Routing to another subnet off WAN interface
-
Below is (hopefully) a simplified diagram of the network layout I’m working with:
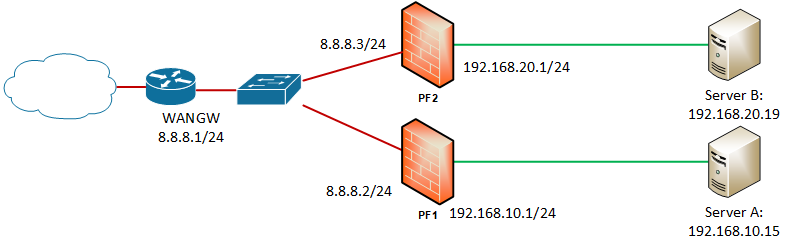
Servers A & B are in their own subnets, each with a pfSense instance providing NAT, with a default upstream gateway (WANGW) providing onward access to the Internet. This is working fine, and each server has in/outbound access to the Internet.
What I’m trying to do, is allow Server A to access Server B using its internal address 192.168.20.19. To do this, I’ve done the following:
- On PF1, added a gateway (GW_PF2) pointing to PF2’s WAN interface (8.8.8.3)
- On PF1, added a floating rule:
a. Action: pass
b. Quick
c. Interface: WAN
d. Dir: Out
e. Protocol: Any
f. Source: Any
g. Dest: 192.168.20.0/24
h. Gateway: GW_PF2 - Changed Outbound NAT on PF1 to Hybrid Outbound NAT, and added a manual rule:
a. Do not NAT: ticked
b. Interface: WAN
c. Source: 192.168.10.0/24
d. Dest: 192.168.20.0/24 - Repeated steps 1, 2 & 3 on PF2
This is almost working, if server A pings server B I can see the packets arrive. However, it seems that when PF2 receives Server B’s reply, it’s trying to forward the packet to PF2’s default gateway (8.8.8.1) rather than PF1.
Am I missing a step? (I wondered if the reply-to state might be causing an issue?) Or is there a simpler way to achieve what I’m trying to do?
Many thanks,
-
Unless you are Google it is a very bad idea to use their IP space for your own use as a private LAN. You should not be using any public space IPs as a LAN.
Things like VOIP can break easily.
Set up a VPN instance between the two firewalls
or connect the two firewalls via a third interface on each of them on a subnet such as 172.16.20.0/30. Then you can run something like RIP on them.
-
See this thread:
https://forum.netgate.com/post/864715 -
Why not configure IKEv2 site-to-site IPsec? It easy 5 minute job Karl!
-
@Derelict said in Routing to another subnet off WAN interface:
See this thread:
https://forum.netgate.com/post/864715Thanks - in particular this post https://forum.netgate.com/post/864578 made it all make sense.
I sorted this out by removing the upstream gateway on the WAN interface itself, and relying on the default gateway in System->Routing. I then added a static route and gateway for the other subnet.
I was then able to remove the floating rule so it all feels much cleaner now.
I did go down a similar path during my testing, but don't think I realised that by removing the gateway on the WAN interface I needed to re-add the outbound NAT entries that would usually be created by the automatic rule generation for accessing the wider Internet.
-
@dragoangel said in Routing to another subnet off WAN interface:
Why not configure IKEv2 site-to-site IPsec? It easy 5 minute job Karl!
As the traffic is still on our network we didn't need the encryption/overhead of the VPN (traffic could be ~500 Mb/s). I did consider just a tunnel if I couldn't get the routing to work but have now got it sorted as above.