Quick NAT/OpenVPN questions.
-
Good day, PFSense community. I work with a lot of networking but not to much in the routing realm.
When I upgraded to the latest version this last weekend, our PFSense box had been up 53 days with no issues whatsoever. With a minimal install, you just set it and forget it. Which is what we've done. I did the upgrade so that we could connect to a dedicated VPN service (NordVPN). Their configuration document was very thorough.
Last night we ran into an issue accessing VUDU. According to their website, they block VPN IP addresses. Fair enough. So, I have to route some internal traffic around the OpenVPN interface to the regular WAN interface which brings me to some general questions.
Higher mappings have higher precedence? I believe that they do.
I know that I can create a reservation for the device that accesses VUDU and then put in a rule for that IP to use the WAN interface.
Is there a way to put in a range of IP addresses or do I just need to use the /## method?
For the destination, can you use a domain name? *.vudu.com or similar or do I have to use an IP address range?
Thanks for any thoughts/guidance.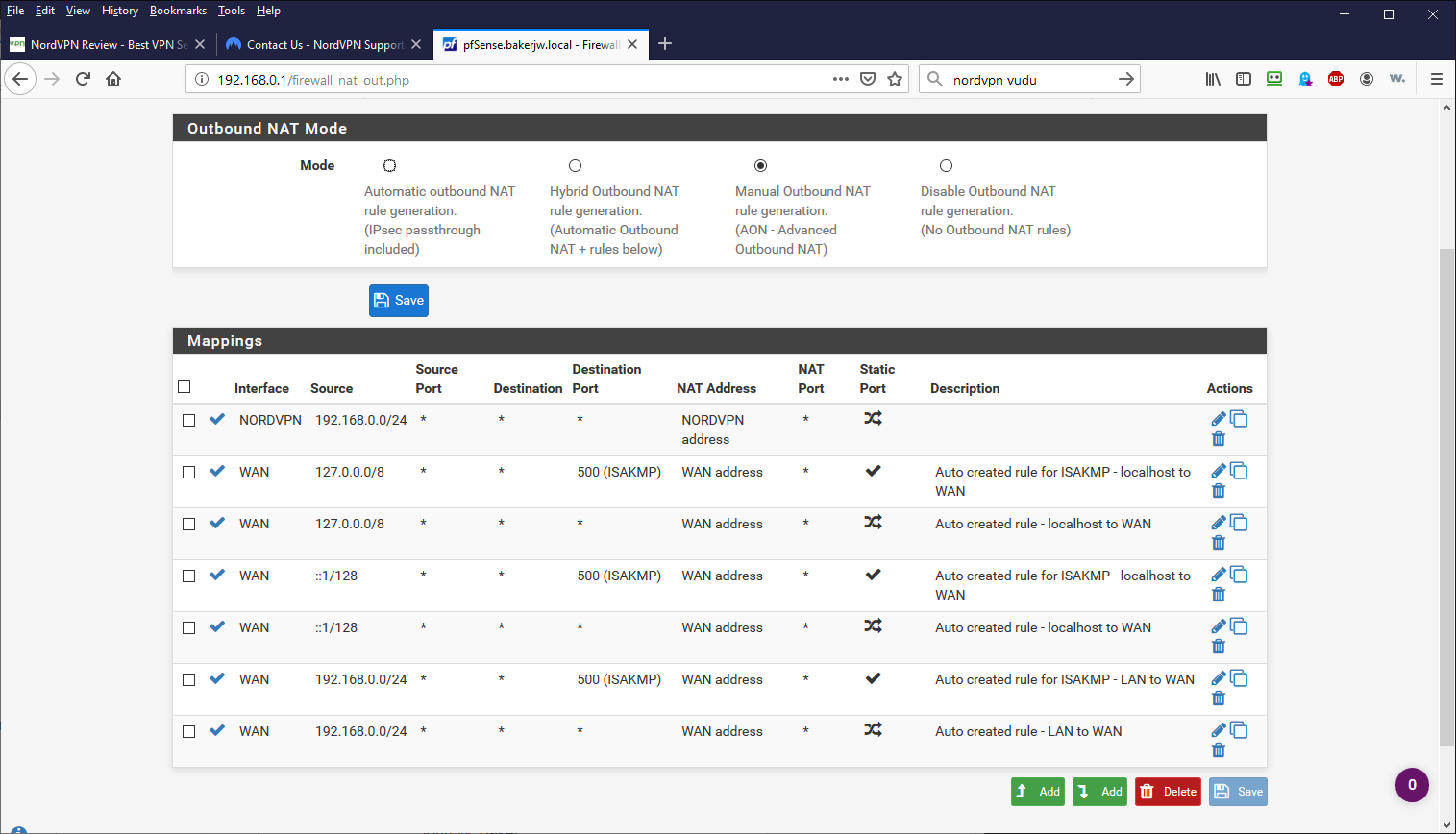
-
You may use aliases. Firewall > Aliases > IP.
Here you can put in IP ranges or FQDNs.
After creating an IP aliase, it can be used as source or destination in firewall or NAT rules. -
I've been reading up a bit about outbound NAT and routing.
This document mentions outbound NAT doesn't control which interface is used.
Instead it says to use policy routing or static routes.
https://docs.netgate.com/pfsense/en/latest/nat/outbound-nat.htmlI am trying some static routes now to see if I can force traffic out of the WAN port.
-
Use policy routing not static routes.
-
@Derelict
Thanks. Now I am getting somewhere.I have a PHP script on my webhost that gives information back about the connection that launched it. I was able to finally get my personal workstation to hit it without the VPN.
VUDU is still unhappy but I'm getting to know the lay of the land a bt better.Thanks for all of the patience.
ETA...
With a single Internet IP on the WAN side and a Class C subnet, is NAT even needed if I am using policy routing? That is what it seems to say in the PFSense book. <-- Great resource too BTW.
Apparently yes. Disabling it blocks everything. -
@bakerjw The other side will not have a route back to your private LAN subnet. You need to NAT so the return traffic goes to the your tunnel address which is a connected route on the other side.
-
I'd recommend everyone using a VPN Provider with pfSense to watch
https://www.netgate.com/resources/videos/openvpn-as-a-wan-on-pfsense.html
-Rico