Intermittent connection issue
-
@johnpoz said in Intermittent connection issue:
The different with dnsmasq and unbound for forwarding is dnsmasq out of the box forwards to ALL of the forwarders you have set at the same time, and uses just uses the first answer. I don't think you can tell unbound to do that.. Would have to check the unbound docs - but there is no way to set that in the gui of pfsense. This can be good for when you have bad peering isp or issues talking via some paths, etc.
Well restarting unbound never helps because it flushes your cache. But you do have a lot of timeouts you showed - so something not great with your isp either which could be problems.
For all we know your isp connections has gotten better, and has zero to do with unbound restarting.
Again when you have issues with dns - you can not just assume the problem is X, you need to troubleshoot the exact issue your seeing... Not just dns not working sometimes.. Pick something that didn't work and find out why.. Are you still seeing a lot of timeouts in your infra info?
You can also make sure you setup prefetch with unbound, this can help with problematic issues because it will look up stuff in the background before the ttl expire and it flushes out of the cache. Also setting serve 0 ttl can really help as well. Since now even if the cache expired, it would serve up the last entry when client asks for it - and then look it up in the background again.
I see. I thought both dnsmasq and unbound forwarding works that way.
For some reason, I have 0 timeouts now. The one I showed you with a lot of timeouts was when I had DHCP and OpenVPN client registrations in unbound enabled.
Yeah, that's possible. It could be that the ISP connection has gotten better and is another coincidence. I really don't know but I was trying to pinpoint the issue to one specific module on my whole infra but I still can't isolate it.
Ok, so I'll enable these three, I guess:
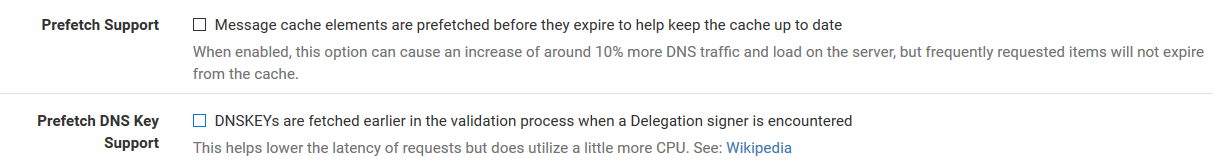
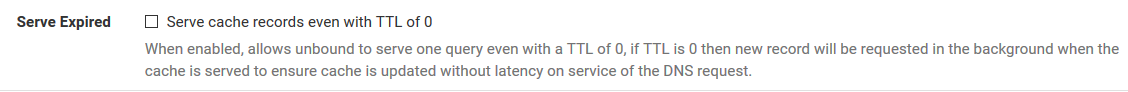
How does the Serve Expired setting help though? So if the record has a TTL of already, it will still serve it to the client and update the cache in the background. What if the record is really no longer valid, how would serving an invalid record to the client help? I'm trying to understand how that setting works.
-
Nevermind! I enabled those three options for both my infras and this problematic infra started getting DNS timeouts again! Tried to ping 8.8.8.8 from Diagnostics -> Ping using the WAN interface and 100% packet loss. When I think that one isolation step solves the problem, it bites me in the back after a few days of trying it. This is insane.
-
And lets go over this again - restarting unbound to change a feature has ZERO to do you with pinging anything by IP.. But if your having packetloss then resolving anything or even forwarding is going to be problematic at best.
-
@johnpoz said in Intermittent connection issue:
And lets go over this again - restarting unbound to change a feature has ZERO to do you with pinging anything by IP.. But if your having packetloss then resolving anything or even forwarding is going to be problematic at best.
Yes, I completely agree. I just stated what I did and observed, I didn't say that the unbound restart directly caused me having packet losses.
I still don't get it though. I don't know what to tell these ISP people because all along I still believe that the issue is with their network. I just can't prove it.
-
@kevindd992002, this is a very interesting thread. I've very similar experience with my pfsense. Some of my testing could give input to further investigations.
The problem is almost identical to what you have described. Occationally I cannot access webpages. This typically happens first time starting to browse Internet. It is any type of website, it could be a frequently accessed site or an one time visit. But It also occurs in the middle of when I'm browsing e.g. after a break.
But if I open up several tabs and start to access different websites, and constantly refresh and try to access them I finally start to connect to one or several of the websites. However there could still be one of them that is not loading.For e.g. when watching Netflix I could have and issue at the beginning when I start loading the first movie or even connecting to Netflix. However once the movie has started I cannot recall I have ever experienced a loading or connection issues. The same is true for Citrix when logging on to a remote desktop. I could have issues to connect to begin with but once connected I cannot recall any loading/connection issues.
I replaced my old Netgear SRX5308 with pfSense on a box from Protecli (amd64) Intel Celeron CPU J3160 @ 1.60GHz 4 CPUs: 1 package x 4 core, AES-NI CPU Crypto: Yes (active).
The old SRX5308 never had any connection issues however it was slow and capped my fiber connection. I have installed pfSense 3 times to make sure I have a default installation. Last 3 months I have been searching and reading Internet for trouble shoooting tips. I have tested several tips and none have solved the issue so far. -
I've had spare time and proceeded with the reinstallation of pfsense from scratch and since then I had 0 problems with unbound and no packet loss, so far. I'm not entirely sure if the issue was caused by some bug in pfsense (doubtful) but like @johnpoz said it could be just my ISP fixing something in the backend and was just coincidental to when I reinstalled pfsense. So far so good though, I'll definitely post back if I encounter the same issue (which I certainly hope I won't).
-
@johnpoz said in Intermittent connection issue:
The different with dnsmasq and unbound for forwarding is dnsmasq out of the box forwards to ALL of the forwarders you have set at the same time, and uses just uses the first answer. I don't think you can tell unbound to do that.. Would have to check the unbound docs - but there is no way to set that in the gui of pfsense. This can be good for when you have bad peering isp or issues talking via some paths, etc.
Well restarting unbound never helps because it flushes your cache. But you do have a lot of timeouts you showed - so something not great with your isp either which could be problems.
For all we know your isp connections has gotten better, and has zero to do with unbound restarting.
Again when you have issues with dns - you can not just assume the problem is X, you need to troubleshoot the exact issue your seeing... Not just dns not working sometimes.. Pick something that didn't work and find out why.. Are you still seeing a lot of timeouts in your infra info?
You can also make sure you setup prefetch with unbound, this can help with problematic issues because it will look up stuff in the background before the ttl expire and it flushes out of the cache. Also setting serve 0 ttl can really help as well. Since now even if the cache expired, it would serve up the last entry when client asks for it - and then look it up in the background again.
Does this mean that unbound, by default, when set to forwarding mode queries the DNS servers you set in General sequentially and that you cannot change this behavior?
-
@kevindd992002 and @johnpoz
This is my understanding from the documentation. "unbound will use the system DNS servers from System > General Setup or those received from a dynamic WAN, rather than using the root servers directly"When I changed my DNS resolver setting to "Enable Forwarding Mode" most of my intermittent connection issues have disappeared. Sometimes I still have to wait a sec or two before the webpage loads completely, but In general the pages load immediately and there are no long periods of total non-connection.
I have not tried using the DNS Forwarder (dnsmasq). The documentation on “DNS Query Forwarding” mentions that DNSSEC need to be disabled but I have not done this. Maybe it works for me as I did check that the DNS servers I choose were supporting DNSSEC.
-
I don't see any GUI setting for DNSSEC in dnsmasq so I'm not sure if it's supported. But yeah, if my upstream DNS server is just the ISP modem anyway (double NAT config), I won't use the "simultaneous query of DNS servers" capability of dnsmasq. In that case, would staying with unbound and forwarding be advisable since it has DNSSEC support and other settings that you can customize?
-
@johnpoz Do you still have any ideas on my question?
-
Just an update to this issue:
My ISP had my account migrated to their VLAN for static (public) IP configs for two weeks testing and I had 0 problems with unbound (resolver). As soon as they transferred me back to using dynamic IP with CGNAT, the issue went back right away when using unbound (resolver). I had to go back to using unbound (forwarder) again as a workaround.
They wanted me to switch over to using static IP but to do that I would have to upgrade my subscription with them and pay the extra static IP subscription. That won't happen. I'm trying to fight with them now and convince them that the issue is with their dynamic IP network.
-
Not being able to use the default resolver, unbound, in resolving mode means a severe connection problem.
Very standard DNS data traffic is one of the basic Internet minimal requirements. -
Exactly. That's what I've been telling them. DNS traffic is nothing special. It's like they're forcing their customers to only forward DNS requests.
-
@kevindd992002 said in Intermittent connection issue:
It's like they're forcing their customers
They discovered, like many before, that that info is worth a max. People are using already themself's massively the "let bring everything to 8.8.8.8".
And lets face it : if you are an ISP, and you have to make this deal with nearby Google's data centre to invest in a very costly 50 / 50 % fiber POP between the Google data centre and the ISP centre (ISP users consume a LOT of Youtube traffic !!) then what should this ISP do ? They cash cash out or they 'make this another deal'.
So, yes, DNS is manly 'visible' to they can grab it, and do what they want with it.Btw : it's the technical point of views that interests me here. I don't care what Google does, neither my ISP. They can have it, I don't care.
-
Get a different ISP? Clearly you pointed out them that their carrier grade nat is broken..
-
@Gertjan said in Intermittent connection issue:
@kevindd992002 said in Intermittent connection issue:
It's like they're forcing their customers
They discovered, like many before, that that info is worth a max. People are using already themself's massively the "let bring everything to 8.8.8.8".
And lets face it : if you are an ISP, and you have to make this deal with nearby Google's data centre to invest in a very costly 50 / 50 % fiber POP between the Google data centre and the ISP centre (ISP users consume a LOT of Youtube traffic !!) then what should this ISP do ? They cash cash out or they 'make this another deal'.
So, yes, DNS is manly 'visible' to they can grab it, and do what they want with it.Btw : it's the technical point of views that interests me here. I don't care what Google does, neither my ISP. They can have it, I don't care.
But I don't forward to 8.8.8.8. I'm trying to resolve. Sorry, not sure what you mean?
@johnpoz said in Intermittent connection issue:
Get a different ISP? Clearly you pointed out them that their carrier grade nat is broken..
I can't, I'm still locked in with them (contract) and I have a point-to-point VPN connection with my other house that's using the same ISP (so best connection quality).
-
@kevindd992002 said in Intermittent connection issue:
But I don't forward to 8.8.8.8
8.8.8 is just an example. And I was talking about 8.8.8.8, choosen by your ISP, the DNs where they are forwarding to.
@kevindd992002 said in Intermittent connection issue:
I had to go back to using unbound (forwarder) again as a workaround.
To who ?
Sending DNS request to
Hostname IP address IPv4 / IPv6 Organization a.root-servers.net 198.41.0.4, 2001:503:ba3e::2:30 VeriSign, Inc. b.root-servers.net 199.9.14.201, 2001:500:200::b University of Southern California (ISI) c.root-servers.net 192.33.4.12, 2001:500:2::c Cogent Communications d.root-servers.net 199.7.91.13, 2001:500:2d::d University of Maryland e.root-servers.net 192.203.230.10, 2001:500:a8::e NASA f.root-servers.net 192.5.5.241, 2001:500:2f::f Internet Systems Consortium, Inc. g.root-servers.net 192.112.36.4, 2001:500:12::d0d US Department of Defense (NIC) h.root-servers.net 198.97.190.53, 2001:500:1::53 US Army (Research Lab) i.root-servers.net 192.36.148.17, 2001:7fe::53 Netnod j.root-servers.net 192.58.128.30, 2001:503:c27::2:30 VeriSign, Inc. k.root-servers.net 193.0.14.129, 2001:7fd::1 RIPE NCC l.root-servers.net 199.7.83.42, 2001:500:9f::42 ICANN m.root-servers.net 202.12.27.33, 2001:dc3::35 WIDE Projector, the DNS you choose to forward to, what is the difference ? Yet you said that the first 13 are not possible.
Read, for example https://securitytrails.com/blog/dns-root-servers and understand something is very wrong.
Reset pfSense to default, and see if it works. If not, take a look at your ISP contract.
@kevindd992002 said in Intermittent connection issue:
I have a point-to-point VPN connection
Aha. That changes a lot.
Use pfSense with default settings (again !) and the resolver will work.
Adding a VPN and suddenly it stops. That make the solution rather simple. : remove things that break things.
Or setup correctly the new things. -
@Gertjan said in Intermittent connection issue:
@kevindd992002 said in Intermittent connection issue:
But I don't forward to 8.8.8.8
8.8.8 is just an example. And I was talking about 8.8.8.8, choosen by your ISP, the DNs where they are forwarding to.
@kevindd992002 said in Intermittent connection issue:
I had to go back to using unbound (forwarder) again as a workaround.
To who ?
Sending DNS request to
Hostname IP address IPv4 / IPv6 Organization a.root-servers.net 198.41.0.4, 2001:503:ba3e::2:30 VeriSign, Inc. b.root-servers.net 199.9.14.201, 2001:500:200::b University of Southern California (ISI) c.root-servers.net 192.33.4.12, 2001:500:2::c Cogent Communications d.root-servers.net 199.7.91.13, 2001:500:2d::d University of Maryland e.root-servers.net 192.203.230.10, 2001:500:a8::e NASA f.root-servers.net 192.5.5.241, 2001:500:2f::f Internet Systems Consortium, Inc. g.root-servers.net 192.112.36.4, 2001:500:12::d0d US Department of Defense (NIC) h.root-servers.net 198.97.190.53, 2001:500:1::53 US Army (Research Lab) i.root-servers.net 192.36.148.17, 2001:7fe::53 Netnod j.root-servers.net 192.58.128.30, 2001:503:c27::2:30 VeriSign, Inc. k.root-servers.net 193.0.14.129, 2001:7fd::1 RIPE NCC l.root-servers.net 199.7.83.42, 2001:500:9f::42 ICANN m.root-servers.net 202.12.27.33, 2001:dc3::35 WIDE Projector, the DNS you choose to forward to, what is the difference ? Yet you said that the first 13 are not possible.
Read, for example https://securitytrails.com/blog/dns-root-serversand understand something is very wrong.
Reset pfSense to default, and see if it works. If not, take a look at your ISP contract.
@kevindd992002 said in Intermittent connection issue:
I have a point-to-point VPN connection
Aha. That changes a lot.
Use pfSense with default settings (again !) and the resolver will work.
Adding a VPN and suddenly it stops. That make the solution rather simple. : remove things that break things.
Or setup correctly the new things.I'm currently forwarding to another local ISP's DNS servers that's known to be more stable. This works fine. As soon as I use resolver (querying against root hints servers), I get random drops. Are you saying ISP themselves just forward to Google for example? I was under the impression that they act as a resolver.
The link you gave is not found.
If you remember, we've been over the resetting of things to defaults :) It doesn't work. What I've been able to deduce/conclude is what I've explained just recently (resolver vs forwarder).
Not sure how a point to point VPN connection affects this? DNS traffic isn't routing through the tunnel. Also, like I said I did try pfsense with default settings already, to no avail. With a static IP from the ISP, everything works as expected. So there's really something wrong with their dynamic IP VLAN.
-
@kevindd992002 said in Intermittent connection issue:
I was under the impression that they act as a resolver.
You have no idea what they do.. They could resolve, they could forward... You threw your dns over the fence to them - what they do with it is out of your control... You just hope they give you back an answer, and you trust them to give you good info... They could give you whatever they want..
This is one of the big advantages to resolving - you control the dns.. You ask the authoritative NS directly... Not just trust someone else to have the right answer.
For all you know they forward, and the person they forward to forwards ;) Yes at some point there has to be a resolver.. But it could be a couple of forwarders in there for sure..
-
@johnpoz said in Intermittent connection issue:
@kevindd992002 said in Intermittent connection issue:
I was under the impression that they act as a resolver.
You have no idea what they do.. They could resolve, they could forward... You threw your dns over the fence to them - what they do with it is out of your control... You just hope they give you back an answer, and you trust them to give you good info... They could give you whatever they want..
This is one of the big advantages to resolving - you control the dns.. You ask the authoritative NS directly... Not just trust someone else to have the right answer.
For all you know they forward, and the person they forward to forwards ;) Yes at some point there has to be a resolver.. But it could be a couple of forwarders in there for sure..
Exactly! I want to have my own resolver. I told them that I don't want to rely on their DNS servers.