Was My ISP on Phishing Expedition?
-
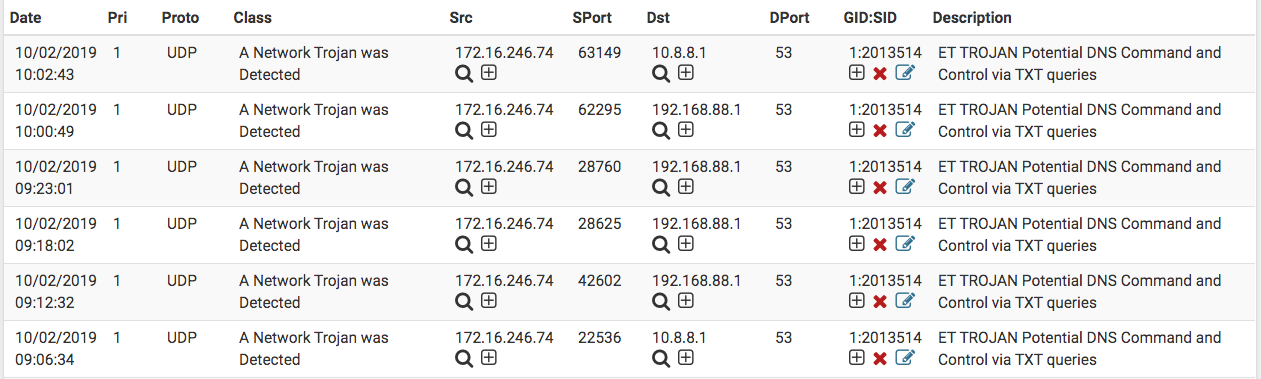
So, the other day my Internet was down and a public IP address was not available from my ISP. The next day the Internet was still down; however, I noticed I received a private IP address from my ISP (172.16.246.74) that raised a red flag. My configured router's address is 10.0.8.1, yet my ISP was attempting to connecting to 192.168.88.1 the router's default IP address. So I wondered whether this default address available even when the router has a custom configuration? Below is what my IDS/IPS showed and I wondered whether my ISP was on a phishing expedition with a 10.8.8.1 address as well as whether my router gave out its name Mikrotik why they tried the default address. I use OpenDNS, not my ISP DSN server.
-
@NollipfSense said in Was My ISP on Phishing Expedition?:
yet my ISP was attempting to connecting to 192.168.88.1 the router's default IP address.
?
How can the ISP (want to) connect to a router's LAN address ?
This upstream router, the one above pfSense, has a firewall , right ?The IDS running on pfSense sees suspected DNS packets ... why ?
Do you let 'unknown' DNS packets coming in ? Are you hosting a master or salve DNS server ?My pfSense WAN interface uses the default rule : none. So, nothing comes in - except answers from stuff I asked for. I guess ... I'm not even "IDS", I trust my LAN devices.
-
@Gertjan said in Was My ISP on Phishing Expedition?:
How can the ISP (want to) connect to a router's LAN address ?
This upstream router, the one above pfSense, has a firewall , right ?Thank you Gertjan for responding! Yes, yes...it wasn't going anywhere. The only upstream above the pfSense is the cable modem...so, it wasn't going anywhere pass the NIC.
@Gertjan said in Was My ISP on Phishing Expedition?:
The IDS running on pfSense sees suspected DNS packets ... why ?
Do you let 'unknown' DNS packets coming in ? Are you hosting a master or salve DNS server ?Because the NIC with IDS/IPS would see the packet before the firewall would. No, that's strictly forbidden. No, no master nor slave...just the edge pfSense does DNS.
@Gertjan said in Was My ISP on Phishing Expedition?:
My pfSense WAN interface uses the default rule : none. So, nothing comes in - except answers from stuff I asked for. I guess ... I'm not even "IDS", I trust my LAN devices.
Same here...have highly trusted LAN govern by a new Mikrotik RB450Gx4; however, its default LAN is 192.168.88.1...but that's not its current custom IP address configuration that is 10.0.8.1. That's why I am curious why the connection attempt to that default address or to 10.8.8.1...none exist on my network. However, my ISP knew that I had the earlier Mikrotik RB450G when that was my edge router.
What I am suspecting is my ISP was wanting to make it look as if I have Internet by issuing a private address to make the cable modem appear to be working by the link light blinking. I came to this conclusion because shortly after the intrusion event attempt, I received a call from the ISP that they were coming out to my home to test. It seems that they wanted to extract additional fee(s) for service.
Of course, I am highly pissed...these are things they have done to the common uninformed person, and it's deceitful. Does my suspicion reasonable...makes sense?