[solved] VPN Tunnel via PIA seems not to be working.
-
Hi All
Repost from the NAT section,
Im very new to FPsense and not a network guy, but do know the basic of networking, so....
Im trying to setup a box with the following interfaces
LAN:192.168.8.0/24
DMZ:172.16.0.0/24
External:217.x.x.x/29Currently my lan interface is .2 - later i want to have 2 ips on that interface - one that routes trafic directly to the internet, the other that routes traffic via VPN, so i can chose how to route, either by the default gw on the client, or via outbound rules defined on the fpSense box, which is running on vmware.
Right now, i can create a bsic outbound nat rule that routes all trafic just fine to the internet, but im hvping problem routing via PIA VPN - the tunnel seems to be up, but im not able to ping via the VPN (using the diag/ping menu)
Here is a few screenshots of my rather basic setup:
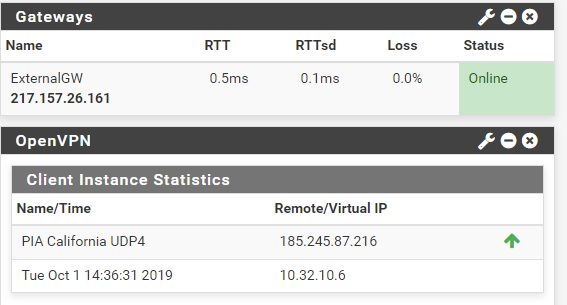
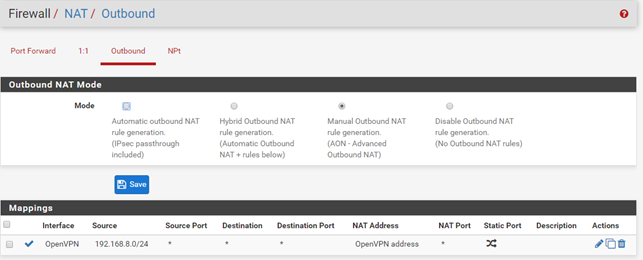
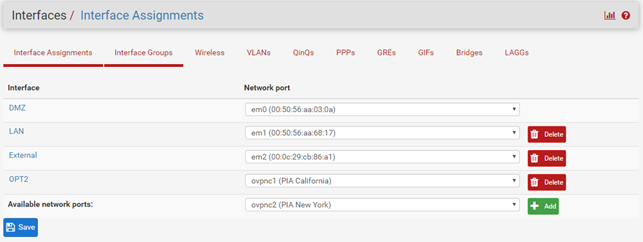
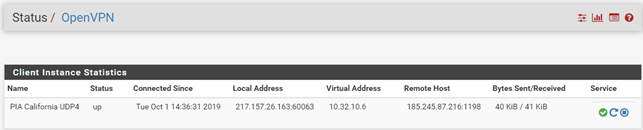
And the VPN Client log.
Oct 1 14:36:31 openvpn 39557 Initialization Sequence Completed Oct 1 14:36:31 openvpn[link text]([link url]([link url]([link url](link url)))) 39557 /usr/local/sbin/ovpn-linkup ovpnc1 1500 1542 10.32.10.6 10.32.10.5 init Oct 1 14:36:31 openvpn 39557 /sbin/ifconfig ovpnc1 10.32.10.6 10.32.10.5 mtu 1500 netmask 255.255.255.255 up Oct 1 14:36:31 openvpn 39557 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Oct 1 14:36:31 openvpn 39557 TUN/TAP device /dev/tun1 opened Oct 1 14:36:31 openvpn 39557 TUN/TAP device ovpnc1 exists previously, keep at program end Oct 1 14:36:30 openvpn 39557 /usr/local/sbin/ovpn-linkdown ovpnc1 1500 1542 10.63.10.6 10.63.10.5 init Oct 1 14:36:30 openvpn 39557 Closing TUN/TAP interface Oct 1 14:36:30 openvpn 39557 NOTE: Pulled options changed on restart, will need to close and reopen TUN/TAP device. Oct 1 14:36:30 openvpn 39557 Preserving previous TUN/TAP instance: ovpnc1 Oct 1 14:36:30 openvpn 39557 WARNING: cipher with small block size in use, reducing reneg-bytes to 64MB to mitigate SWEET32 attacks. Oct 1 14:36:30 openvpn 39557 Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication Oct 1 14:36:30 openvpn 39557 WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC). Oct 1 14:36:30 openvpn 39557 Incoming Data Channel: Cipher 'BF-CBC' initialized with 128 bit key Oct 1 14:36:30 openvpn 39557 Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication Oct 1 14:36:30 openvpn 39557 WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC). Oct 1 14:36:30 openvpn 39557 Outgoing Data Channel: Cipher 'BF-CBC' initialized with 128 bit key Oct 1 14:36:30 openvpn 39557 OPTIONS IMPORT: --ifconfig/up options modified Oct 1 14:36:30 openvpn 39557 OPTIONS IMPORT: compression parms modified Oct 1 14:36:30 openvpn 39557 OPTIONS IMPORT: timers and/or timeouts modified Oct 1 14:36:30 openvpn 39557 Options error: option 'route' cannot be used in this context ([PUSH-OPTIONS]) Oct 1 14:36:30 openvpn 39557 Options error: option 'dhcp-option' cannot be used in this context ([PUSH-OPTIONS]) Oct 1 14:36:30 openvpn 39557 Options error: option 'dhcp-option' cannot be used in this context ([PUSH-OPTIONS]) Oct 1 14:36:30 openvpn 39557 Options error: option 'redirect-gateway' cannot be used in this context ([PUSH-OPTIONS]) Oct 1 14:36:30 openvpn 39557 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 209.222.18.222,dhcp-option DNS 209.222.18.218,ping 10,comp-lzo no,route 10.32.10.1,topology net30,ifconfig 10.32.10.6 10.32.10.5,auth-token' Oct 1 14:36:29 openvpn 39557 SENT CONTROL [1efe3a4d68841b4268e0aba6bc46aadb]: 'PUSH_REQUEST' (status=1) Oct 1 14:36:28 openvpn 39557 [1efe3a4d68841b4268e0aba6bc46aadb] Peer Connection Initiated with [AF_INET]185.245.87.216:1198 Oct 1 14:36:28 openvpn 39557 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA Oct 1 14:36:28 openvpn 39557 VERIFY OK: depth=0, C=US, ST=CA, L=LosAngeles, O=Private Internet Access, OU=Private Internet Access, CN=1efe3a4d68841b4268e0aba6bc46aadb, name=1efe3a4d68841b4268e0aba6bc46aadb Oct 1 14:36:28 openvpn 39557 VERIFY EKU OK Oct 1 14:36:28 openvpn 39557 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Oct 1 14:36:28 openvpn 39557 Validating certificate extended key usage Oct 1 14:36:28 openvpn 39557 VERIFY KU OK Oct 1 14:36:28 openvpn 39557 VERIFY OK: depth=1, C=US, ST=CA, L=LosAngeles, O=Private Internet Access, OU=Private Internet Access, CN=Private Internet Access, name=Private Internet Access, emailAddress=secure@privateinternetaccess.com Oct 1 14:36:28 openvpn 39557 TLS: Initial packet from [AF_INET]185.245.87.216:1198, sid=178a35ee 21a89d95I have a few custome client settings as well:
reneg-sec 0
remote-cert-tls server
persist-key
persist-tun
route-nopullCan anyone see what im mssing or have done wrong, thanks
PS. i know PIA might not be the best choise given the current laws in the US, but might change that in the future.
/Stig -
@stig-joergensen said in VPN Tunnel via PIA seems not to be working.:
Currently my lan interface is .2 - later i want to have 2 ips on that interface - one that routes trafic directly to the internet, the other that routes traffic via VPN, so i can chose how to route, either by the default gw on the client, or via outbound rules defined on the fpSense box, which is running on vmware.
It want work that way. You can do the routing with policy routing firewall rules, but you can only decide the route on the basis of source or destination addresses, not on the gateway address it uses.
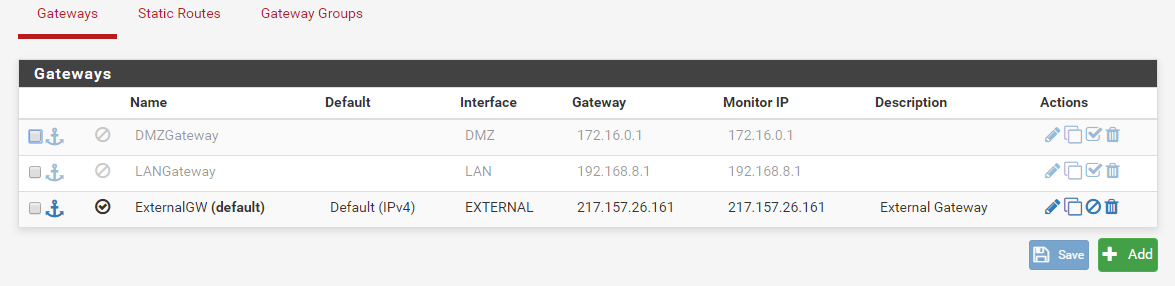
If you want to do it that way, you have to use different interfaces on pfSense.For policy routing you have to add a firewall rule or edit an existing one, open the Advanced Options, go down to the gateway section and select the particular gateway you want. For PIA select OPT2 here.
-
Ok, then ill add a new interface when that time comes.
But right now, i cannot get it to route via the VPN tunnel. Im not sure the tunnel works, it show as up, but i cannot ping the lower address on the far side (but ive read somewhere, that ping might not be the best choise to troubleshoot the vpn tunnel).
So how can i even validate the tunnel is working?
-
Check out your public IP, e.g. here: https://whatismyipaddress.com
-
Yes, and thats what i do - but i get connection timeout when the outbound nat rule is using the VPN interface - but if i change that to use the external interface, then it works as expected.
Which is why i dont think the tunnel is working, even though it states it up.
-
I guess it's on the policy routing rule. Have you configured it?
Post a screenshot.Which PIA do you use? The interface assignments screenshot shows two, but only one has an interface assigned.
-
That might be what i have missed, i cant recall anything about policy routing, will check when i get home.
Im using the California one (i made two, to see if it was the server end that had an issue - with different server addresses, but same settings)
Will post once i get home to check up on this.
Thanks.
-
@viragomann said in VPN Tunnel via PIA seems not to be working.:
I guess it's on the policy routing rule. Have you configured it?
Ehhh, where do i find these policy routing rules?
Under firewall/rules or ?
-
@stig-joergensen said in VPN Tunnel via PIA seems not to be working.:
Ehhh, where do i find these policy routing rules?
@viragomann said in VPN Tunnel via PIA seems not to be working.:
For policy routing you have to add a firewall rule or edit an existing one, open the Advanced Options, go down to the gateway section and select the particular gateway you want. For PIA select OPT2 here.
-
but PIA or OTP2 dont have a gateway
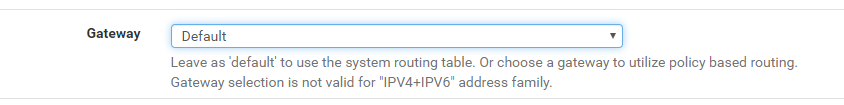
There is only the external gateway defined here:
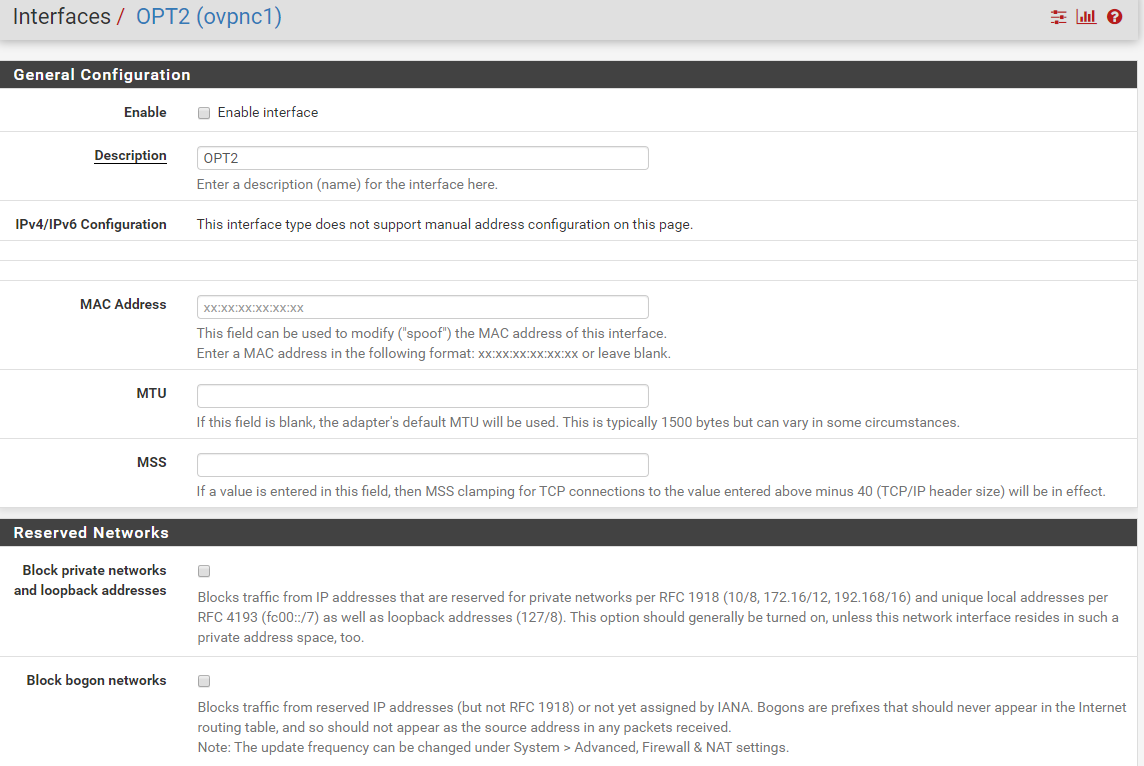
and i cannot edit the interface OPT2 (otherwise i would have renamed it) due to Chrome autofill
-
If you assign an interface to the OpenVPN instance and activate it, it will appear.
You didn't enable it. -
Hmm, here is where chrome autofill messes stuff up
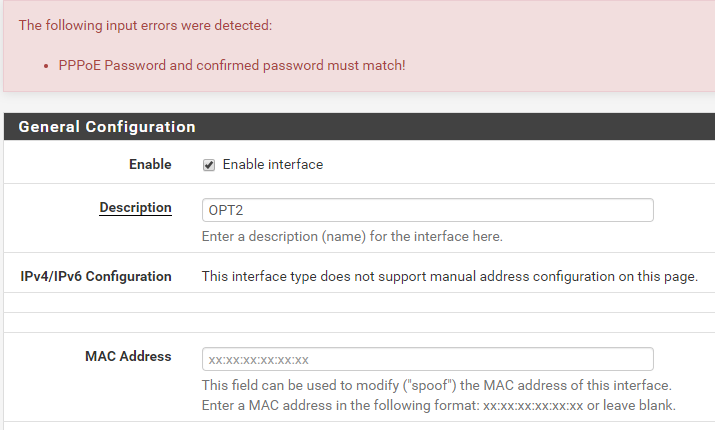
The MAC Adress is prefilled with username but clearing this is apperently not enough
I think a hidden field exists - will see how i can get chrome to ignore autofill on this page..
-
Never seen this error on OpenVPN interfaces.
Maybe it helps if you change the interface assignment to something else the check if the field are filled and delete if, then switch back to the OpenVPN instance.
-
By using guest browsing i was able to make it work:
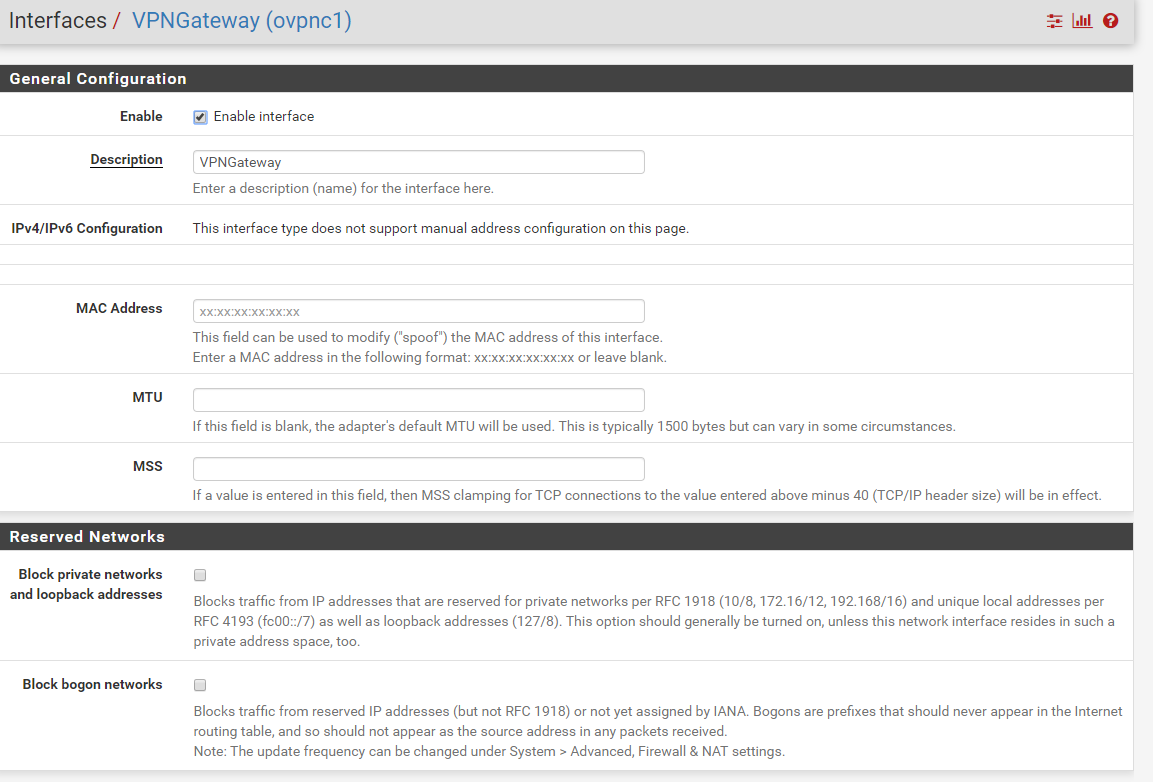
but sadly it sais gateway offline:
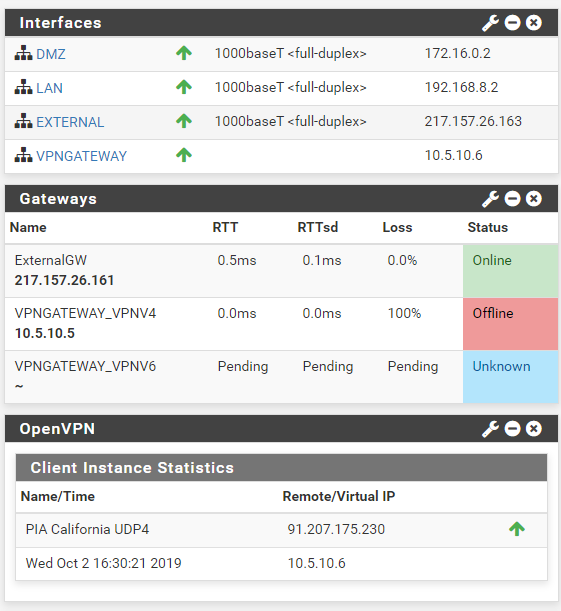
with this config:
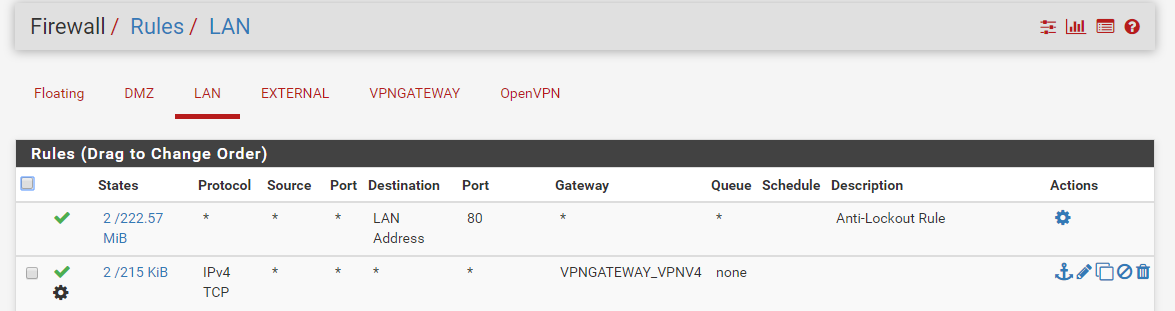
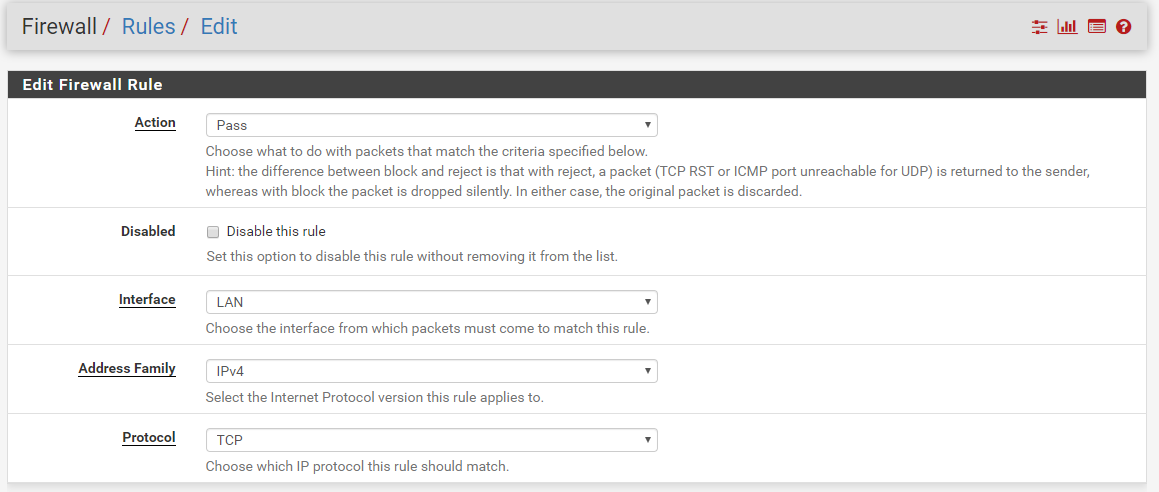
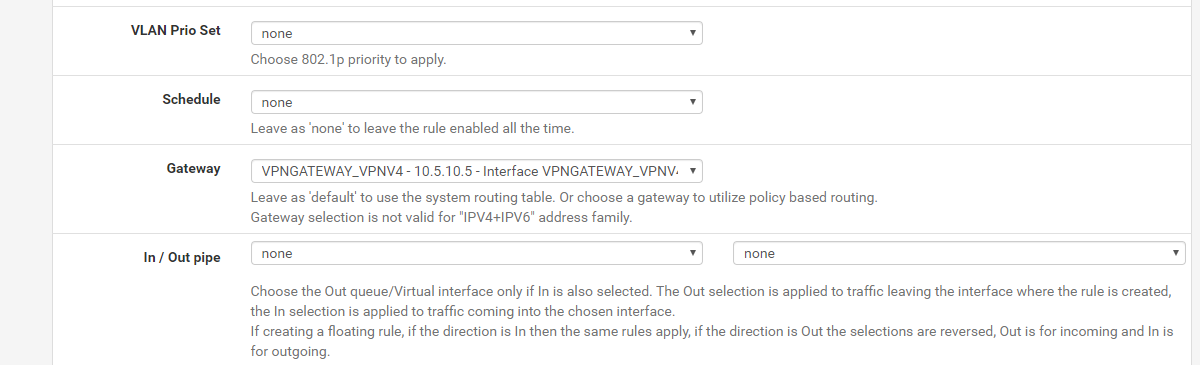
-
@stig-joergensen said in VPN Tunnel via PIA seems not to be working.:
but sadly it sais gateway offline:
That means that the gateway address doesn't respond to pings. Maybe the outbound traffic works anyway.
-
Damn, you are right - it does infact work - just not with ping... tracert works just fine - and internet browseing also
Thanks a million - i knew i was something very simple...
Is their a method where I can change how it discovers if the gateway is up?
-
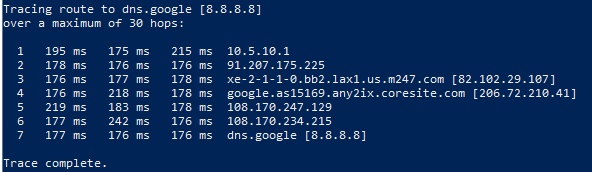
is there a way i can mark this as solved?
-
@stig-joergensen said in VPN Tunnel via PIA seems not to be working.:
Is their a method where I can change how it discovers if the gateway is up?
You may entering any other public address which responses on ping in the gateway settings at monitoring. System > Routing > Gateways. E.g. 8.8.8.8.
However, I don't know if pfSense automatically routes that over the VPN. So you may test it first. Otherwise you can additionally set a static route.Marking as solved is only possible by editing the topic manually AFAIK.
-
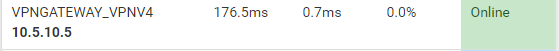
Yep
Setting the monitor IP on the gateway made it green - Happy days :
-
And edited the title
Thanks again for all your help and time, Much appreciated