FreeRadius 3: Fall-through vlan assignment.
-
I am a new user to PFSense, and have been kicking the tires quite a bit, including giving dynamic VLAN assignments by MAC. I have this working, but I cannot find a configuration item that would allow me to authenticate the MAC and give a VLAN assignment back, else return a different VLAN for those clients which did not authenticate successfully with a MAC to the radius server.
I don't want to pursue this further if it's folly, but I think I am on the right track. Is there a way to produce a fall-through vlan assignment?
-
Isn't it a function of the switch rather than FreeRadius, I don't use FreeRadius MAC auth myself but looking on one of my switches:-
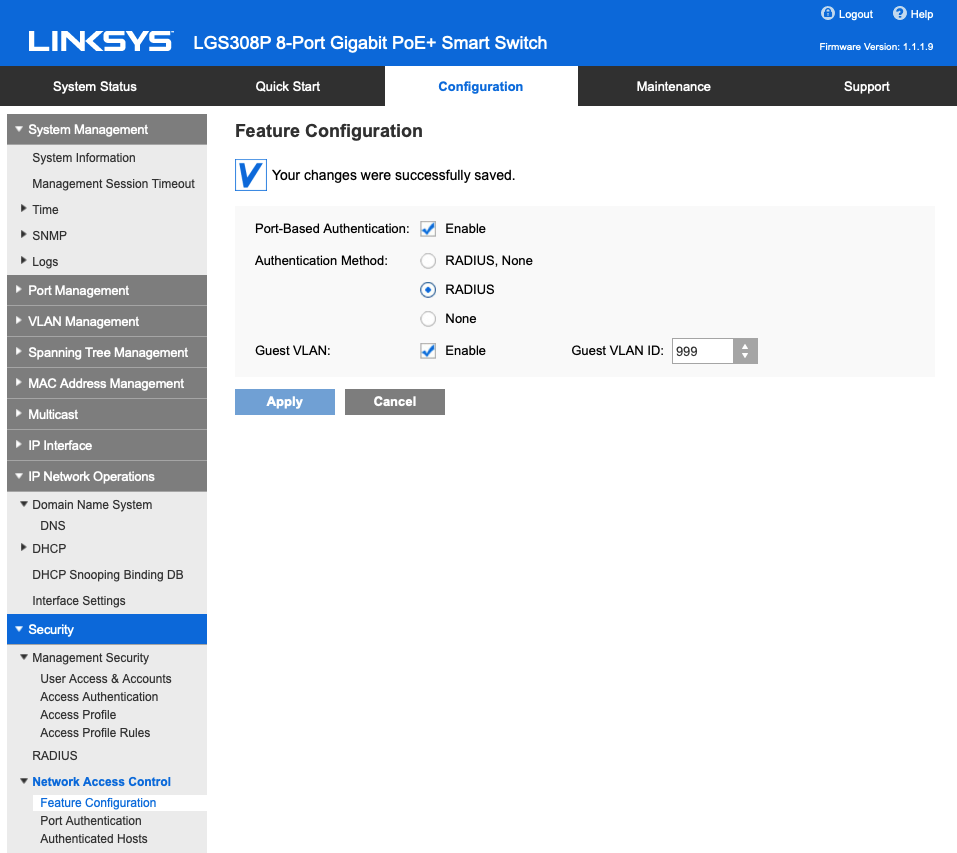
-
@NogBadTheBad
You're correct, it is a function of the switch, or wireless AP.
These devices typically have a facility to allow MAC authentication using a RADIUS authentication provider, in which case a RADIUS based authentication handshake takes place but instead of a username/password being exchanged the MAC address is passed as the username AND password. Hint: This will be a PAP type authentication.
The format of the MAC address is important, the switch or AP and the RADIUS server have to agree on how to process it, is it aa:bb:cc:dd:ee:ff, or aa-bb-cc-dd-ee-ff, or AA-BB-CC-DD-EE-FF, etc.
When the RADIUS server grants access, it returns an attribute value (could need to be custom depending on the equipment vendor) containing the desired VLAN number.
If the RADIUS server does not grant access, the equipment (switch or AP) will assign a default vlan to the connection.
The net result is if RADIUS MAC passes you get assigned the desired VLAN, and if it fails you end up on the Guest VLAN which terminates in a Captive Portal or some such alternate authentication mechanism. -
@awebster Thank you guys so much for your help. I have the mac address authentication working, I think I missed the native-vlan option on the client device. Thanks for pointing me in the right direction.