Clarification on Gateway for users
-
Hi,
I was wondering if someone could clear up my question, currently we have dual WAN, the idea i that i want a set of users to navigate on the WAN2 which has better speeds then the default WAN, ( i dont put it as the default because that IP is registered with the banks and changing that is a headache) so i put a pool of IP on the LAN and on advance i put the gateway to use WAN2, as soon as i do that, those users cannot see another VLANs would i also need to put a rule on the VLAN?Thank you
-
If you state a gateway in a filter rule this rule allows only traffic to that gateway. Since the gateway cannot reach your other internal networks, they are not accessible.
So you have to add an additional filter rule with your internal networks in the destination box and without a gateway stated and put this rule to the top of the rule set.
-
https://www.netgate.com/docs/pfsense/routing/bypassing-policy-routing.html
https://docs.netgate.com/pfsense/en/latest/book/multiwan/policy-routing-configuration.html#bypassing-policy-routing
-
Thanks for the reply, so adding those rules i can see now ping the VLANs but whats odd is that the IP i want to use to navigate on the WAN2 is not navegating on the WAN2 it still using the WAN default.
the ip 192.168.3.211, now 192.168.3.211 can ping the VLAN scannerfreenas NET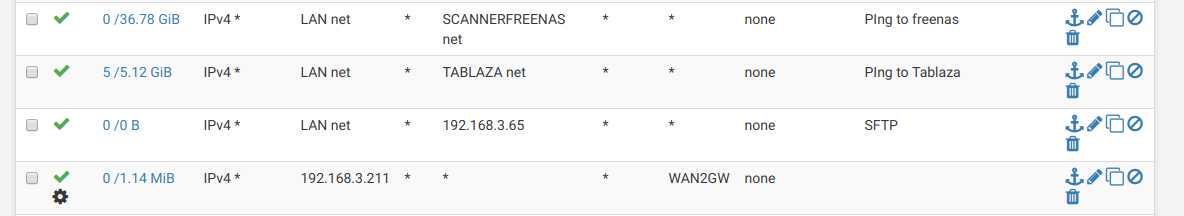
-
Is the WAN2 gateway marked as up?
-
Thanks for the reply, correct it is up and running
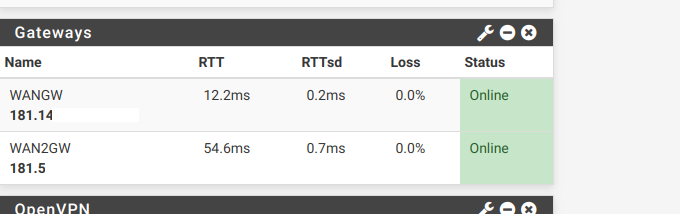
-
Then there is some other rule somewhere matching and passing the traffic, or you are looking at dangling states. Reload www.wimi.com a couple times.
-
Thanks for the reply, after carefully looking at the rules, it was a rule of the squid as i have WPAD i disabled on the machine the autodetect and now it shows the the WAN2 gateway but whats very odd i tried to ping my email server, which is on the VIP on the WAN2 i check the states and saw this, i tried adding the IP of the email server on top the 192.168.3.213 but no luck. The VIP of the email server ends in 236
LAN icmp 192.168.3.211:1 -> 192.168.3.213:1 (181..xx.xxx.236:1) 0:0 35 / 0 2 KiB / 0 B WAN2 icmp 181.57.xx.xx:36351 (192.168.3.211:1) -> 192.168.3.213:36351 0:0 35 / 0 2 KiB / 0 B LAN tcp 192.168.3.211:56953 -> 192.168.3.213:80 (181.xx.xx.236:80) CLOSED:SYN_SENT 2 / 0 104 B / 0 B WAN2 tcp 181.57.xxx.xx:60892 (192.168.3.211:56953) -> 192.168.3.213:80 SYN_SENT:CLOSED 2 / 0 104 B / 0 BThank you
-
So you are trying to connect to a port-forwarded IP address? You will need to bypass policy routing for that too.
A better solution than NAT reflection is split DNS so inside connections are made to inside IP addresses.
-
@Derelict said in Clarification on Gateway for users:
split DNS
Thanks for the reply, yes that's correct currently I have NAT reflection , a split DNS is just an A record on pfSense on Host override? so if mail.mydomain.com to resolve to the 192.168.3.213 rather then resolving by the WAN?
Thank you
-
Yes. You will have to also bypass that NAT reflected address and it should work.
Split DNS is better. But better is subjective.
Put a bypass rule like the others but for destination 192.168.3.213
-
Thanks for the reply, your right it had to be done that way thank you again