ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps
-
I recently replaced a Cisco ASA 5505 at a remote branch with a pfsense appliance. I am trying to establish a S2S vpn between the two locations. I can get Phase 1 connected just fine. But only one side of Phase 2 seems to work. Site A is using 10.2.0.0 /16. Site B is using 10.1.0.0 /16 but a vendor makes us use 192.168.1.0 /24. I setup both of these as separate phase 2s but if I try and ping the gateway for either remote network, only one works at a time and not both. I've tried telling the Phase 1 to build split the connections but this didn't work either.
I read the documentation on building IPsec between the Cisco and the pfsense appliance and using their same example it basically did the same thing. I have the Cisco at site B built the same as it was when the Cisco at site A was working so it should be allowing the connection between all the subnets still.
Is this something the pfsense is having an issue with or the Cisco? The VPN log just only tells me that its destroying and rebuilding the connection each time.
-
Check "split connections."
-
I tried that as well and its still the same issue. It will pass traffic and then it will switch when I'm pinging across the subnets.
What I mean is, if i ping 192.168.1.25...it will respond. Then if I ping 10.1.1.25, I will get no response. 30 seconds later 10.1.1.25 will respond and then 192.168.1.25 won't. It doesn't do this randomly however as it seems to switch when depending on which subnet I'm sending traffic to.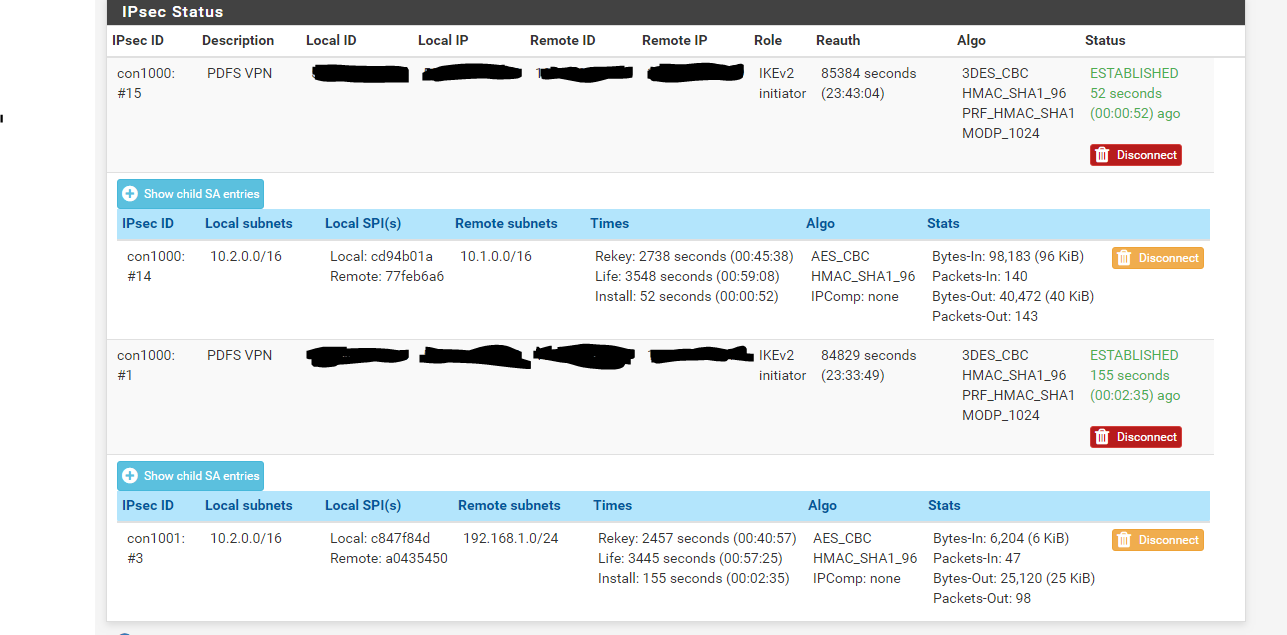
-
@rcogswell00 said in ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps:
if i ping 192.168.1.25...it will respond. Then if I ping 10.1.1.25,
@rcogswell00 said in ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps:
Site B is using 10.1.0.0 /16 but a vendor makes us use 192.168.1.0 /24.
OK I'm confused. So how did you setup that Phase2 settings? BiNAT? With different subnet sizes? Screen please.
-
Site B's network is /16 so there are devices on 10.1.0.0, 10.1.1.0, 10.1.2.0. Site A's network is the same except their IPs start with 10.2. At Site B, there is also a 192.168.1.0 that is also configured on that network and has one device that has a 192.168.1.99 address. I've asked the vendor that controls the device to change its IP address but its been a challenge to have them change it to something on the 10.1 range. In the mean time I need Site B's addresses to talk to both a 10.1 and the 192.168.1. I tried using the NAT/BINAT translation but couldn't get it to work either. I am new when it comes to pfsense devices.
Phase 2a:
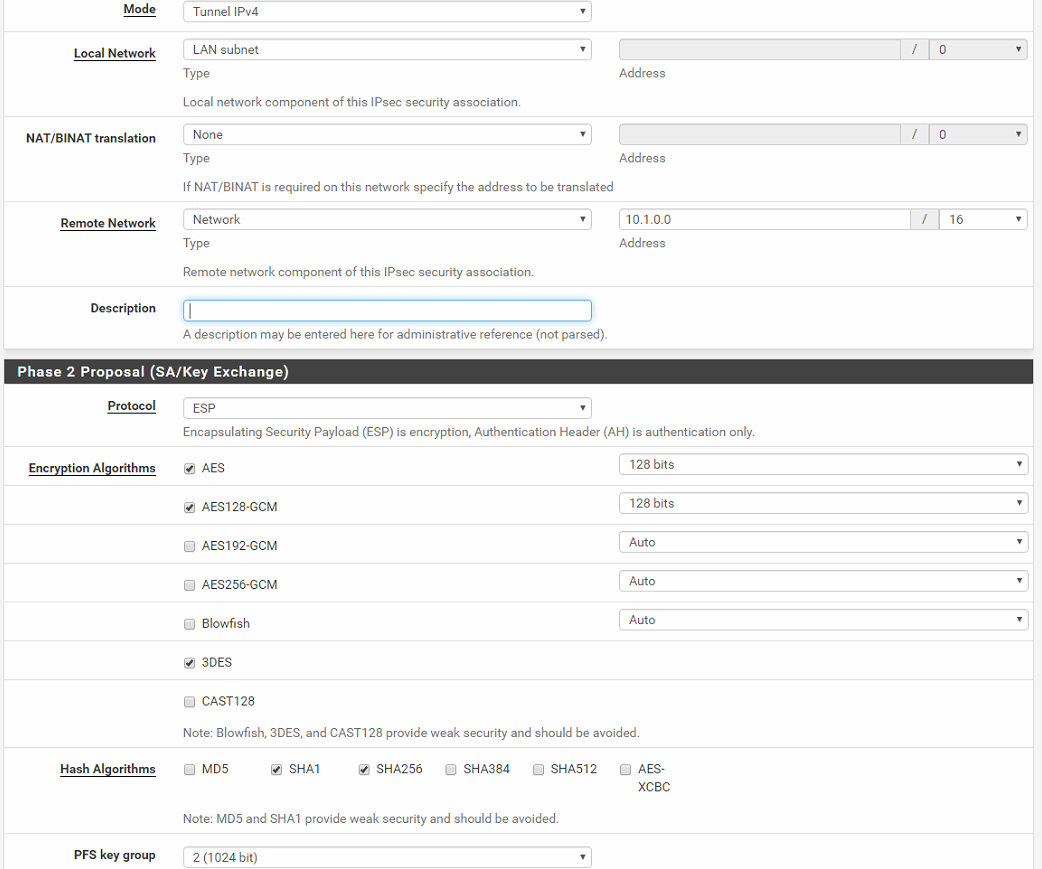
Phase 2b:
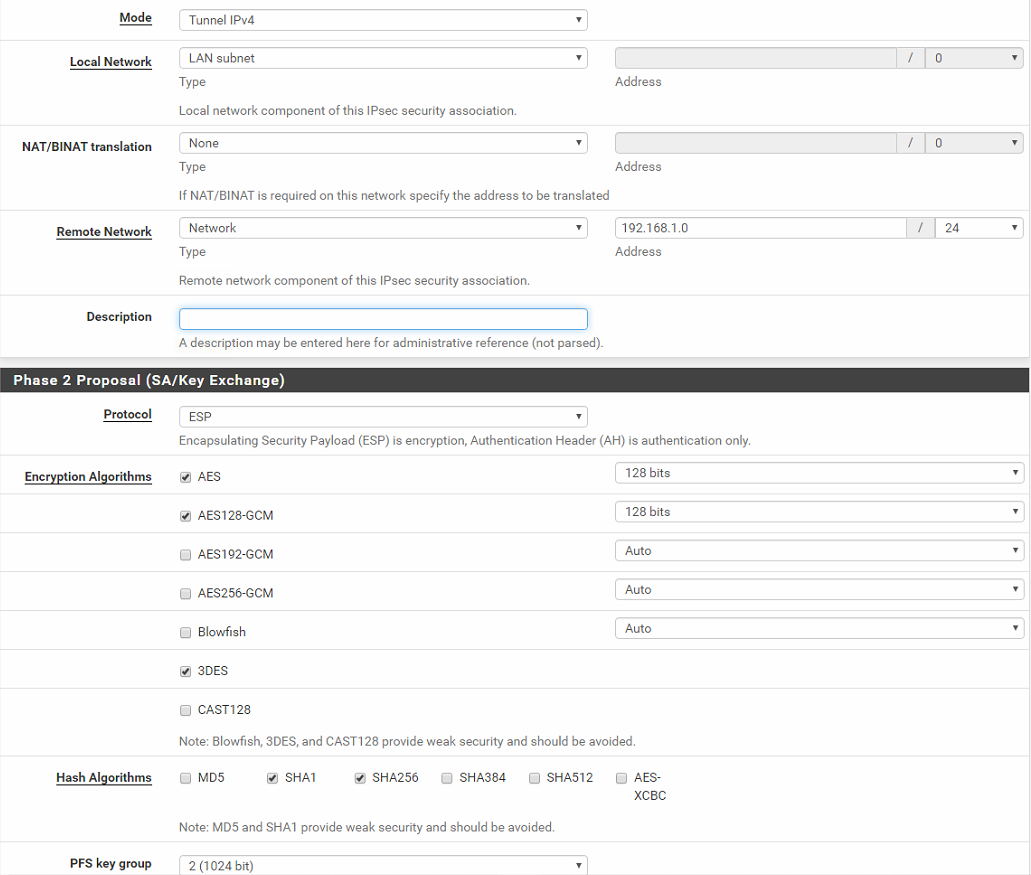
-
Should be no problem. Maybe the access-list in the crypto map on the ASA is wrong.
Split connections should only matter on IKEv2. Is this IKEv2?
-
Yes the connection is using IKEv2.
Here is the ASA side. I would think if the access-list was wrong then neither of the subnets could communicate at all.
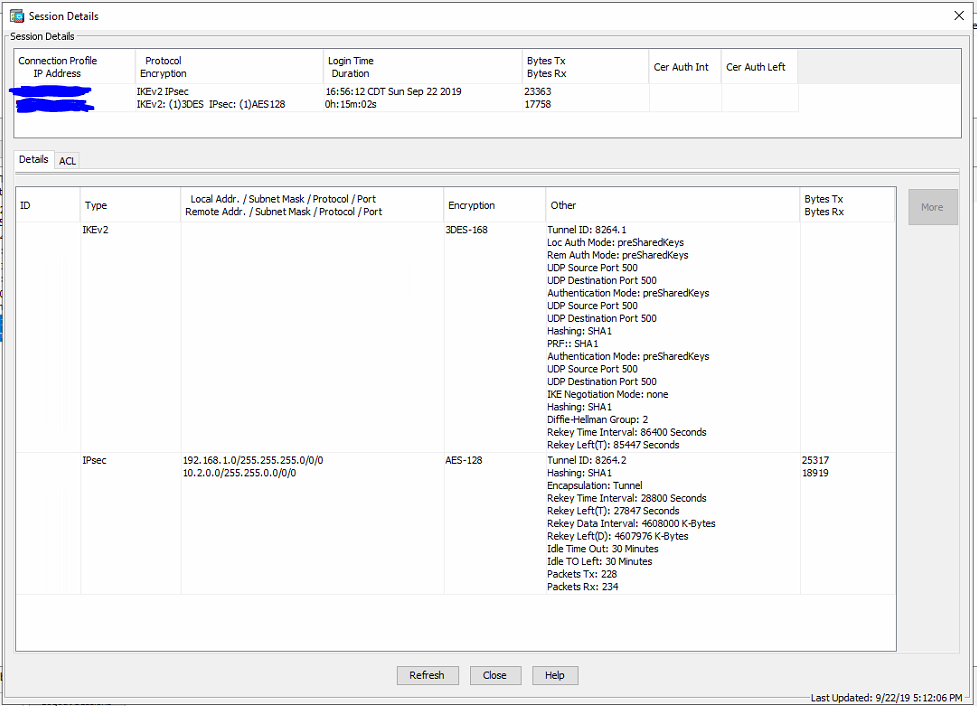
-
That is configured for 192.168.1.0/24 -> 10.2.0.0/16
There is nothing there for 10.1.0.0/16
Like @JeGr I am also confused about exactly what you are trying to accomplish.
If they want to NAT 192.168.1.0/24 to something else, they have to do that on the ASA side.
-
Also: crypto settings. I see wildly configured cipher/enc sets all over the place and an ASA screen saying IKE2 (nice) but 3DES? And SHA1? Please fix that (phase1/2) first, otherwise you have a tunnel, but if that is any "private" at all is doubtful.
-
Site B has the 10.1.0.0/16 and the 192.168.1.0/24. Yes they are connected to each other and i can pass traffic to them all day long. Site A only has the 10.2.0.0/16. Yes the ASA only shows a tunnel right now to 10.2.0.0 and 192.168.1.0. I can easily switch them however by either reconnecting the VPN and passing traffic between 10.2.0.0/16 and 10.1.0.0/16 or just ping the 10.1.0.0/16 enough and the tunnel "flops" and connects.
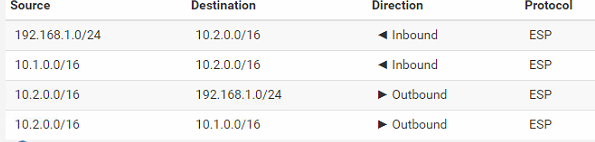
ASA VPN settings
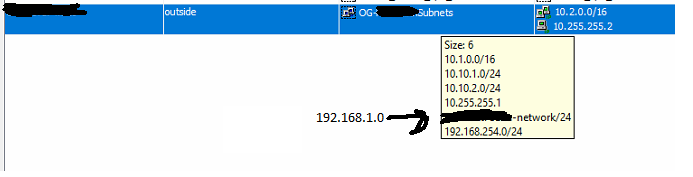
As far as the crypto settings, yes I am aware that its "unsecure" but I was trying to follow the instructions listed in the pfsense manual for connecting the ASA and the pfsense through IPSec. Once I could get it to pass traffic then I would worry about turning security up. I'm just trying to make it work at this point.[Connecting to Cisco PIX/ASA Devices with IPsec] (https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/connecting-to-cisco-pix-asa-devices-with-ipsec.html
-
I do not see anything on the pfSense side to prevent 10.2.0.0/16 from communicating with both 192.168.1.0/24 and 10.1.0.0/16.
Look on the ASA side.
Or better-describe what you are looking to do.
Packet capture on the pfSense IPsec interface. Is the traffic going out?
-
@Derelict said in ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps:
I do not see anything on the pfSense side to prevent 10.2.0.0/16 from communicating with both 192.168.1.0/24 and 10.1.0.0/16.
That is describing what I'm looking to do. You are right, it DOESN'T make sense why it won't send traffic out. The VPN connection is setup exactly the same as our others on the ASA side. The only difference is those are VPNs across to ASA 5505s and this one is trying to use a pfsense appliance. Is there anything that would prevent the ASA from allowing the pfsense to allow multiple phase 2s? I always seems like its some check box somewhere.
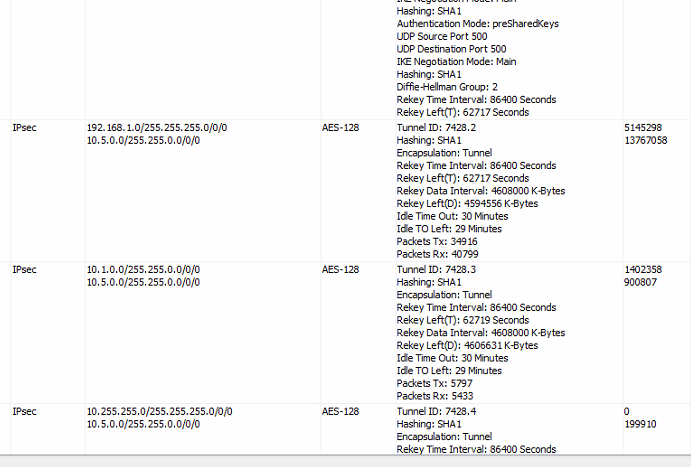
This is an example of another tunnel we have that is between a ASA 5505 and a 5508.
-
How about you post the show running for the pertinent IPsec parts instead of the ASDM screenshots. Makes it MUCH easier to see what's up.
Did you packet capture to verify the traffic isn't being sent out?
-
You absolutely need split tunneling enabled to do multiple IKEv2 selectors to an ASA. The ASA is the reason that checkbox exists in the first place. So leave that enabled.
-
@Derelict said in ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps:
How about you post the show running for the pertinent IPsec parts instead of the ASDM screenshots. Makes it MUCH easier to see what's up.
Did you packet capture to verify the traffic isn't being sent out?
I'll get the config on the ASA out.
Packet capture shows traffic passing depending on which phase 2 is connected. It fails to see anything on the one that is not.
-
@Derelict said in ASA 5505 / pfsense only one Phase 2 traffic passing at a time; swaps:
You absolutely need split tunneling enabled to do multiple IKEv2 selectors to an ASA. The ASA is the reason that checkbox exists in the first place. So leave that enabled.
I figured as much and haven't turned this off.