IPsec ERROR: Could not find phase 1
-
Hello everybody,
I have a problem in the IPsec.
My IP address is 2a00: 61e0: xxxx: xxxx :: and pfSense can not create the config file. It is due to the two colon at the end of the IP address.Get pfSense a full IP address to the end.
e.g .:
2A00: 61e0: 47e1: 74A2: 89b3: 54f3: dd6b: 7823
Is not there a problem.I have tested it three times.
The full length of the IP address works.
Not in a short form 2A00: 61e0: xxxx: xxxx ::
Is this a mistake in pfSense?Here are the system log's.
Oct 27 14:16:15 php-fpm 343 /vpn_ipsec.php: IPsec ERROR: Could not find phase 1 source for connection Test VPN. Omitting from configuration file.Ip Sec Status:
IPsec Status Test VPN Unknown Unknown 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774Incomplete IPsec config file:
[2.4.4-RELEASE][root@Coro.local]/var/etc/ipsec: cat ipsec.conf # This file is automatically generated. Do not edit config setup uniqueids = yes conn bypasslan leftsubnet = 192.168.23.0/24 rightsubnet = 192.168.23.0/24 authby = never type = passthrough auto = routeIPsec log:
Oct 4 17:44:02 ipsec_starter 41610 ipsec starter stopped Oct 4 17:44:02 ipsec_starter 41610 charon stopped after 200 ms Oct 4 17:44:02 charon 00[DMN] signal of type SIGINT received. Shutting down Oct 4 17:43:27 charon 07[NET] sending packet: from 2a00:xxxx:xxxx:xxxx::[500] to 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] Oct 4 17:43:27 charon 13[NET] <bypasslan|1> sending packet: from 2a00:xxxx:xxxx:xxxx::[500] to 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] (65 bytes) Oct 4 17:43:27 charon 13[ENC] <bypasslan|1> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Oct 4 17:43:27 charon 13[IKE] <bypasslan|1> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Oct 4 17:43:27 charon 13[IKE] <bypasslan|1> no shared key found for '2a00:xxxx:xxxx:xxxx::' - '2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774' Oct 4 17:43:27 charon 13[CFG] <bypasslan|1> selected peer config 'bypasslan' Oct 4 17:43:27 charon 13[CFG] <1> looking for peer configs matching 2a00:xxxx:xxxx:xxxx::[2a00:xxxx:xxxx:xxxx::]...2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774] Oct 4 17:43:27 charon 13[ENC] <1> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Oct 4 17:43:27 charon 13[NET] <1> received packet: from 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] to 2a00:xxxx:xxxx:xxxx::[500] (317 bytes) Oct 4 17:43:27 charon 02[NET] waiting for data on sockets Oct 4 17:43:27 charon 02[NET] received packet: from 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] to 2a00:xxxx:xxxx:xxxx::[500] Oct 4 17:43:27 charon 07[NET] sending packet: from 2a00:xxxx:xxxx:xxxx::[500] to 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] Oct 4 17:43:27 charon 14[NET] <1> sending packet: from 2a00:xxxx:xxxx:xxxx::[500] to 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] (712 bytes) Oct 4 17:43:27 charon 14[ENC] <1> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Oct 4 17:43:27 charon 14[LIB] <1> size of DH secret exponent: 4095 bits Oct 4 17:43:26 charon 14[CFG] <1> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/MODP_4096 Oct 4 17:43:26 charon 14[IKE] <1> 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774 is initiating an IKE_SA Oct 4 17:43:26 charon 14[ENC] <1> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Oct 4 17:43:26 charon 14[NET] <1> received packet: from 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] to 2a00:xxxx:xxxx:xxxx::[500] (712 bytes) Oct 4 17:43:26 charon 02[NET] waiting for data on sockets Oct 4 17:43:26 charon 02[NET] received packet: from 2a02:xxxx:xxxx:xxxx:xxxx:fe6e:9774[500] to 2a00:xxxx:xxxx:xxxx::[500] Oct 4 17:43:09 ipsec_starter 41610 'bypasslan' shunt PASS policy installed Oct 4 17:43:09 charon 16[CFG] received stroke: route 'bypasslan' Oct 4 17:43:09 charon 15[CFG] added configuration 'bypasslan' Oct 4 17:43:09 charon 15[CFG] received stroke: add connection 'bypasslan' Oct 4 17:43:09 ipsec_starter 41610 charon (41810) started after 60 ms Oct 4 17:43:09 charon 16[LIB] created thread 16 [802018300] Oct 4 17:43:09 charon 15[LIB] created thread 15 [80201a600] Oct 4 17:43:09 charon 02[NET] waiting for data on sockets Oct 4 17:43:09 charon 05[LIB] created thread 05 [802017e00] Oct 4 17:43:09 charon 14[LIB] created thread 14 [802180000] Oct 4 17:43:09 charon 13[LIB] created thread 13 [802019200] Oct 4 17:43:09 charon 12[LIB] created thread 12 [80201ab00] Oct 4 17:43:09 charon 11[LIB] created thread 11 [802019700] Oct 4 17:43:09 charon 10[LIB] created thread 10 [802180500] Oct 4 17:43:09 charon 09[LIB] created thread 09 [80201a100] Oct 4 17:43:09 charon 08[LIB] created thread 08 [802018800] Oct 4 17:43:09 charon 04[LIB] created thread 04 [802017900] Oct 4 17:43:09 charon 06[LIB] created thread 06 [802019c00] Oct 4 17:43:09 charon 07[LIB] created thread 07 [802018d00] Oct 4 17:43:09 charon 02[LIB] created thread 02 [802016f00] Oct 4 17:43:09 charon 03[LIB] created thread 03 [802017400] Oct 4 17:43:09 charon 01[LIB] created thread 01 [802016a00] Oct 4 17:43:09 charon 00[JOB] spawning 16 worker threads Oct 4 17:43:09 charon 00[LIB] unable to load 8 plugin features (7 due to unmet dependencies) Oct 4 17:43:09 charon 00[LIB] loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap whitelist addrblock counters Oct 4 17:43:09 charon 00[LIB] unloading plugin 'eap-sim-file' without loaded features Oct 4 17:43:09 charon 00[CFG] loaded 0 RADIUS server configurations Oct 4 17:43:09 charon 00[LIB] feature CUSTOM:sim-provider in plugin 'eap-sim-file' has unmet dependency: CUSTOM:eap-sim-file-triplets Oct 4 17:43:09 charon 00[LIB] feature CUSTOM:sim-card in plugin 'eap-sim-file' has unmet dependency: CUSTOM:eap-sim-file-triplets Oct 4 17:43:09 charon 00[LIB] feature CUSTOM:eap-sim-file-triplets in plugin 'eap-sim-file' failed to load Oct 4 17:43:09 charon 00[CFG] opening triplet file /usr/local/etc/ipsec.d/triplets.dat failed: No such file or directory Oct 4 17:43:09 charon 00[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets' Oct 4 17:43:09 charon 00[CFG] loading crls from '/usr/local/etc/ipsec.d/crls' Oct 4 17:43:09 charon 00[CFG] loading attribute certificates from '/usr/local/etc/ipsec.d/acerts' Oct 4 17:43:09 charon 00[CFG] loading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts' Oct 4 17:43:09 charon 00[CFG] loading aa certificates from '/usr/local/etc/ipsec.d/aacerts' Oct 4 17:43:09 charon 00[CFG] loading ca certificates from '/usr/local/etc/ipsec.d/cacerts' Oct 4 17:43:09 charon 00[LIB] feature CERT_DECODE:OCSP_REQUEST in plugin 'pem' has unmet dependency: CERT_DECODE:OCSP_REQUEST Oct 4 17:43:09 charon 00[LIB] feature PRIVKEY:BLISS in plugin 'pem' has unmet dependency: PRIVKEY:BLISS Oct 4 17:43:09 charon 00[LIB] feature PRIVKEY:DSA in plugin 'pem' has unmet dependency: PRIVKEY:DSA Oct 4 17:43:09 charon 00[CFG] ipseckey plugin is disabled Oct 4 17:43:09 charon 00[LIB] feature PUBKEY:DSA in plugin 'pem' has unmet dependency: PUBKEY:DSA Oct 4 17:43:09 charon 00[LIB] feature PUBKEY:BLISS in plugin 'pem' has unmet dependency: PUBKEY:BLISS Oct 4 17:43:09 charon 00[NET] enabling UDP decapsulation for IPv6 on port 4500 failed Oct 4 17:43:09 charon 00[KNL] unable to set UDP_ENCAP: Invalid argument Oct 4 17:43:09 charon 00[LIB] plugin 'counters': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'addrblock': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'whitelist': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'xauth-eap': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'xauth-generic': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-peap': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-ttls': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-tls': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-radius': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-dynamic': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-mschapv2': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-md5': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-sim-file': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-sim': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'eap-identity': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'updown': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'vici': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'stroke': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'socket-default': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'resolve': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'kernel-pfroute': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'kernel-pfkey': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'attr': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'curl': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'hmac': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'cmac': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'xcbc': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'curve25519': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'fips-prf': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'openssl': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pem': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'ipseckey': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'sshkey': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'dnskey': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pgp': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pkcs12': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pkcs8': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pkcs7': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pkcs1': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'pubkey': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'constraints': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'revocation': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'x509': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'nonce': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'random': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'md5': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'md4': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'sha1': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'sha2': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'rc2': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'blowfish': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'des': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'aes': loaded successfully Oct 4 17:43:09 charon 00[LIB] plugin 'unbound': loaded successfully Oct 4 17:43:09 charon 00[DMN] Starting IKE charon daemon (strongSwan 5.7.1, FreeBSD 11.2-RELEASE-p10, amd64) Oct 4 17:43:09 ipsec_starter 41033 no known IPsec stack detected, ignoring! Oct 4 17:43:09 ipsec_starter 41033 no KLIPS IPsec stack detected Oct 4 17:43:09 ipsec_starter 41033 no netkey IPsec stack detected Oct 4 17:43:09 ipsec_starter 41033 Starting strongSwan 5.7.1 IPsec [starter]... -
@chris_6n said in IPsec ERROR: Could not find phase 1:
IPsec ERROR:
Hello
PFSense uses PHP's built-in function Net_IPv6::checkIPv6 to verify that the ipv6 address is valid. If this function returns the value that the address is invalid, then this error is displayed.This function returns true if the ipv6 address contains 8 groups of 4 hexadecimal digits (128 bits)
-
-
@chris_6n
You can try editing the file /etc/inc/vpn.inc and disable address verification
line 280-283
but I don't know if Strongswan or PFSense will work correctly after that .
I recommend saving the original file before editing itif (!is_ipaddr($ep)) { log_error(sprintf(gettext("IPsec ERROR: Could not find phase 1 source for connection %s. Omitting from configuration file."), $ph1ent['descr'])); continue; }you have to do this
/* if (!is_ipaddr($ep)) { log_error(sprintf(gettext("IPsec ERROR: Could not find phase 1 source for connection %s. Omitting from configuration file."), $ph1ent['descr'])); continue; } */ -
The error message in the system log is no longer available.
The rest is as before. It did not need success.
IPSec status is Unknown.There must be another IP Check function.
Who builds something like that?Many people in Germany get such ip addresses.
From German glass fiber. -
I do not see that
is_ipaddr()fails when given an address ending in a::.There must be something else going on.
For instance, you can run the following in Diagnostics > Command Prompt at the bottom:
$ep = "2A00:61e0:47e1:74A2::"; if (!is_ipaddr($ep)) { echo sprintf(gettext("Invalid IPv6 address: %s"), $ep); } else { echo sprintf(gettext("VALID IPv6 address: %s"), $ep); }And you get:
VALID IPv6 address: 2A00:61e0:47e1:74A2::Change it to something invalid and it does the expected:
$ep = "2A00:61e0:47e1:74A2::g"; if (!is_ipaddr($ep)) { echo sprintf(gettext("Invalid IPv6 address: %s"), $ep); } else { echo sprintf(gettext("VALID IPv6 address: %s"), $ep); }Invalid IPv6 address: 2A00:61e0:47e1:74A2::g -
Okay, I have tested it.
The result with my IP address is VALID IPv6 address.Can it be that behind the IP address is a hidden blank?
In the Dashboard Interfaces behind my address is also a hidden blank!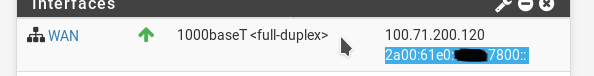
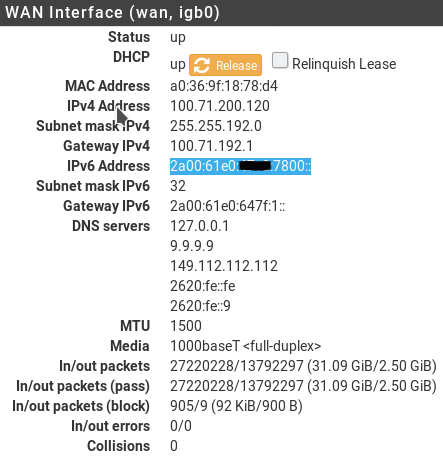
In the Status / Interfaces there is no hidden blank behind it.