Firewall Rule to Allow RDP from WAN to LAN......Need help
-
^ looks correct? What are you looking at? It sure not the mess he posted.. Has gateway set on his wan rule, the dest is Lan Net vs wan address in his port forward.
Here is the 3 things that need to be touched to port forward rdp
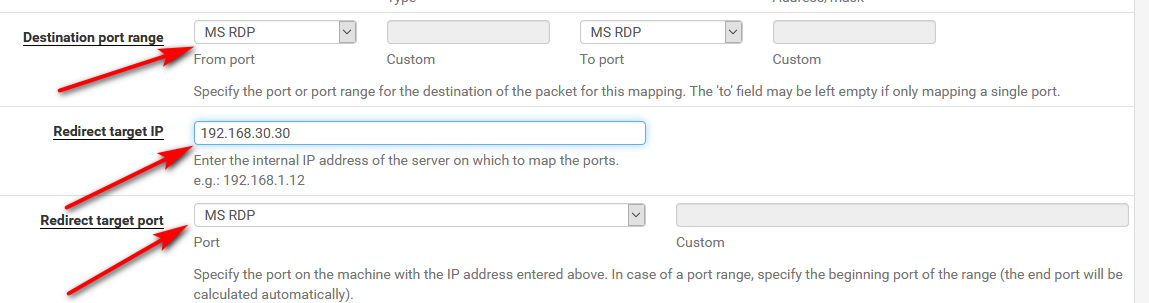
That is it, don't touch anything else - the defaults are all you need. It will create the firewall rule for you. You just need to make sure you turn off the default block rfc1918 rule because your source is actually rfc1918.
edit: Lets get tcp working before he worries about having a UDP connection ;) But sure if he wanted he could change it from default of tcp to tcp/udp.
-
I have tried with NAT Rule that did not helped so used PASS and took the screen shot at that time..
In one of the forum in netgate to mentioned gateway instead of default so I have tried that as well whether it may help...
-
List of things to check is here:
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.html
-
It should take you like 2 minutes top to trouble shoot a port forward..
Sniff on wan, do you see traffic to 3389? Sniff on Lan - do you see pfsense sending 3389 on to IP you want to send it to..
If you do - your problem is prob firewall on host your sending too, maybe rdp isn't even listening? Maybe it is using a different gateway other than pfsense? Maybe where you wanted to send it is now on a different IP? etc. etc..
Troubleshooting a port forward does not mean randomly changing settings ;)
-
Hi,
And make sure you have enabled "Remote Desktop" on your computer you are trying to RDP :) -
Thanks friends for the help, I can able to access my Windows Machines from WAN to LAN..
Two things I have done one is enabled firewall rules in WAN and added route in my source machine (ie) in WAN network.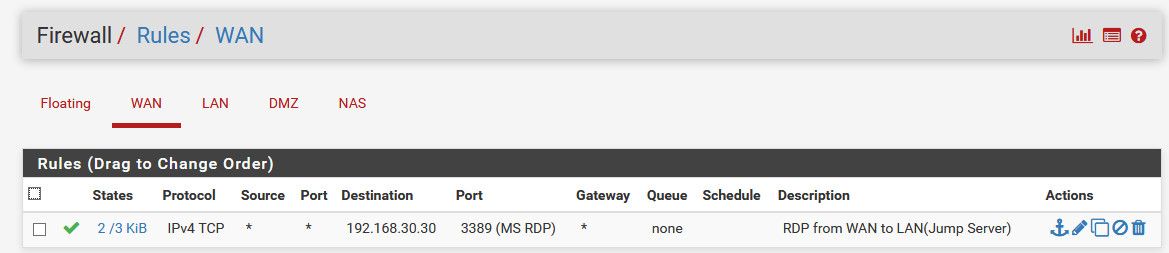
route add 192.168.30.0 mask 255.255.255.0 192.168.50.100
-
So you turned off NAT in pfsense?
-
Yes I have turned off NAT in pfsense...
now I need help in configuring Open VPN for my mentioned design... to access my LAN network through Internet...
Airtel Internet Modem -->Asus RT-AX88U Wireless Router --->PFsense-->LAN and DMZ..
I need to do triple NAT here.. apart from doing this ... can you suggest some other good options...
-
Well if you turned off nat in pfsense, then you would need to route.. And you would really need to be connected via a transit network or your going to run into issues with asymmetrical traffic unless you do host routing on each box that actually sits in any transit network (the network between routers)..
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
I need to do triple NAT here.. apart from doing this ... can you suggest some other good options...
i went back and read the entire thread again. Why do you need this part: Asus RT-AX88U Wireless Router?
Jeff
-
I doubt he does to be honest... Should just be used as AP to be honest... And now that he has nat turned off good luck getting that modem and asus to actually route and not nat ;)
He should put his modem into bridge mode, and just use pfsense as his edge nat and firewall, and wireless should just be AP... Simplifies the whole mess.
-
I want my family to connect their internet directly without PFsense..SO I have connected Asus RT-Ax88U router between Airtel internet moden and Pfsense...
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
I want my family to connect their internet directly without PFsense..SO I have connected Asus RT-Ax88U router between Airtel internet moden and Pfsense...
I'm assuming wirelessly, like for mobile devices and stuff? Or wired into the Asus? Is this so they aren't filtered or less confusing for them, or what?
You should, like @johnpoz says above, change it up a little bit.
Airtel Internet Modem (in bridge mode) -> pfsense -> LAN -> Asus RT-AX88U (VLAN'd for only your family to use)
That would make NAT-ing and VPN-ing (like you say you want to do) and etc. into or out of your network so much easier, promise.
Jeff
-
As you have explained it, its a complete and utter mess..
Isolating traffic is very simple, keeping your family away from your network is very simple and does not require such an nonsense network. Pfsense, vlan switch and AP that does vlans.. Can be done with dumb switches and and dumb AP as well - just a bit more complicated and and extra hardware depending..
But what you have drawn out is just a mess.. and complete and utter nightmare to try and actually manage.
If you explain what you want, we can show you how to do it correctly, easy and with a min budget..
-
I have below components
- Airtel Internet Modem
- TP-Link T2500G-10MPS 8-Port Gigabit L2 Managed
- Desktop Tower Server which have my LAN VMs on it.(with Two Physical NIC's)
- Asus RT-AX88U Wireless Router
- Laser Printer
I have installed pfsense on my tower server as VM.
I need the following :
- I want my family to connect internet through wifi without any disturbance even I reboot pfsense they should not get affected.
- I want to access my LAB through wifi from internal network.
- I want to access my LAB machines through internet(ie) from remote site as well.
- I want to connect my printer through pfsense LAN network.
Kindly provide me the network design to achieve above..
Thanks in Advance,
Dinu -
So bridge your modem, connect it to your VM Pfsense on wan.. Then put your networks behind, connected via your smart switch.. Do whatever vlans you want, put 3rd party firmware on your asus so you can do vlans = done!
If your soho wifi router can not run 3rd party firmware that actually supports vlans, then get a real AP.
You can connect your other vms to whatever vlans you want on your host.
Do you need a drawing?
I ran such a network for many years before I put my pfsense on actual hardware.. An I still run some VMs on different vlans. Its really basic 101 networking.. Running pfsense is not all that different than running on hardware, only difference is your running some virtual switches vs just hardware one.. Be happy to put together an example drawing if that is what you want with a few vlans, etc.
What you run as your hypervisor means nothing other than some details on how you setup up the vswitches and do some vlans on your VM Host.
Once you have a vlan capable switch, and AP that does vlans - how you segment your network is very simple. The whole thing with having the correct hardware that allows you to do what you want. A vlan capable switch and AP is key - then segmentation becomes simple configuration. The whole point behind vlans ;)
-
Can you pls put me drawing and send it to me ? It will be really helpful....
my switch have Vlan capable....
So bridge your modem, connect it to your VM Pfsense on wan.. Then put your networks behind, connected via your smart switch.. Do whatever vlans you want, put 3rd party firmware on your asus so you can do vlans = done!
As per above, wifi asus router will come behind firewall and if i reboot my pfsense then it will affect the internet which is being use by my family (TV, Mobile, Laptop, etc..) I dont want that to happen...
FYI : I have Windows 2012 R2 on my host with VMware work station installed. pfsense is on VMware workstation... already I have different Vswitch from Vmware workstation for my LAN, DMZ, freeSAN etc..
-
Any Update pls ??
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
if i reboot my pfsense
Why and the F would you do that.. The only time you need to reboot pfsense would be to upgrade its version.
-
I said I don't my family to use PFsense firewall... They have to access the internet without any disturbance...
Do you have any recommended diagram ?
If not I will prepare on my own....