1:1 NAT failing.
-
I have the following;
extra public 69.63.67.141
WAN ip is 69.63.67.142.
LAN ip is 10.100.10.116
I created virtual IP-(IP alias)
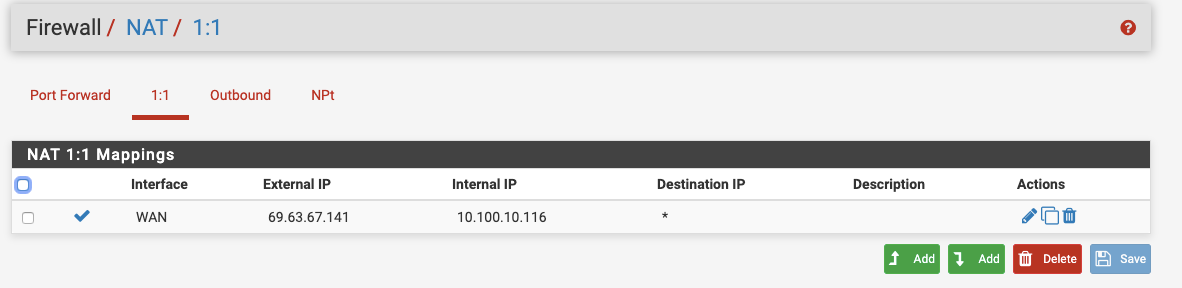
created 1:1 NAT - external as 69.63.67.141 and internal as 10.100.10.116
I created a rule on the WAN interface to allow SSH but it doesn't go through.
I have rebooted a couple of times but with no success.
One thing I have noticed, whenever I create NAT, internet is lost on 10.100.10.116 host. -
You should allow the NAT rule creation to auto-create the WAN firewall rule. Did you do this, or did you manually create the WAN rule, like I think I understand from your post above.
It's at the very bottom of the NAT rule creation screen. Start over, delete the WAN rule you made, and delete the NAT rule you created. Make a new NAT rule, let the process auto-create the WAN rule, and you should be good to go.
If that still doesn't work, walk carefully thru all of these NAT port forward troubleshooting steps.
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.html
And, finally, if that doesn't work, you need to post screenshots of your NAT rules and WAN firewall rules.
Jeff
-
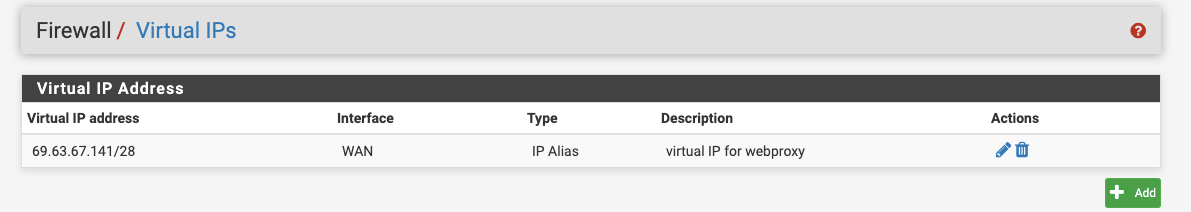
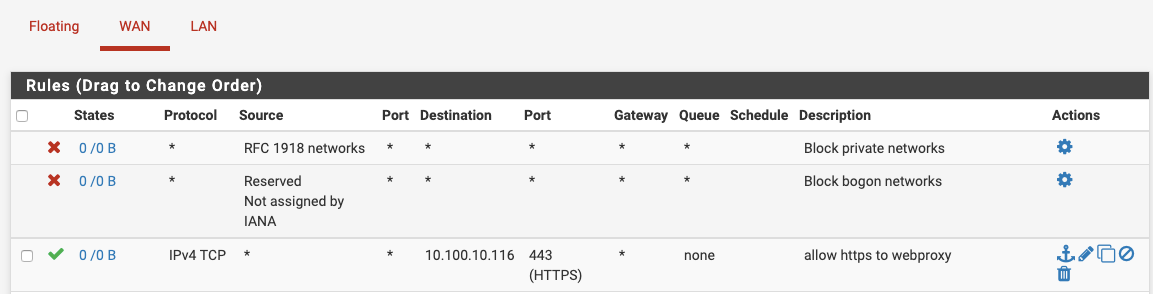
Thanks for your prompt support. Below are the screenshots
virtual IP
1:1 NAT
Rules
-
@akuma1x 1:1 NAT does not auto-create rules. If it did, its only choices would be "all traffic" or "no traffic" without further input from the administrator, which the administrator provides by manually creating firewall rules to the inside address on WAN.
@ivanupsons Note that your WAN rule has logged no hits. Are you certain the 69.63.67.141 address on the outside even works? Can you use Diagnostics > Ping and ping out to, say, 8.8.8.8 using that VIP as a source address?
Are you certain that inbound connections to 69.63.67.141:443 even arrive on WAN?
-
@Derelict I apologize, you're right.
I totally missed the "1:1 NAT" topic section we are in. My bad...
Jeff
-
@ivanupsons Do you actually have that "extra public" IP address 69.63.67.141 routed to you from your ISP? That would be when you would use VIP (virtual IP address) in this case.
Jeff
-
There is a difference between routed to you and on the WAN interface but either provisioning would work in the configuration shown. The only real difference would be in a routed scenario, you would not need the VIP at all.
-
@Derelict I tested the public IP on the internet switch and it works. I can browse when I configure it on my laptop.
I have done "Diagnostics > Ping and ping out to, say, 8.8.8.8 using that VIP as a source address" but no response. 100% packet loss. -
It's just layer 2/3. it works or it doesn't. If it doesn't it's not pfSense.
Sorry but that's just the facts.
-
You say you have 1 VIP but you set mask to /28. /28 is network with 14 IPs. You must set /32 mask on your VIP. So maybe this you problem?
P.S. yours x.x.x.141/28 is overlapping your assigned WAN IP x.x.x.142 - "good job". -
@ivanupsons said in 1:1 NAT failing.:
I tested the public IP on the internet switch and it works. I can browse when I configure it on my laptop.
I have done "Diagnostics > Ping and ping out to, say, 8.8.8.8 using that VIP as a source address" but no response. 100% packet loss.Maybe your ISP gear doesn't like multiple IP addresses on a single MAC address or something stupid/silly like that.
Packet capture and see what is really going on. See what ARP traffic there is, etc.
@dragoangel said in 1:1 NAT failing.:
P.S. yours x.x.x.141/28 is overlapping your assigned WAN IP x.x.x.142 - "good job".
Nothing wrong with the addresses chosen based on what we have been shown.
69.63.67.129 - 69.63.67.142 are available for use in 69.63.67.128/28.
The only thing we have not been shown that I can see is which of those addresses the ISP's gateway is using. .129 would not surprise me.