XG-7100 Site-to-Site IPSec AWS VPC VPN: Cannot Ping Private Subnet EC2 Host
-
I used the pfSense AWS VPC Wizard to set up a site-to-site IPSec VPN connection between my netgate XG-7100 and an AWS VPC. The XG-7100 (Status -> IPSec -> Overview page) shows the two IPSec tunnels as ESTABLISHED (green), and I can successfully ping from the inside tunnel address to the VPC side of the tunnel per Testing Connectivity.
However, I cannot ping an EC2 host (private IP: 192.168.26.86) in a private subnet of the VPC from the XG-7100. What am I missing to make this work? Thank you in advance!
Network Setup:
- ASUS AC1300 wi-fi router (10.0.0.1/24)
- PC A (IP: 10.0.0.107)
- netgate XG-7100 (WAN IP: 10.0.0.20, LAN: 172.16.0.1/24)
- PC B (IP: 172.16.0.12)
- Site-to-site VPN: BP-enabled
- AWS VPC (192.168.0.0/16):
- Private subnet (192.168.0.0/19)
- EC2 host (private IP: 192.168.26.86) - security group inbound rule allows all IPv4 ICMP traffic
- Public subnet (192.168.32.0/19)
- Private subnet (192.168.0.0/19)
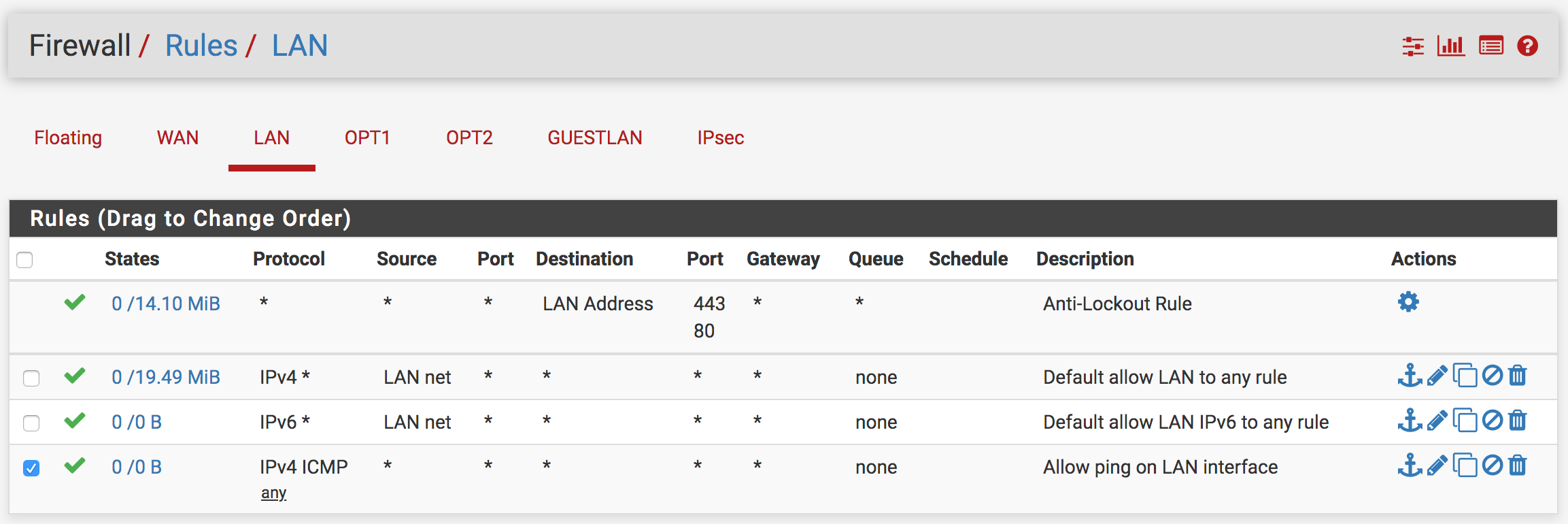
XG-7100 Firewall Rules: LAN
- Allows IPv4 ICMP traffic:
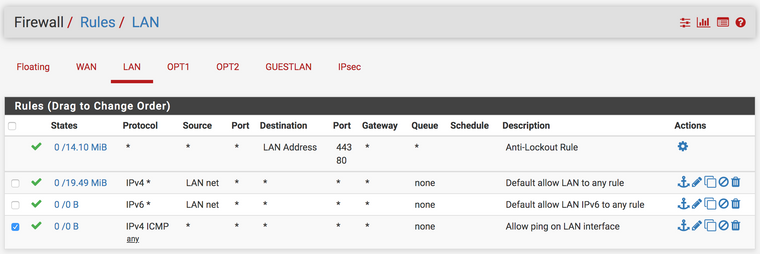
XG-7100 Virtual IPs
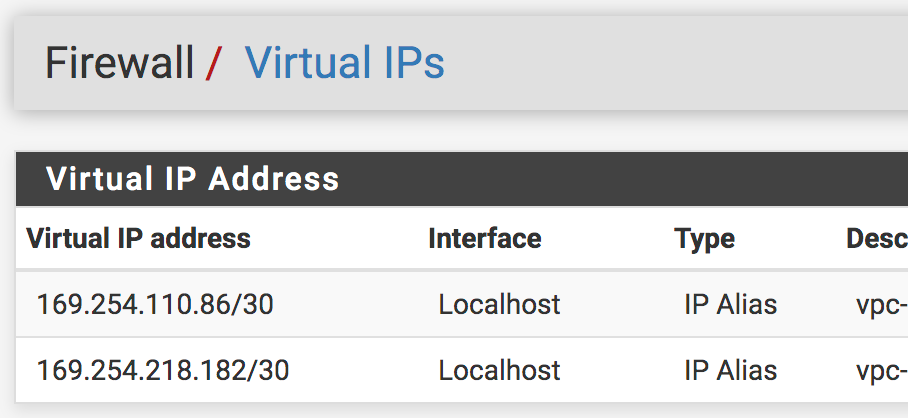
I can ping from inside tunnel address to the VPC side of tunnel (used XG-7100 Diagnostics -> Ping):
PING 169.254.110.85 (169.254.110.85) from 169.254.110.86: 56 data bytes 64 bytes from 169.254.110.85: icmp_seq=0 ttl=254 time=12.093 ms 64 bytes from 169.254.110.85: icmp_seq=1 ttl=254 time=11.960 ms 64 bytes from 169.254.110.85: icmp_seq=2 ttl=254 time=11.903 ms --- 169.254.110.85 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 11.903/11.985/12.093/0.080 msPING 169.254.218.181 (169.254.218.181) from 169.254.218.182: 56 data bytes 64 bytes from 169.254.218.181: icmp_seq=0 ttl=254 time=12.180 ms 64 bytes from 169.254.218.181: icmp_seq=1 ttl=254 time=12.012 ms 64 bytes from 169.254.218.181: icmp_seq=2 ttl=254 time=12.024 ms --- 169.254.218.181 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 12.012/12.072/12.180/0.077 ms - ASUS AC1300 wi-fi router (10.0.0.1/24)
-
Courtesy of AWS support this issue was due to the following:
- I selected BGP routing in the pfSense AWS VPC Wizard
- IPSEc tunnels were ESTABLISHED (UP), but BGP was stuck in 'Connect' state and hence "DOWN"
- The peer-proposal SA was created as : 172.16.0.0/24 --> 192.168.0.0/16 which implies that both the tunnels were configured as 'Policy based' VPN. This also implies that BGP was not configured on the XG-7100 device for the VPN (because BGP is 'Route'-based VPN always).
They suggested the following resolutions:
- Recreate the VPN in the AWS Console using "Static" routing instead of "Dynamic"
- Configure BGP as per 'Download configuration' on the customer gateway device [Note: I expected the AWS VPC Wizard to do this for me]
I deleted the resources and started the pfSense AWS VPC Wizard from scratch, selecting Static routing instead, and this time it succeeded and enabled me to ping the EC2 host in the private subnet from the XG-7100.