VTI from pfsense 2.4.4-RELEASE-p3 to pfsense 2.4.4-RELEASE-p3 goes inactive after some time.
-
I have an OSPF area back to a colo. One of the OSPF interfaces is a VTI tunnel. The OSPF area is likely extraneous information but I'm being pedantic.
After staying up for about an hour my VTI tunnel invariably goes "inactive" and my routing table re-converges. The IPsec settings match on both ends. What am I doing wrong here? These are the most recent log entries for IPsec:
Sep 22 17:43:12 charon 10[IKE] <con1000|132> nothing to initiate
Sep 22 17:43:12 charon 10[IKE] <con1000|132> activating new tasks
Sep 22 17:43:12 charon 10[ENC] <con1000|132> parsed INFORMATIONAL_V1 request 402067650 [ HASH N(DPD_ACK) ]
Sep 22 17:43:12 charon 10[NET] <con1000|132> received packet: from ...[500] to ...[500] (108 bytes)
Sep 22 17:43:12 charon 10[IKE] <con1000|132> nothing to initiate
Sep 22 17:43:12 charon 10[IKE] <con1000|132> activating new tasks
Sep 22 17:43:12 charon 10[NET] <con1000|132> sending packet: from ...[500] to ...[500] (108 bytes)
Sep 22 17:43:12 charon 10[ENC] <con1000|132> generating INFORMATIONAL_V1 request 1327146047 [ HASH N(DPD) ]
Sep 22 17:43:12 charon 10[IKE] <con1000|132> activating ISAKMP_DPD task
Sep 22 17:43:12 charon 10[IKE] <con1000|132> activating new tasks
Sep 22 17:43:12 charon 10[IKE] <con1000|132> queueing ISAKMP_DPD task
Sep 22 17:43:12 charon 10[IKE] <con1000|132> sending DPD request
Sep 22 17:43:12 charon 10[KNL] <con1000|132> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Sep 22 17:43:12 charon 10[KNL] <con1000|132> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Sep 22 17:43:06 charon 07[CFG] vici client 52899 disconnected
Sep 22 17:43:06 charon 07[KNL] <con3000|129> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 out failed, not found
Sep 22 17:43:06 charon 07[KNL] <con3000|129> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Sep 22 17:43:06 charon 07[KNL] <con1000|132> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 out failed, not found
Sep 22 17:43:06 charon 07[KNL] <con1000|132> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found -
Please show VPN / IPsec / Tunnels page
-
If the tunnel is up, but the routes show inactive, then maybe https://redmine.pfsense.org/issues/9668
If the tunnel is not up, then probably https://redmine.pfsense.org/issues/9767
-
@viktor_g Sorry about that, Here is my phase 1:
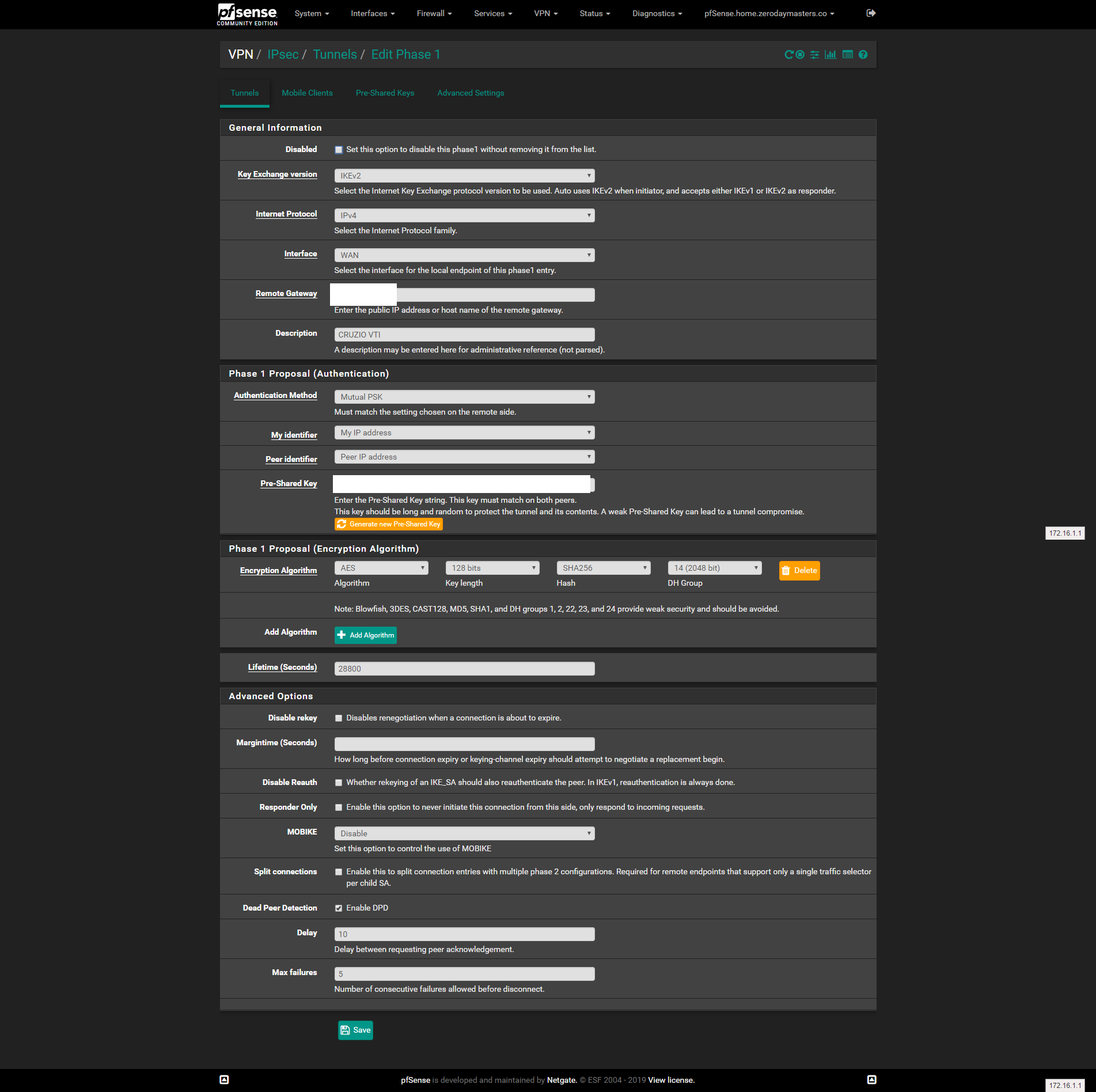
Here is my phase 2:
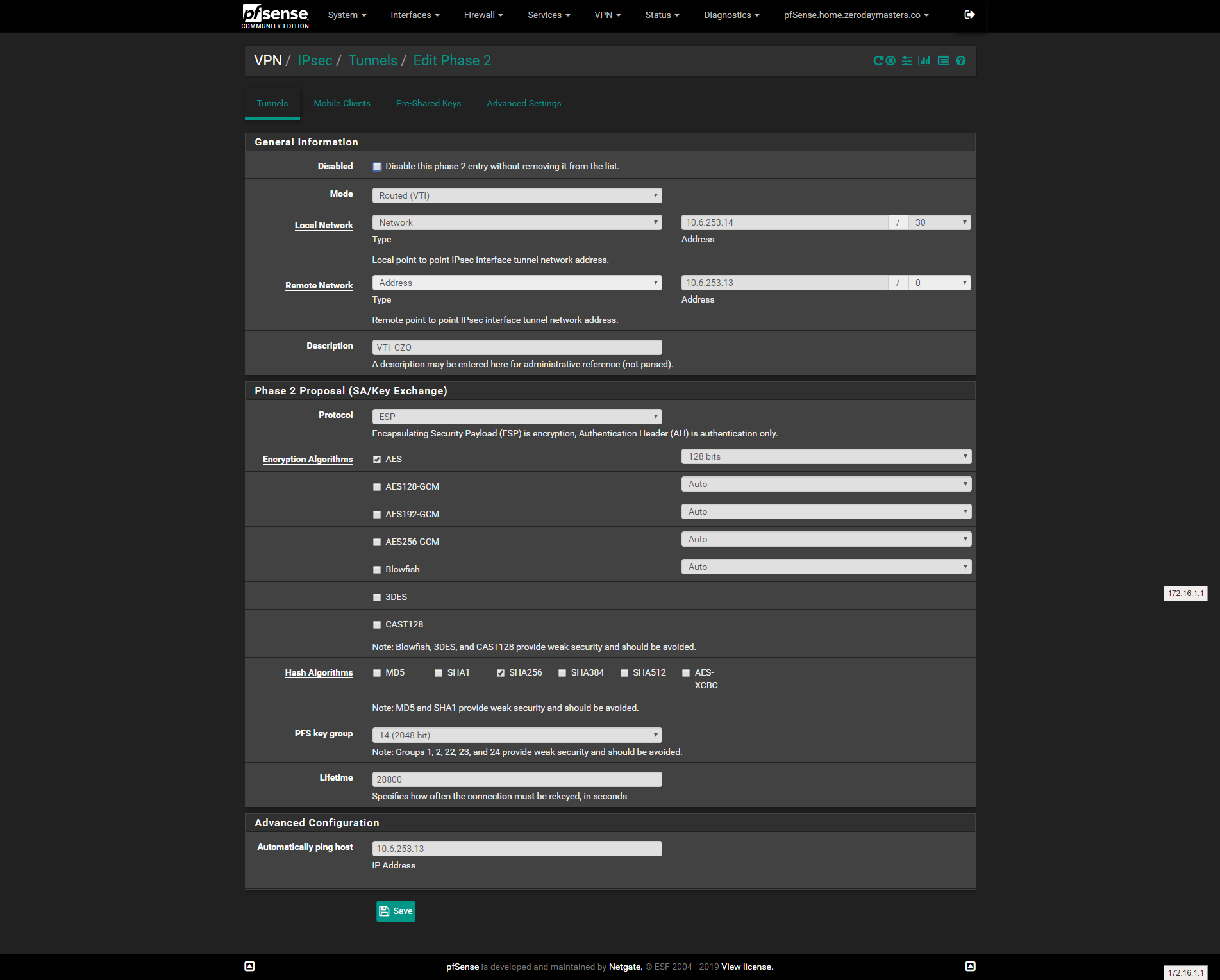
I was originally using IKEv1 and the tunnel was going down. I switched to IKEv2 and the tunnel is up. I can ping the remote gateway from the tunnel interface. However, FRR OSPF is favoring a higher cost interface:
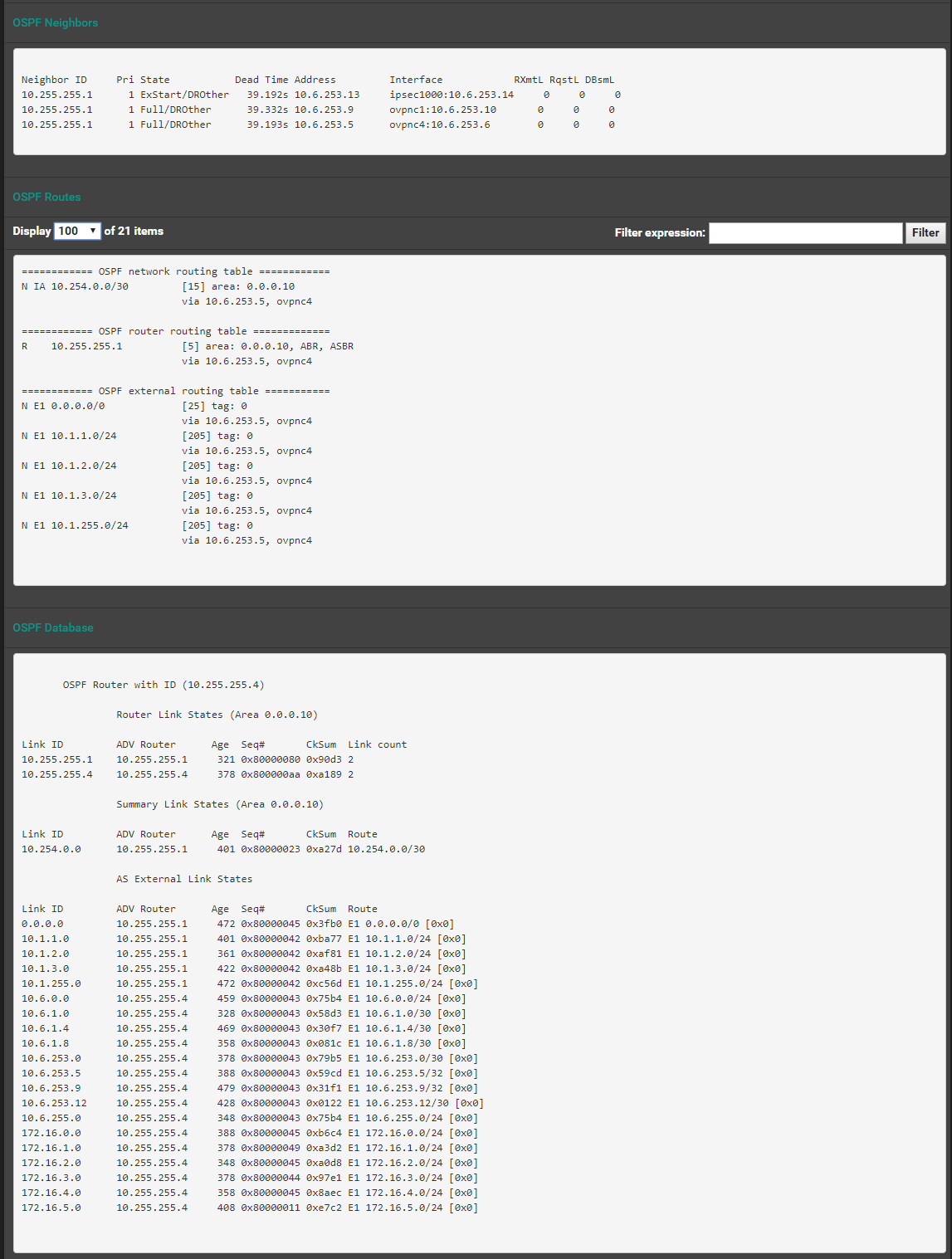
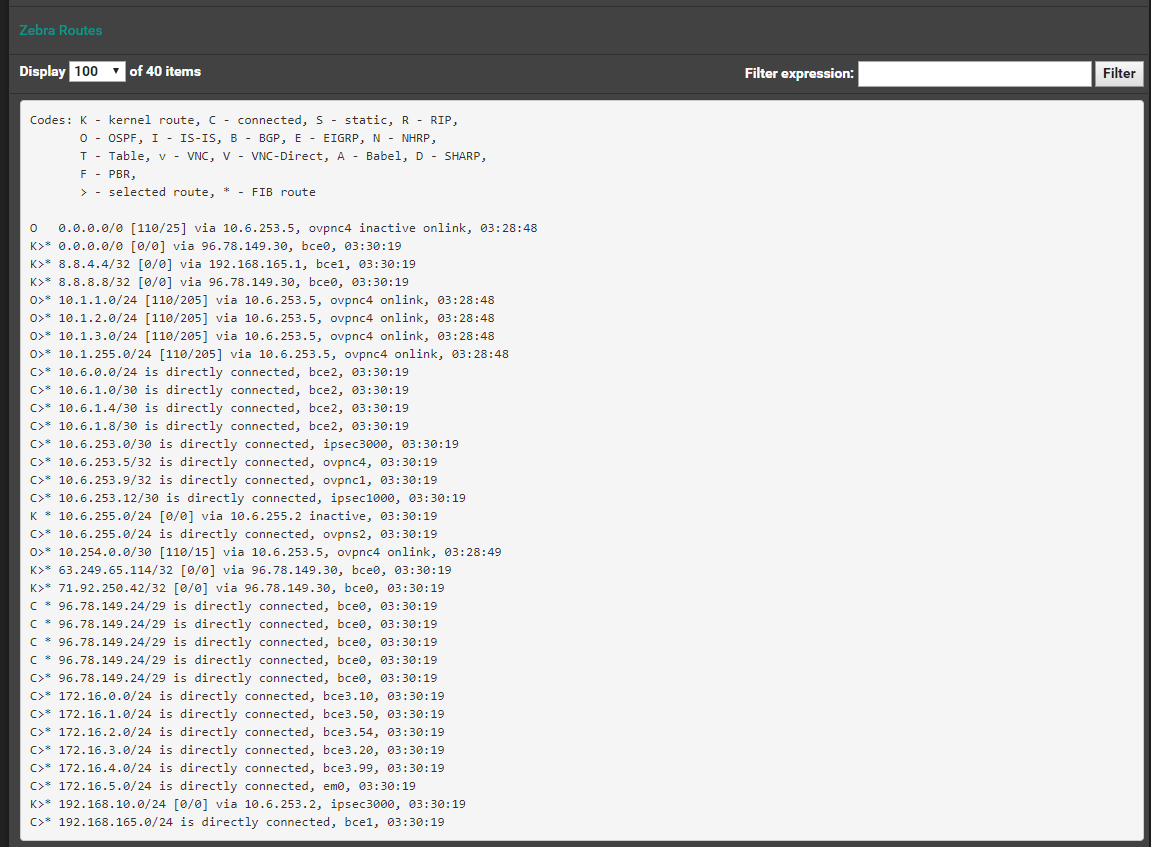
-
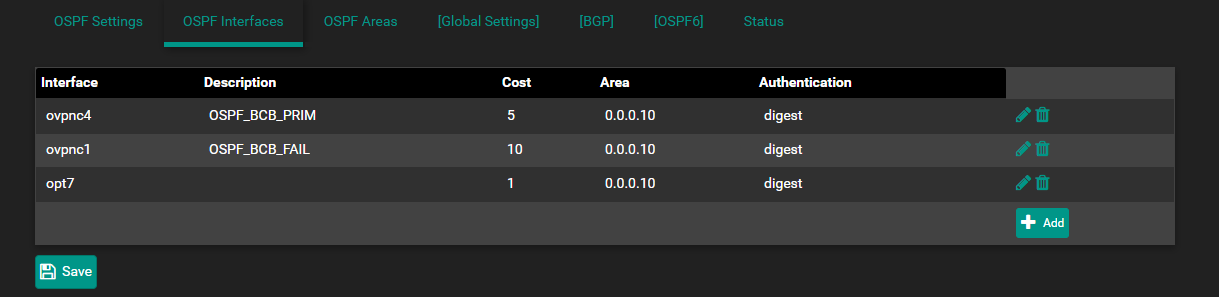
-
For some reason there was an MTU mismatch. I forced an MTU of 1500 for both VTI interfaces and all appears to be well. Not sure if forcing a 1500 MTU is a good idea or not.
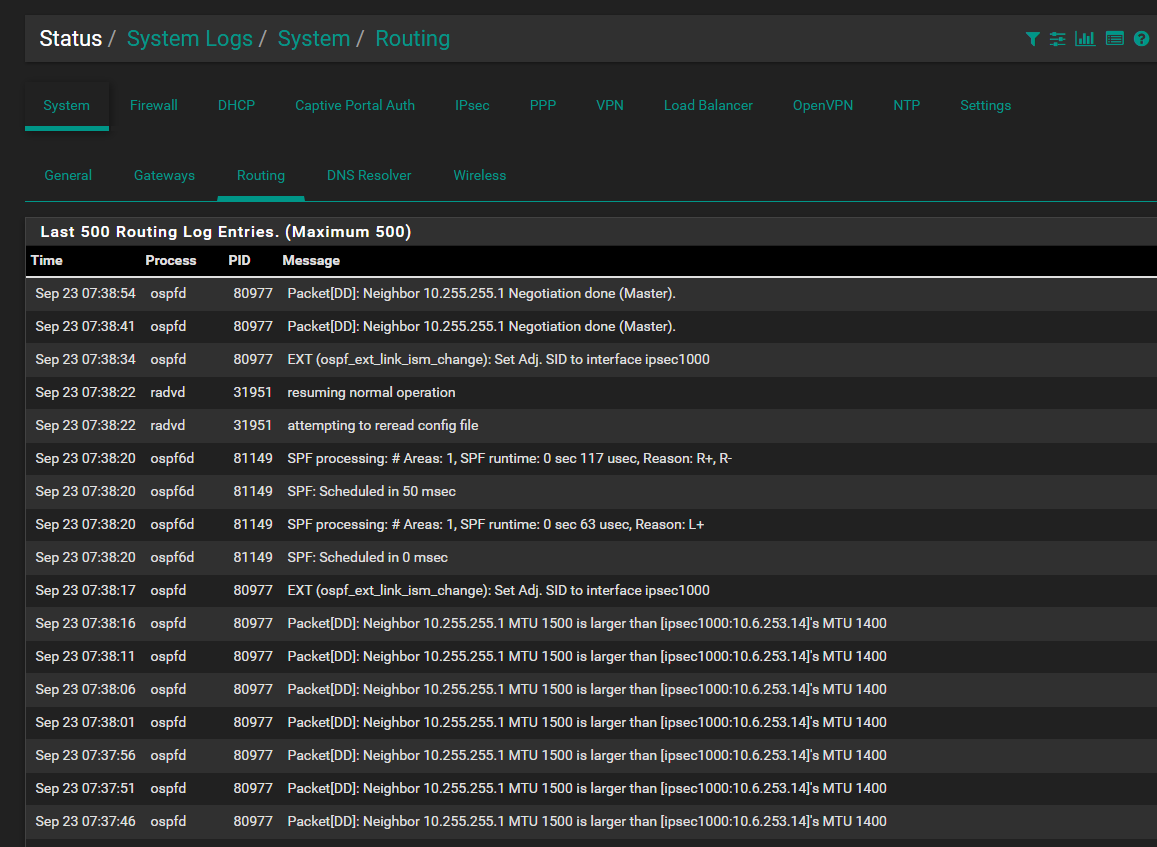
-
I would not force any IPsec-related MTU over 1400. 1380-ish is more realistic.
-
@jimp For the time being this tunnel is just used for local traffic. I am in the process of securing a licensed microwave link back to the colo, At that time I plan on using the VTI tunnel as a failover link to the internet. The best I have managed via IPsec, with AES-NI enhancements enabled, is about 100 Mbps. I have a 500/35 connection locally and a 1 gig port at the colo. Do you have any suggestions to get higher IPsec throughput?
-
MikroTik claims IPsec throughput in excess of 1000 Mbps on some of their ARM based Routerboard products. I wonder if that's realistic? Are there crypto accelerators that work with FreeBSD/pfSense?
-
@0daymaster set MTU to 1380 or 1400 on both sides
pfSense supports AES-NI and cryptodev accelerators
see https://docs.netgate.com/pfsense/en/latest/hardware/cryptographic-accelerator-support.htmlSG-3100 and above NetGate appliances have crypto accelerators:
https://store.netgate.com/pfSense/systems.aspx