LAN to WAN Default deny rule IPv4 blocking port 443
-
Hello, I'm new with PFSENSE (was using SonicWall before) and I have an issue where I notice that the "Default deny rule IPv4" is blocking LAN to WAN connection on port 443. I have double check the destination IP and they are Office 365 and Microsoft IP address.
Is there a way to avoid that or do I need to constantly add new white list?
Other odd thing too is : Where is that list? I cannot see "Default deny rule IPv4" no where in rules or NAT or floating...
I can see a few default rules like the Anti-Lockout Rules but nothing for "Default deny rule IPv4"
Thank you -
Can you show us the logs of blocked traffic?
Are you actually seeing connectivity issues from clients on LAN?
The default rules should allow out all traffic from LAN side clients. You may be seeing this:
https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html#troubleshooting-blocked-log-entries-for-legitimate-connection-packetsSteve
-
Hello Stephenw10.
Yes, the error I see look like the one in the link you sent. So they would be false advertising kind of?
Users didn't report any issues yet as I just replace the router for the PFSENSE this weekend and they did not start working yet...
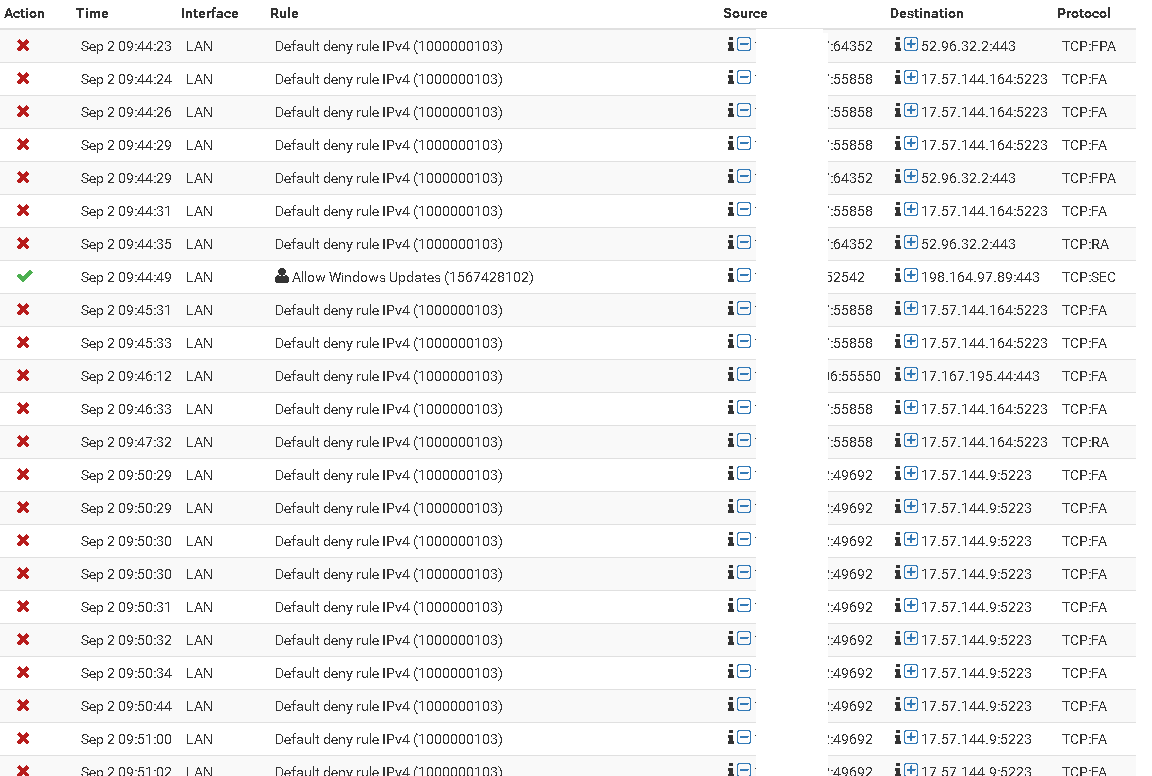
I have upload a screenshot and as you can see there are a lot of them
You will noticed the "Allow Windows Updates" it's me that whitelisted the IP for Microsoft Updates but maybe I don't need them at all?????
Thank you
-
Sorry sent the wrong screenshot, of course those 5223 port will be block. Someone's using a software from Apple that I have not figured out yet.
Here's the one that show the 443 block.
But again, I think the other link was right as we are using a cloud solution antivirus and when I check the last connection from client and some on them was about a 1 minutes ago so I think I'm good. Just weird that it create a lot of entry like that but it's fine. The filtering work fine and it's fast....
Thx again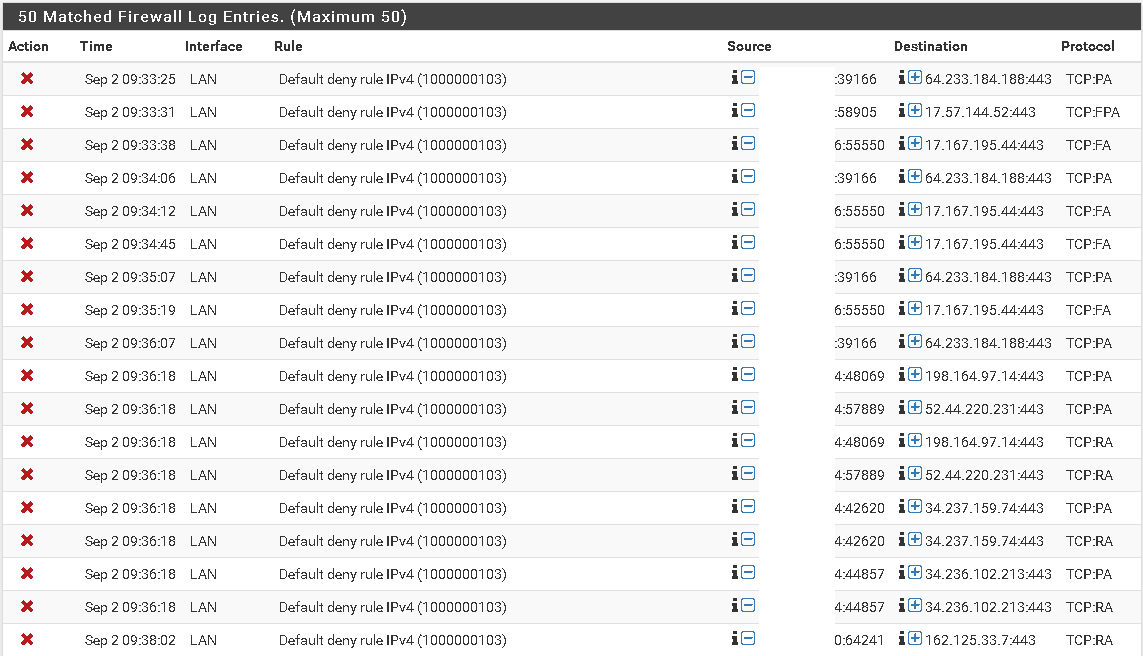
But aain -
Yes, that looks like all out of state TCP traffic. If you're not actually seeing a connectivity issue it's only really a logging issue.
You could set the firewall optimisation to conservative in System > Advanced > Firewall&NAT. That will increases the state timeouts. It's probably not necessary though.
Steve
-
Hello, at least I have something to modify if users complain tomorrow hehe
Thank you!