IPSec connection with NAT/BINAT translation
-
Hi,
I need help to create an IPSec tunnel between 2 Networks.
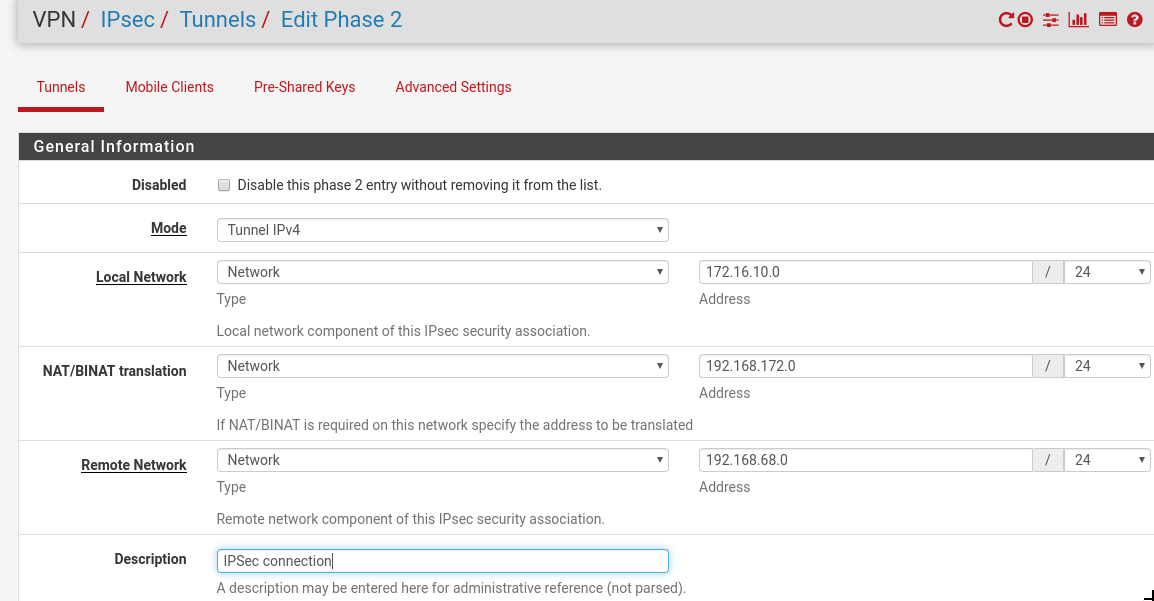
Remote network: 192.168.68.0/24
My local network: 172.16.10.0/24
It is not possible to route from the remote network into my local 172.16.10.0/24-network because this network is already in use.
So I want to use the 192.168.172.0/24 Network as natting-Network.
The IPSec connection is established, but I cannot ping the host 192.168.68.10 from the pfsense or ping in the other direction the 192.168.172.1 whicht should be translated into 172.16.10.1->My pfsense LAN-IPThats what I thought should do the natting:
I am missing anything? Im pretty sure that I allow everthing in my Firewallrules.
Some weeks ago I solved a similar Problem on a Sophos Firewall with 1:1 nat-Rules - maybe I understand the NAT/BINAT-Rule in pfsense IPSec wrong and have to add Rules under Firewall->NAT?
Many thanks for your in advance,
Aleks -
@aleksunil
Hey
show phase 2 settings on the other side of the tunnel. -
That looks fine.
The other side will create a tunnel for:
Local:192.168.68.0/24
Remote: 192.168.172.0/24There will be a 1:1 mapping between 172.16.10.0/24 and 192.168.172.0/24 on your side
If you connect from 172.16.10.135 on your side they will see if coming from source 192.168.172.135 on their side.
If they connect to 192.168.172.23 they will actually get 172.16.10.23 on your side.
You cannot ping the 192.168.172.10 address directly because it does not actually exist on the firewall itself. It is only used for NAT through IPsec. You will have to test using traffic that is actually flowing through IPsec.
Pinging 192.168.172.1 from the other side (which will actually ping 172.16.10.1 on your firewall) should work as long as it is allowed by the firewall rules on your end and you are sourcing it from something in 192.168.68.0/24 on their end.