Problem CARP
-
Tell me please. 2 pfsense are configured in carp mode. 2 virtual ip - wan and lan. On the first, gw responds to ping and is online, the second does not see gw and offline. What could be the problem? With L2, everything is fine. ISP sees arp. MAC reaches gw. On the second pfsense there is arp gw as well. The problem is somewhere on pfsense itself. On a laptop ip works. But pfsense does not ping
-
Have you separate WAN IPs on each pfSense or only one?
-
@viragomann said in Problem CARP:
Have you separate WAN IPs on each pfSense or only one?
Separate. All 3 ip (pfsense1 pfsense2 and VIPs) are all different.
-
So I gues, it's on your outbound NAT. Have you changed the rule for 127.0.0.1/8 (if you're talking about IPv4) to use the virtual IP? This source (pfSense itself) should its unique WAN IP.
-
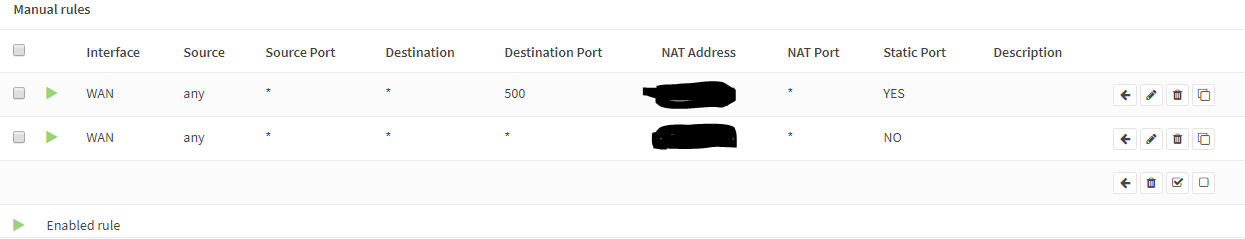
-
The source "any" includes 127.0.0.1/8, of course.
Add a separate rule for 127.0.0.1/8, set the translation address to WAN address and put it to the top of the rule set.
The rule will be synced to the second box if you have enabled XMLRPC sync. -
@Pavel88 You know that this Screenshot is about OPNsense, not pfSense and that you're probably in the wrong forums?
Besides that, deleting any automatically created NAT rules and replacing them with "any" isn't recommended on either platform. Why did you remove them? It has a reason, why we differentiate localhost 127.0.0.1 and the LAN network when doing outbound NAT as @viragomann is absolutely right above. Without the right outbound NAT for 127.0.0.1 (-> has to be WAN address) there will be no internet on the standby node as it can't translate to your WAN VIP without being master.