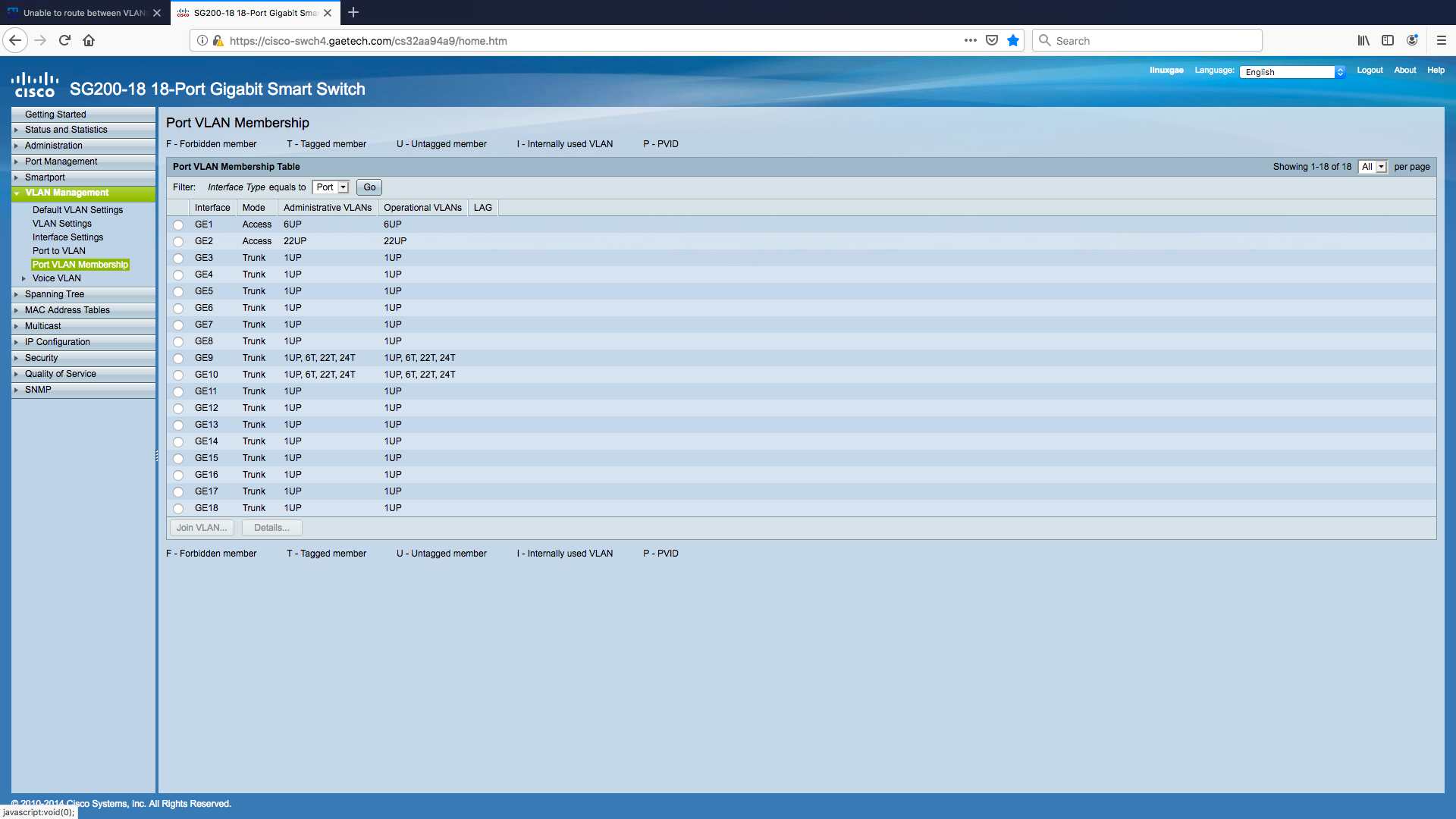
-
So far it looks good, did you add any firewall rules on the OPT 6 Interface to allow access to VLAN 1 ?
-
this is how i've set mine as a layer 2 only
on pfsense a vlan interface with id 20 and one with id 30
vlan 20 iot on port ge1
vlan 30 access point on port ge5
all other port are vlan1
XG2 trunk to pfsense
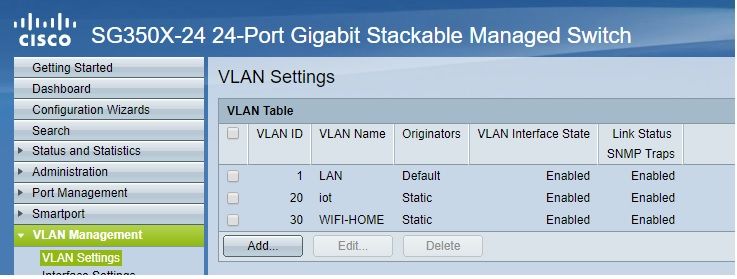
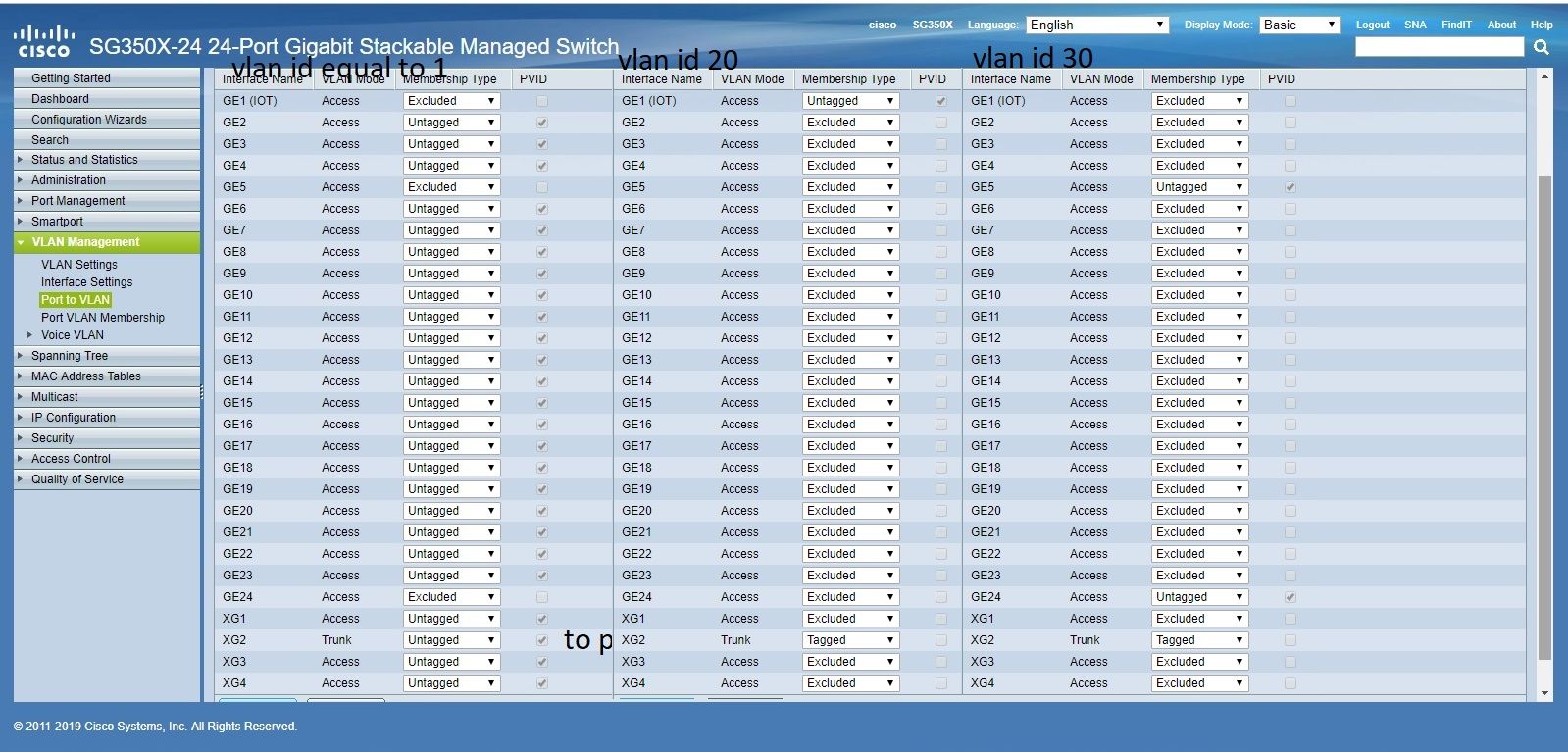
-
@awebster
BTW. Thanks for looking at this for me.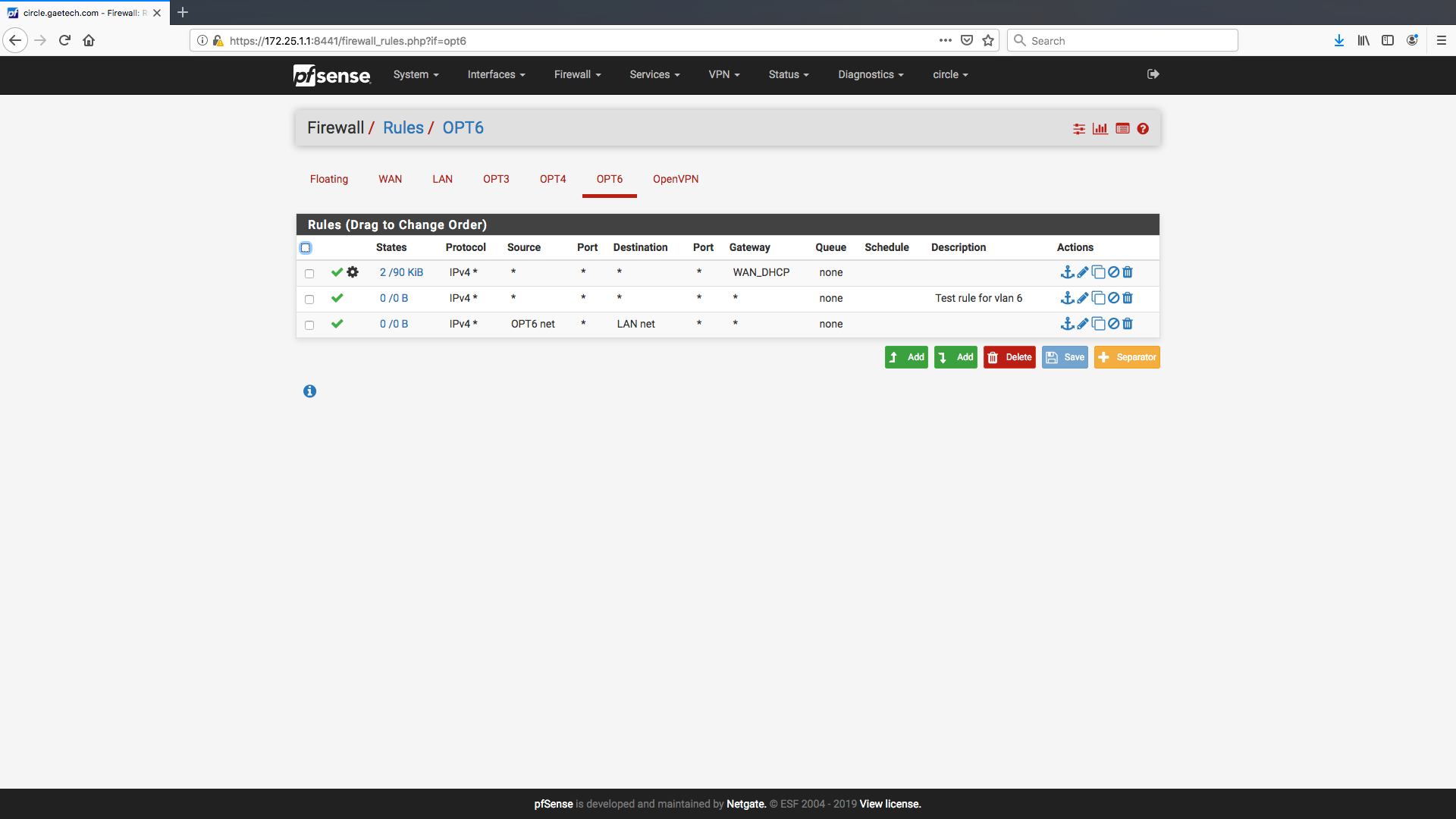
I realize that some rules are essentially unnecessary. I was just trying everything.
-
@kiokoman
I follow you until XG2. -
@linuxgae Your rule order in OPT6 is wrong.
The clue is the first column showing States. You can see 2/ 90KB of traffic, but the other 2 rules have 0 states / 0 Bytes of traffic, so those rules are never used, this is because your first rule is FORCING all the traffic out WAN_DHCP which you have set as the gateway, regardless of the destination IP
This corresponds exactly to the problem you are describing.
To fix it:
Move the OPT6 -> LAN rule to the top.
FYI: You don't usually need to set the gateway in the rule, the firewall will figure that out on its own through the routing table. Forcing the gateway is only used if you want it to ignore the routing table and use that interface specifically. -
Thanks so much.
I would never would have figured this out myself.
I used the out-of-box rules generated for LAN as a template. I never would have guessed that firewall rules would affect
routing.
Again, thanks for the help. -
@kiokoman 350X - very jealous.. Only SG300 here..
-

i was in need of a new switch at home, amazon eu was full of refurbished sg350x for the same price of a sg300-20 as it was for home i took the risk -
Nice! You have any plans of stacking it? Any play time with RSPAN? Prob not if you only have the 1..
-
no plan to stack for the moment, i'm using only 10 port and i have nothing so important to justify another 350 $
I've only had it for 10 days. i'm still learning all it's functions -
This post is deleted! -
SPAN - switch port analyzer..
@johnpoz what would you put as span, do you have it configured on your sg300 ?
something like a machine with wireshark ? i have a spare raspi ...
-
No span is local, talking about RSPAN - this was added in the 350 line.
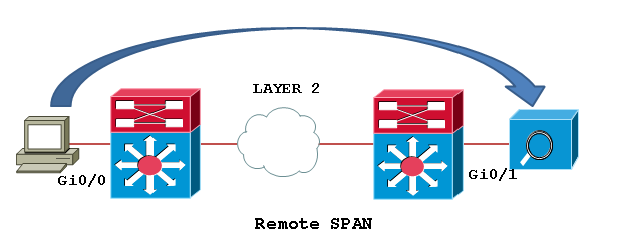
I have done local span on my sg300-28 but would of been cool to be able to span a port that is in my av cabinet on a sg300-10 to a port on my -28 which is on my desk next to me ;)
Would need 2nd switch that also supports rspan - but could be a very useful feature.
-
yup there is that option but obviusly i can't try it