Nat
-
Hello.
I have a vpn configured with ipsec, I need to make a ip nat 10.15.10.1 arrives on my internal network 172.30.20.1 what protocol should I use? -
That has nothing to do with NAT but your Phase 2 configuration of your IPSEC VPN. You can setup BINAT or NAT there and configure your IP NATting accordingly.
-
Ah OK. Thanks.
In part 2 on my ipsec I added network and ip and ip mask, but even asism they told me they can't ping my internal network -
post your settings of the phase 2 configuration and your rules on the ipsec interface.
-
This post is deleted! -
https://ibb.co/YPWpDX6
https://ibb.co/CBD87Nk
https://ibb.co/SmpBrfg
https://ibb.co/WF4fJxr
https://ibb.co/34N8WxRFollow the links:
I posted on this site, because here is giving error when I post the photos -
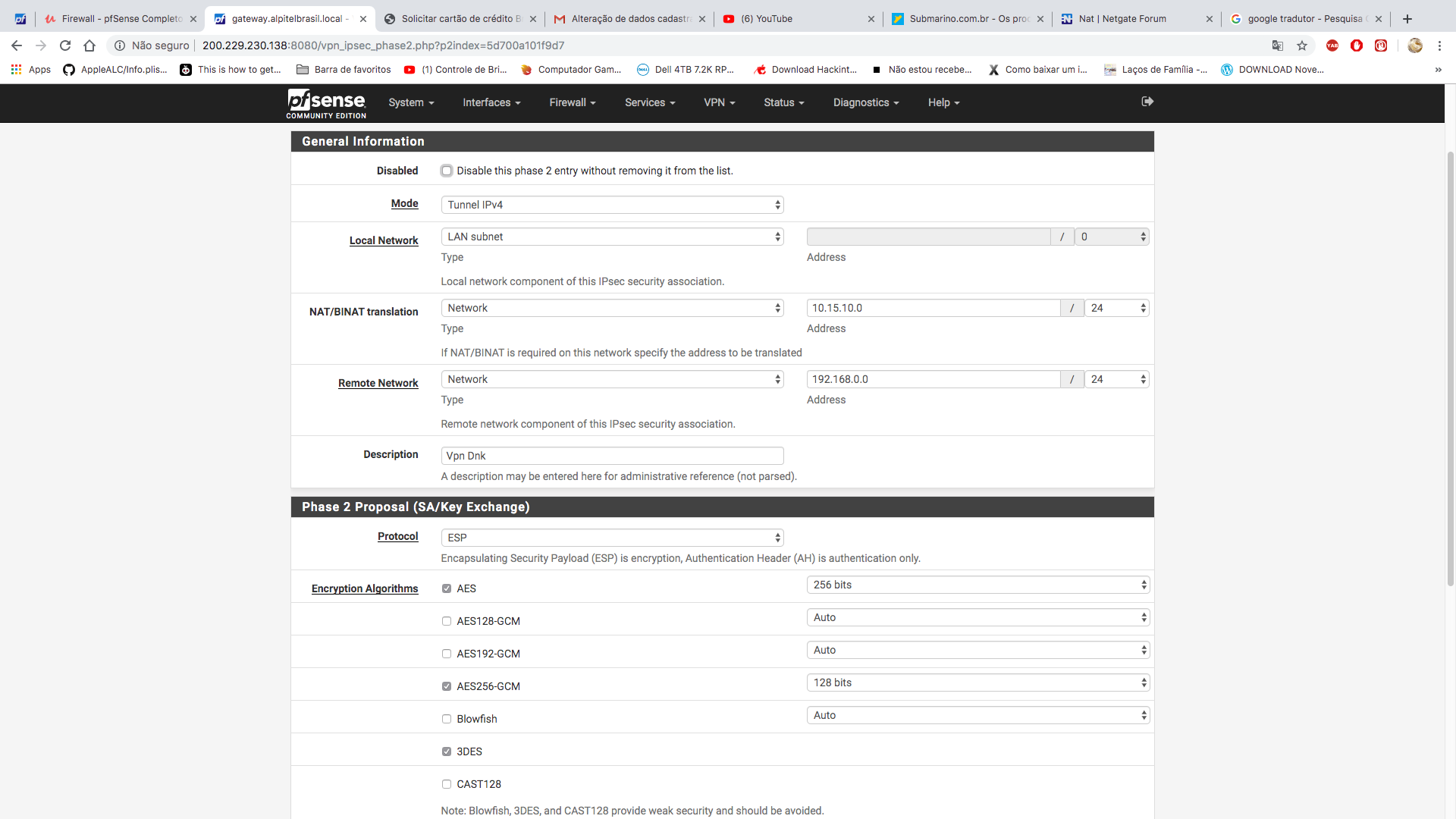
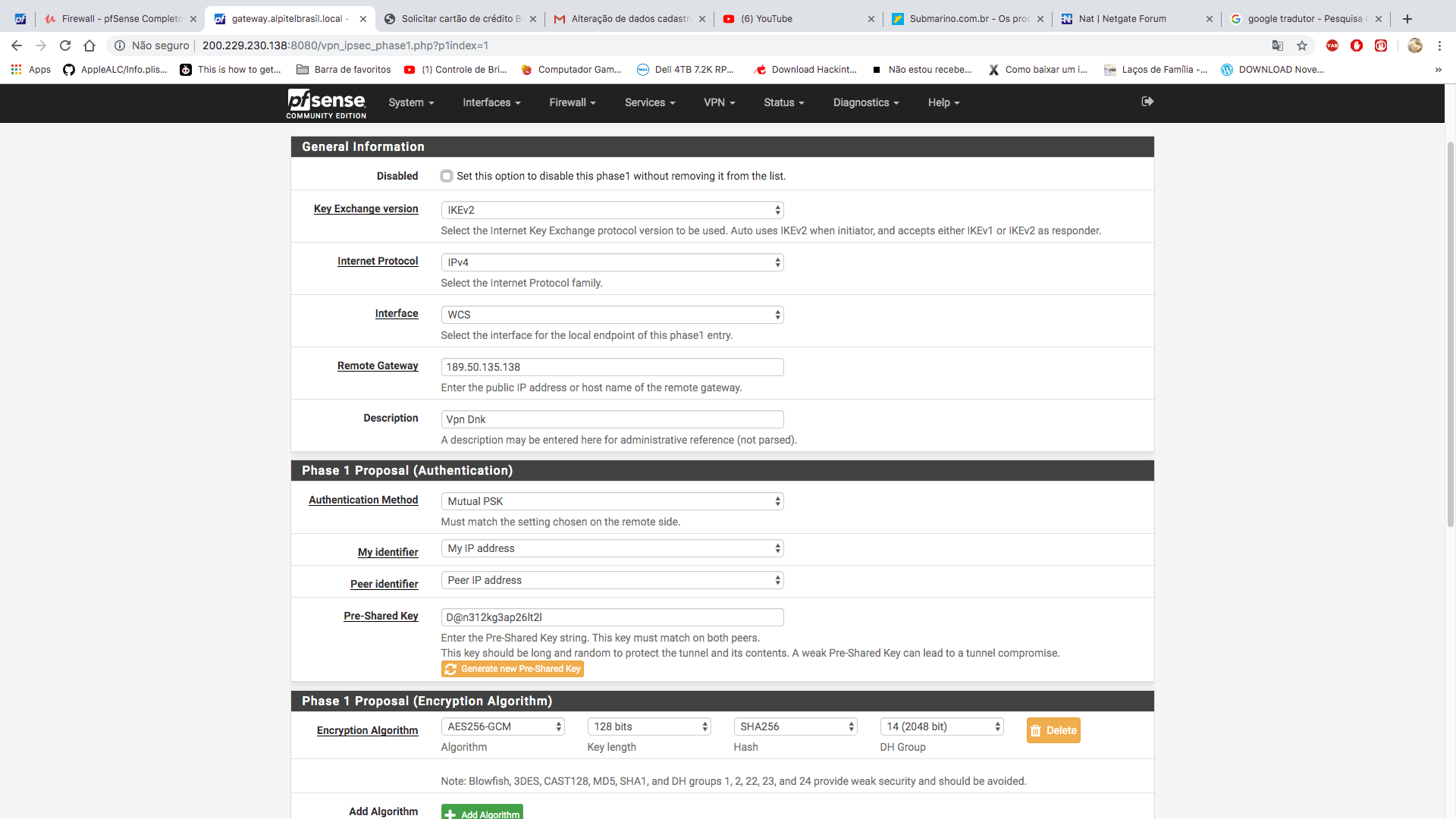
OK so now please again define what IP should show up on which side with what IP? As I only see "LAN network" I guess your local network is 172.30.20.0/24?
Also you are using very strange and potentially unsafe IPSEC crypto settings. Using DH Groups smaller than 2k isn't recommended. Also running 3DES and SHA1 in phase 2 when you run AES-256-CBC and SHA256 on phase 1 makes no sense to me at all. 3DES and SHA1/MD5 are also considered unsafe and should be avoided. To mix in such old things with the newer ones in phase 1 is ... confusing.
-
Thank you for your help.
So the intention is that my network can access the network 192.168.0.1
and this same network, get access to mine which is 172.30.20.1 -
Your intention is fine, but I need config to see to help. I can't just turn on my crystal ball and read minds, you know? ;)
So if your networks don't overlap, why do you try to NAT your IPs when connecting both networks via IPSEC? And that doesn't explain why you used such strange cipher/security settings either.
-
Essa configuração de segurança foi a mesma que me foi passada pela empresa, que eu to tentando liberar o acesso.
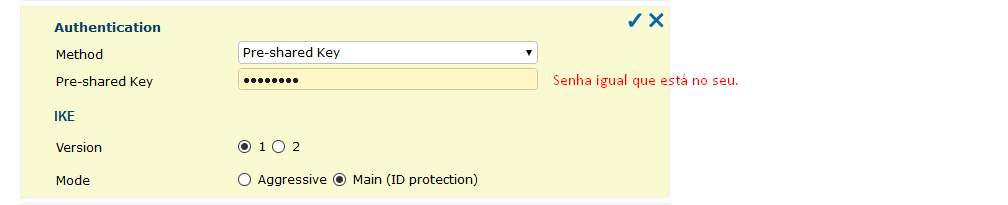
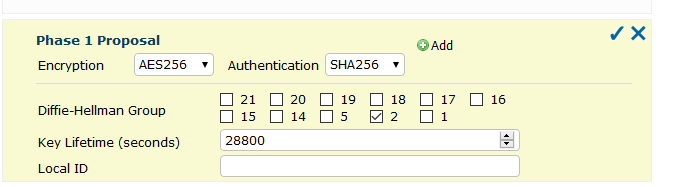
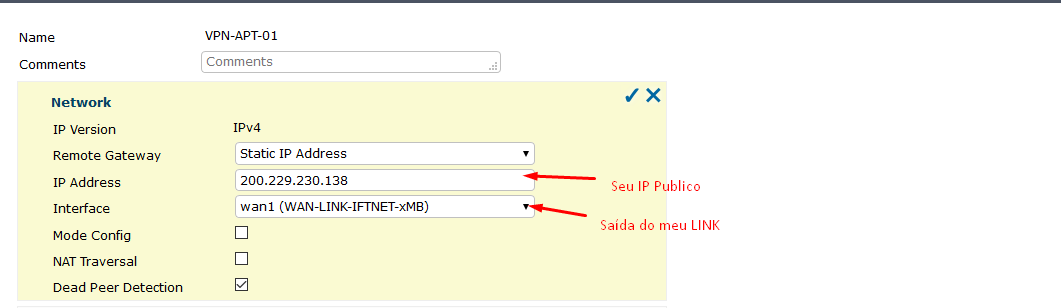
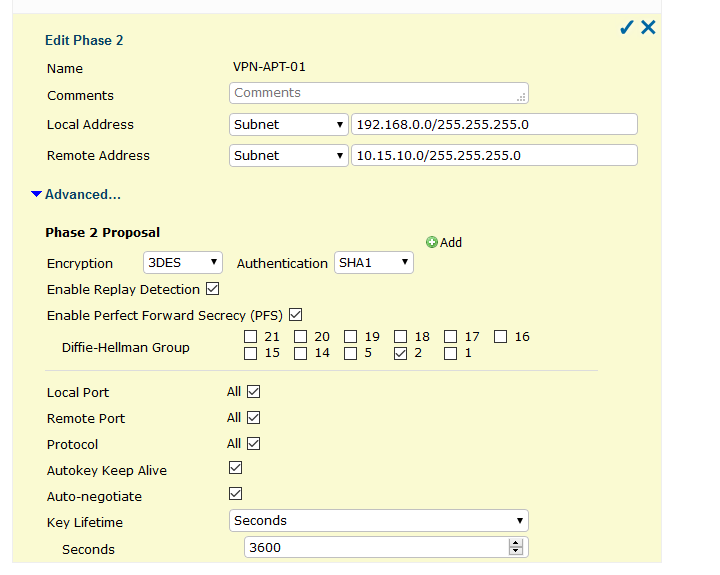
I followed this model sent to me
-
And why was it send to you with
a) such bad settings when there are obviously better settings available!
b) why has the other side configured 10.15.10.0/24 as your remote network if you use 172.30.20.0/24?
c) why do they use bad/weak encryption in phase 2 if there are better possibilities?It simply doesn't make sense. You shouldn't just "mimic" configuration you get sent, if it's wrong or broken, question it instead of trying to bend you configuration in ways it shouldn't.
So I would call back and ask those 3 questions and ask for the settings to be corrected. The only thing that could be right is the "wrong" remote address subnet IF they have already 172.30.20.0/24 in use on THEIR side. Then configuring the BINAT setting in your phase 2 config is right. But unless that is confirmed, I'd reject that configuration as bad/wrong/insecure and ask why.
PS: nothing wrong being a "beginner". Everyone has to start somewhere. But don't try to run a bad/wrong configuration if you can just ask back to correct it (if possible).
-
To be honest, I'm kind of a layman at ipsec, I'm studying to understand better.
I believe the hardest I get, which is dripping 192.168.0.1
-
I will question them, and redo this rule
-
Thank you so much for your help, I will change my security and talked to them too.
-
As said above, try to insist to use at least
- AES-256 (CBC) or AES-256-GCM (better)
- IKEv2 (seems available)
- SHA-256 or SHA-384
- DH Group 20 (nist ecp384)
and the same in phase 2. Lifetimes 28800 and 3600 are OK.
@jimp or @johnpoz or any other global mods: Please move that topic to IPSEC as the NAT part is pretty much nonexistent and/or subject to a IPSEC connection - so nothing to do with classical inbound or outbound NAT settings :)
-
I already fixed

-
Remove the checkbox in front of 3DES so your connection will not simply downgrade if the other side wants to speak 3DES. Otherwise you'll still connect with that :)
Also many peers don't run IPSEC with AES-GCM yet (even in 2019 - a shame!) so be prepared to select AES256 (CBC) instead. Not that performant but secure nontheless. -
Thank you for your help.
unchecked the 3d
I already questioned the other side about the settings. -
@felipe_antocheski said in Nat:
protocol
OpenVPN is fast, flexible, and secure you should give it a try.
-
I already have and use the problem that when I connect with it I can't use my local network