private ip for WAN , public ip for LAN
-
Hi,
I have just installed pfsense 2.4 for a SOHO I work and I'm getting problems with the routing.
I have asked my ISP for a /29 network with public ips for the DMZ, but instead of giving my directly what I asked they gave me a this:WAN 10.219.16.244/30
LAN 152.206.43.32/29
(these are not the real ips the gave me)So, I have something like this:
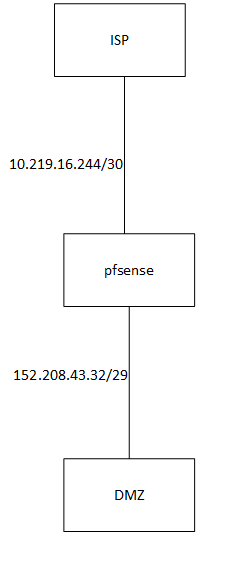
the connection between my pfsense and the isp gateway works just fine but there is no way i get internet connection.
What I'm missing here?(I've done this before but with a public IP on the WAN side)
Hope you could help me!
Thanks anyway -
Have you tried reversing them? WAN at 152.blah? Why would they assign you a LAN network?
-
i have not really tried as you suggested because i have called back my isp and they reassured me the networks are exactly as i explained. so i assume they mean what they say and it is not an error
-
personally,out of ideas, i will try as @kom suggested, igore the 10.219 and configure with 152.208. maybe they have an upstream device with that 10.219 that is out of your control
-
If they routed your public /29 to you, then you need to make sure you turn off nat.. Or you would be natting to the transit network IP (ie the private on your wan) so no that more than likely would never work.
You can most definitely route a public netblock over a rfc1918 transit..
Where you might have problem here is the pfsense with its rfc1918 on wan that is only transit and they do not nat upstream, so no internet. Will have an issue checking for its updates and getting packages, etc. It would need to use its lan IP as source which is on the public /29 to get to the internet.
edit: Just spitballing here, but you might be better off using the /29 they gave you as vips on your wan so that pfsense could then nat to the vips and itself would be able to get internet.. The guy that would know for sure the best way to set this up would be @Derelict
-
@joregartinez You can use it just like that I think with the /29 configured on your DMZ interface. In that case, you would probably want to disable NAT for it (enter hybrid NAT mode and put a NO NAT rule for the /29 there.)
Binding services on the firewall itself (Like a VPN Server) should be able to be told to listen on the DMZ address, but I can think of things the system is going to do that will break that, like the host route to the other side. You might need a VIP on the WAN for that. Outbound NAT for connections from the firewall itself should be able to be told to use the DMZ address as well using manual outbound NAT but I have never tried that. Seems it should work just fine but you might hit some kind of route-to weirdness I'm not thinking of. But if you have a VIP on the WAN for service binding you might as well just use that.
It is generally a bad idea (as in it breaks things) to NAT connections from the firewall itself and from the WAN address. You will want to do exactly that, though.
If you do put a VIP on the WAN make it a /32. Note that hosts on the DMZ will not be able to access that VIP because they will not know it is not on their local subnet.