NAT and IPSEC
-
Hello together,
i´ve got a problem with an ipsec tunnel and NAT. But i`m shure that I am not smart enough to get it running.
I have an ipsec tunnel with an attached VLAN (an internal address). There is a NAT defined for a computer in another VLAN.
The incoming path is working fine, the packets are coming in and beeing forwarded using the NAT.
BUT, the way back is not working. The answers for the computer behind the NAT are going out, but on the wrong interface (default GW) but using the NAT.
When I will integrate the additional VLAN in the ipsec, the packets are going on the correct ipsec tunnel but without the outgoing NAT.So, how do I get NAT and IPSEC running together?
I did try to change the NAT with 1:1, port forward, outgoing... but no change in the handling.
Maybe somebody could give me some hints to get this running.
Thanks
Alex
-
Hi ho,
some additional Infos:
This is the VPN Tunnel Phase 2
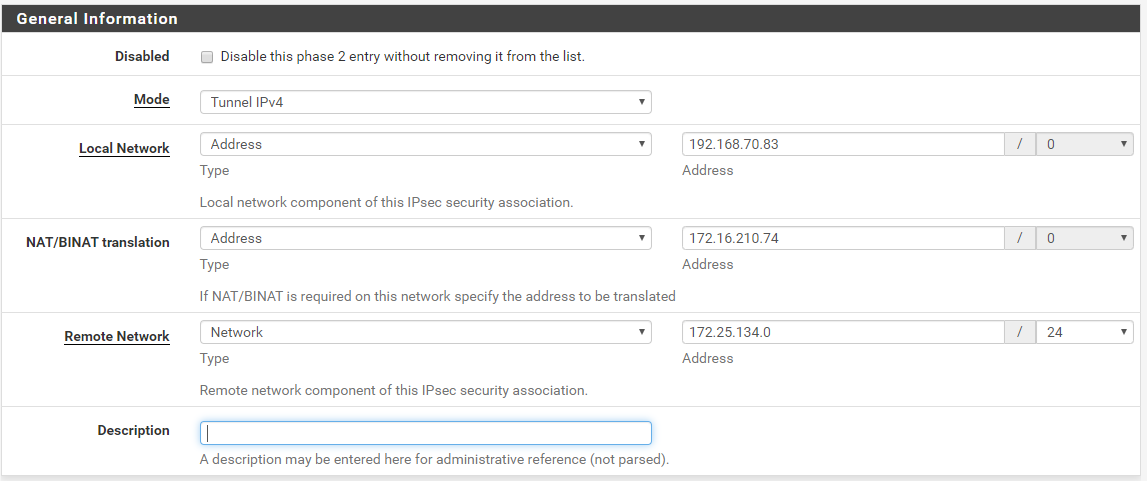
So, I will access the 192.168.70.83 using the 172.16.210.74 as NAT when the traffic is coming from the 172.25.134.0/24
So, the Packets are coming in, will get natted to the correct server, but on the way back, they will not get the outgoing NAT, so the Packets are going out using the 192.168.70.83 Address which is not known on the other side of the VPN Tunnel...
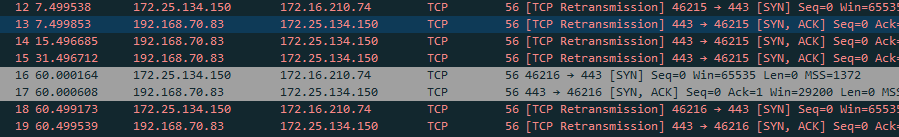
I hvae alos setup an outgoing NAT, but i think that i normaly do not need one, but with or without it is not working.
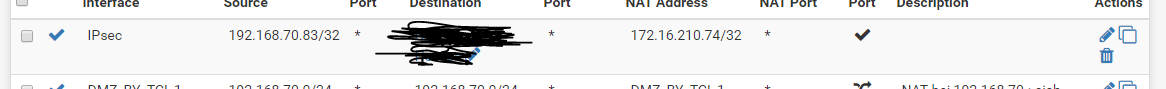
Maybe someone could tell me my mistake.
Thanks
Alex
-
Hello Alex, I attempted to create the same setup (using pfsense 2.4.4-3), and it failed EXACLTY the same way.
The extra NAT rule did not work either for me.
Do you have any update on this configuration ?
Did you took the capture (a) on the pfsense, or in the (b) 172.25.x.x network ? In the (a) case it MIGHT be normal, since in the CAVEAT section in the help, the documentation states that the capture is performed before the NAT. In the (b) case, yes the NAT does not work properly.
Hope to reading from you Alex, or from anyone,
I have been banging my head against the netgate device for two days now, and I cannot switch to OpenVPN, since our big client requires IPSEC usage, with a NAT/PAT.
Julien.
-
PfSense or better pf in FreeBSD for that matter, cannot do NAT after IPSec. Dunno if that has ever been fixed or not, but that's one of the few things the whole setup cannot do.
https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=185876
https://forums.freebsd.org/threads/solved-ipsec-l2tp-vpn-on-10-0-no-traffic-to-internet.45691/
-
Thanks Grimeton for the reply, the bugs you are linking to seems to be resolved now.
The documentation seems to agree that NAT is possible in a 1:1 form, and in a NAT/PAT form. (Although nobody seems to use the latter, and it might be buggy).
Too bad my netgate support is expired when I need it.
-
@anohles said in NAT and IPSEC:
So, the Packets are coming in, will get natted to the correct server, but on the way back, they will not get the outgoing NAT, so the Packets are going out using the 192.168.70.83 Address which is not known on the other side of the VPN Tunnel...
That is not true. Packet captures in the outbound direction happen before NAT occurs but the NAT WILL occur.
In the example above, the other side should create a tunnel like this:
Local Network: Network: 172.25.134.0/24
Remote Network: Host: 172.16.210.74ETA: This is only on captures on IPsec/enc0. Interface captures will be post-NAT for outbound traffic and pre-NAT for inbound.
-
Ok thanks, so I cannot confirm if NAT is working or not just by looking at the client logs or captures.
I will setup a server platform to test my client settings, and not just blindly trust my peer that says "your incoming address must be wrong".
-
@julienb If you can, check on the other end what IP-address you see there. If it is the one you expect, then NAT is working.