IPSEC with outbound NAT + 1:1 NAT
-
I have 2 sites (with pfsense) connected via an ipsec tunnel:
Tunnel works fine without SNAT/DNAT, but "shit" happens when i configure SNAT /
DNAT.Site 1:
Machine 1: 172.20.74.31
GW 1 (Pfsense)Site 2:
GW2 Pfense has notably an interface 10.45.226.1
Machine 2 : 10.45.226.3From Machine 1, to ping Machine 2 on this interface, i ping 10.100.45.2
I use DNAT
1:1 NAT to translate 10.100.45.2 to 10.45.226.3
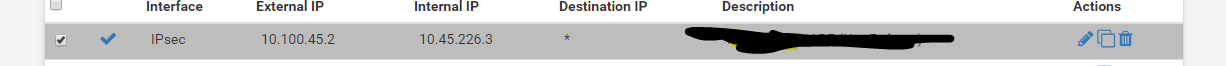
I use SNAT (outbound NAT) to translate 172.20.0.0/16 to GW Interace on the right lan.
What happens :
Packets get routed from Machine 1 to Machine 2, i can see them, and i can see Machine 2 reply. (with tcpdump)
If i packet capture on GW 2 :Ipsec Interface :
- I see the echo request from 172.20.74.31 to 10.100.45.2
LAN interface:
- I see the echo request AND the reply from GW1 Iface to 10.45.226.3
WAN Interface (which should do .... with my setup) :
- I see the reply from 10.100.45.2 to 172.20.74.31
Why does my reply packets go through WAN interface instead of using the normal route.
- WAN is indeed setup as default GW, but i assume it knows from phase2/enc domain to define a correct return route ? no ?
- I don't have any static rules.
- I ve set the FW in allow all by default.
Any clues ?
-
Few complements (i haven't have solved the issue)
I see the following statesvtnet4 icmp 10.45.226.1:15026 (172.20.74.31:47548) -> 10.45.226.3:15026 0:0
enc0 icmp 10.45.226.3:47548 (10.100.45.2:47548) <- 172.20.74.31:47548 0:0where enc0 is ipsec i assume
and vtnet4 is the LAN interface.This issue is driving me mad, i can provide schemes, and answer to anyone willing to help.