Tunnel Up, Pings Pass but UDP and TCP Fail
-
I'm working to make a full mesh of my four pfSense routers/sites using IPsec tunnels. I'm on my last tunnel and all of a sudden I'm having issue. I created my tunnel P1 and it came up fine. I then went back and created my P2 and restarted the tunnel. It comes back up and I can ping from one side to the other and vise versa. When I try to do a traceroute across the tunnel it fails. If I set tracert to ICMP it will work. I have firewall rules set to allow all on both ends. Both routers already have 2 working tunnels to different routers so I'm a bit confused. I attached firewall rules, P1 config, P2 config, and traceroutes. Thanks in advance.
Edit: I have been informed my tests should fail in any situation. I re-tested by connecting a laptop to one of the routers and trying to load the web page of the other using the remote tunnel IP. That is also failing.
Site A
IPsec FW Rules
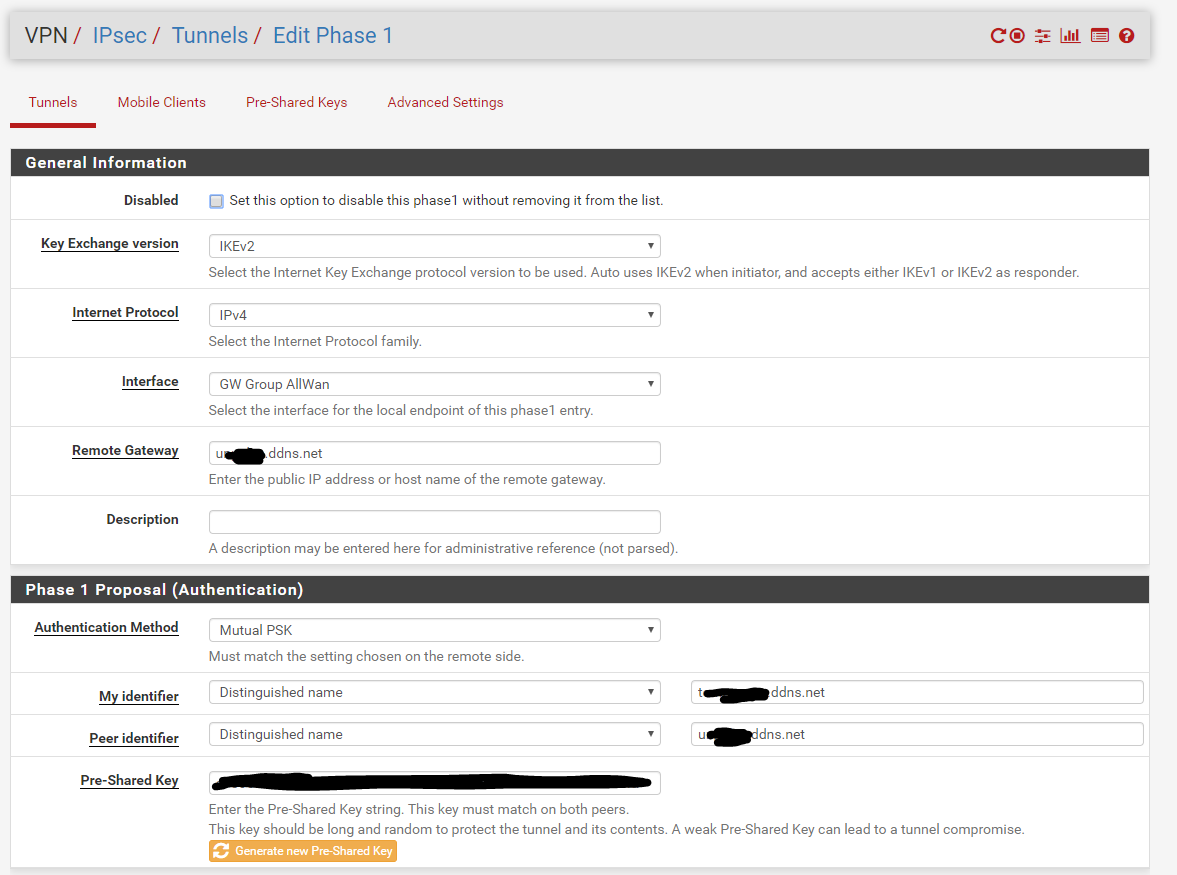
P1 Config
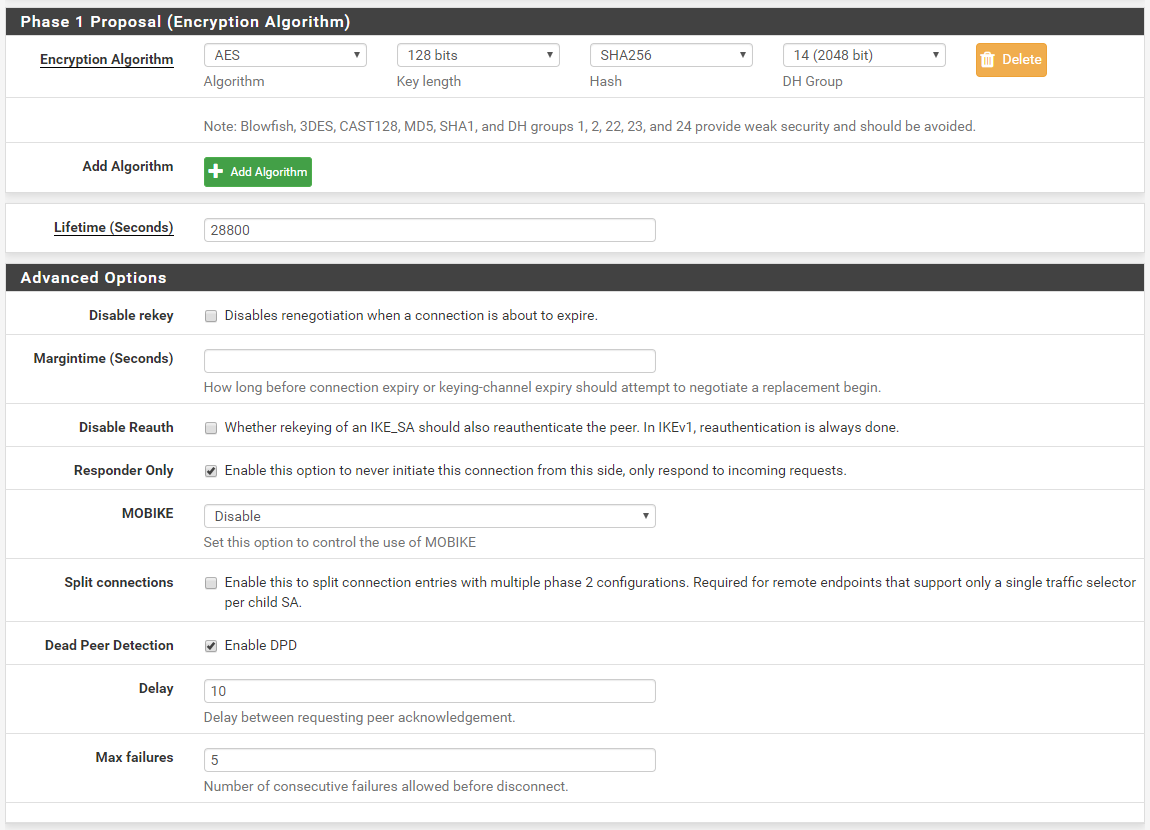
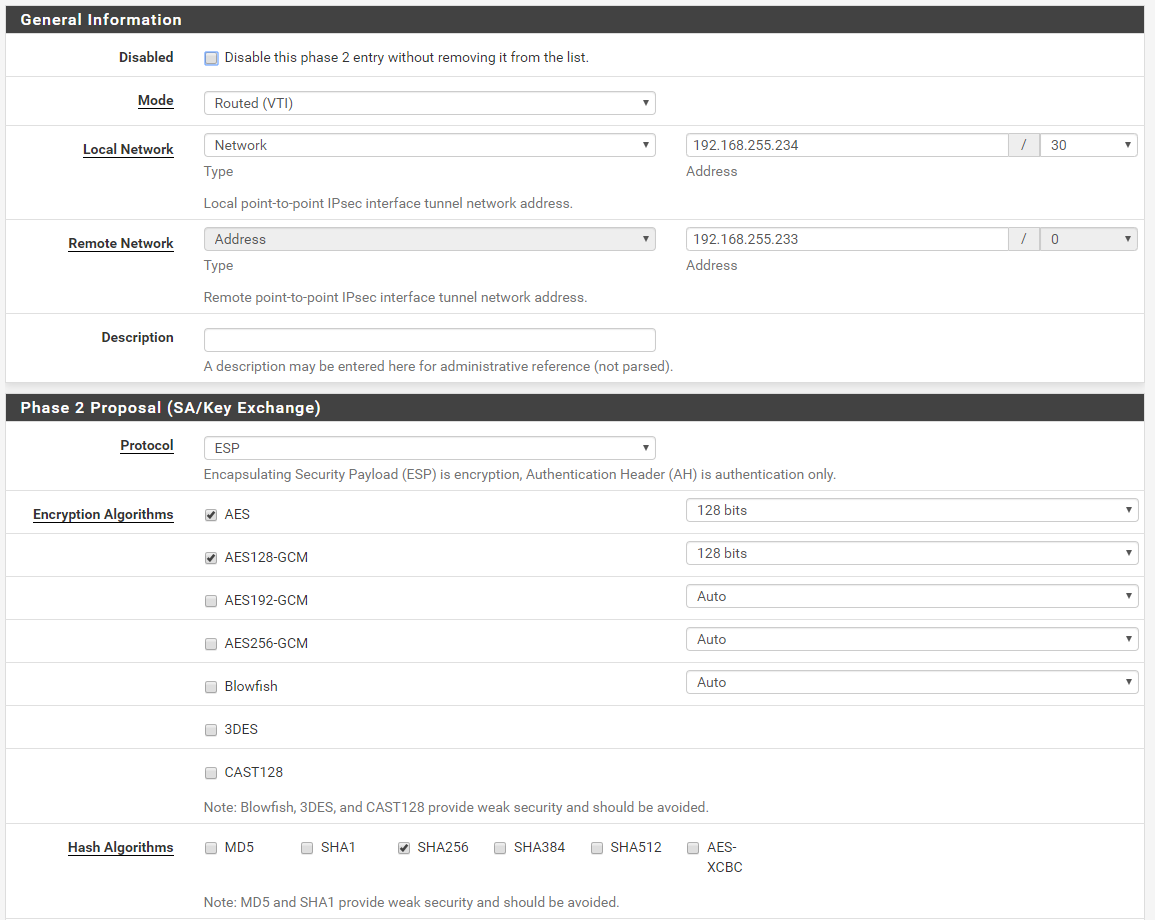
P2 Config
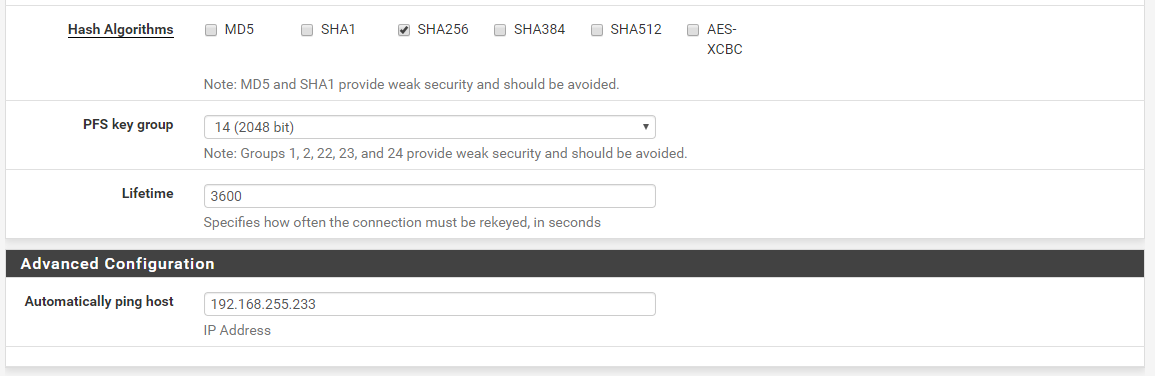
Traceroute UDP
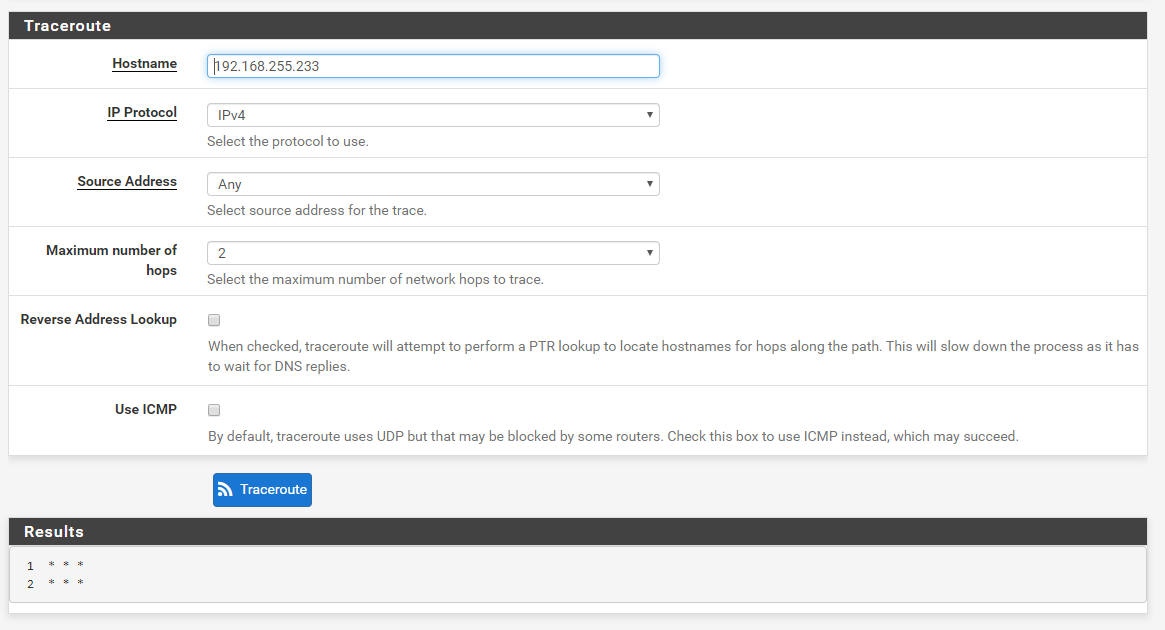
Traceroute ICMP
Site B
IPsec FW Rules
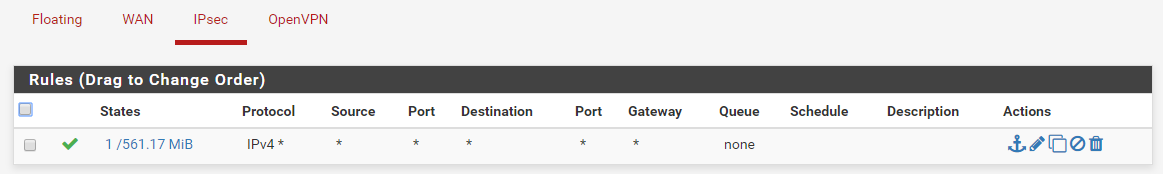
P1 Config
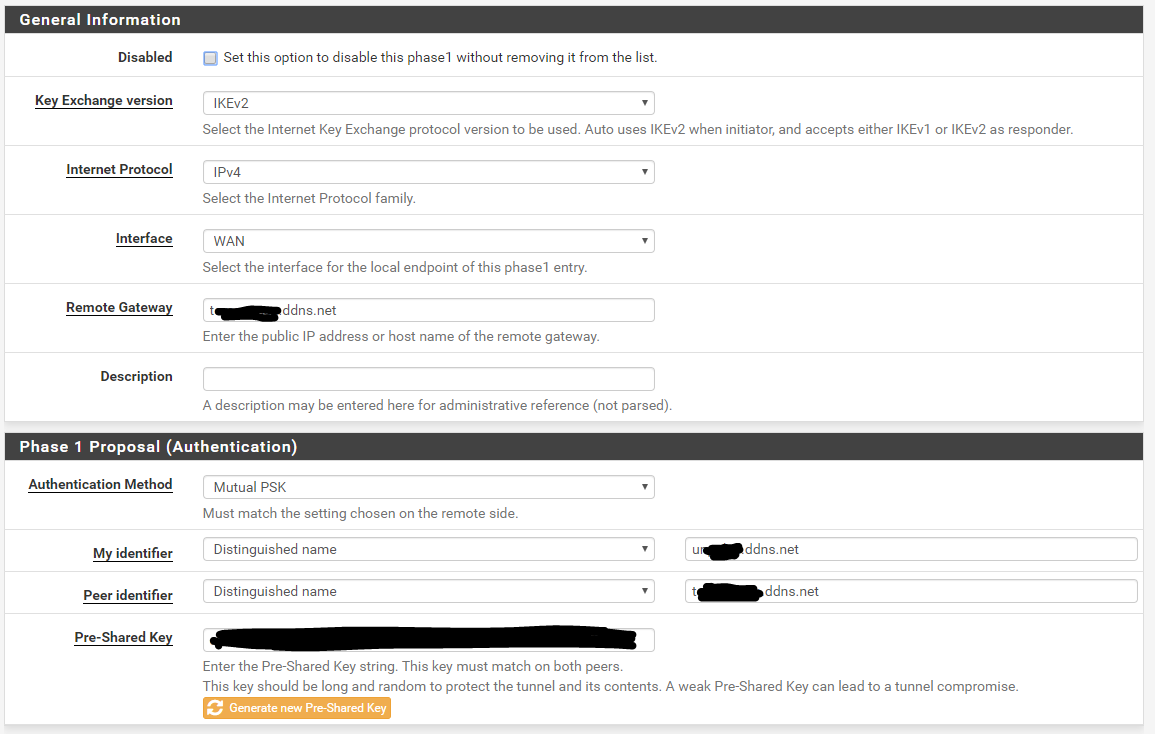
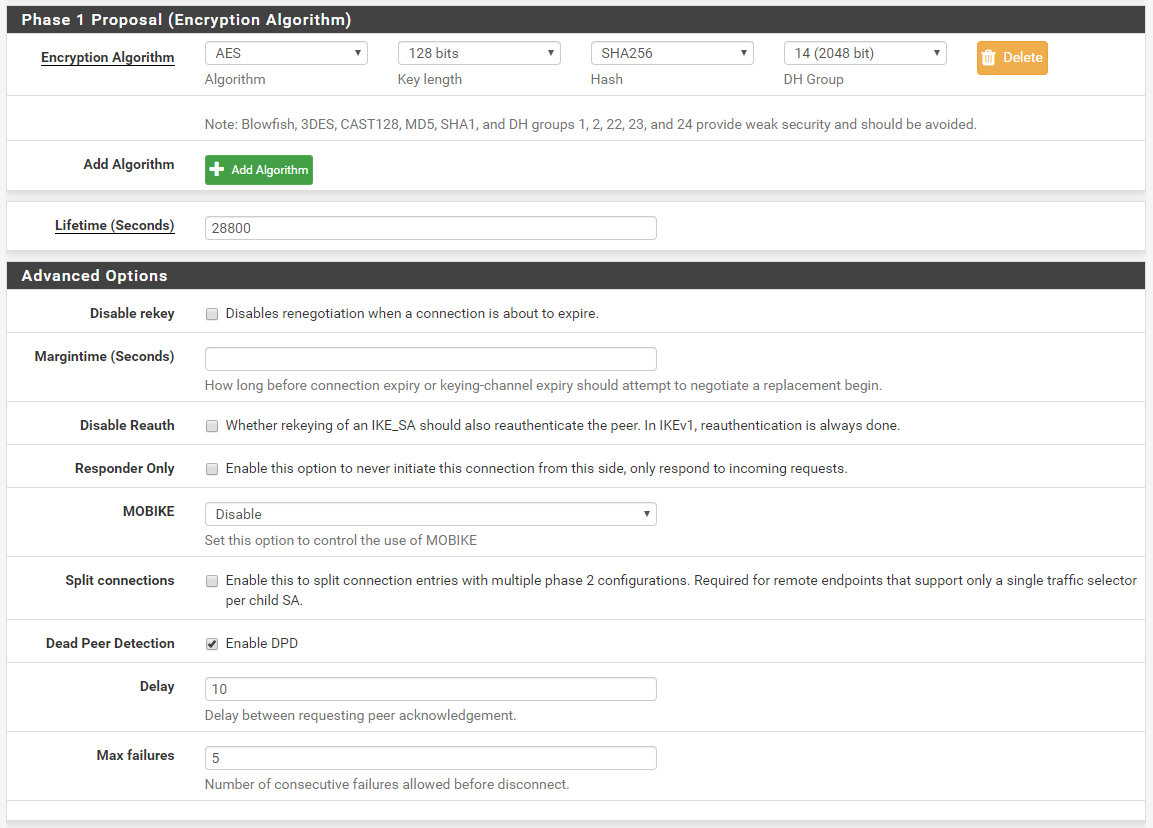
P2 Config
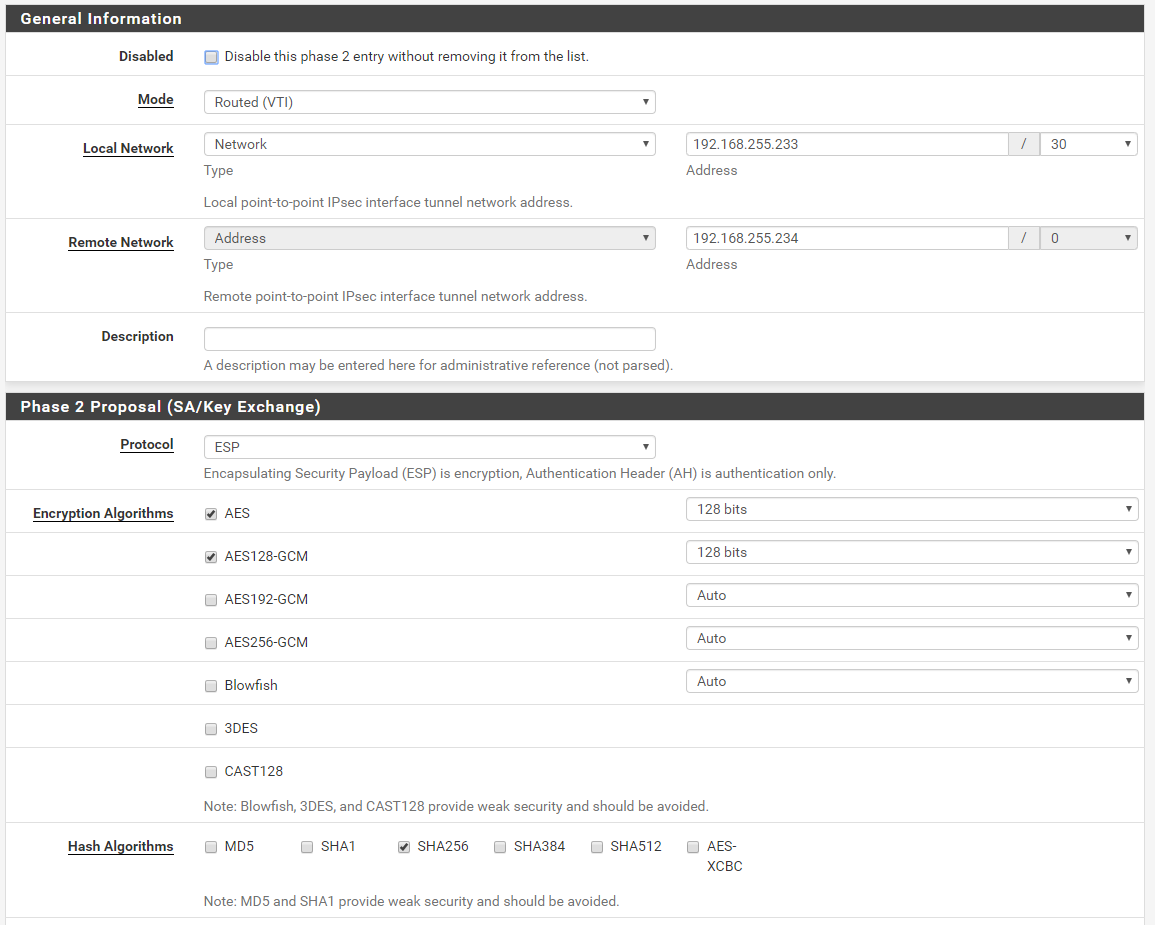
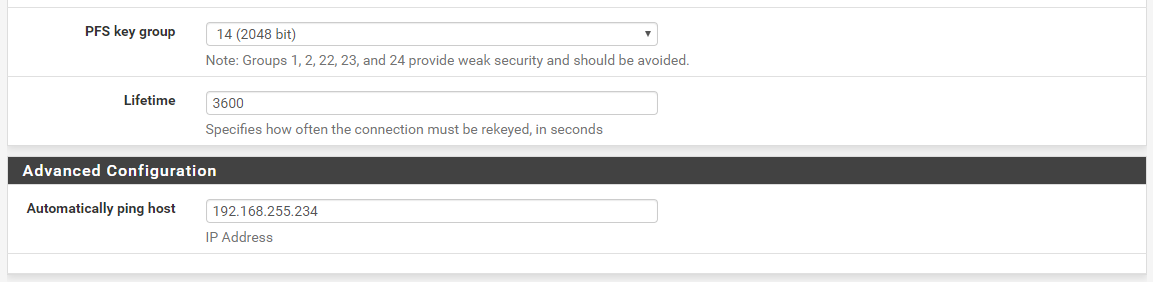
Traceroute UDP
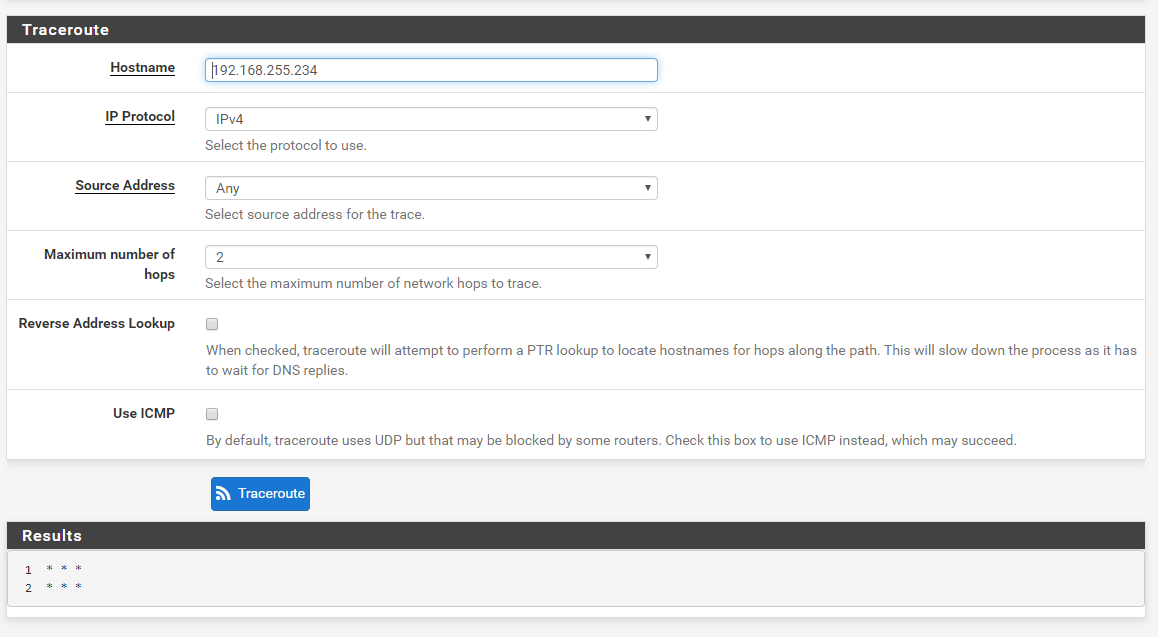
Traceroute ICMP
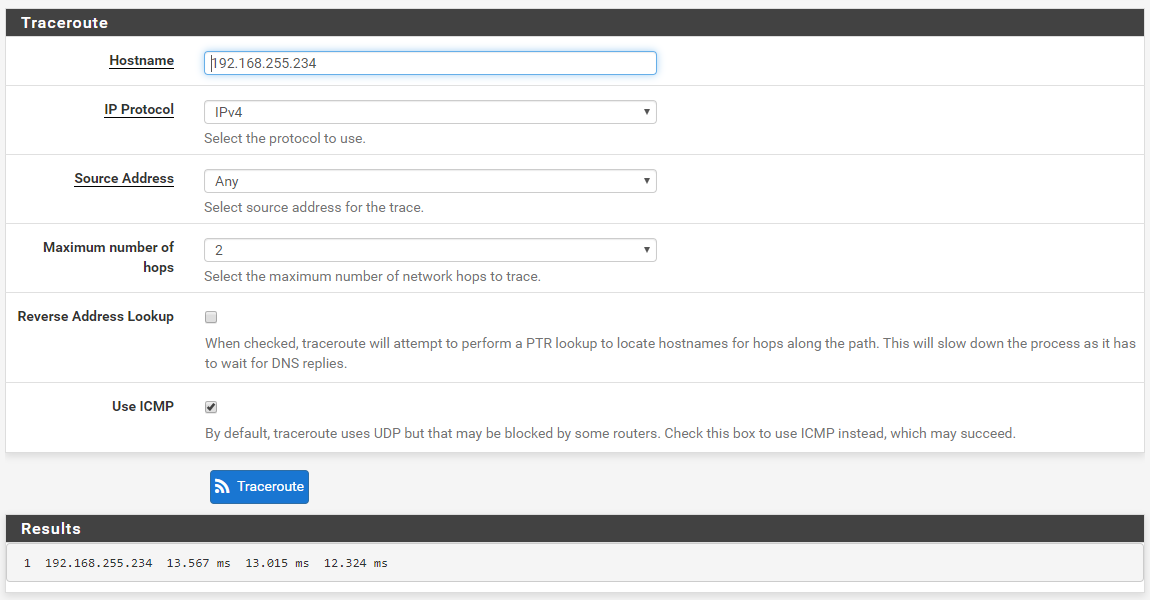
-
Did you ever figure this out? Same thing is happening to me, but I am not using VTI I am using policy routing (tunnel mode in the phase 2). That should not make a difference, though. I have a feeling our issue is the same. It's frustrating because at first I thought I had MTU / MSS issues, but now it seems that perhaps it is protocol dependent.
-
Actually, for me, traceroute with UDP and ICMP are working, but TCP is not. Seems that TCP replies are not coming back, based on packet capture.
-
I think eventually it just fixed itself or I rebuilt tunnels/routers until it worked. My recent experience with ipsec tunnels in pfSense has been very hit or miss. A lot of weird issue like this that never really get fixed they just magically start working or don't. You can't check my post history for my ipsec issues.
-
@scurrier I think I have the same issue.
https://forum.netgate.com/topic/155727/site-to-site-ipsec-suspect-not-passing-tcp-traffic
How did you make traceroute use a specific protocol?