IPsec Phase 2 entry for access to WAN interface?
-
I've setup an IPsec tunnel between 2 locations, and everything is working fine. The "location B" is a pfSense behind a router (port forwarding for IPsec). PpfSense has a WAN address 192.168.0.6 . There are other devices in 192.168.0.0/24 network I need to be able to access from "location A", and I have no idea how to achieve that. There is also a 192.168.0.0/24 network in use on "location A", so I obviously need to do some translation voodoo on Phase 2 entry, but I don't know if it's even possible. Any ideas?
-
Perhaps you need Phase 2 BINAT:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/nat-with-ipsec-phase-2-networks.html -
@viktor_g said in IPsec Phase 2 entry for access to WAN interface?:
Perhaps you need Phase 2 BINAT:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/nat-with-ipsec-phase-2-networks.htmlYes, that's what I meant with translation, but the trick is, the subnet I want to reach is on WAN interface on the "location B", so I guess it's not something I can define in Phase 2 entry.
-
@marama So, you can try to use Policy NAT with some pseudo net which translates to 192.168.0.0/24 of WAN (10.0.0.0/24 in example):
Port Forward with source field:
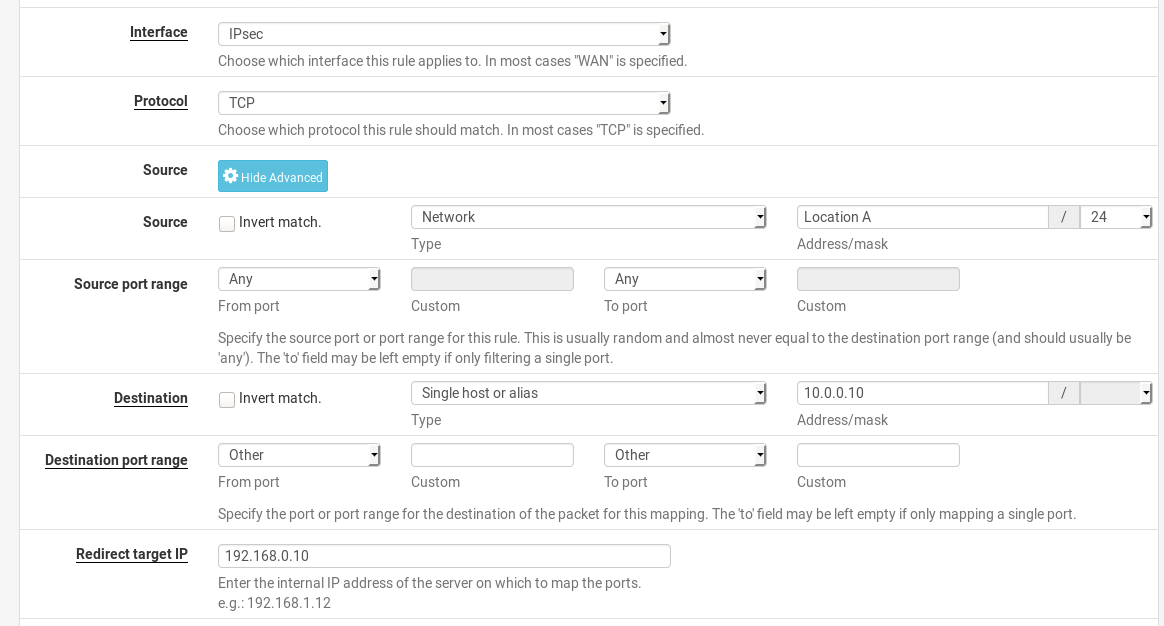
or 1:1 NAT with destination field