Had my pfSense been compromised?
-
@johnpoz is there any log or place i can look that would tell me what IP address requested the deleted rule to be added after the event?
My poroblem isnt that upnp is enabled as that is required for multiple PS4's to work on my network but that I cannot tell what device caused the open ports and requested the upnp rules once they are deleted. -
Wouldn't the dest IP in the log tell you who opened it?
I don't use UPnP... its horrible idea from a general security point of view.. When I did have it enabled for my sons playstation, the play station was on isolated vlan, and UPNP was restricted to only allow requests from his ps ip.. And also restricted in what ports could be allowed also - sure and the F do not need 53 inbound, or 88.. Its not doing freaking kerb inbound, etc..
The lack of documentation in these game consoles and what is actually required is just horrific... How freaking hard is it to say game X needs ABC inbound, and EFG outbound..
Some of them lists ports.. but then they don't call out if inbound or outbound or both, etc.. For example why would they need 80 inbound... This isn't even viable on many home connections because their isp AUP prevents running services and block such a port anyway, etc..
So sorry off the top of my head I don't know that much about how its implemented in pfsense - other than not something I would suggest any one run ;)
-
@johnpoz haha fair enough, i did set up manual rules but gave up after a while especially as there are 2 playstations on the network its just easier.
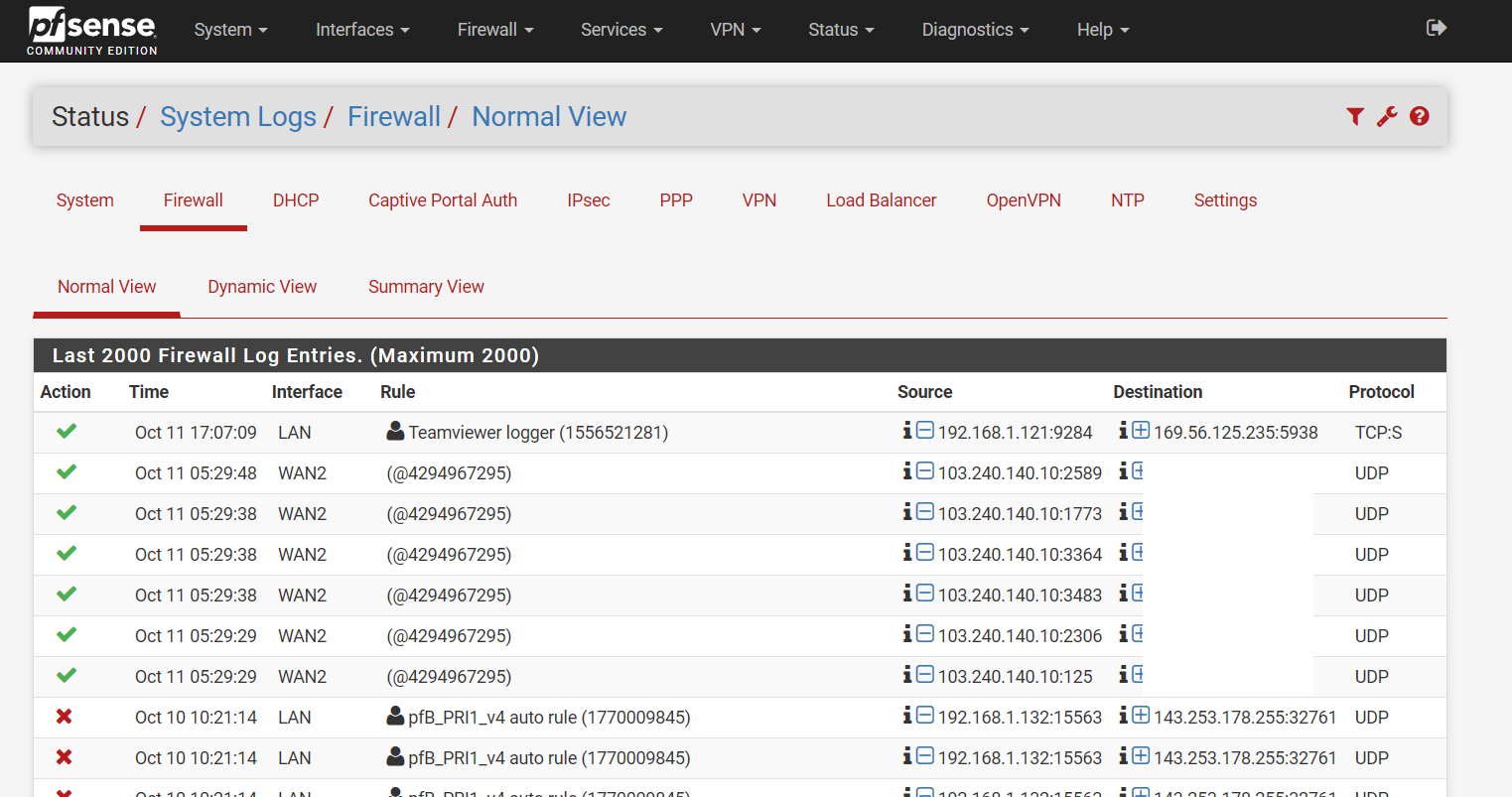
The IP it shows is just the external IP I cant see which internal IP requested the rule, ive had other things on the network do this as well and its always a pain to see where it originated after the event. I was just hoping someone knew an easier way to find out. Weird how I also have the same IP addresses and ports connecting to my network as OP. -
Not sure call it weird, he had or still has UPnP running - this for explains what he saw in the logs.
-
@johnpoz sorry i meant weird how we both had connections from the same IP address and the same ports. But i aggree it does look like upnp is running on his firewall.
-
Suppose this could be any number of IoT's phoning home? TV, etc.?
-
@provels yeah I thought that too but I tried them one by one tonight and didn't see anything however looking closer at the rules that were opened up it all seems to be Microsoft authentication stuff and I don't run Windows.
Also I have now added a rule to the ACLs for upnp to stop low ports being opened. -
@hulleyrob Maybe it's "Steven's Phone"...
https://alltvspots.com/tag/xfinity-stevens-phone/ -
@provels haha yeah is windows phone even a thing anymore? Could be anything i suppose but I’m going to keep a more careful eye on it for a while.
-
@hulleyrob Glad you asked! I have 2 - 1 Nokia, 1 MS; one for use, one for backup. MS sold 2 and I bought them both! Going on 5 years, same battery, Windows 10, updates monthly. Makes calls and texts, takes pictures, navigation, in-a-pinch Internet, a few apps (not app-happy here). Best $30 (x2) I ever spent. Consumer Cellular, $25/month. I'll stop now.
-
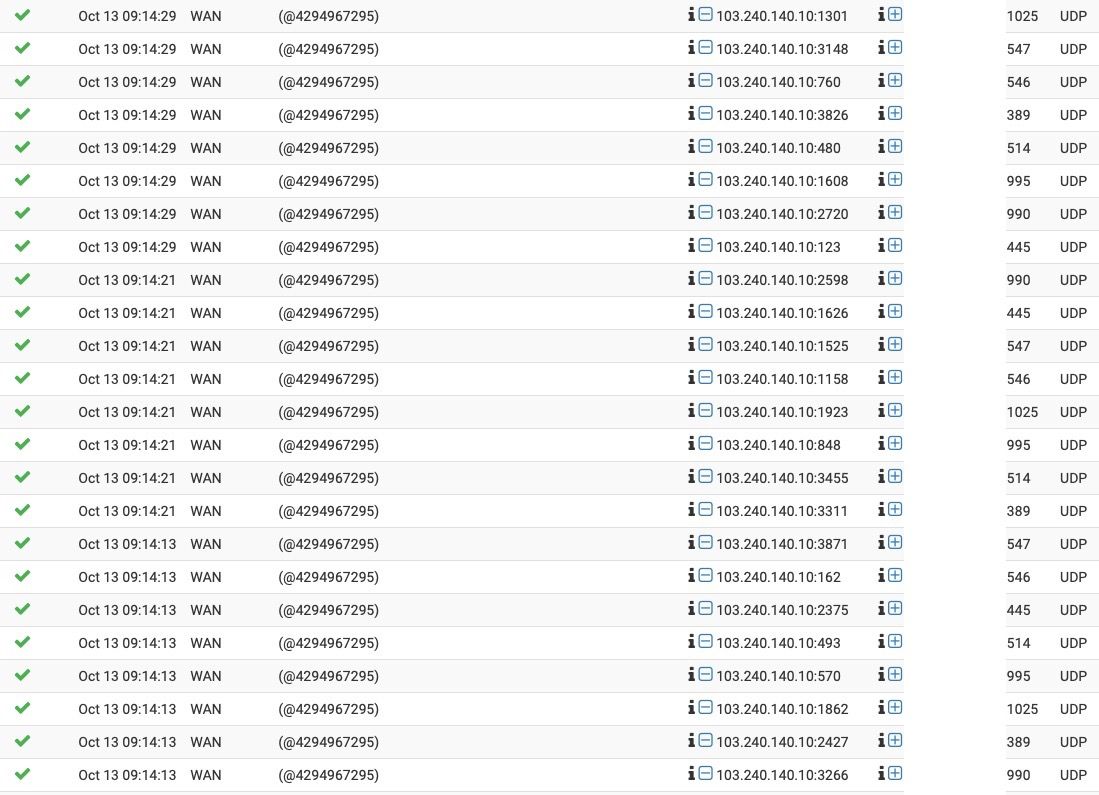
514 is syslog, 995 is pop3 ssl, 546 and 547 is dhcpv6... 990 ftps
WTF why would any devices open those? 445 is smb over tcp.. 389 LDAP
Those are not unique to windows...But I would be concerned with stuff opening those up... Which is why you never run freaking UPnP... Its was a horrible idea from day one..
Why not just sniff on your interface for the UPnP ports and see what is hitting them.
-
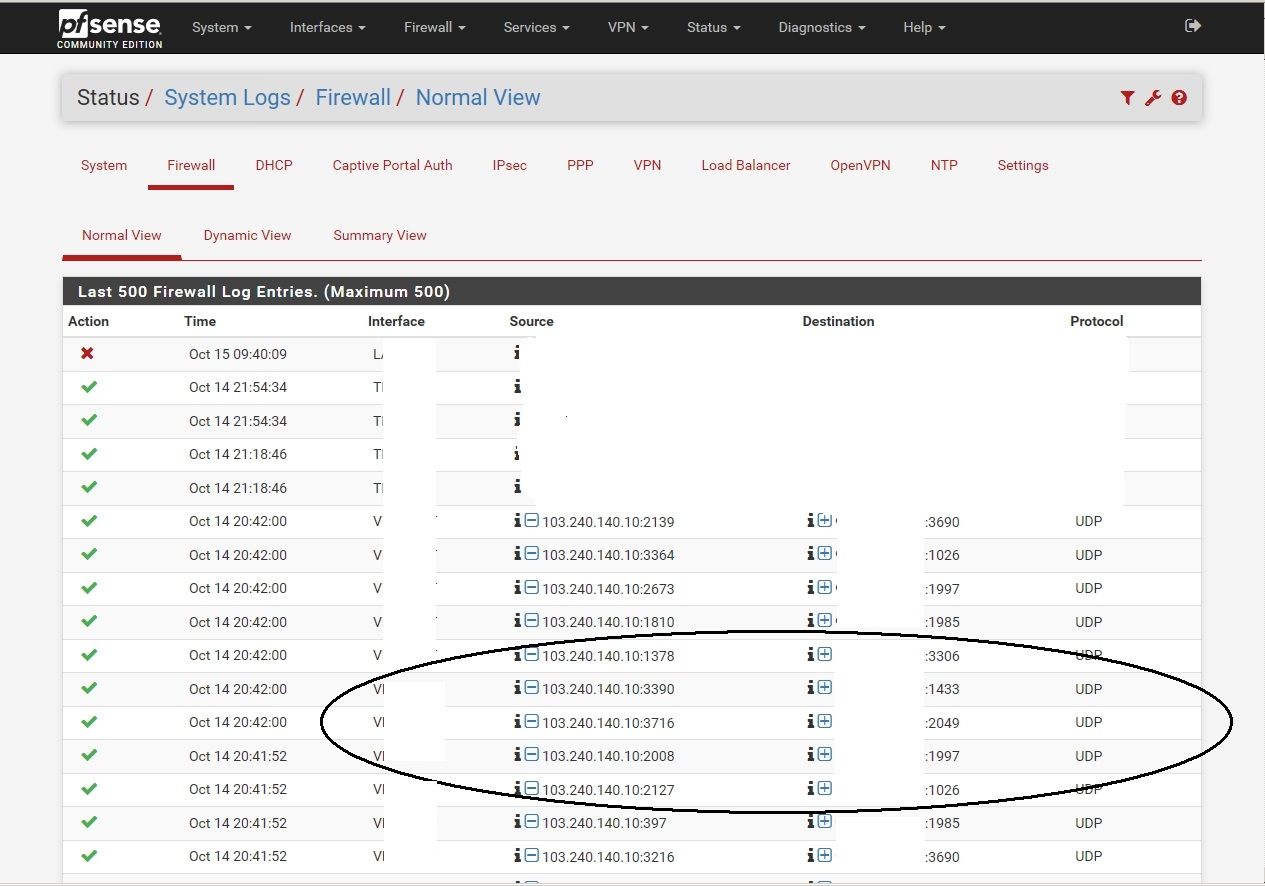
Hi, I have exactly the same problem - weird incoming connections from the same ip (103.240.140.10). UPnP is disabled. No open WAN ports, no floating rules. Pfsense 2.4.4-RELEASE-p3 (amd64). I googled this IP and realize it has been blacklisted at some places:
http://sanyalnet-cloud-vps.freeddns.org/mirai-ips.txt
https://whatismyipaddress.eu/downloads/ip-blacklist.txt
I have only Windows 7 PC's in my LAN. They all were shut down when this traffic appear. Sorry for my bad English.
-
https://www.abuseipdb.com/check/103.240.140.10
But not why the traffic was passed. -
Your not even showing your rule Ids or description. For all we know you have an any any rule on your wan?
-
When I place the mouse over the green check on left on the rule, it shows "pass/0". When I click it opens a popup: "The rule that triggered this action is:" Nothing else.
-
Rule description is @4294967295.
-
Does anyone have an idea where the rule id comes from as it looks like we all have the same rule ID number creating these rules maybe this will give us an idea of where they are coming from?
Ideally there would be some logging or history but as everyone has said upnp is a bad idea for most people so i guess thats why it doesnt exist.
Also they are also 8 seconds apart in batches but this could be the time that the service runs each time?
-
So I just turned UPnP on - to test.. And then set my plex to use UPnP vs the static forward I have setup.
So I disabled my normal port forward.. Then enable UPnP
And I get this.
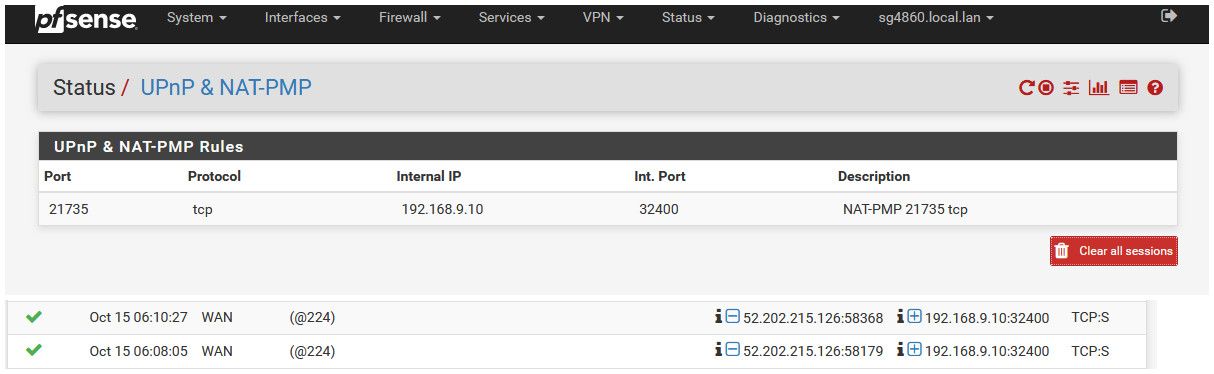
After doing a can you see me for the port listed in the UPnP status 21735
Is not coming up with that ID number.. A google for that ID and pfsense came up with this thread
https://forum.netgate.com/topic/128685/firewall-log-showing-strange-pass-entryCan we see the raw firewall logs for these entries. Like in that thread.
example - here is the raw entry for one of those passed via upnp
Oct 15 06:10:27 filterlog: 224,0,miniupnpd,0,igb1,match,pass,in,4,0x0,,42,13284,0,DF,6,tcp,60,52.202.215.126,192.168.9.10,58368,32400,0,S,2623792563,,26883,,mss;sackOK;TS;nop;wscaleYou can see from the log that miniupnpd there.. So lets see the raw for these entries.
From that other thread
Mar 25 14:42:05 pfSense filterlog: 4294967295,,,0,re0,short,pass,in,4,0x0,,239,10359,0,DF,6,tcp,36,105.212.87.78,[MYIPADDRESS],2123,23,-4,S,errormsg='[bad hdr length 20 - too long, > 16]',Not exactly sure what "short" means as the reason...
-
@johnpoz yeah sure i did look at those last night but couldnt see anything that looked much differant from in the screenshot but maybe you will see something i cannot. Will post as soon as i get home from work. Thanks to everyone for input and testing this.
-
Here is my raw filter log for this:
Oct 14 20:42:00 filterlog: 4294967295,,,0,pppoe0,short,pass,in,4,0x0,,241,53405,0,none,17,udp,27,103.240.140.10,[MYIPADDRESS],1810,1985,7