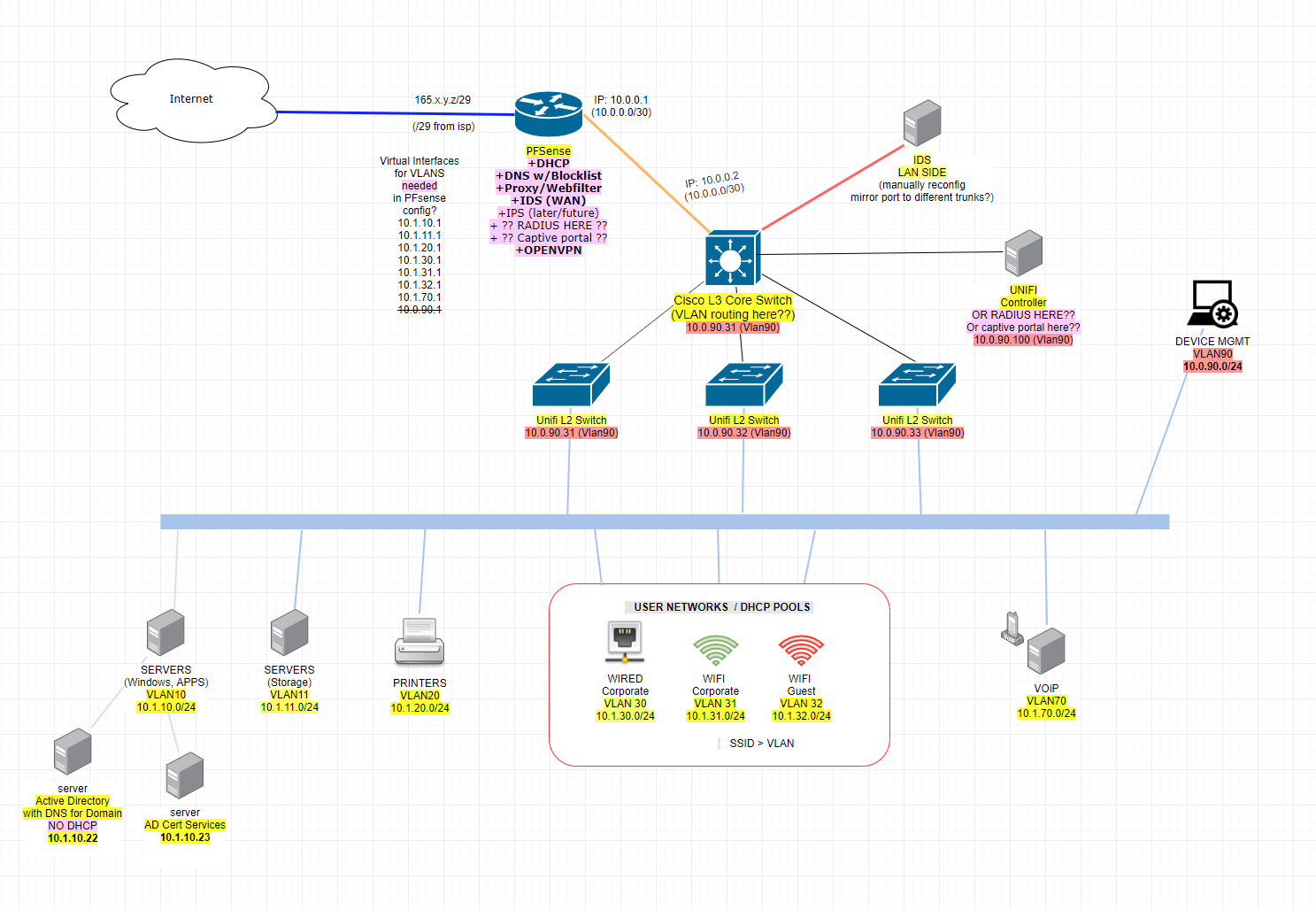
Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?
-
@dotdash said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Yes, the /30 transit network is a good idea. If you want to use pfSense for dhcp, use an ip helper on the switch.
@JKnott said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Is it OK to use 10.0.0.0/30 (10.0.0.1 and 10.0.0.2) for link between Pfsense LAN side the the Core switch WAN side? Or should this be a 192.x or 172.16.x or something to differentiate from the LAN 10.x.x? Best practice? Pro's con's or doesn't matter?
You cannot have multiple subnets in the same address range, so no you cannot have 10.0.0.0 /30 and 10.0.0.0 /20. You can use any addresses you want, so long as they don't overlap. You could even use 10.0.16.0 /20 if you wanted.
Sorry, I should have said that the 10.0.0.0/20 is a guideline for the subnets that will be created within the available scope of the "/20" range.
Not actually using the /20 as a /20 network. No overlaps with the subnets. I.e. we could partition (16) /24's within that "/20" address space. -
@dotdash said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Yes, the /30 transit network is a good idea. If you want to use pfSense for dhcp, use an ip helper on the switch.
Can you explain more about how ip helper-address would work here? How would I set that up? Would I create the virtual interfaces on pfsense (like suggested in image) and then for each interface mapped to x.x.x.2 on the L3 switch for those matching VLAN/subnets I would define ip help-address to forward DHCP requests from Cisco switch to PFsense?
Have you tried this or verified it works? So many people just say pfsense w/DHCP doesn't work with downstream router.
-
@dotdash said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
f you want to use pfSense for dhcp, use an ip helper on the switch.
Pfsense can not do that... It has come up like 100 times over the years ;)
you can use the cisco, just use it as L2.. Then you can have pfsense be dhcp, and very simple easy firewall rules... The only question is if all your traffic between vlans can be handled by your pfsense box... How many interfaces does it have?
Pfsense can be a relay - it can not handle the scope of ranges it does not have an interface in.. You can not use a helper to point to pfsense and expect it to hand out an IP from the vlan that traffic was sent from.
You can for sure use pfsense with downstream networks via downstream routers - it just can not provide dhcp to those downstream networks. Use something else for your dhcp - doesn't have to be the switch.. You could run isc dhcp on anything you want, you just can not do it on pfsense. Or just use MS as dhcp if your a MS shop and have that setup anyway. You show windows AD in your drawing - that should be our dhcp server - have your ip helper on cisco point their for your dhcp for all your vlans.
And yes if you are doing to do downstream networks - then a /30 transit works just fine.
As a network grows, then yeah it quite often becomes necessary to route like your drawing at the L3.. Its just more complicated setup. And is way more difficult to firewall between the vlans on that cisco, then it would be at pfsense - but if your pfsense doesn't have enough interfaces to be able to handle all the intervlan traffic at full speed then sure you can go to something like your cisco to do the intervlan routing.
-
@johnpoz said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
@dotdash said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
f you want to use pfSense for dhcp, use an ip helper on the switch.
Pfsense can not do that... It has come up like 100 times over the years ;)
you can use the cisco, just use it as L2.. Then you can have pfsense be dhcp, and very simple easy firewall rules... The only question is if all your traffic between vlans can be handled by your pfsense box... How many interfaces does it have?
Pfsense can be a relay - it can not handle the scope of ranges it does not have an interface in.. You can not use a helper to point to pfsense and expect it to hand out an IP from the vlan that traffic was sent from.
You can for sure use pfsense with downstream networks via downstream routers - it just can not provide dhcp to those downstream networks. Use something else for your dhcp - doesn't have to be the switch.. You could run isc dhcp on anything you want, you just can not do it on pfsense. Or just use MS as dhcp if your a MS shop and have that setup anyway.
And yes if you are doing to do downstream networks - then a /30 transit works just fine.
Right now pfsense test box has 2 interfaces - WAN / LAN. Pfsense doesn't need to handle all of our LAN traffic. We don't want it to. We only want PFsense to manage internet-bound traffice going through the WAN, as well as a perform a few other low-traffic functions as indicated. The WAN upstream speed is only 100mbps. Should be fine.
More concerned with you reporting that the ip helper-address won't work. I'm still digging and reading, but it seems like it should work? As I said in OP though, I'm a noob at this point, so still learning.
-
The ip helper just forwards the broadcasts to the specified ip. But, yeah, my bad, I forgot you can't set the DHCP server in pfSense to a range outside of the actual interface. I've never had a setup using a L3 switch where they didn't have an existing dhcp server, so I haven't tried that in a long time.
-
You can do your setup - pfsense can not just do dhcp for your whole network with that setup... But to be honest just use your AD.. That is normally what you should do in a MS shop.. It can handle it for sure - you would just setup the helpers on the cisco for all your vlans connected to it.
-
@johnpoz said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Pfsense can be a relay - it can not handle the scope of ranges it does not have an interface in.. You can not use a helper to point to pfsense and expect it to hand out an IP from the vlan that traffic was sent from.
Hmm maybe pfsense box needs to be on Proxmox or something where I can and pass through virtual interfaces? Seems like a complicated mess to do it that way though.
What about IP Alias on the pfsense side for the VLAN subnets?
"Can be in a different subnet than the real interface IP when used directly on an interface."
^ pfsense docs -
@johnpoz said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
You can do your setup - pfsense can not just do dhcp for your whole network with that setup... But to be honest just use your AD.. That is normally what you should do in a MS shop.. It can handle it for sure - you would just setup the helpers on the cisco for all your vlans connected to it.
Would rather do DHCP on Cisco than the MS stuff.
So in that case, no "virtual interfaces" or anything to do with the VLAN's required on the pfsense side.
The pfsense box would only have and know two interfaces and two IP's? The WAN side IP (an ip in the /29) and the LAN side IP (the /30).
Everything downstream from pfsense wanting to escape to the internet would head towards pfsense LAN side IP 10.0.0.1 ??... or actually the VLAN's first IP like 10.1.0.1 and that IP would be the Cisco managing that VLAN and routing the traffic through to the pfsense /30?
-
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Would rather do DHCP on Cisco than the MS stuff.
From someone that I take has never done dhcp on cisco ;) hehehe MS is the way to go - been doing this since before AD.. back in the days of 3.11... MS does dhcp just fine - and it makes management of your members easy, because the dhcp server can register your members in DNS..
When you run dhcp on something other than your AD - it just complicates it for no reason. The MS dhcp server is very feature reach and can handle 1000's and 1000's of clients with 100's of scopes..
For pfsense to allow your downstream network out - you will have to setup a gateway pointing to the IP of your cisco IP on the transit /30... Once you create routes to the downstream networks - you can do it with 1 if all your downstream fall under a single cidr... But you will have to adjust the firewall rules on the transit interface of pfsense to allow the downstream network to go where you want them to go on the internet - could be an any any, but source would have to be adjusted from the default "lan net"
Once you create the routes in pfsense - auto outbound nat will allow for them to be natted to pfsense wan IP.
-
Mostly linux here. It's the MS stuff that gives me headache while I learn to navigate through it.... and networking planning at this level too, I suppose :P
Anyway I can manage the DHCP pools on Cisco through IOS CLI no problem... the SG CLI is actually slower/more of a PITA than CLI for that IMO. It just would have been nicer to manage all the DHCP pools through pfsense gui to save one more interface to have to log in to and navigate around in.
So here's the updated image... does the pink stuff by PFsense still look ok?
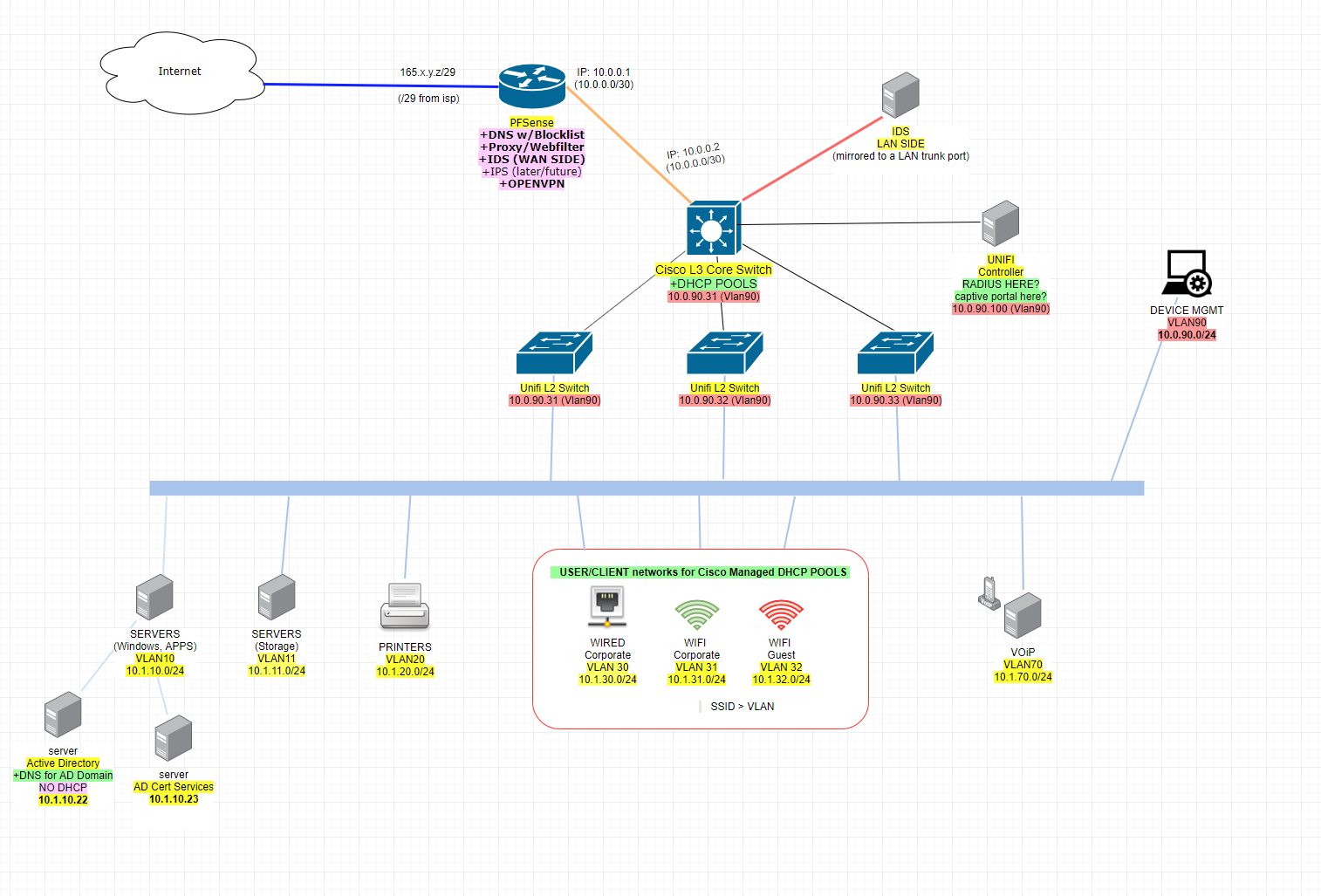
So I will:
- Let pfsense be super authorative top dog DNS for the overall network**
- Let pfsense manage OpenVPN ... is ok like this?
- Let pfsense manage http proxy / filter (squid?) for LAN traffic going out through WAN
- Let unifi controller manage radius
- Let unifi controller manage captive portal
**I originally wanted DNS at pfsense because I was thinking in terms of blacklists like DNSMASQ does, which is still good... but I forgot with pfsense (i.e. freebsd PF) I'm sure there is some plugin or script or something that leverages "blackhole". I forget how I used to do this long ago with freebsd and pf...something about tables. I'm sure there is some pfsense way of accomplishing this. Goal = kill traffic to known bad IP's. MS of course wants to manage DNS for everything in its "domain" so I let it do that, but I want MS to get it's DNS resolutions from pfsense.
-
I would, personally, avoid anything 10dot like the plague.
If you want a /20 I would use something random like 172.19.16.0/20
-
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
but I want MS to get it's DNS resolutions from pfsense.
Why? I would let the firewall be a firewall. If you want a DNS blacklist server I would put it on the inside (hint: it could be another pfSense software instance doing just that). I would also consider a separate node for squid. You could put it between the edge and the internal layer 3 switch on a couple transit interfaces.
Having everything on the edge device is a disease and leads to problems with VPN traffic and policy routing/multi-wan and other issues.
-
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
Let unifi controller manage radius
You mean run radius on the same box? The unifi controller software can not do radius..It can only point to one - you could run radius on the same box I guess..
Sure you can have any downstream dns being authoritative for your domain(s) just forward to pfsense and then let unbound resolve.
-
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
It's the MS stuff that gives me headache
I'm allergic to it too.

-
Trying to wrap my head around this a bit more. Found some tutorials that talk about this solution and "simple, just use VLAN TRUNKING!"... but... VLAN TRUNK would conflict with the /30 static route between the L3 switch and PFSENSE we're talking about here, no? See image... it's one (VLAN TRUNK) or the other (STATIC /30 route) right?
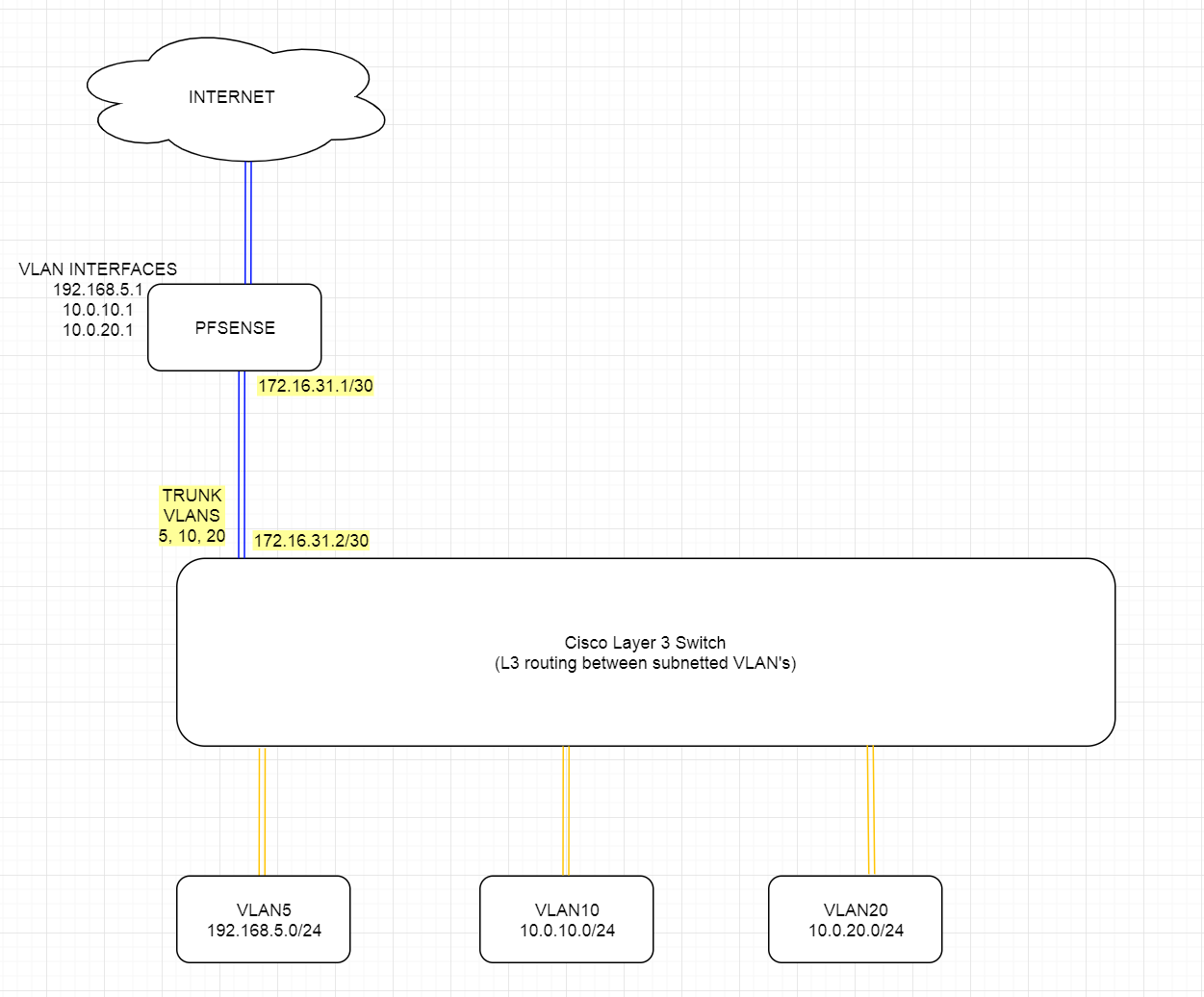
Assume orange connections are 10GBE and blue are 1GBE.
I would presume if you VLAN trunk the 10GBE vlans like that, then potentially the pipe to pfsense could get flooded with traffic as well.
Feels like I'm putting a bicycle on top of a car and riding the bike. :(
-
You can use either - you can have pfsense route the vlans, ie trunk all of them up to pfsense... Now your switch is only L2 and not doing any L3..
You do can do either - there is not right or wrong way.. You use the one that best suites your needs..
As to being a problem with hairpin - depends on how much intervlan traffic you have... But you can always use more uplink to router if sharing 1 physical link is a bottle neck, etc. etc..
But yes a bottle neck in required intervlan traffic is normally a reason to use a downstream router.
BTW: your going to trunk all your vlans up to pfsense, then the transit becomes moot.
-
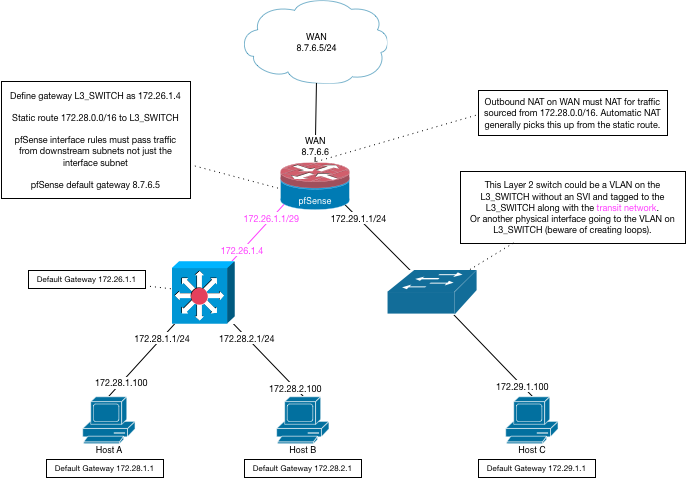
-
@johnpoz said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
You can use either - you can have pfsense route the vlans, ie trunk all of them up to pfsense... Now your switch is only L2 and not doing any L3..
You do can do either - there is not right or wrong way.. You use the one that best suites your needs..
I guess my overnight concern was if I use the /30 between L3 switch and PFSENSE, what's that going to look like on PFSENSE configuration side.
Will I still be able to define gateways for VLAN's (i.e. 10.0.10.1, 10.0.20.1, etc.) at/in pfsense? Will I see see the VLAN tagged traffic and be able to setup firewall rules per-device-in-a-vlan (i.e. a windows wsus.mydomain.com server in VLAN20 "SERVERS" can only go outbound to wsus.microsoft.com port 80, etc.)
-
Dude I already went over this your going to let your downstream do all the routing then there are NO VLANS on pfsense... all there is the transit, and routes... You do not create any vlan interfaces on pfsense when your using downstream router to get to those networks - it will NEVER see the tags..
Your gateways for vlans will be on your L3 doing routing via SVI setups on it..
And yes you can still firewall them, you would just do all the firewall on the transit interface - and you would not have any control over devices talking intervlan - only control of them going to the internet.
-
@Jpub said in Planning to use PFsense with Cisco L3 core router and Unifi for L2... does this look ok? suggestions?:
VLAN TRUNK would conflict with the /30 static route between the L3 switch and PFSENSE we're talking about here, no?
Why would they conflict? They'd conflict only if you tried assigning the same addresses to multiple connections. Each VLAN would have it's own address range.