NATing behind IPSec Vti Tunnel
-
I've managed to setup an IPSEC (vti) tunnel between PFsense running on AWS and my Cisco router at home. Reason for this, is to have access to a public IP since my stupid ISP has resorted to NATing its customers. So basically i want to point to public IP on pfsense in the cloud, and be able to reach my local services at home. However, i'm stuck on the NAT part. If i use my phone to connect to the ipsec vpn, i can access my local network, but outside of the vpn, no luck. Doing a TCPDUMP on the local server shows tracffic hitting it but port still shows blocked. See screenshots
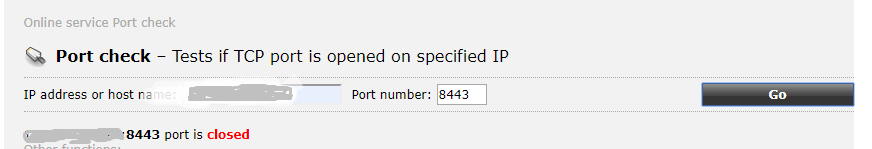
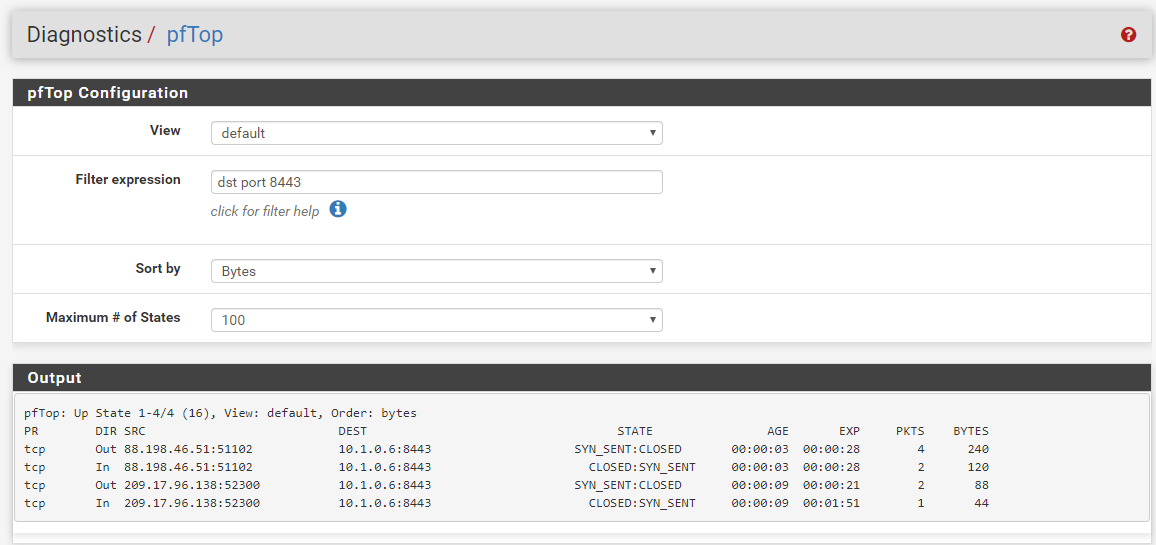
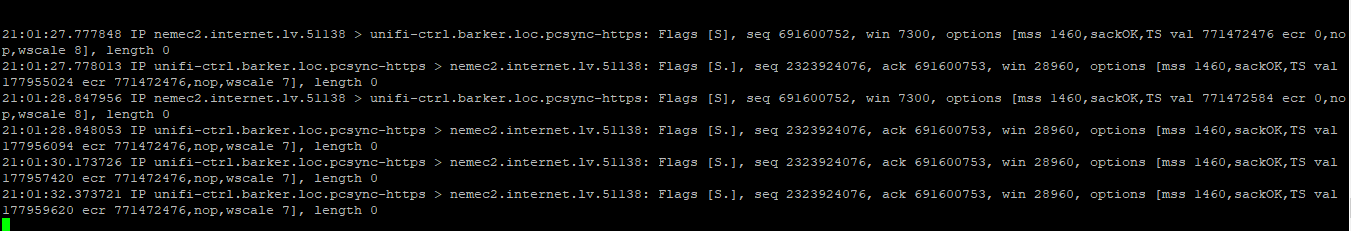
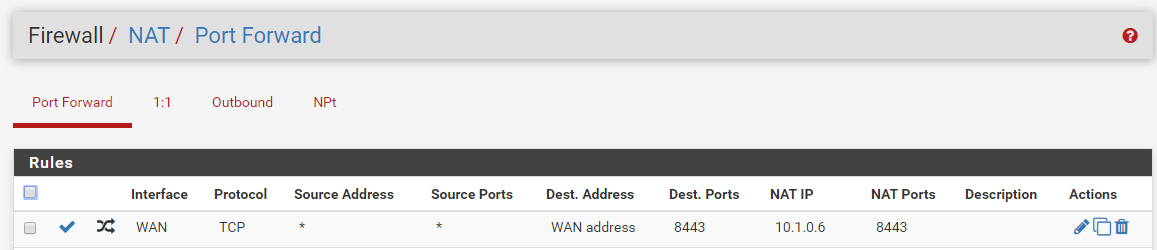 image url)
image url)

-
So Your home is behind NAT now so you cannot connect directly.
You want to:
- Connect via IKEv2 using your phone into an AWS IPsec
- From there, go across a VTI to your home network
?
Where does the NAT come in?
Probably need a better explanation of exactly what you want to do and what is not working. Be descriptive and let us know what subnets are in what part of the network.
A diagram would be great.
-
I'm already able to connect to VPN using phone and access my home network. But that's not the goal. I want to access my home network without having to connect to VPN. Hence the NAT from outside public to host behind tunnel.
Phone > Public IP of pfsense > VPN Tunnel > Home Network > NVR
iphone > 55.55.55.55 > 10.2.0.0/30 > 172.10.15.0/24 > 172.10.15.20:554I want to access 55.55.55.55:554 from internet
-
I still don't know what you are representing with that diagram.
But if you want to connect to a WAN from an arbitrary internet address and hit a port forward to something across an IPsec VTI, you cannot do that with IPsec.
You can do it with OpenVPN, though.
-
i also have openvpn up, can you explain how to do this?
what about if i do a L2TP over Ipsec? or gre ? -
https://forum.netgate.com/post/489029
The diagram is down below. There are two. That was written against the one with the blue symbols. The version of pfSense there is old but the principles haven't changed.