PFSense/Unbound Rejecting Queries
-
I'm trying to understand why PFSense is rejecting these DNS queries.
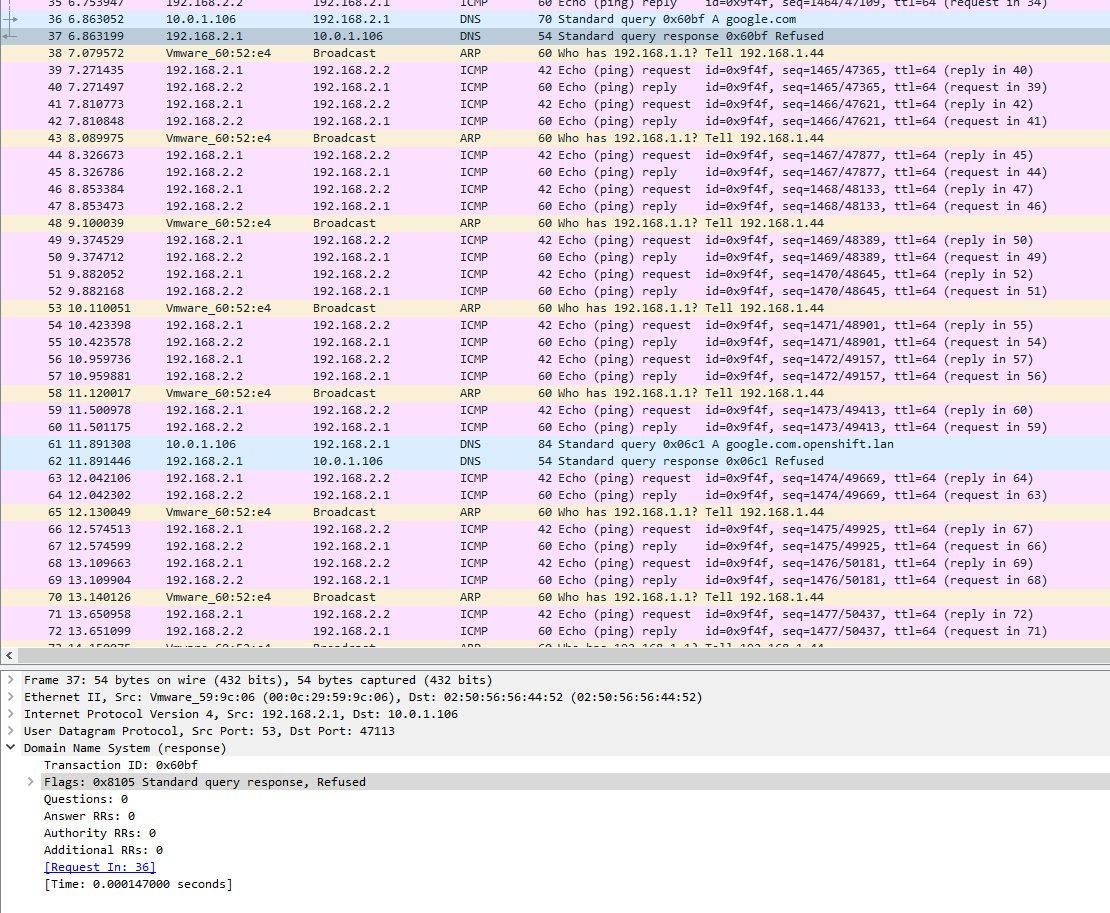
Here are the DNS resolver settings. For starters, the ALL interface is selected, but so is the OpenShift interface which is receiving these queries.
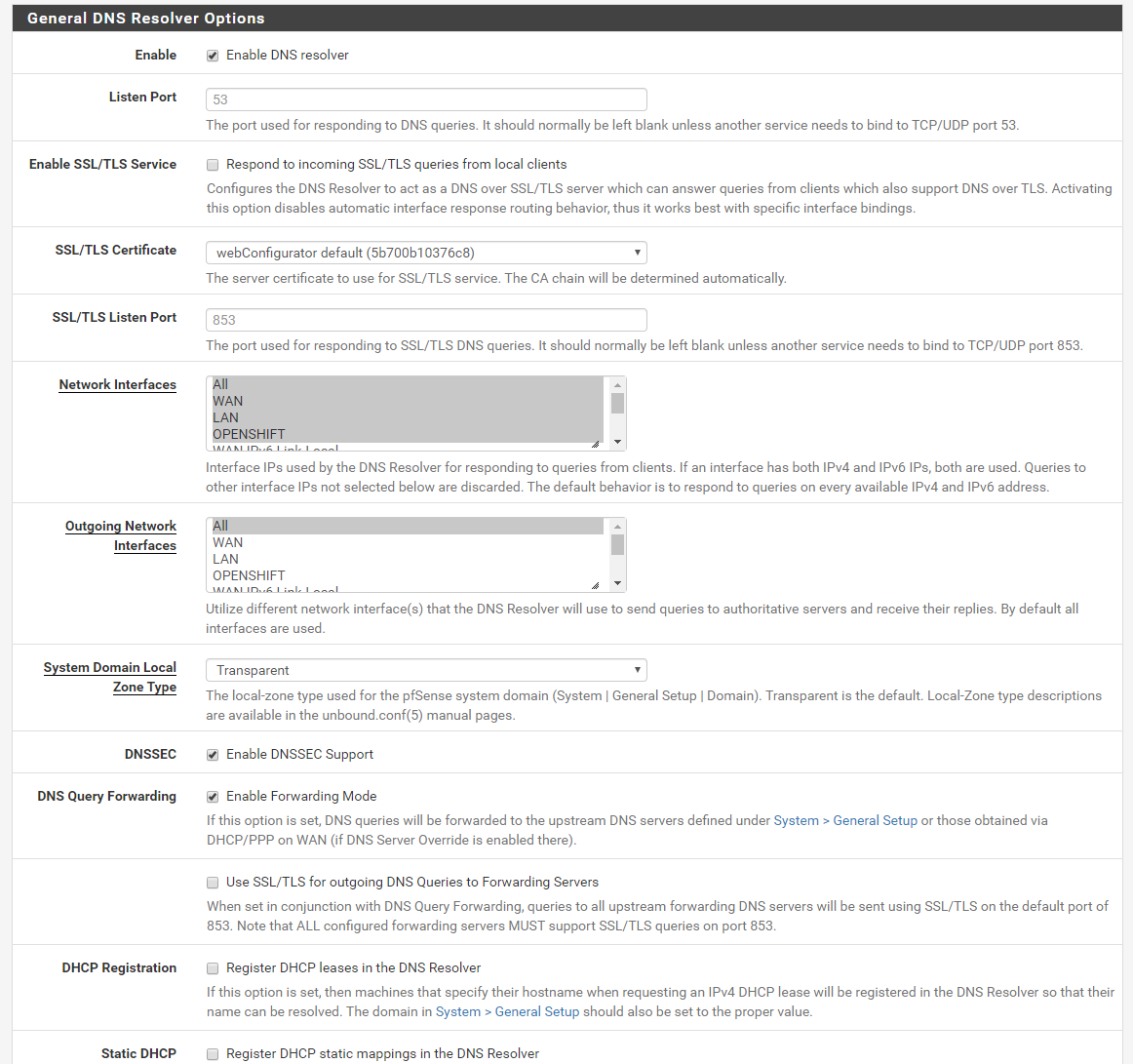
-
REFUSED is usually due to policy reasons. What happens if you select only All for Network Interfaces? Maybe something weird is happening of you select All and other specific interfaces.
-
a) rejecting sth. like "google.com.yourdomain.tld" isn't unexpected.
b) why are your selecting "ANY" but adding WAN, LAN, Openshift as network interface IPs?
c) Do you have anything set in the other tabs (access lists etc.)?
d) Is there anything wrong with resolving? Why do you forward DNS? -
I'm not sure if the issue has been solved, but I had the same issue and the issue drove me crazy. But I found out, that I just need to create an Access List, that accepts Requests from my Clients. Easiest is to creat an allow all list since I've already done the Filtering in Firewall-Rules and in the Listening interfaces Tab.
To make the ACL simply go to Access Lists:
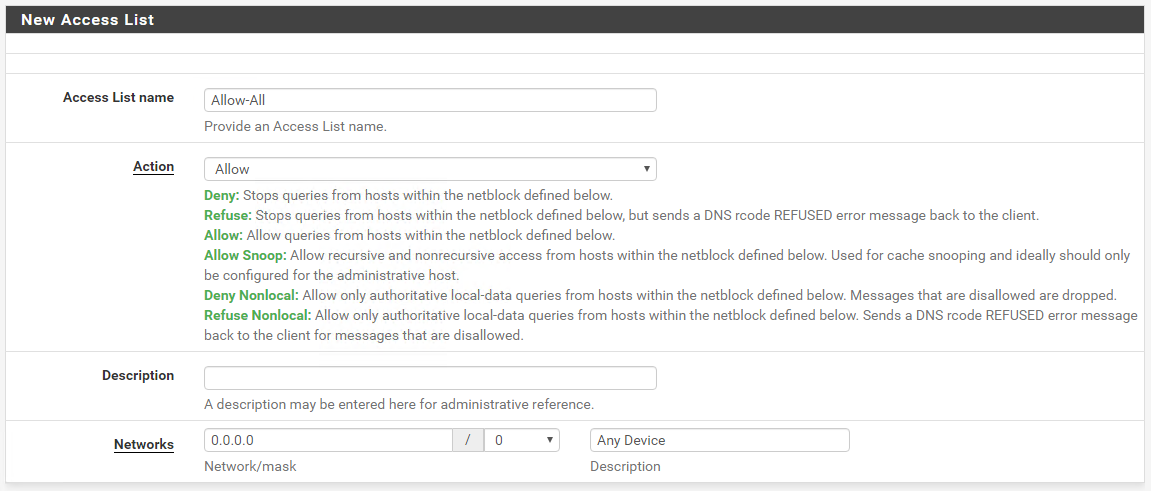
And then create a new one, that allows the Clients:
Hope I could help you and maybe other people experiencing this issue.
-
FYI- Do not make an ACL like the one shown in that screenshot. It's incredibly dangerous.
You never want to allow from all (
0.0.0.0/0) since one mistake with your WAN rules could lead to you acting as a DDoS reflector, among other things.Only add ACLs for specific local networks to which you need to provide access. Directly connected networks are typically added to the ACL list automatically, though they don't show in the GUI.
In this case, since the query was refused from the client address
10.0.1.106, then you'd probably want to add an ACL for that particular subnet (most likely10.0.1.0/24) -
I'm really curious on the why behind this. It worked for me but I did a lot of searching and watching set up videos before I installed pfsense and not a single one of them mentioned this.
I'm just worried that my set up puts me in a weird minority that requires me to use access lists.
-
Out of the box pfsense will create auto acl that allows all locally attached networks to query unbound.
Unless you checked this box in advanced unbound

Any locally attached network will be able to query unbound. But downstream networks, or tunnel networks (vpn) would not.
If you want such networks to be able to query unbound, then you would need to create an acl to allow them.
-
Thanks. That option was not checked but adding the ACL resolved my problem nonetheless.
-
I didn't expect it to be checked, if your default and your other networks worked without you creating acls ;) Mine is checked because I like seeing all my ACLs vs having auto.
-
Same problem here. I need to toggle the option in the GUI twice,
after that in works properly. Removing the ACL afterwards doesnt change anything.
It looks like, there is a glitch in the GUI.
It works for some time, but afterwards it needs the ACL again. So no great news here.